Cloud NGFW for AWS
Create an NGFW Resource on AWS
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Create an NGFW Resource on AWS
Create a Cloud NGFW for AWS resource.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Now that you have created rulestacks and rules, you can create an NGFW resource and
associate a local rulestack with that NGFW. During the configuration of your NGFW,
you must choose how to create NGFW endpoints—automatically or manually. If you chose
to manually create NGFW endpoints, you create NGFW endpoints in the
availability zones you specify.
Complete the following steps to create an NGFW.
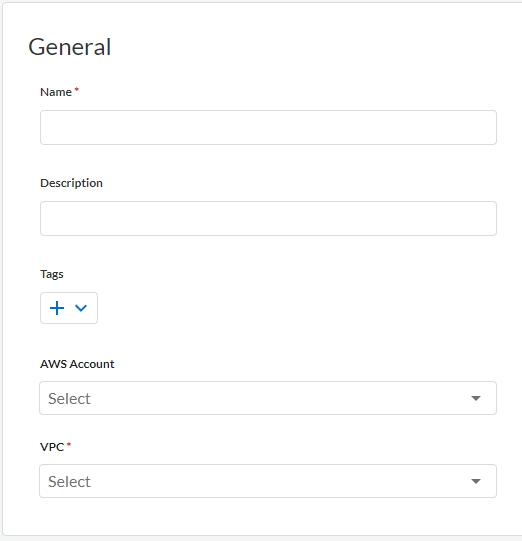
- Select NGFWs.Click Add Firewall.Enter a descriptive Name.(Optional) Enter a Description.Select an AWS Account from the drop-down to associate with this NGFW.Select a VPC from the drop-down.
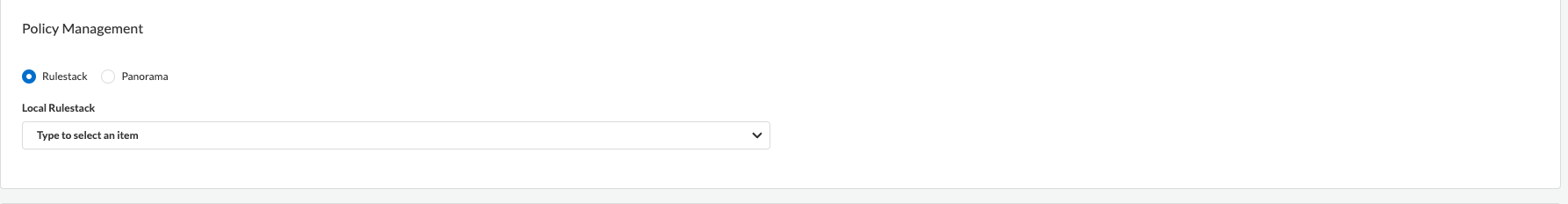
![]() In the Policy Management section, select a local rulestack from the drop-down.
In the Policy Management section, select a local rulestack from the drop-down.![]() Specify AWS availability zones or subnets. Specify whether or not the Cloud NGFW tenant will (service-managed mode) or won't (customer-managed mode) deploy NGFW endpoints.
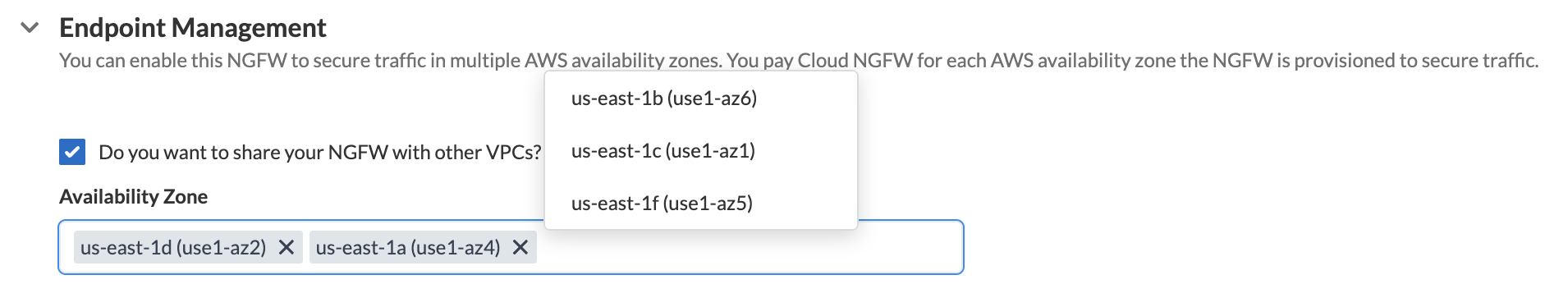
Specify AWS availability zones or subnets. Specify whether or not the Cloud NGFW tenant will (service-managed mode) or won't (customer-managed mode) deploy NGFW endpoints.- Yes (service-managed)—in service-managed mode, the Cloud NGFW tenant automatically creates NGFW endpoints in the VPC subnets you specify. Perform the endpoint management for service-managed mode through Cloud NGFW console only. The endpoint management for service-managed mode can only be done by associating or disassociating a subnet. Associating a subnet creates the endpoint and disassociating a subnet removes the endpoint.
- No (customer-managed)—in customer-managed mode, you must manually create NGFW endpoints in each availability zone you specify.
In the Endpoint Management section, you can enable your Cloud NGFW for securing traffic in multiple AWS availability zones. You pay for each AWS availability zone that your NGFW is provisioned to secure traffic. You can manage how the endpoints are created for your NGFW in these availability zones. You pay AWS for each VPC (gateway load balancer) endpoint that you create for your NGFW.The Availability Zone displays the Zone ID and the corresponding Availability Zone Name in your Palo Alto Networks account. Use this information when mapping your availability zones to your AWS accounts.![]() Click Create.
Click Create.