Cloud NGFW for AWS
View Audit Logs on Cloud NGFW for AWS
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
View Audit Logs on Cloud NGFW for AWS
Learn about audit logging on Cloud NGFW for AWS.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Track administrator activity on Cloud NGFW for AWS to achieve real-time reporting of
activity across your deployment. If you have reason to believe that an administrator
account is compromised, the audit log provides you with a full history of where an
administrator navigated throughout the Cloud NGFW tenant and what configuration
changes they made so you can analyze in detail and respond to all actions taken be
the compromised account.
If you have already deployed Cloud NGFW for AWS, you may need to update your CFT. If
your current CFT does not include the Audit Log field.
The log group must be created in the AWS console in the same
region where the Cloud NGFW CFT was deployed.
When an event occurs, an audit log is generated and forwarded to the CloudWatch log
group you specify.
- If necessary, update your CFT to add permissions necessary to write to the Audit Log CloudWatch log group.
- Log in to the Cloud NGFW console.Select AWS AccountsDownload CFT to download the CFT as a yaml file.Upload, edit, and apply your CFT to the AWS console.
- Log in to the AWS Console and select CloudFormationStacks.
- Locate the Cloud NGFW stack—PaloAltoNetworksCrossAccountRoleSetup.
- Select Update.
- Select Replace current template and Upload a template file.
- Select your CFT yaml file and click Next.
- Verify the CFT stack setting and click Next.
- Verify the CFT stack options and click Next.
- Review the CFT stack and click Update.
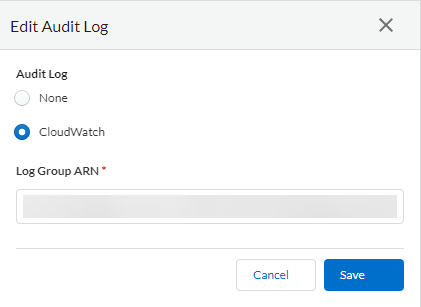
Log in to the Cloud NGFW tenant console.Select Tenant.Click the Audit Log Settings edit icon.![]() Select the CloudWatch radio button.Enter the Amazon Resource Name (ARN) of your target CloudWatch Log Group.Ensure that the ARN you enter here corresponds with the CloudWatch Log Group you specified in your CFT stack.Click Save.
Select the CloudWatch radio button.Enter the Amazon Resource Name (ARN) of your target CloudWatch Log Group.Ensure that the ARN you enter here corresponds with the CloudWatch Log Group you specified in your CFT stack.Click Save.![]()