Cloud NGFW for AWS
Introducing Cloud NGFW for AWS
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Introducing Cloud NGFW for AWS
Cloud NGFW for AWS is Palo Alto Networks ML-Powered Next-Gen Firewall (NGFW).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can discover Cloud NGFW in the AWS Marketplace and consume it in your AWS virtual private
clouds (VPC). With Cloud NGFW, you can access the core NGFW capabilities such as App-ID,
URL filtering based on URL categories and geolocations, SSL/TLS decryption, etc.
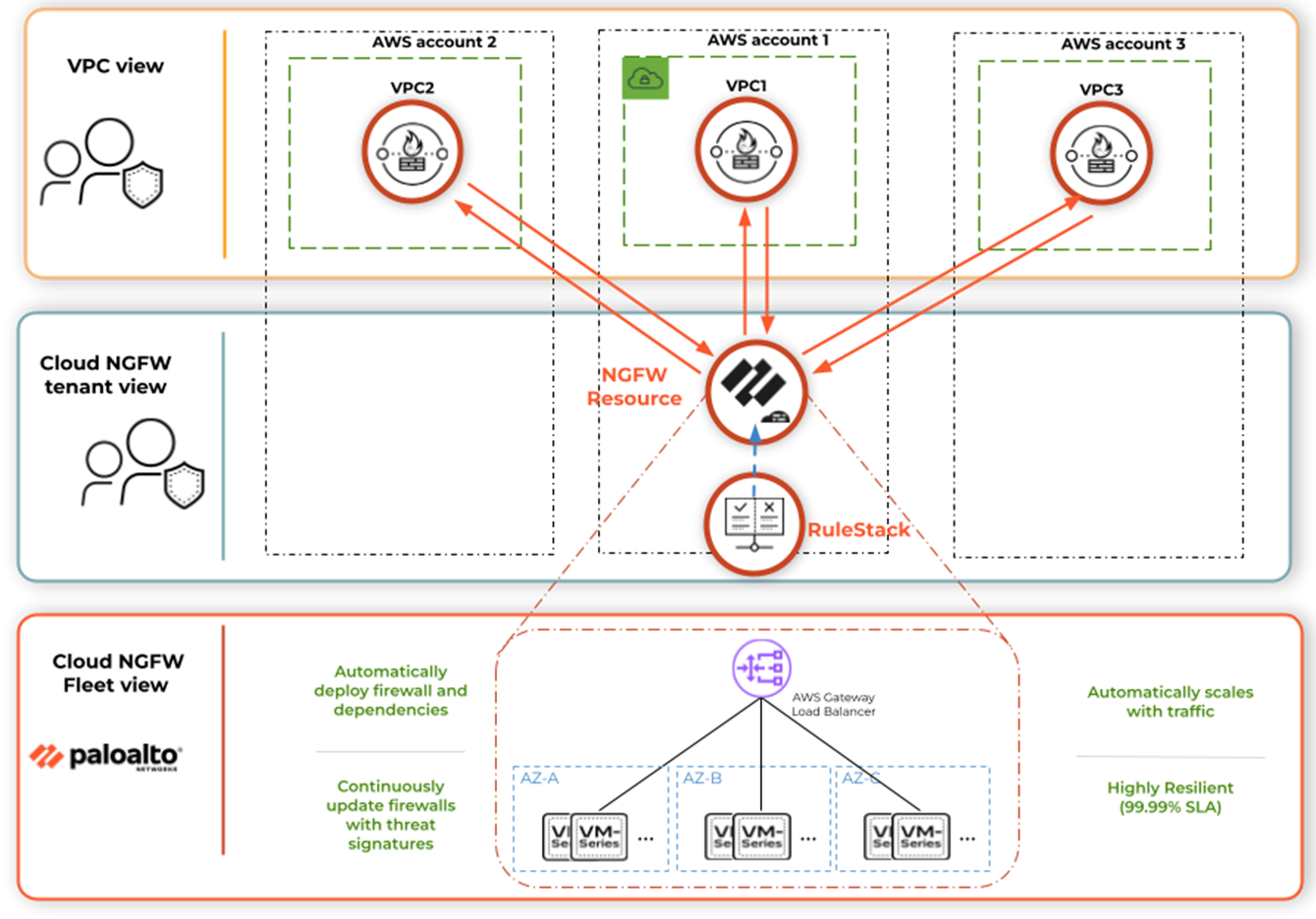
Cloud NGFW Components
Cloud NGFW for AWS creates a number of components that work together to secure your
AWS environment.
- The Cloud NGFW tenant is an instantiation of the Cloud NGFW service associated with your AWS account when one of your AWS users subscribes to the service. Cloud NGFW designates you, the subscribing AWS user, as the administrator of a Cloud NGFW tenant (the TenantAdmin user role), who can invite other users to the tenant. Based on the assigned role, other users can create Cloud NGFW resources and configure rulestacks with the tenant.
- The Cloud NGFW Resource (or simply NGFW) is associated with your VPC and can span multiple availability zones. This resource has built-in resiliency, scalability, and lifecycle management.
- To use the Cloud NGFW resource, you create a dedicated subnet in your VPC for each desired AWS availability zone, then create NGFW endpoints on the subnets and update the VPC route tables to send the traffic through these Cloud NGFW endpoints.
- Rulestacks define the NGFW traffic filtering behavior such as advanced access control (App-ID, URL Filtering) and threat prevention. A rulestack includes a set of security rules and the associated objects and Security Profiles. To use a rulestack, you associate the rulestack with one or more NGFW resources. Cloud NGFW provides two types of rulestacks.Cloud NGFW supports two types of Rulestacks:
- Local Rulestack: Local account administrators can associate a local rulestack with an NGFW in their AWS account. A local rulestack includes local rules.
- Global Rulestack: The AWS Firewall Manager administrator can author a firewall Manager Service (FMS) policy and associate a Global Rulestack with it. AWS Firewall Manager manages the Global Rulestack across all these NGFWs in different AWS accounts of an AWS Organization. A Global Rulestack includes pre-rules and post-rules.
About Cloud NGFW Endpoints
The NGFW is a firewall resource, dedicated to the VPC you specify, that provide
next-generation firewall capabilities. Upon creation, an NGFW is associated with one
or more VPCs. NGFW endpoints are constructs created—manually or automatically—in
each availability zone in the VPCs you specify. The NGFW applies your Security
policy to the traffic received by the NGFW endpoints and enforces that policy. When
creating your NGFW, you must specify at least one VPC and a local rulestack.
Additionally, you must also specify how and where the associated NGFW endpoints are
deployed.
NGFW endpoints are responsible for directing traffic to the NGFW for inspection and
enforcement. NGFW endpoints intercept traffic and route it to the NGFW for
inspection and policy enforcement. You can use two management modes to create
endpoints automatically or manually.
- In a service-managed mode, the Cloud NGFW tenant creates an endpoint in each to subnet you specify. The NGFW service retrieves a list of subnets in the VPC you specified and, from that list, you choose the subnets that should have an endpoint.
- In a customer-managed mode, choose existing availability zones that need to be secured in your specified VPC and then manually create the NGFW endpoints in existing subnets in the chosen availability zones. After the NGFW has been created, you must go to the AWS console to complete the NGFW endpoint creation process.
After creating an NGFW and NGFW endpoints, you must update your AWS route tables to
ensure that traffic is sent to the NGFW. Which route tables you update and how you
update them depends on your specific deployment. See Direct Traffic to Cloud NGFW for more
information.
Cloud NGFW in Action
- Subscribe to the Cloud NGFW Service—Begin by subscribing to the Cloud NGFW for AWS service through the AWS Marketplace. After subscribing, you can create a Cloud NGFW Tenant. The subscribing AWS IAM user is the Tenant administrator (TenantAdmin), which allows that user to invite additional users and assign roles. Add your AWS account to the Cloud NGFW tenant. Adding your account grants the necessary permissions needed by Cloud NGFW to store logs, create NGFW endpoints, and access the keys needed for decryption.
- Create Rulestacks—After adding users and assigning roles in the Cloud NGFW tenant console, Local Rulestack admins can author a rule and rulestacks.
- Create NGFWs—Deploy NGFW firewall resources to protect your VPCs. While creating your NGFWs, associate the local rulestacks you created previously.You have two options to create Cloud NGFW endpoints. In the first (service managed) option, you create a dedicated subnet in your VPC for each desired AWS availability zone, then specify those subnets when creating Cloud NGFW resources. In this option, Cloud NGFW creates the NGFW endpoints in your subnets. Alternatively, in the second (customer managed) option, you specify the desired AWS availability zones, where you want the NGFW resource to secure the traffic. In this option, Cloud NGFW creates a Cloud NGFW resource only that will manifest as VPC endpoint resources in your AWS account. You're then responsible for creating a dedicated subnet in your VPC for each desired AWS availability zone, and create the VPC endpoints as well
- Update VPC route tables—After deploying your Cloud NGFW resource, you must Direct Traffic to Cloud NGFW for more information by updating your VPC route tables, this directs traffic to the NGFW firewall resource for inspection and enforcement.
Cloud NGFW Use Cases
Cloud NGFW provides you with the tools and functionality to secure inbound traffic,
outbound traffic, and East-West traffic.
- Inbound traffic refers to any traffic originating outside of your AWS region and bound for resources inside your application VPCs, such as servers or load balancers. Cloud NGFW can prevent malware and vulnerabilities from entering your VPC in the inbound traffic allowed by AWS security groups.
- Outbound traffic refers to traffic originating within your application VPC. Direct this traffic to destinations outside of the AWS region. Cloud NGFW protects outbound traffic flows by ensuring that resources in your application VPC connect to allowed services and allowed URLs while preventing exfiltration of sensitive data and information.
- East-West traffic is traffic that moves within an AWS region. Specifically, you deploy traffic between source and destination in two different application VPCs or in two different subnets in the same VPCs. Cloud NGFW can stop the propagation of malware within your AWS environment.
