Cloud NGFW for AWS
Getting Started from an AWS Members Account
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Getting Started from an AWS Members Account
Learn how to subscribe and add users to your Cloud NGFW for AWS
deployment.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Complete the following steps to subscribe to the Cloud NGFW service—you can subscribe
to a Cloud NGFW Pay-as-you-go (PAYG) SaaS Subscription.
This procedure begins the process of creating your first user—a tenant administrator.
A tenant admin is the highest level of user in the Cloud NGFW service. It provides
the ability to add AWS accounts to the Cloud NGFW service and onboard additional
users.
Create a Cloud NGFW PAYG SaaS subscription before you can sign up for a Cloud
NGFW for AWS Credits contract.
Cloud NGFW PAYG SaaS Subscription
Before you subscribe to and deploy Cloud NGFW for AWS in your AWS
environment, you must consider and create the following. During the subscription
process, you define the parameters described below in a CloudFormation Template
(CFT) to complete the initial configuration.
- Endpoint configuration (Mandatory)—the cross-account IAM role includes permissions to permit Cloud NGFW to read VPC resource information, which is required for configuring NGFW endpoints.
- Endpoint Creation (Optional)—you can configure Cloud NGFW to create and manage NGFW endpoints in your AWS environment. By selecting Yes, you're giving Cloud NGFW permissions to create and manage the necessary endpoints in your VPCs. If you select No, you must create and view NGFW endpoints manually.
- Permissions for Logging (Optional)—Cloud NGFW allows you to send traffic, threat, and decryption logs to an S3 bucket, Cloudwatch Log Group, or Kinesis Data Firehose. For Cloud NGFW to send those logs to the intended destination, you must provide the necessary permissions.The Cloud NGFW console redirects you to the AWS CloudFormation console and prompts you to create a stack. This stack sets up cross-account IAM roles, designates (but does not create) logging destinations, and lets Cloud NGFW access certificates in your AWS account’s Secrets Manager for decryption.The stack prepopulates the logging destinations for CloudWatch log group and Kinesis Data Firehose delivery stream with a destination called PaloAltoCloudNGFW. The S3 Bucket field is not prepopulated. If you want to send the logs to a different destination, you should create that destination and replace the default value the name before you complete stack creation.For an S3 Bucket log destination, you must provide the name of the destination bucket.If you are using a Kinesis Data Firehose, the source for that delivery stream must Direct PUT.
- Audit Logging (Optional)—you can send audit logs, which track administrator activity, to a Cloudwatch Log Group. The CFT stack includes a default Cloudwatch Log Group destination called PaloAltoCloudNGFWAuditLog. You can create a Cloudwatch Log Group with the default name value or replace the default value with the name of another Cloudwatch Log Group.
- Permissions for Decryption (Optional)—to use Cloud NGFW to inspect encrypted traffic flows, you must allow Cloud NGFW to retrieve the necessary certificate from the AWS Secrets Manager. You must enable Cloud NGFW to use attribute-based access control by specifying a tag when you launch the CFT stack.By default, the CFT includes the tag PaloAltoCloudNGFW. You can change this tag by configuring the ARN in the service and replacing the default value in the CFT.
Complete this procedure to subscribe with a Cloud NGFW PAYG SaaS Subscription.
- Log in to the AWS Console.Navigate to the Cloud NGFW for AWS in the AWS Marketplace.Click Subscribe.Click Set up product. This launches the Configure and Launch (SaaS Quick Launch) page in AWS Marketplace. Palo Alto Networks has enabled its Cloud NGFW products with quick launch and you can now create and deploy a new tenant using the quick launch.
![]() Click Enable integration on the Configure and Launch page of the quick launch to ensure that you have the required IAM permissions from AWS.If you are a new user, the Enable integration button automatically appears in the Step 1 of the Configure and Launch page.
Click Enable integration on the Configure and Launch page of the quick launch to ensure that you have the required IAM permissions from AWS.If you are a new user, the Enable integration button automatically appears in the Step 1 of the Configure and Launch page.![]() Click Login or create an account button to either sign in to an existing account or to create a new account on the vendor website. This takes you to a Create Tenant registration page of the Cloud NGFW for AWS Tenant.
Click Login or create an account button to either sign in to an existing account or to create a new account on the vendor website. This takes you to a Create Tenant registration page of the Cloud NGFW for AWS Tenant.![]()
- If you are a new user, you will need to create a Cloud NGFW account. Enter your email address.You must use the same email when you log in to the Cloud NGFW service for the first time. Additionally, upon logging in for the first time, this email address is used to create the first user—a tenant admin. Additionally, the email address domain of users invited by the tenant admin must match the email address domain of the tenant admin’s login credentials.Enter your First and Last Name.Click Create.After you click Create, an email with an activation button is sent to the email address you entered above.
![]() Click the Activate Account button in the email you received.The link is active for 7 days. If you don't click the link within 7 days, you will need to request for activation mail to be resent.
Click the Activate Account button in the email you received.The link is active for 7 days. If you don't click the link within 7 days, you will need to request for activation mail to be resent.![]() Enter and re-enter your new password.Click Create My Account.
Enter and re-enter your new password.Click Create My Account.![]() Configure your multifactor authentication (MFA).
Configure your multifactor authentication (MFA).![]() If you have not registered to MFA, but know your SSO password, you are prompted to register to MFA on your first login to any of the applications. To reset MFA, raise a support ticket.Choose one of the MFA methods and click Setup.Complete the MFA verification process —For example, If you click the Setup button for Email Authentication, you will be prompted to click the Send me the code button. On clicking, you will receive an email with the verification code. Enter the verification code and click Verify. Alternatively, you may choose to complete the MFA verification process using Okta Verify, Security Key or Biometric Authenticator or the Google Authenticator.Sign in to the Tenant with your registered email and password and click Continue to Finish Subscription.
If you have not registered to MFA, but know your SSO password, you are prompted to register to MFA on your first login to any of the applications. To reset MFA, raise a support ticket.Choose one of the MFA methods and click Setup.Complete the MFA verification process —For example, If you click the Setup button for Email Authentication, you will be prompted to click the Send me the code button. On clicking, you will receive an email with the verification code. Enter the verification code and click Verify. Alternatively, you may choose to complete the MFA verification process using Okta Verify, Security Key or Biometric Authenticator or the Google Authenticator.Sign in to the Tenant with your registered email and password and click Continue to Finish Subscription.![]() The quick launch page now shows that you have successfully linked your account to the AWS Marketplace subscription.
The quick launch page now shows that you have successfully linked your account to the AWS Marketplace subscription.![]()
- If you are an existing user and have not registered to SSO, but wish to create a new tenant using the same email id, you will receive an activation email after logging into the tenant. Follow steps 6d to 6k to register your tenant.If you are an existing user on Cloud NGFW, but not a Tenant Admin, then MFA is currently not available. You will continue to login without being prompted for MFA registration.If you are an existing user who has registered to SSO and wish to create a new tenant using the same email id, you will be prompted to select a Tenant and click Continue.Click Launch Template and select the CFT region and create roles and permissions for your tenant.Cloud NGFW opens the AWS CloudFormation template (CFT) console associated with the AWS account you specified in a new browser tab. If you have a pop-up blocker installed, the new tab might be blocked. In this case, in the Cloud NGFW console, select AWS Accounts and locate the AWS account you just added. Click Pending in the Status column.In the Capabilities section at the bottom of the CFT console, check I acknowledge that AWS CloudFormation might create IAM resources.Click Create Stack. The CFT associated with the subscription (for example, PaloAltoNetworksCrossAccountRoleSetup) appears.Click Launch your product.
- Enter your email and password, then click Log In.Select AWS Accounts.Verify that the Status has changed to Success.The Onboarding Status remains in the Pending state until AWS has finished launching the CFT.
![]() SAML 2.0 can be used as an identity provider for Cloud NGFW for AWS. For more information, see Manage Third Party Identity Provider Integrations Through Common Services and How To Enable a Third-Party Identity Provider (IDP).
SAML 2.0 can be used as an identity provider for Cloud NGFW for AWS. For more information, see Manage Third Party Identity Provider Integrations Through Common Services and How To Enable a Third-Party Identity Provider (IDP).Secure Your Current Cloud NGFW Access Using SSO and MFA
Use the information in this section to migrate an existing cognito user to SSO. If you are an existing user of Cloud NGFW for AWS, you need to register for additional security measures, such as SSO and MFA for an existing tenant (by activating the user email with SSO+MFA), in order to login and access existing tenants.- Enter the email address with which you have registered to AWS Cloud NGFW and click Log in.
![]() Enter the password and click Log in.You will be prompted to register to Palo Alto Networks Single Sign-On (SSO).
Enter the password and click Log in.You will be prompted to register to Palo Alto Networks Single Sign-On (SSO).![]() Click Continue to continue with registering to SSO. Alternatively, you may choose to click Register Later to continue with your previous login credentials. However, you will be prompted to register to SSO each time you try to login.
Click Continue to continue with registering to SSO. Alternatively, you may choose to click Register Later to continue with your previous login credentials. However, you will be prompted to register to SSO each time you try to login.![]() You will receive an email with instructions to register to SSO. Follow the instructions and complete the registration to SSO and MFA as described above.Click Continue.During your next login, you will be prompted with the Enable and Log Out button to log back in using SSO.
You will receive an email with instructions to register to SSO. Follow the instructions and complete the registration to SSO and MFA as described above.Click Continue.During your next login, you will be prompted with the Enable and Log Out button to log back in using SSO.![]() Enter your email address and click Log in. You will be prompted with the SSO Sign In page.Enter your email address and click Next.Enter the password and click Log In.Complete the MFA verification process. You will now be able to access the Cloud NGFW tenant page after logging in with your SSO credentials.
Enter your email address and click Log in. You will be prompted with the SSO Sign In page.Enter your email address and click Next.Enter the password and click Log In.Complete the MFA verification process. You will now be able to access the Cloud NGFW tenant page after logging in with your SSO credentials.Multi Tenant User of a Single User Supported on Multiple Tenants
The Cloud NGFW for AWS supports single login credentials for multiple tenants. When you log into the Cloud NGFW console, login credentials are used to associate the user with the appropriate tenant. If the same login credentials are used for multiple tenants, the login page prompts you to select the tenant you want to configure.After logging in to the Cloud NGFW, use the drop-down menu to select the appropriate tenant, then click Continue.![]() The table below illustrates use cases for multi-tenant scenarios:Use caseStepsUser A has already registered to tenant A and user A is being invited to tenant B.You will not receive an activation email.User A has already registered to tenant A and subscribes to a new tenant through the AWS Marketplace subscription.You will not receive an activation email.
The table below illustrates use cases for multi-tenant scenarios:Use caseStepsUser A has already registered to tenant A and user A is being invited to tenant B.You will not receive an activation email.User A has already registered to tenant A and subscribes to a new tenant through the AWS Marketplace subscription.You will not receive an activation email.Add Multiple AWS Accounts
You can onboard multiple AWS accounts onto the same tenant. Once onboarded, you can create firewall resources in multiple accounts. Additionally, you’ll have the ability to deploy Cloud NGFW endpoints across onboarded accounts for the firewall resource in any AWS account.Your AWS account subscription integrates with an enhanced subscription experience from the AWS Marketplace Service. This integration occurs when you create a Cloud NGFW Tenant; your AWS account links to the Cloud NGFW tenant.Multiple AWS account subscriptions can be added to the tenant. Cloud NGFW supports up to 200 accounts.You can onboard multiple AWS accounts (with no new subscription requirements) to the tenant from the Cloud NGFW console, and you create firewall resources in all onboarded AWS accounts in the tenant.To facilitate ease of use, only one billing account exists in the tenant; if the billing account is unsubscribed from AWS Marketplace, the next billing account for the tenant is dynamically selected. Additional account state changes are introduced to better manage the AWS account life cycle in the tenant. When the last AWS account is unsubscribed from the tenant, it triggers a clean up of tenant resources if there is no active contract attached to the tenant.10 pending accounts are supported per tenant.In addition to support for Multi-Account Tenant, Cloud NGFW supports a multi-VPC firewall resource model. With multi-VPC support, you can enable your Cloud NGFW to secure traffic in multiple AWS VPCs. You pay for Cloud NGFW usage for each AWS availability zone for which the NGFW is provisioned to secure traffic.Use the Endpoint Management section of the Create Firewall page to manage how endpoints are created for the NGFW in these availability zones. You pay AWS for each VPC (gateway load balancer) endpoint you create for the NGFW.When using multi-VPC firewall resource, consider the following:- Multi-VPC firewalls are only supported in Customer Managed Mode.
- Endpoints for a multi-VPC firewall resource may exist in any VPC in any of the successfully onboarded accounts. 50 endpoints are supported for a multi-VPC firewall resource.
- When you disable the multi-VPC feature for a firewall resource, an endpoint can only exist in the Anchor VPC (and Anchor account). The Anchor represents a resilient connection to the availability zone. The Anchor VPC and Anchor Account refer to the VPC and the account associated with the firewall resource at creation time. Communication to the VPC fails if an endpoint exists outside the Anchor Account and VPC.
- When you remove an account from the tenant, all endpoints from multi-VPC firewalls must be removed from the account. The call fails if an endpoint exists in an account that was removed from the tenant.
- When creating endpoints across accounts for a firewall resource, the endpoints should be created in one of the zone IDs that are mapped to the zones defined in the firewall configuration.
- Zone ID names are treated differently in AWS. For separate accounts, use the same zone ID to ensure that the endpoint appears in the correct zone.
- While the account ID is optional for a single account, multiple accounts must use the account ID.
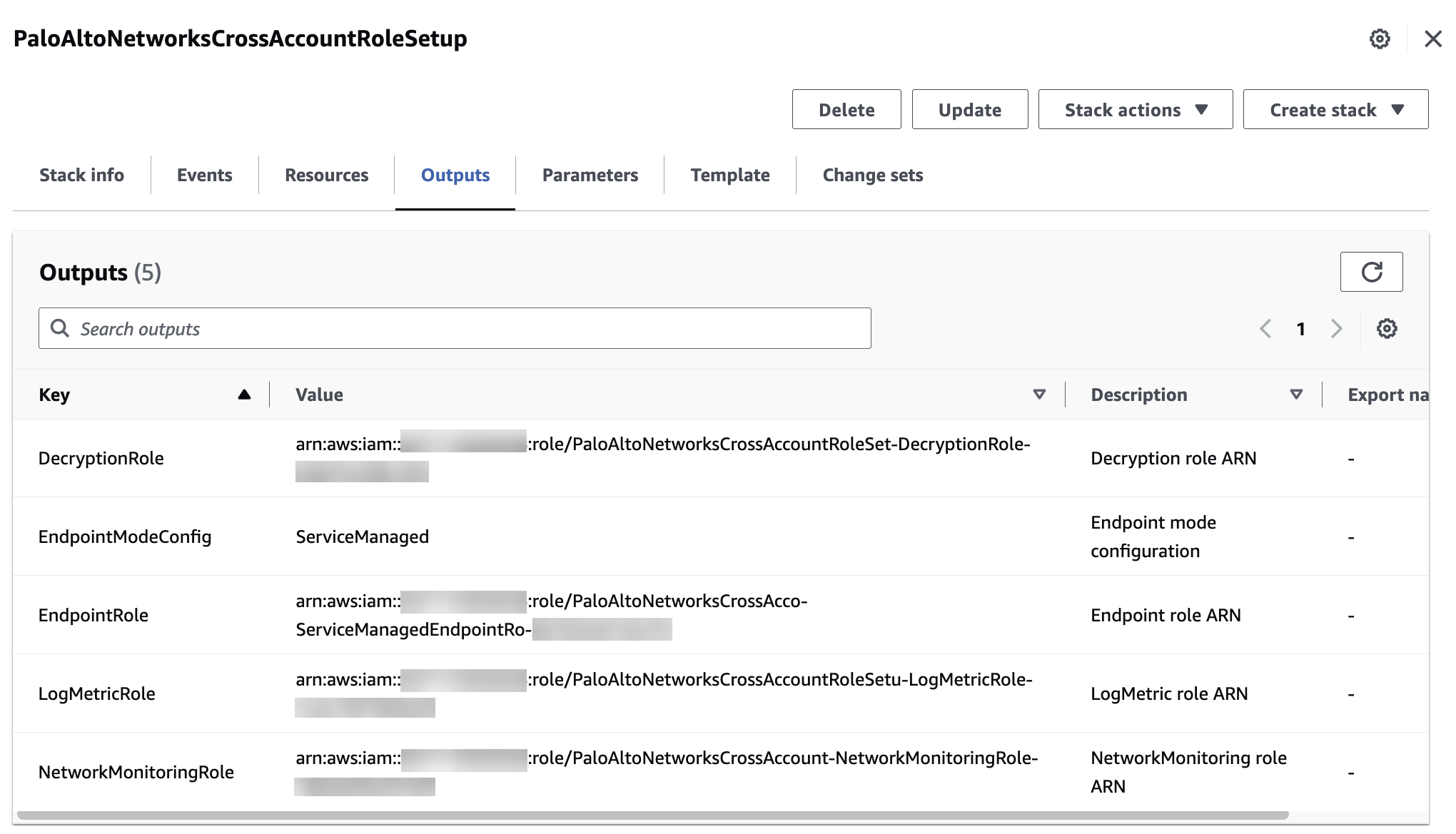
The Zone Name (for example, us-east-la) will have a different mapping to the Zone ID (for example, use1-az4) across different accounts.You can add cross account roles from your AWS account to the Cloud NGFW Tenant using the AWS Marketplace enhanced subscription experience. This process requires you to add additional IAM permissions and resource deployment. You can also use the Cloud NGFW console to manually add the role ARNs. Cross Account Roles management is supported for incremental additions of the roles.Cloudformation template update is supported.For example, the certificate in account1 and the certificate in account2 can be mapped to a rulestack in account3 which could be associated with a firewall resource in account4. In this scenario, all accounts (1-4) must be successfully onboarded.For AWS accounts that are already onboarded, you can add additional accounts using Multi-Account Tenant. Start by accessing the AWS Marketplace subscription page for your Palo Alto Networks NGFW subscription.- Access your subscription in AWS Marketplace.In Step 1, ensure that your subscription has the necessary AWS administrator permissions.In Step 2, link a new or existing vendor account. Click Login or create vendor account to access an existing Cloud NGFW account to link your tenant and enable communication with the AWS Service. The Palo Alto Networks Cloud NGFW login page appears.In the Welcome screen, click Login with an Existing Account.Enter your login credentials for the Cloud NGFW tenant. After logging in, AWS Marketplace shows that you have successfully linked your vendor account.If a CloudFormation template (CFT) does not exist for your account, of, if you need to configure an existing CFT, see the information at the end of this article for manually adding a CloudFormation template.If a CFT exists, move to Step 4 and launch the Cloud NGFW console to continue the configuration. Click Launch product.Log into the Cloud NGFW console.Select AWS Accounts.Choose the AWS Account ID for which you want to add as a Multi-Account Tenant.Click Add AWS Account.Enter the name of the AWS Accout ID for the account you want to add to the existing account.Log into your AWS account.Create a stack using the AWS console; click Create Stack on AWS, or, alternately use the AWS CLI.Select I acknowledge that AWS Cloud Formation might create IAM resources with custom names.Click Create Stack.Once the status shows CREATE_COMPLETE copy the Role ARN Value from the Outputs tab in the AWS console.
![]() Add the Role ARN values to the Cloud NGFW tenant console.
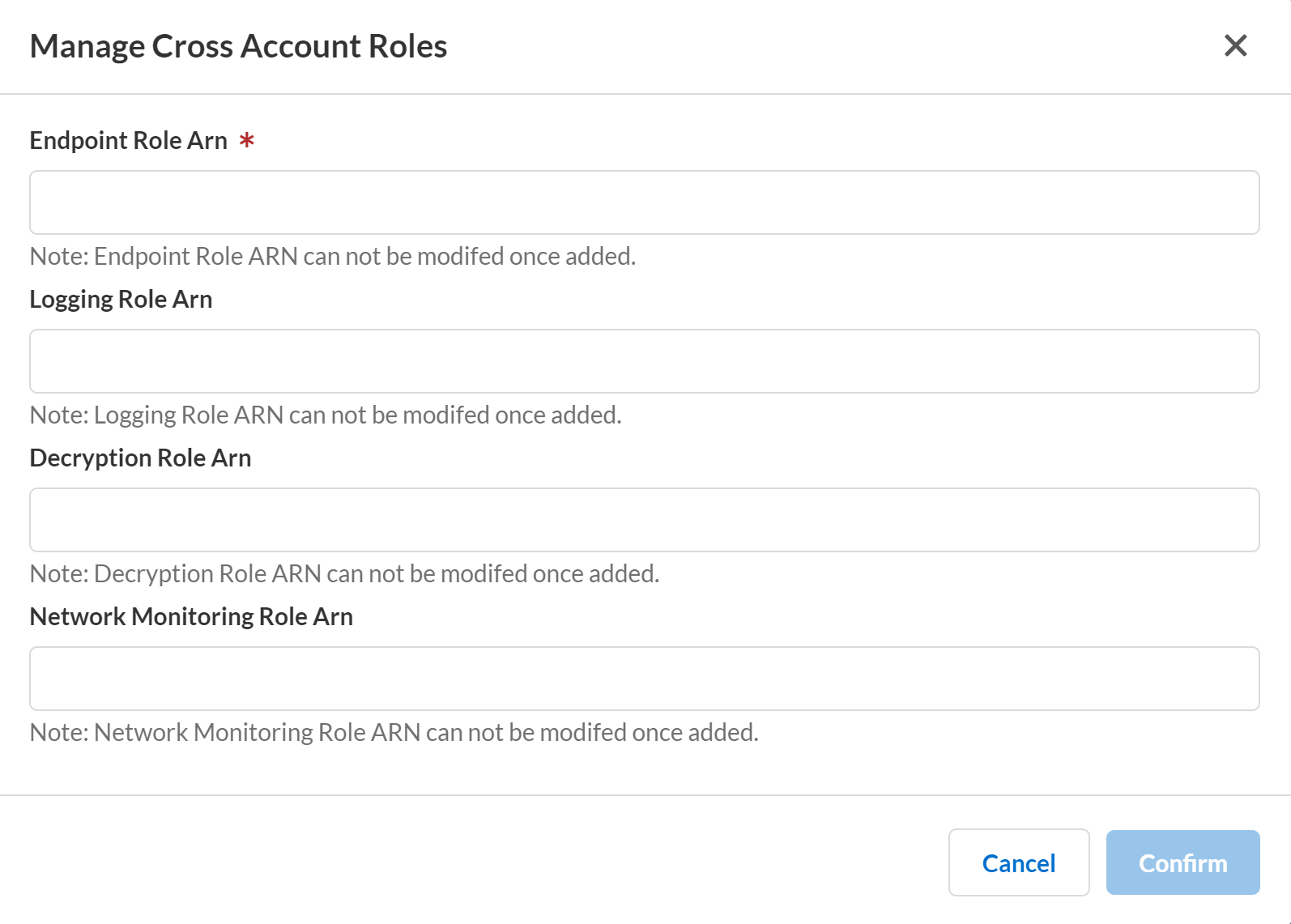
Add the Role ARN values to the Cloud NGFW tenant console.- Return the Cloud NGFW tenant console.In the Cloud NGFW tenant console, select SettingsAWS Accounts.Select the radio button of the AWS account you are adding and select Manage Cross Account Roles from the Actions drop-down.Paste the Role ARN values from the previous step into the corresponding fields.Click Confirm.
![]()