Next-Generation Firewall
Use Case: ACC—Path of Information Discovery
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Use Case: ACC—Path of Information Discovery
The ACC has a wealth of information that you can use
as a starting point for analyzing network traffic. Let’s look at
an example on using the ACC to uncover events of interest. This
example illustrates how you can use the ACC to ensure that legitimate
users can be held accountable for their actions, detect and track
unauthorized activity, and detect and diagnose compromised hosts
and vulnerable systems on your network.
The widgets and filters in the ACC give you the capability to
analyze the data and filter the views based on events of interest
or concern. You can trace events that pique your interest, directly
export a PDF of a tab, access the raw logs, and save a personalized
view of the activity that you want to track. These capabilities
make it possible for you to monitor activity and develop policies
and countermeasures for fortifying your network against malicious
activity. In this section, you will Interact with the ACC widgets
across different tabs, drill down using widget filters, and pivot the
ACC views using global filters, and export a PDF for sharing with
incidence response or IT teams.
At first glance, you see the Application Usage and User Activity
widgets in the ACCNetwork
Activity tab. The User Activity widget
shows that user Marsha Wirth has transferred 154 Megabytes of data
during the last hour. This volume is nearly six times more than
any other user on the network. To see the trend over the past few hours,
expand the Time period to the Last
6 Hrs, and now Marsha’s activity has been 1.7 Gigabytes
over 1,500 sessions and has triggered 455 threats signatures.
Because Marsha has transferred a large volume of data, apply
her username as a global filter (ACC Filters)
and pivot all the views in the ACC to Marsha’s traffic activity.

The Application Usage tab now shows that the top application
that Martha used was rapidshare, a Swiss-owned file-hosting site
that belongs to the file-sharing URL category. For further investigation,
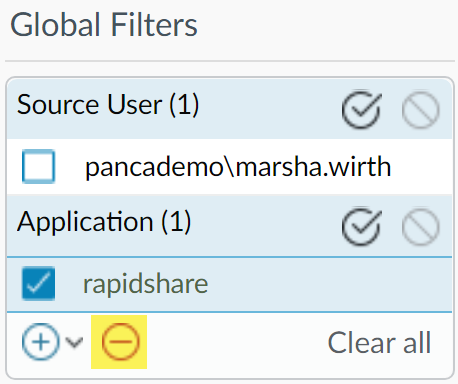
add rapidshare as a global filter, and view Marsha’s activity in
the context of rapidshare.
Consider whether you want to sanction rapidshare for company
use. Should you allow uploads to this site and do you need a QoS
policy to limit bandwidth?
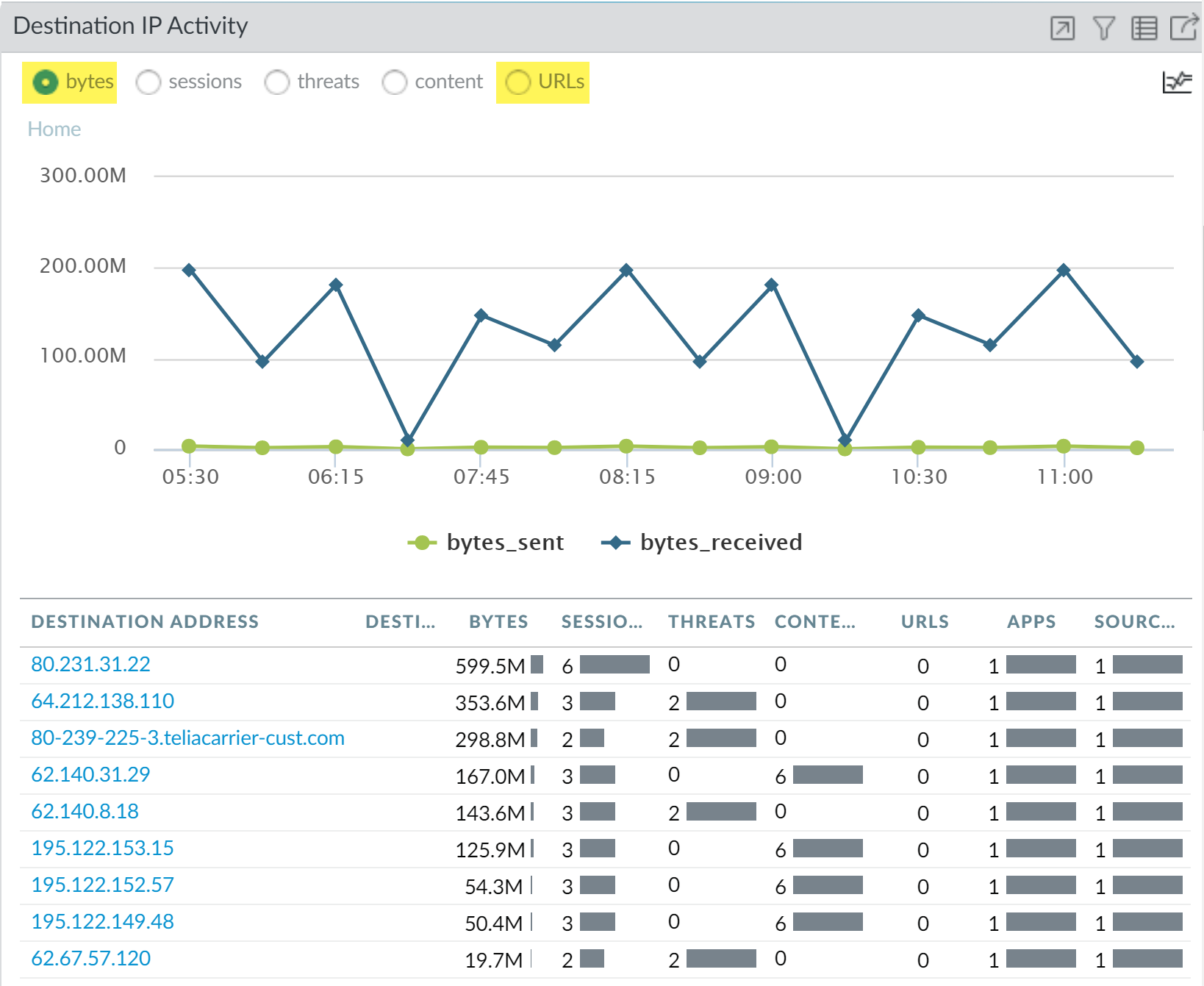
To view which IP addresses Marsha has communicated with, check
the Destination IP Activity widget, and view
the data by bytes and by URLs.
To find out which countries Marsha communicated with, sort on sessions in
the Destination Regions widget.

From this data, you can confirm that Marsha, a user on your network,
has established sessions in Canada, Germany, Sweden, United Kingdom,
and the United States. She logged 2 threats in her sessions with
each destination country.
To look at Marsha’s activity from a threat perspective, remove
the global filter for rapidshare.
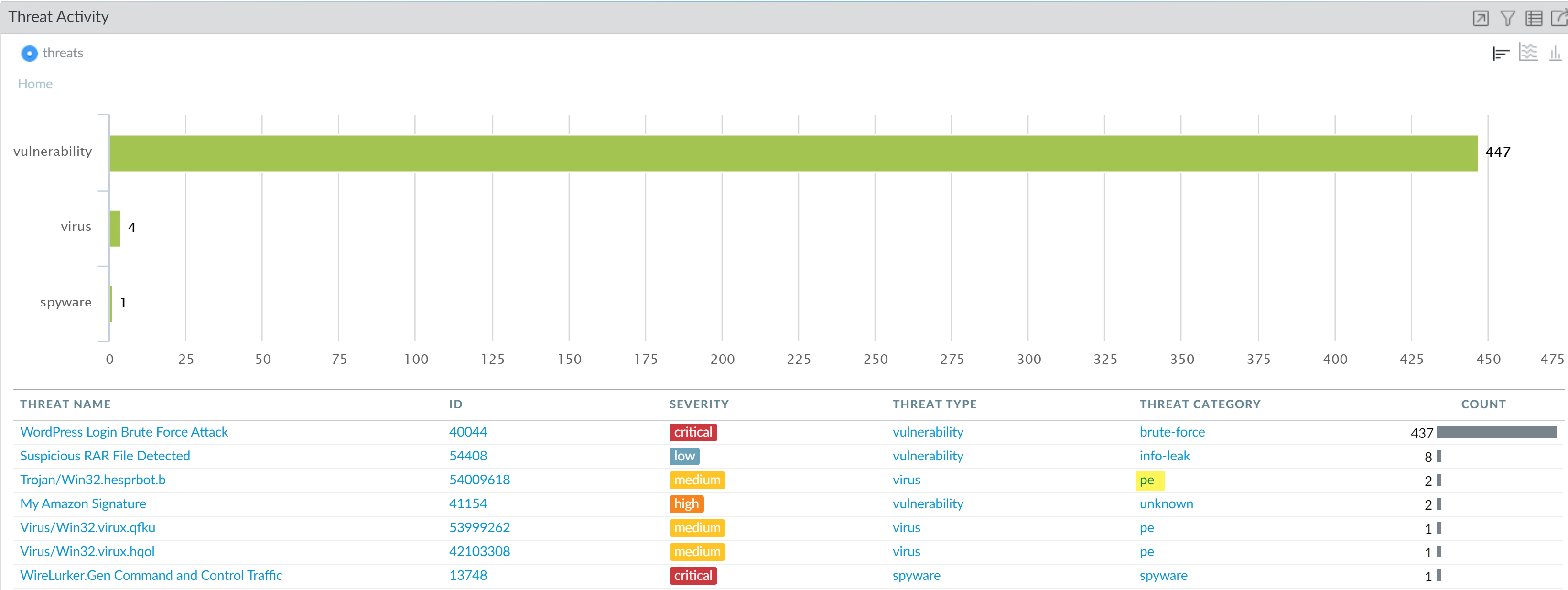
In the Threat Activity widget on the Threat
Activity tab, view the threats. The widget displays
that her activity had triggered a match for 452 vulnerabilities
in the brute force, information leak, portable executable (PE) and
spyware threat category. Several of these vulnerabilities are of
critical severity.
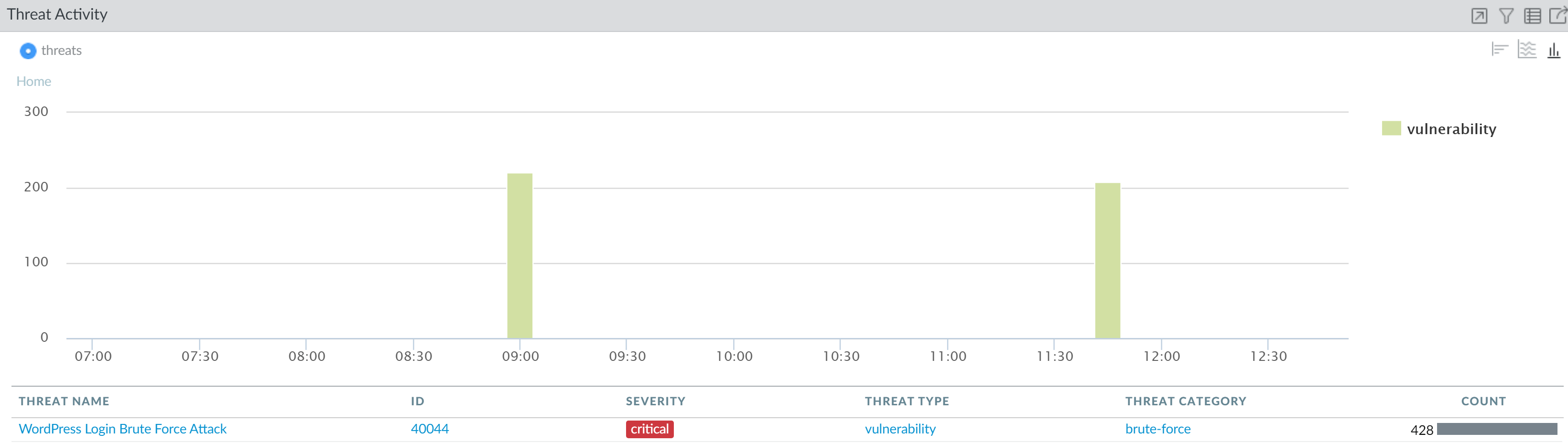
To further drill-down into each vulnerability, click into the
graph and narrow the scope of your investigation. Each click automatically
applies a local filter on the widget.
To investigate each threat by name, you can create a global filter
for say, WordPress Login Brute Force Attack.
Then, view the User Activity widget in the Network
Activity tab. The tab is automatically filtered to display
threat activity for Marsha (notice the global filters in the screenshot).

Notice that this Microsoft code-execution vulnerability was triggered
over email, by the imap application. You can now establish that
Martha has IE vulnerabilities and email attachment vulnerabilities,
and perhaps her computer needs to be patched. You can now either
navigate to the Blocked Threats widget in
the Blocked Activity tab to check how many
of these vulnerabilities were blocked.
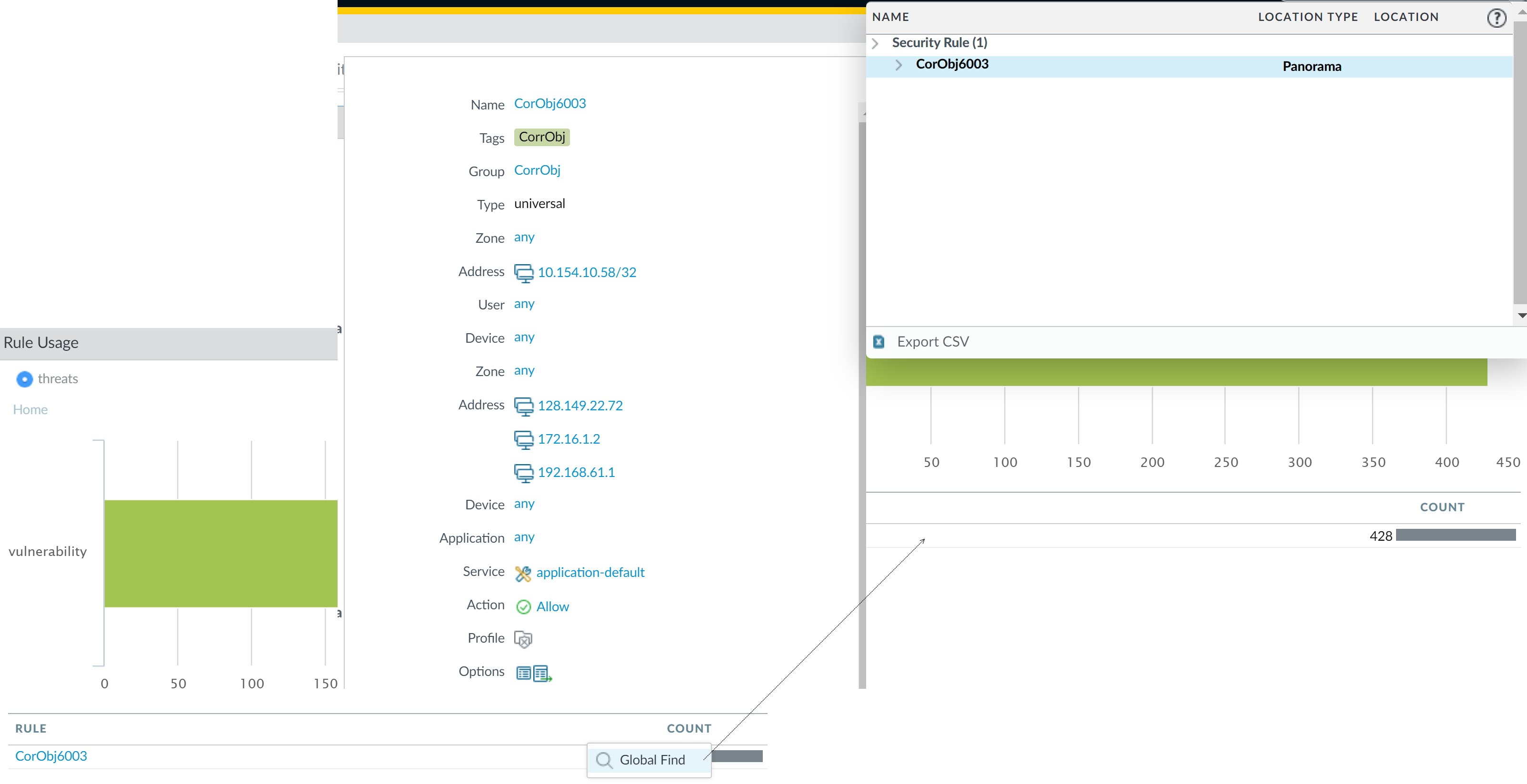
Or, you can check the Rule Usage widget
on the Network Activity tab to discover how
many vulnerabilities made it into your network and which security
rule allowed this traffic, and navigate directly to the security
rule using the Global Find capability.
Then, drill into the attackers using web-browsing to attack target
destination. Consider modifying the security policy rule to restrict
these malicious IP addresses or more narrowly defining which IP
addresses can access your network resources.
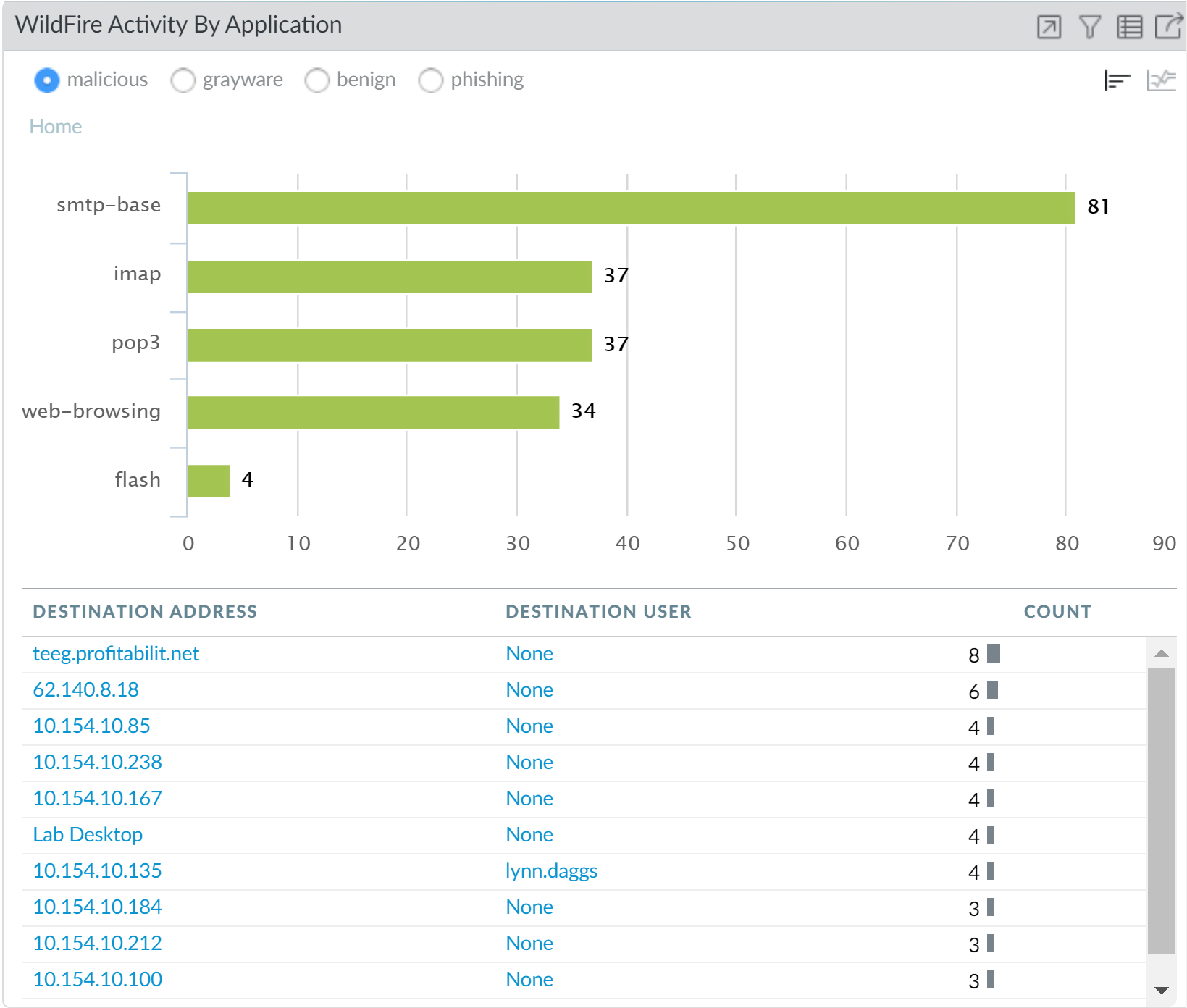
To review if any threats were logged over web-browsing, check
Marsha’s activity in the WildFire Activity by Application widget
in the Threat Activity tab. You can confirm
that Marsha had no malicious activity, but to verify that other
no other user was compromised by the web-browsing application, negate
Marsha as a global filter and look for other users who triggered
threats over web-browsing.

Click into the bar for imap in the graph and drill into the inbound
threats associated with the application. To find out who an IP address
is registered to, hover over the attacker IP address and select
the Who Is link in the drop-down.

Because the session count from this IP address is high, check
the Blocked Content and Blocked
Threats widgets in the Blocked Activity tab
for events related to this IP address. The Blocked Activity tab
allows you to validate whether or not your policy rules are effective
in blocking content or threats when a host on your network is compromised.
Use the Export PDF capability on the ACC
to export the current view (create a snapshot of the data) and send
it to an incidence response team. To view the threat logs directly
from the widget, you can also click the
![]() icon to jump to
the logs; the query is generated automatically and only the relevant
logs are displayed onscreen (for example in MonitorLogsThreat Logs).
icon to jump to
the logs; the query is generated automatically and only the relevant
logs are displayed onscreen (for example in MonitorLogsThreat Logs).
You have now used the ACC to review network data/trends to find
which applications or users are generating the most traffic, and
how many application are responsible for the threats seen on the
network. You were able to identify which application(s), user(s)
generated the traffic, determine whether the application was on
the default port, and which policy rule(s) allowed the traffic into
the network, and determine whether the threat is spreading laterally
on the network. You also identified the destination IP addresses,
geo-locations with which hosts on the network are communicating
with. Use the conclusions from your investigation to craft goal-oriented
policies that can secure users and your network.
