Next-Generation Firewall
Use Case 1: Firewall Requires DNS Resolution
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Use Case 1: Firewall Requires DNS Resolution
Configure DNS when the firewall needs DNS resolutions.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
In this use case, the firewall is the client
requesting DNS resolutions of FQDNs for Security policy rules, reporting,
management services (such as email, Kerberos, SNMP, syslog, and
more), and management events such as software update services, dynamic
software updates, and WildFire. In dynamic environments, FQDNs change
more frequently; accurate DNS resolutions allow the firewall to
enforce accurate policing, provide reporting and management services, and
handle management events. The shared, global DNS services perform
the DNS resolution for the management plane functions.
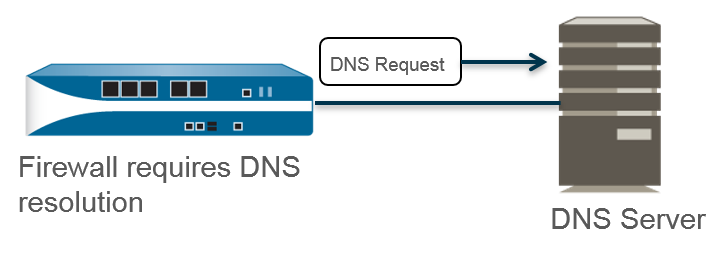
- Edit the Services settings (DeviceSetupServicesGlobal for firewalls that support multiple virtual systems; DeviceSetupServices for those that don’t).Configure the connection to DNS servers that can provide DNS resolutions.You must manually configure at least one DNS server on the firewall or it won’t be able to resolve hostnames; the firewall cannot use DNS server settings from another source, such as an ISP.
- On the Services tab, for DNS, select Servers and enter the Primary DNS Server address and Secondary DNS Server address.(PAN-OS 11.2.1 and later releases) (Optional) To configure encrypted DNS for server connections:
- Select one Encrypted DNS Connection Type
(other than None, which is the default
setting):
- DoH—DNS over HTTPS (Hypertext Transfer Protocol Secure). DoH uses port 443. When DoH is the connection type, a primary DNS address is required and the firewall sends all DNS requests to the primary DNS server using DoH. If no response arrives from the Primary DNS server, the firewall sends DoH requests to the secondary DNS server.
- DoT—DNS over TLS (Transport Layer Security). DoT uses port 853, which is dedicated to DoT traffic. When DoT is the connection type, a primary DNS address is required and the firewall sends all DNS requests to the primary DNS server using DoT. If no response arrives from the Primary DNS server, the firewall sends DoT requests to the secondary DNS server.
- None—Default setting. No encrypted DNS is specified for server connections.
- Select Fallback on Unencrypted DNS to have the firewall fall back to traditional DNS (cleartext) if the DNS server rejects encrypted DNS or times out (the firewall receives no response of the configured connection type [DoH or DoT] from the primary or secondary DNS server within the configured TCP timeout period).
- Enter the TCP Timeout (sec), range is 1 to 10; default is 1 second.
![]() Proceed to Step 4.As an alternative to specifying DNS Servers, you can configure a DNS Proxy Object if you want to configure advanced DNS functions such as split DNS, DNS proxy overrides, DNS proxy rules, static entries, or DNS inheritance. Beginning with PAN-OS 11.2.1, the DNS proxy supports encrypted DNS.
Proceed to Step 4.As an alternative to specifying DNS Servers, you can configure a DNS Proxy Object if you want to configure advanced DNS functions such as split DNS, DNS proxy overrides, DNS proxy rules, static entries, or DNS inheritance. Beginning with PAN-OS 11.2.1, the DNS proxy supports encrypted DNS.- On the Services tab, for DNS, select DNS Proxy Object.From the DNS Proxy list, select the DNS proxy that you want to use to configure global DNS services, or select DNS Proxy to configure a new DNS proxy object as follows:
- Enable and then enter a Name for the DNS proxy object.
- On firewalls that support multiple virtual systems, for Location, select Shared for global, firewall-wide DNS proxy services.Shared DNS proxy objects don’t use DNS server profiles because they don’t require a specific service route belonging to a tenant virtual system.
- Enter the Primary DNS server IP address. Optionally enter a Secondary DNS server IP address.
(PAN-OS 11.2.1 and later releases) (Optional) Configure the DNS proxy object with encrypted DNS.Select the Advanced tab. Ensure that Cache is enabled and Cache EDNS Responses is enabled (both are enabled by default).Click OK to save the DNS Proxy object.(Optional) Set a Minimum FQDN Refresh Time (sec) to limit how frequently the firewall refreshes FQDN cache entries.By default, the firewall refreshes each FQDN in its cache based on the individual TTL for the FQDN in a DNS record, as long as the TTL is greater than or equal to this minimum FQDN refresh setting (or as long as the TTL is greater than or equal to the default setting of 30 seconds if you don’t configure a minimum FQDN refresh time). To set a minimum FQDN refresh time, enter a value in seconds (range is 0 to 14,400; default is 30). A setting of 0 means the firewall refreshes FQDNs based on the TTL value in the DNS records; the firewall doesn’t enforce a minimum FQDN refresh time. The firewall uses the higher of the DNS TTL time and the minimum FQDN refresh time.If the TTL for the FQDN in DNS is short, but your FQDN resolutions don’t change as frequently as the TTL timeframe so don’t need a faster refresh, you should set a Minimum FQDN Refresh Time to avoid making FQDN refresh attempts more often than necessary.(Optional) Specify an FQDN Stale Entry Timeout (min), which is the number of minutes that the firewall continues to use stale FQDN resolutions in the event of an unreachable DNS server (range is 0 to 10,080; default is 1,440).A setting of 0 means the firewall does not continue to use a stale FQDN entry.Make sure the FQDN stale entry timeout is short enough not to allow incorrect traffic forwarding (which can pose a security risk), but long enough to allow traffic continuity without causing an unplanned network outage.Click OK and Commit.