Prisma Access
Set Up Prisma Access
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Set Up Prisma Access
Learn how to set up Prisma Access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Before you can use Prisma Access to secure your remote networks and mobile users,
configure an infrastructure subnet. Prisma Access uses IP addresses within this subnet
to establish a network between your remote network locations, mobile users, headquarters
and data center (if applicable). Prisma Access also uses service connections to access
internal resources from your headquarters or data center location.
This sub-network will be an extension to your existing network. Hence, it should not
overlap with any existing IP subnets in your network.
Carefully select the infrastructure subnet you use. Changing it
requires that you reach out to your Palo Alto Networks account representative, who will
contact the Site Reliability Engineering (SRE) team and submit a request for the change.
A maintenance window is required. Changing the infrastructure subnet without a
maintenance window can result in a Prisma Access outage and inconsistent feature
behavior.
The following example shows a 172.16.54.0/23 subnet that is being used for the Prisma Access infrastructure subnet.
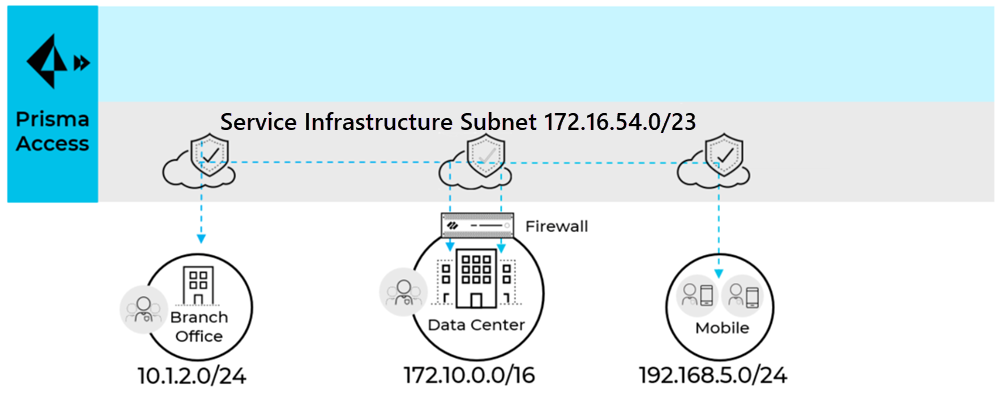
For small networks with less than 50 sites and 2500 mobile users, consider a /24 subnet.
For medium sized networks with less than 100 sites and less then 5000 mobile users,
consider a /23 subnet. In most cases a /23 subnet is sufficient. If there are more than
100 sites or 5000 mobile users or expected future growth, contact Palo Alto Networks to
evaluate whether you need a larger subnet size.
Learn how to set up Prisma Access.
Set Up Prisma Access (Strata Cloud Manager)
Learn how to set up your cloud service infrastructure for remote sites and mobile
users.
The following workflow provides you with the summary steps that you take
to install and configure Prisma Access.
- Launch Strata Cloud Manager through the hub.
- Launch an internet browser and Sign In to the hub.Launch Strata Cloud Manager.Specify trusted IP addresses for Prisma Access (Managed by Strata Cloud Manager) administrators.Only administrators that log in from these source IP addresses (and also that successfully authenticate) can access Prisma Access (Managed by Strata Cloud Manager). The IP addresses must be public addresses. By default, there aren’t any trusted addresses enforced (the list is set to any). To get started, find the Settings menu on the left navigation panel and click IP Restrictions.
![]() Identify your license requirements; then Activate and install the Prisma Access components.Enable the service infrastructure and service connections that allows communication between Prisma Access elements.Secure mobile users with GlobalProtect or Explicit Proxy, as required for your deployment.Plan, create, and configure remote network connections.(Optional) Change the authentication method from local authentication to your organization’s authentication method.(Optional) Forward logs from Strata Logging Service to an external Syslog receiver.(Optional) Check the status of Prisma Access.You can retrieve the status of all cloud services, including Prisma Access and Strata Logging Service, and a historical record of the service uptime by accessing the app instance from the hub.You can also sign up for email or text message notifications so that you are notified when infrastructure updates are planned; when updates occur; and when Palo Alto Networks® creates, updates, or resolves an incident. To sign up for email updates, go to the Resources section of the hub home page and then select Service Status. You can then Subscribe to specific updates and incidents for your cloud services.
Identify your license requirements; then Activate and install the Prisma Access components.Enable the service infrastructure and service connections that allows communication between Prisma Access elements.Secure mobile users with GlobalProtect or Explicit Proxy, as required for your deployment.Plan, create, and configure remote network connections.(Optional) Change the authentication method from local authentication to your organization’s authentication method.(Optional) Forward logs from Strata Logging Service to an external Syslog receiver.(Optional) Check the status of Prisma Access.You can retrieve the status of all cloud services, including Prisma Access and Strata Logging Service, and a historical record of the service uptime by accessing the app instance from the hub.You can also sign up for email or text message notifications so that you are notified when infrastructure updates are planned; when updates occur; and when Palo Alto Networks® creates, updates, or resolves an incident. To sign up for email updates, go to the Resources section of the hub home page and then select Service Status. You can then Subscribe to specific updates and incidents for your cloud services.Set Up Prisma Access (Panorama)
Provides quick steps to implement Prisma Access.The following workflow provides you with the summary steps that you take to install and configure Prisma Access (Managed by Panorama) Access.If you are setting up a deployment that includes multiple instances of Prisma Access on a single Panorama (multitenancy), see . Most organizations do not have a need to create and manage multiple tenants.- Add the following URLs and ports to an allow list on any security appliance that you use with the Panorama appliance that manages Prisma Access.In addition, if your Panorama appliance uses a (PanoramaSetupServiceProxy Server), or if you use SSL forward proxy with Prisma Access, be sure to add the following URLs and ports to an allow list on the proxy or proxy server.
- api.gpcloudservice.com (for Prisma Access)
- api.paloaltonetworks.com (for Prisma Access)
- apitrusted.paloaltonetworks.com (for Prisma Access)
If there is a Palo Alto Networks next-generation firewall between the Panorama appliance and the internet, you must add a security policy rule on the firewall to allow the paloalto-logging-service and paloalto-shared-services App-IDs from the Panorama appliance to the internet. These applications allow SSL-secured communication to Prisma Access and to Strata Logging Service that the Panorama appliance uses to query logs. If the Panorama appliance is behind a legacy Layer 4 firewall, permit ports 443 and 444 outbound from the Panorama to allow this traffic from the Panorama. Note that opening layer 4 ports instead of using Palo Alto Networks App-IDs is less secure and not recommended.Add the ports used by Panorama to allow lists in your network.Identify your license requirements; then Activate and install the Prisma Access components.Import your existing Panorama configuration to Prisma Access, or create new templates and device groups to begin configuration of Prisma Access.In order to push configuration—such as security policy, authentication policy, server profiles, security profiles, address objects, and application groups—to Prisma Access, you must either create new templates and device groups with the configuration settings you want to push to Prisma Access, or leverage your existing device groups and templates by adding them to the template stacks and device group hierarchies that Prisma Access creates when you onboard the service.Prisma Access creates the following templates and device groups, depending on what you have purchased (for example, if you do not purchase an Explicit Proxy license, you will not see the Explicit Proxy templates and device groups):- Templates:
- Explicit_Proxy_Template
- Explicit_Proxy_Template_Stack
- Mobile_User_Template
- Mobile_User_Template_Stack
- Remote_Network_Template
- Remote_Network_Template_Stack
- Service_Conn_Template
- Service_Conn_Template_Stack
- Device Groups:
- Explicit_Proxy_Device_Group
- Mobile_User_Device_Group
- Remote_Network_Device_Group
- Service_Conn_Device_Group
Configuration is simplified in Prisma Access because you do not have to configure any of the infrastructure settings, such as interfaces and routing protocols. This configuration is automated and pushed from Panorama in the templates and device groups that the service creates automatically. You can configure any infrastructure settings that are required by the service, such as settings required to create IPSec VPN tunnels to the IPSec-capable devices at your remote network locations, directly from the plugin. Optionally, you can add templates and device group hierarchies to the configuration to simplify the service setup.To simplify the service setup, create or import the templates and device groups you need before you begin the setup tasks for using Prisma Access.When creating templates and device groups for Prisma Access, you do not need to assign managed devices to it. Instead, you will add them to the template stacks and device group hierarchies that Prisma Access creates. Do not add any of the templates or device groups created by Prisma Access to any other template stacks or device groups.Sign up for email notifications using Strata Cloud Manager.Prisma Access provides you with notifications about the service, including any dataplane upgrades, using notifications from this app.Change the default master key for Panorama and in the Cloud Services plugin.Palo Alto Networks recommends changing the master key in Panorama and in the Cloud Services plugin as a security best practice and that you change the master key monthly.Because the Panorama and Prisma Access master keys do not synchronize, Palo Alto Networks recommends that you do not automatically rotate the master key in Panorama without also synchronizing the master key in Prisma Access. You can use the Panorama UI or API commands to change the master keys.Be sure to keep track of the master key you deploy because master keys cannot be recovered. When a master key expires, you must enter the current master key in order to configure a new master key. You must reset your Panorama appliance to factory default if you cannot provide the current master key when it expires.- Change the master key in Panorama.
- Select PanoramaMaster Key and Diagnostics.Do not specify a Current Master Key.
- Configure the New Master Key and Confirm Master Key.Make a note of the master key you configured.
- Configure the master key Lifetime and Time for Reminder.
- Click OK.
Change the master key for Prisma Access by selecting PanoramaCloud ServicesConfigurationService OperationsEdit master key, then entering the same master key you entered for Panorama.You can also change the master key by using API commands. This requires two steps–one to change the Panorama master key and one to change the Prisma Access master key. Use the following API commands to change the master key:- Panorama: XML APIOperational Commandsrequestmaster-key
- Prisma Access: XML APIOperational Commandsrequestpluginscloud_servicesprisma-accesssync
Enable the service infrastructure and service connections that allows communication between Prisma Access elements.- Plan to enable the service infrastructure and service connections.Enable the service infrastructure.Create a service connection to allow access to your corporate resources.If you don’t require access to your corporate resources, you should still create a service connection to enable access between mobile users and remote networks.Prisma Access Mobile User Deployments and secure mobile users with GlobalProtect or Explicit Proxy, as required for your deployment.To set up GlobalProtect on Prisma Access (Managed by Panorama):
- Configure zones for mobile users by creating two zones in the Mobile_User_Template (for example, Mobile-Users and Internet) and mapping the zones. You should map any zone that is not Prisma Access connected users or HQ or branch offices to Untrust.Under PanoramaCloud ServicesConfigurationMobile Users, map Internet to Untrust; Mobile-Users to Trust.
- Configure authentication.We recommend using local authentication as a first step to verify that the service is set up and your users have internet access. You can later switch to using your corporate authentication methods.
- Configure Security policies for the device group.To create a Security policy to allow traffic to the Internet, select the Mobile_User_Device_Group PoliciesSecurityPrerulesAdd a rule. For example: Mobile-Users to Internet.
- Commit and push your changes to get started with the service.Do not Commit to Panorama, as that only commits the changes locally to Panorama and does not push the changes to the Prisma Access infrastructure.
- Select PanoramaCloud ServicesStatusMonitorMobile Users to view the Status and verify that you can ping the Portal FQDN.
- Validate that Prisma Access is securing Internet traffic for mobile users by downloading and installing the GlobalProtect app, using the app to connect to the portal as a mobile user (local user), browsing to a few websites on the internet, and checking the traffic logs on Panorama.
To secure mobile users with an explicit proxy:- Read the Explicit Proxy Configuration Guidelines.
- Configure SAML Authentication. SAML authentication is required for Explicit Proxy.
- Set up Group Mapping using the Cloud Identity Engine.
- Complete the Explicit Proxy configuration.
- Commit and Push your changes.
Plan, create, and configure remote network connections.- Add one or more remote networks to Prisma Access.You can onboard one location and then add additional locations using the bulk import capability.Create a Security policy rule to allow traffic from the remote networks to HQ (For example: Trust to Trust).Validate the connectivity between the service connection, remote network connection, and mobile users.Run the API Script Used to Retrieve Prisma Access IP Addresses and Use the Legacy Script to Retrieve Mobile User IP Addresses.You add these addresses to an allow list on your organization’s network to limit inbound access to your enterprise network and applications.(Optional) Change the authentication method from local authentication to your organization’s authentication method.
- Create an authentication profile that meets your organization’s requirements (SAML, LDAP, RADIUS, etc).If your organization uses an on-premises authentication server such as RADIUS or Active Directory, add the IP addresses that Prisma Access uses as its source IP address for internal requests (Retrieve the IP Addresses for Prisma Access) to allow lists in your network, or allow the IP addresses of the entire Infrastructure Subnet (Prisma Access takes the loopback IP address from this subnet).Update the Authentication Profile for the Prisma Access portal and gateway to use this new authentication profile.(Optional) Forward logs from Strata Logging Service to an external Syslog receiver.