Prisma SD-WAN
Configure SASE Connectivity
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 5.6
- 6.1
- 6.2
- 6.3
- 6.4
- 6.5
- New Features Guide
- On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Configure SASE Connectivity
Learn how to configure SASE connectivity for connecting Prisma SD-WAN
sites with Prisma Access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Configure SASE connectivity to set parameters for connecting Prisma SD-WAN sites to Prisma Access.
This is a one-time activity.
- Select ManageResourcesSASE Connectivity.
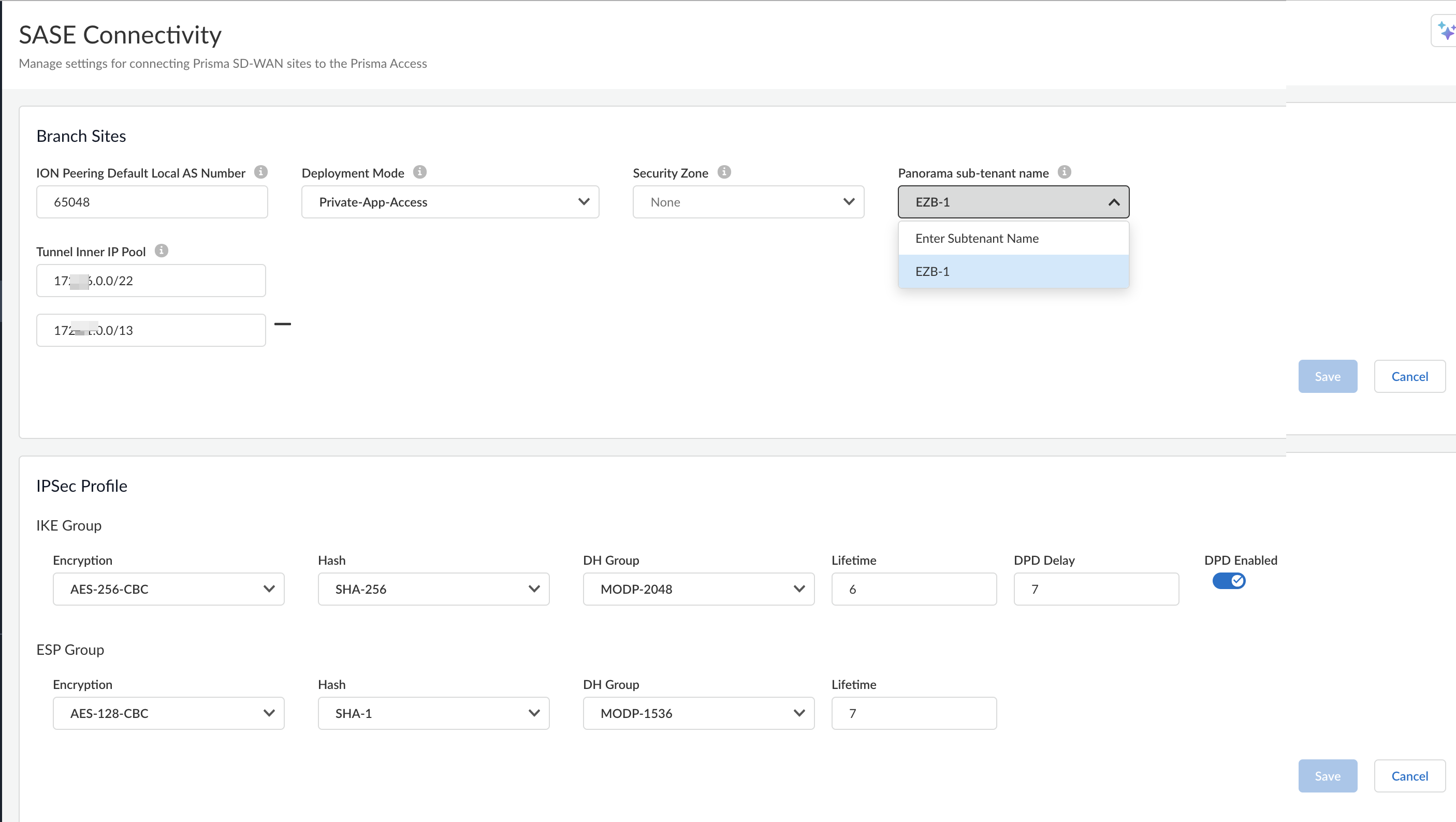
![]() Enter an ION Peering Default Local AS Number.The BGP Local AS number is defined to quickly on-board ECMP sites. This can be a 16-bit AS number, but private BGP AS number(s) are recommended.Select a Deployment Mode.The deployment mode supports the auto-configuration of BGP route-map settings for the following cases:
Enter an ION Peering Default Local AS Number.The BGP Local AS number is defined to quickly on-board ECMP sites. This can be a 16-bit AS number, but private BGP AS number(s) are recommended.Select a Deployment Mode.The deployment mode supports the auto-configuration of BGP route-map settings for the following cases:- Private-App-Access is the default setting which supports both Private App access and Internet.
- Internet-Only provides Internet only access by limiting route propagation inside Prisma Access with BGP no-advertise.
- Internet-Only-With-Mobile-User-Access provides Internet and Mobile User access by limiting route propagation out of Prisma Access with BGP no-export.
Changes to the Deployment Mode affect only new tunnels or tunnels that have been modified.Specify a Tunnel Inner IP Pool using IP/Mask notation.This IP Pool should be unused or unique across the entire network and should not be used by the Palo Alto Service Infrastructure Subnet.The number of tunnels that can be created in the Prisma SD-WAN Fabric to Prisma Access are directly limited by this configuration. Each tunnel will use a /31 subnet from this pool.(Optional) Select a Security Zone to bind the tunnel(s) created in the onboarding process to the selected zone.If you don’t select a Security Zone, the created tunnels will not be bound to a security zone.(Optional) Select a Panorama tenant from the Panorama sub-tenant name drop-down.You will see this field only if you have a Prisma Access Panorama-managed tenant.Click Save.(Optional) Update IPSec profiles for the tunnel(s) to Prisma Access.This synchronizes the IPSec profile between Prisma SD-WAN and Prisma Access.(Optional) To view additional information for SASE connectivity:- Select WorkflowsPrisma SD-WAN SetupBranch Sites and select a site.View details in the Prisma Access Connectivity section.
![]()