Enterprise DLP
Create Gmail Transport Rules
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create Gmail Transport Rules
Transport rules establish the actions Gmail takes based on the monitor, quarantine,
or block verdicts rendered by Enterprise Data Loss Prevention (E-DLP).
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Transport rules instruct Gmail to forward emails to Enterprise Data Loss Prevention (E-DLP) and
establish the actions Gmail takes based on the quarantine,or block verdicts rendered
by Enterprise DLP.
Create Gmail transport rules to forward emails from Gmail to the Enterprise DLP
for inspection to prevent exfiltration of sensitive data. Additionally, you must
create transport rules to specify the actions Gmail takes based on the verdicts
rendered by Enterprise DLP. The following transport rules are required:
- Email TransportRequired to forward all outbound emails from Gmail to the Enterprise DLP for inline email inspection and verdict rendering. The email transport rule is required in all cases regardless of the verdict Enterprise DLP renders.Enterprise DLP adds x-panw-inspected: true and x-panw-action: monitor to the email header for all forwarded and inspected emails. If an outbound email already includes these two headers, it will not be forwarded to Enterprise DLP again. If Enterprise DLP already inspected and rendered a verdict, Gmail automatically takes the action specified in the quarantine, or block transport rule.Enterprise DLP adds one of the following X-PANW-Processing-Status email headers based on the inspection status.
- X-PANW-Processing-Status: completed—Enterprise DLP successfully inspected the forwarded email.
- X-PANW-Processing-Status: limited—Enterprise DLP couldn't finish inspecting the forwarded email due to the Email DLP Max Timeout setting. This setting defines the amount of time allowed for Enterprise DLP to inspect the email.
- X-PANW-Processing-Status: failed—Enterprise DLP failed to inspect the forwarded email due to an error or unavailability of a dependent service. For example, the Enterprise DLP scanning service or Cloud Identity Engine being unavailable or returning an error.
These are informational headers designed to provide you with essential details regarding the Enterprise DLP inspection status and outcome for each forwarded email to facilitating better governance and operational transparency. If you write custom transport rules based on these headers, be sure they don't interfere with the transport rules required for Email DLP functionality. - QuarantineInstructs Gmail to quarantine and forward the email to the spam quarantine mailbox hosted by Gmail when Enterprise DLP returns a Quarantine verdict for an email that contains sensitive data. An email administrator must review and take action on quarantined emails after Enterprise DLP inspection.Enterprise DLP adds x-panw-action: quarantine to the email header for inspected emails if Enterprise DLP renders a Quarantine verdict. The email is transported back to Gmail and forwarded to the hosted quarantine spam inbox so an email administrator can review the email contents and decide whether to approve or block the email. Any future emails with this header already included will not be forwarded to Enterprise DLP again. Instead, Gmail will take the action specified in the quarantine transport rule.
- BlockInstructs Gmail on the action to take when Enterprise DLP returns a Block verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: block to the email header for all inspected emails. Any future emails with this header already included will not be forwarded to Enterprise DLP for inspection. Instead, Gmail takes the action specified in the Block transport rule.
- EncryptInstructs Gmail on the action to take when Enterprise DLP returns a Encrypt verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: encrypt to the email header for all inspected emails. Any future emails with this header already included will not be forwarded to Enterprise DLP for inspection. Instead, Gmail takes the action specified in the Encrypt transport rule.
(Custom Routing only) If using custom routing to forward
emails existing email infrastructure like Proofpoint or Mimecast, you must create
all the required Email DLP transport rules in the respective service's management
interface.
A transport rule isn't required for emails that match your Email DLP policy where the action is set to
Monitor. In this case, Enterprise DLP adds
x-panw-action - monitor to the email header, a
DLP incident is created, and the email continues to its
intended recipient.
Create a Gmail Email Transport Rule
Create a Gmail email transport rule to forward traffic to the Enterprise Data Loss Prevention (E-DLP) cloud service for inline email inspection.
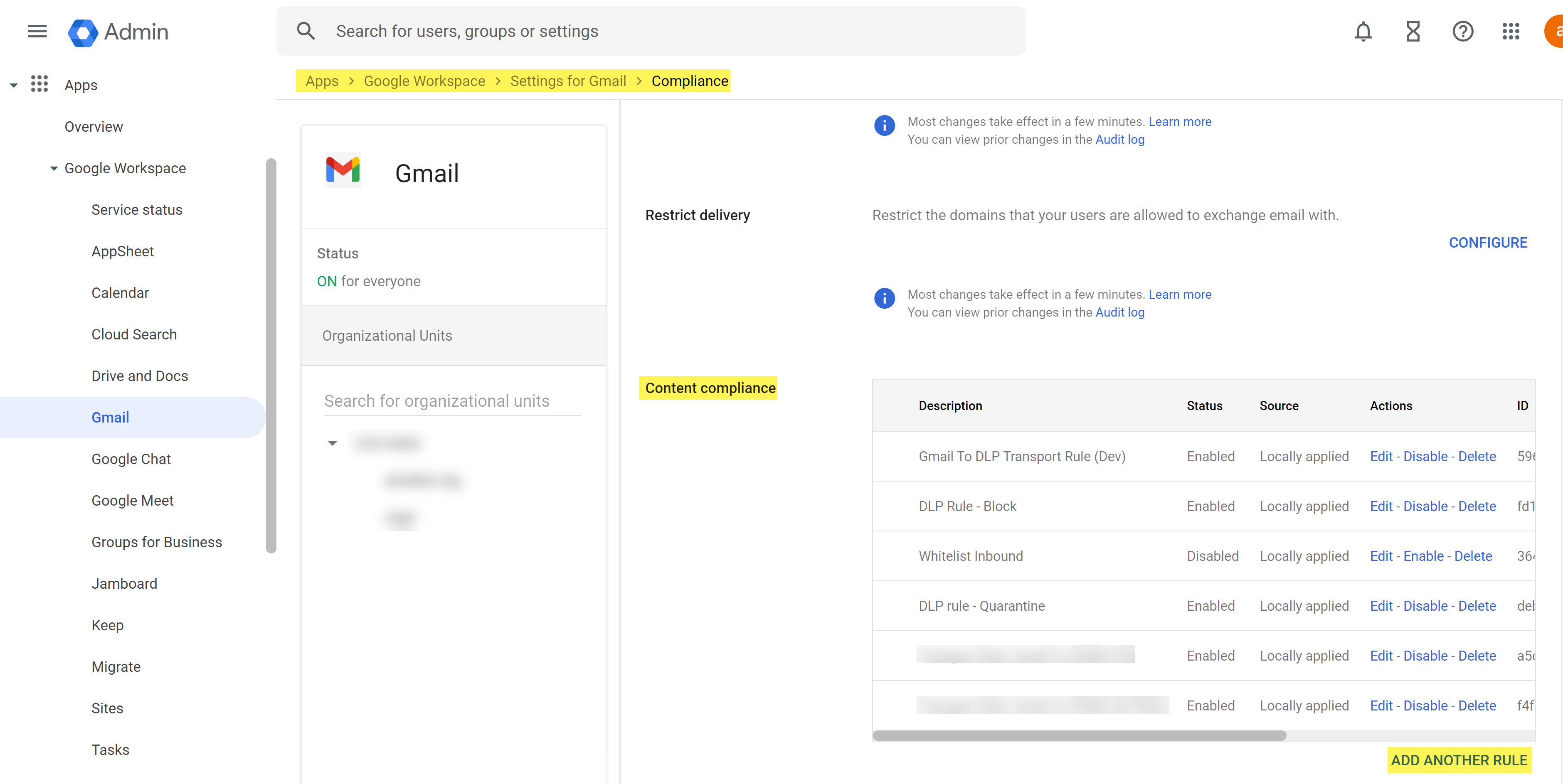
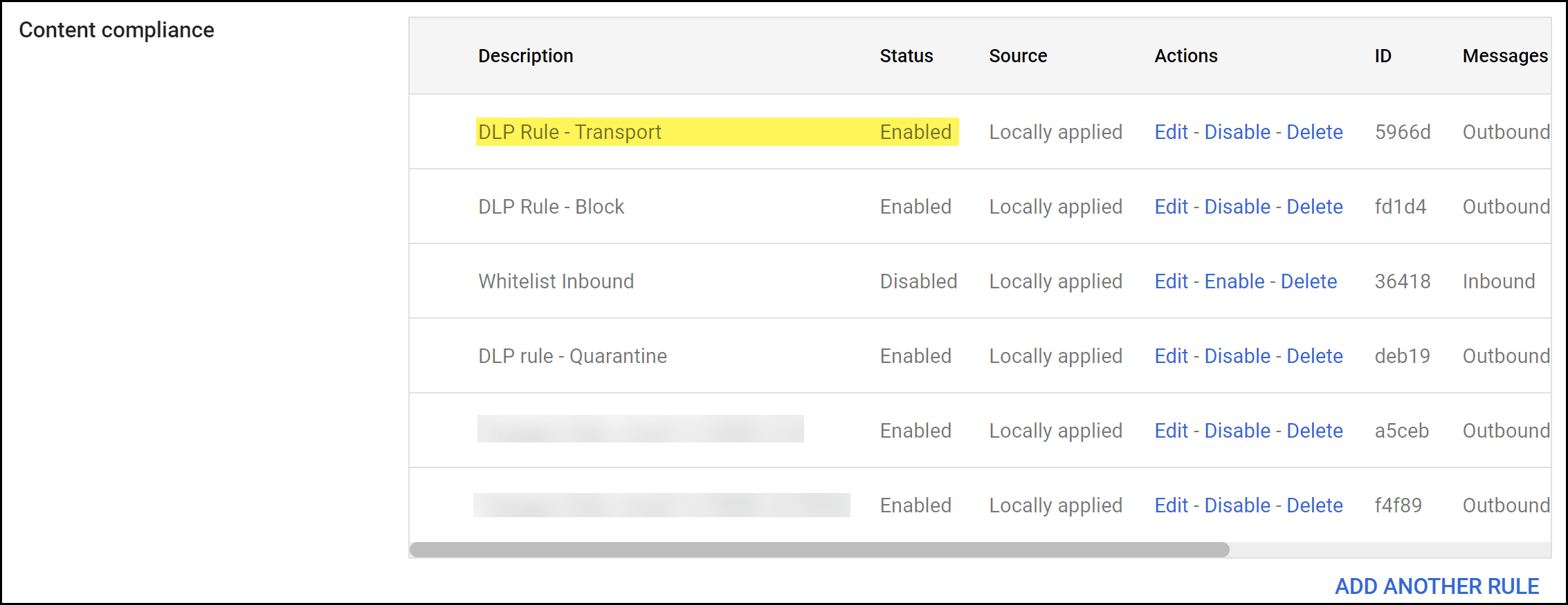
- Log in to the Google Admin portal.In the Dashboard, select AppsGoogle WorkspaceGmailCompliance.In the Content compliance section, Add Another Rule.
![]() Configure the email transport rule.
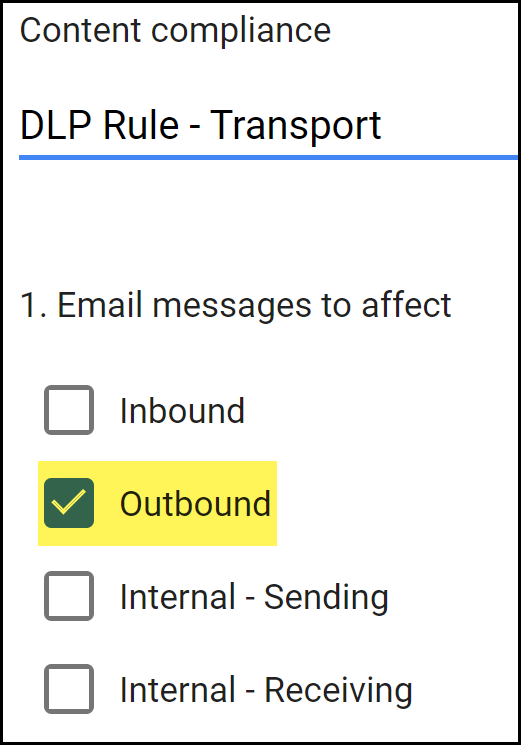
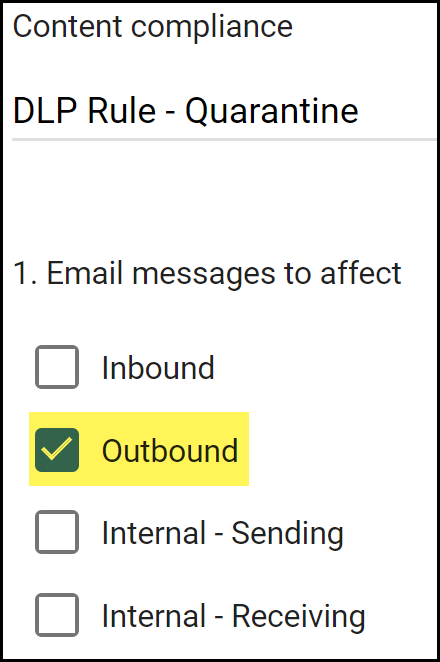
Configure the email transport rule.- In the Content compliance field, enter a descriptive name for the transport rule.For the Email messages to affect, select Outbound.This instructs Gmail to forward the email to Enterprise DLP before it leaves your network when the email recipient is outside your organization.
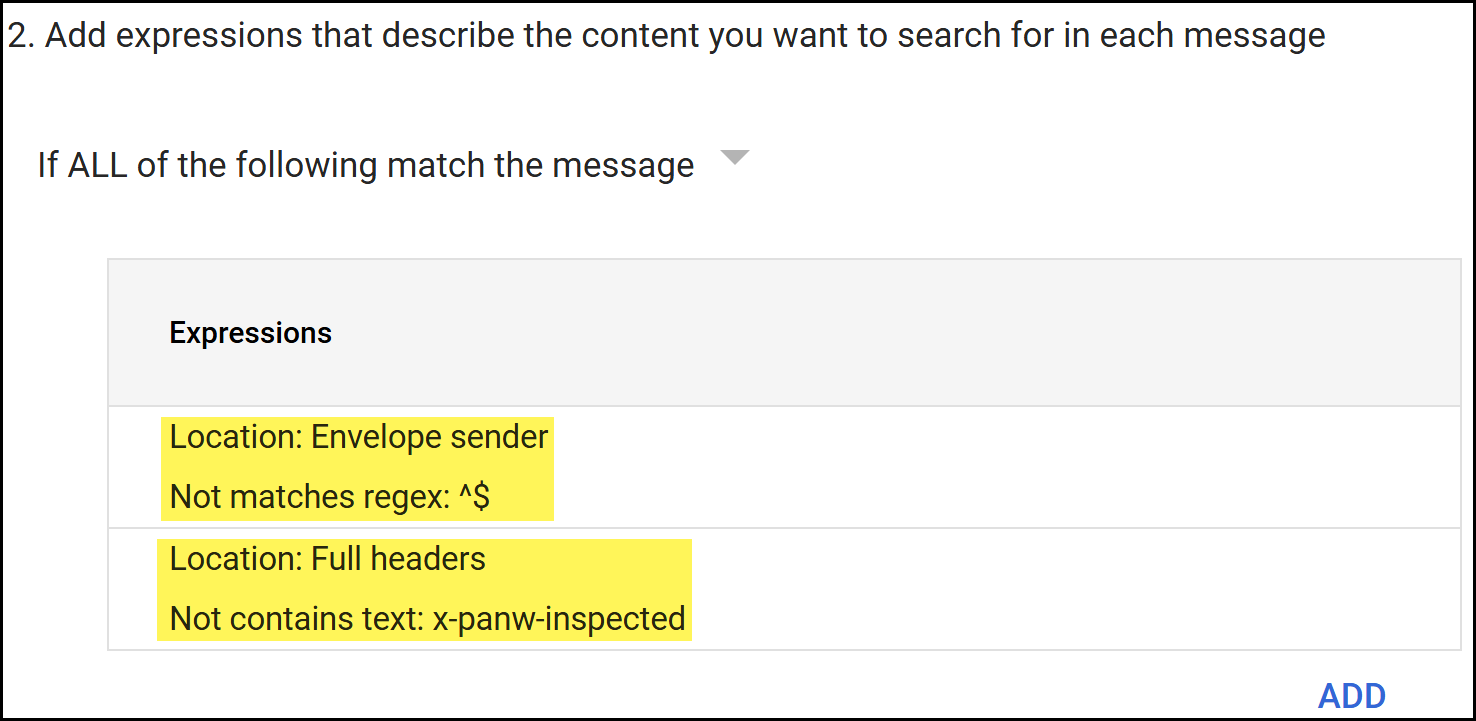
![]() Configure email forwarding to Enterprise DLP for emails that have not been inspected.
Configure email forwarding to Enterprise DLP for emails that have not been inspected.- In the Add experiences that describe the content you want to search for in each message section, select If ALL of the following match the message.
- Add a condition to forward emails that haven't been inspected by Enterprise DLP.
- In the Add setting page, select Advanced content match.
- For the Location, select Full Headers.
- For the Match type, select Not contains text.
- For the Content, enter x-panw-inspected.
Click Save to continue. - Add a condition to forward emails to Enterprise DLP when the sender is blank or empty.
- In the Add setting page, select Advanced content match.
- For the Location, select Envelope Sender.
- For the Match type, select Not matches regex.
- For the Regexp, enter ^$.
Click Save to continue. - Save.
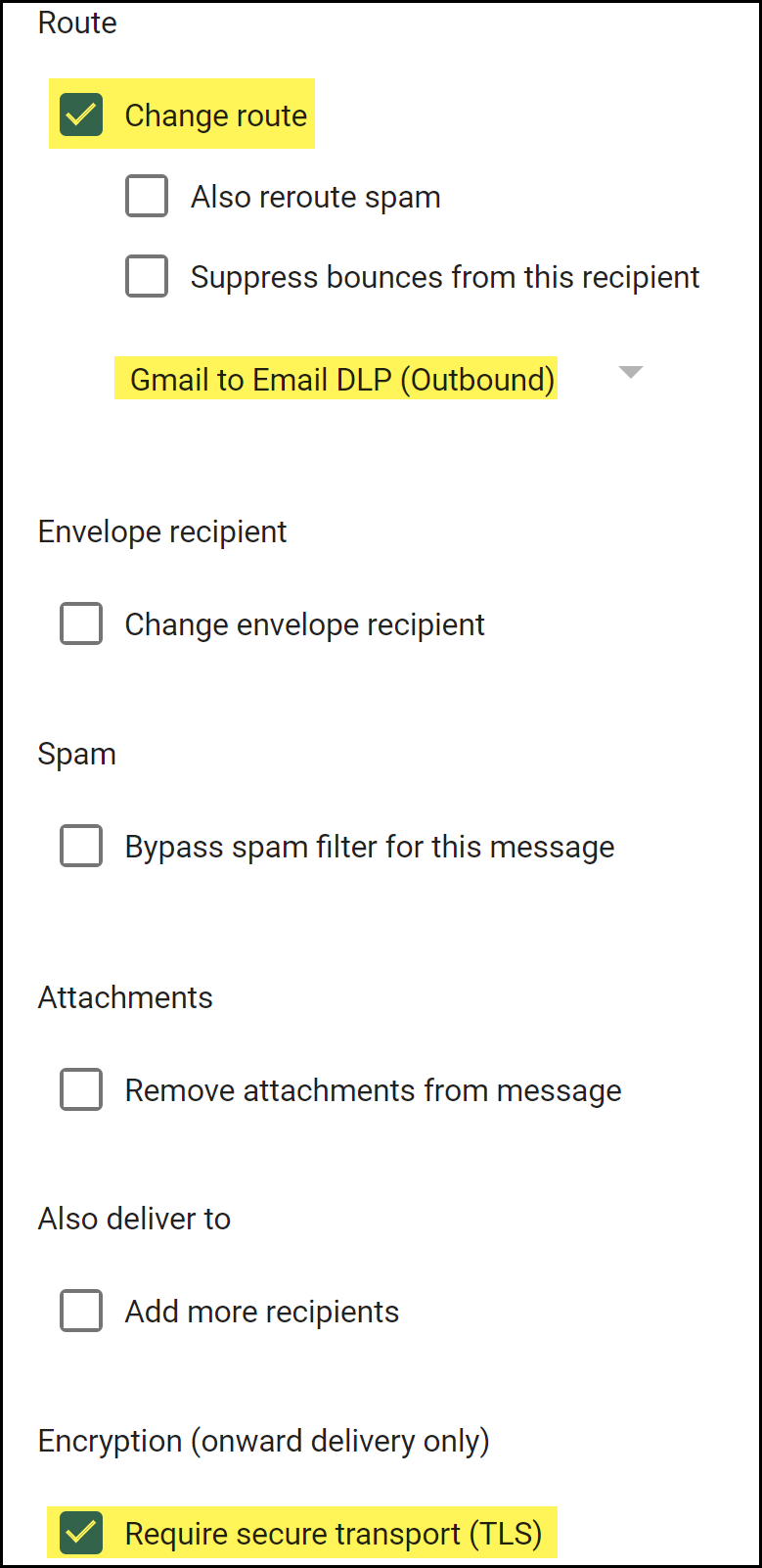
![]() Configure the action Gmail takes for emails that have already been inspected by Enterprise DLP, and the encryption settings.
Configure the action Gmail takes for emails that have already been inspected by Enterprise DLP, and the encryption settings.- In the If the above expressions match, do the following section, enable Change Route.
- Select the Email DLP Host you created.
- For the Encryption (onward delivery only), select Require secure transport (TLS).
![]() Configure the types of Gmail accounts the transport rule affects.
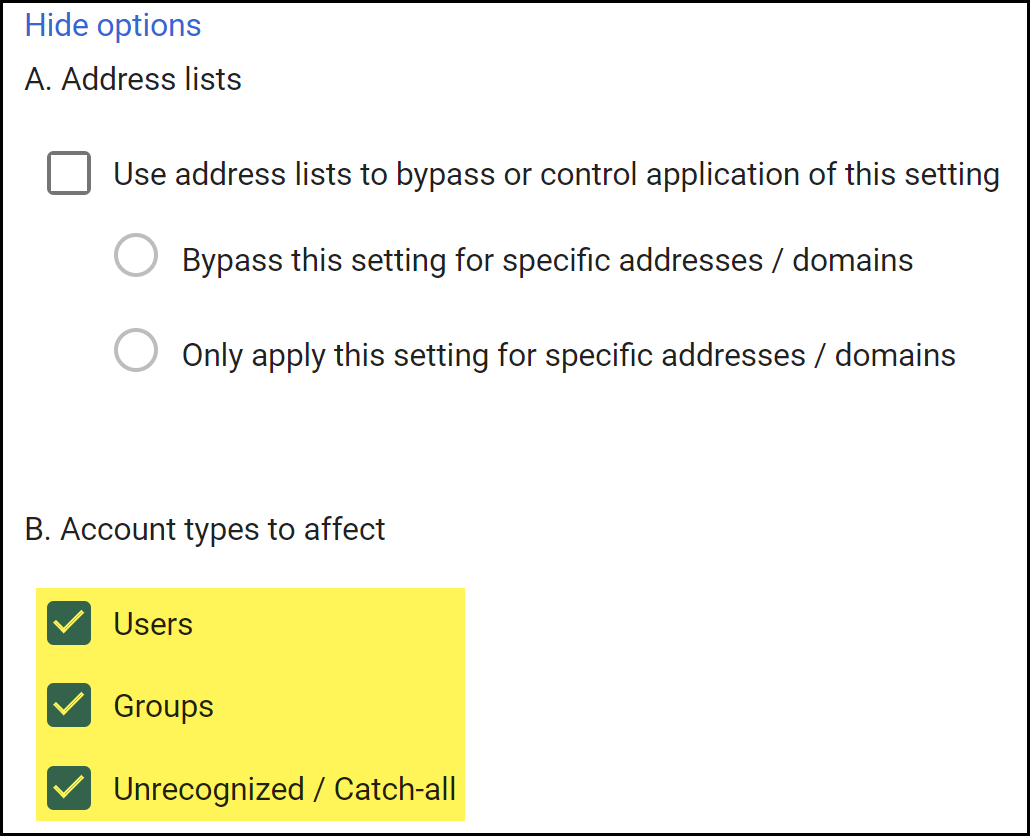
Configure the types of Gmail accounts the transport rule affects.- Show Options.After you expand the options menu, the button displays Hide Options.
- In the Account types to affect section, select Users, Groups, and Unrecognized / Catch-all.
![]() Save.Verify that the email transport rule was successfully added and that the Status is Enabled.
Save.Verify that the email transport rule was successfully added and that the Status is Enabled.![]()
Create a Gmail Quarantine Transport Rule
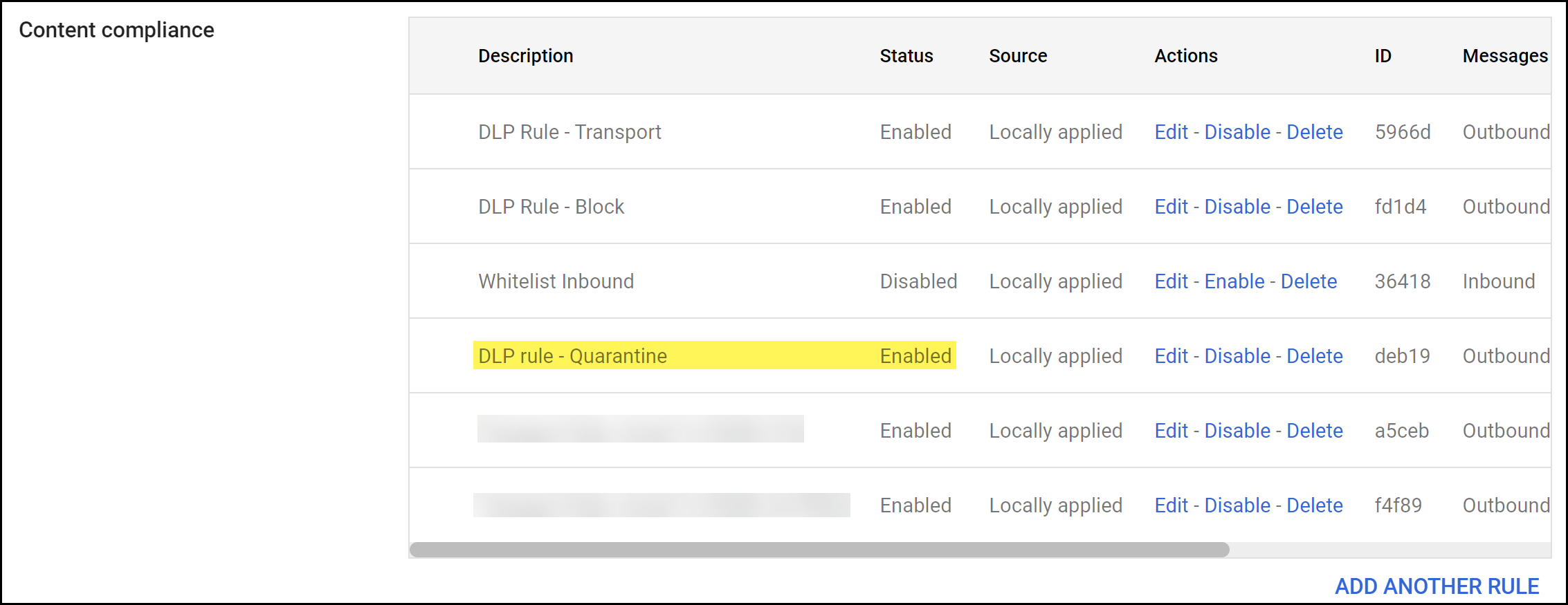
Create a Gmail quarantine transport rule to quarantine and forward a quarantined email to Gmail hosted quarantine for approval after inspection by Enterprise Data Loss Prevention (E-DLP).- Log in to the Google Admin portal.In the Dashboard, select AppsGoogle WorkspaceGmailCompliance.In the Content compliance section, Add Another Rule.
![]() Configure the quarantine transport rule.
Configure the quarantine transport rule.- In the Content compliance field, enter a descriptive name for the transport rule.For the Email messages to affect, select Outbound.This instructs Gmail to forward the email to Enterprise DLP before it leaves your network when the email recipient is outside your organization.
![]() Configure email forwarding to Enterprise DLP for emails that have not been inspected.
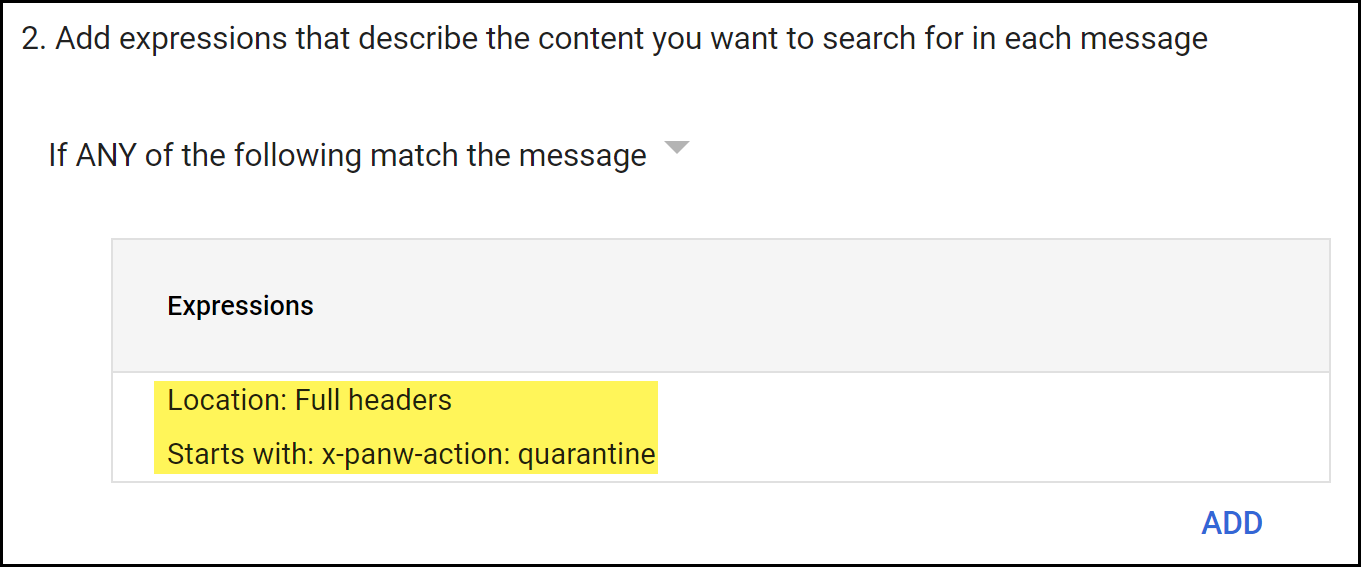
Configure email forwarding to Enterprise DLP for emails that have not been inspected.- In the Add experiences that describe the content you want to search for in each message section, select If ANY of the following match the message.
- Add.
- In the Add setting page, select Advanced content match.
- For the Location, select Full Headers.
- For the Match type, select Starts with.
- For the Content, enter x-panw-action: quarantine.
- Save.
![]() Configure the action Gmail takes for emails that need to be quarantined.
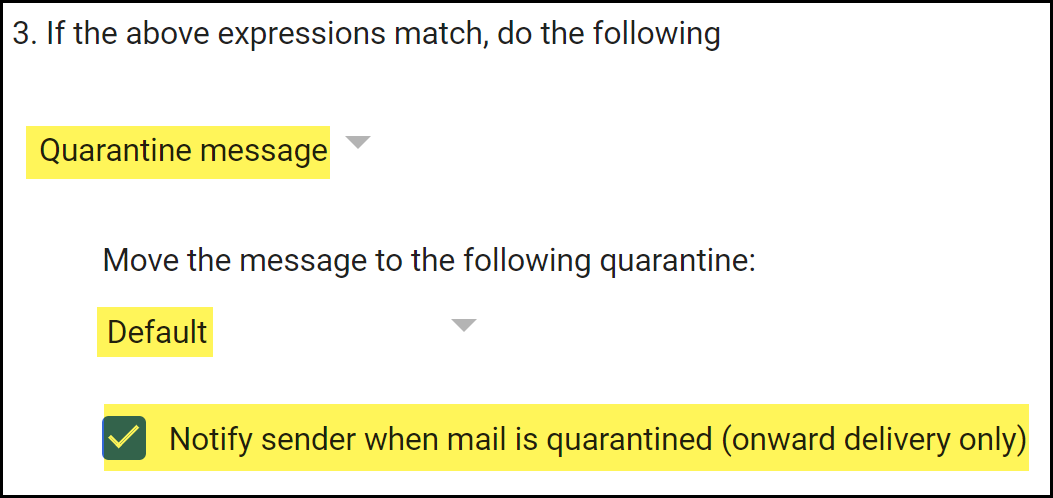
Configure the action Gmail takes for emails that need to be quarantined.- In the If the above expressions match, do the following section, select Quarantine message.
- In the Move the message to the following quarantine, select the Gmail quarantine inbox you want to forward emails that need to be reviewed by an email administrator.
- Enable Notify sender when email is quarantined (onward delivery only).
![]() Configure the types of Gmail accounts the transport rule affects.
Configure the types of Gmail accounts the transport rule affects.- Show Options.After you expand the options menu, the button displays Hide Options.
- In the Account types to affect section, select Users, Groups, and Unrecognized / Catch-all.
![]() Save.Verify that the email transport rule was successfully added and that the Status is Enabled.
Save.Verify that the email transport rule was successfully added and that the Status is Enabled.![]() An email administrator must review and allow or reject quarantined emails forwarded to the quarantine mailbox.Due to a Gmail limitation, SaaS Security generates two Email DLP logs (ConfigurationSaaS SecurityData SecurityLogsEmail DLP Logs) when a quarantined email is allowed. The first Email DLP log describes the initial outbound email blocked by Email DLP. The second Email DLP log describes the allowed outbound email that is sent back to Enterprise DLP to add x-panw-inspected: true and x-panw-action: monitor to the email header before it continues on its path to the intended recipient.
An email administrator must review and allow or reject quarantined emails forwarded to the quarantine mailbox.Due to a Gmail limitation, SaaS Security generates two Email DLP logs (ConfigurationSaaS SecurityData SecurityLogsEmail DLP Logs) when a quarantined email is allowed. The first Email DLP log describes the initial outbound email blocked by Email DLP. The second Email DLP log describes the allowed outbound email that is sent back to Enterprise DLP to add x-panw-inspected: true and x-panw-action: monitor to the email header before it continues on its path to the intended recipient.Create a Gmail Block Transport Rule
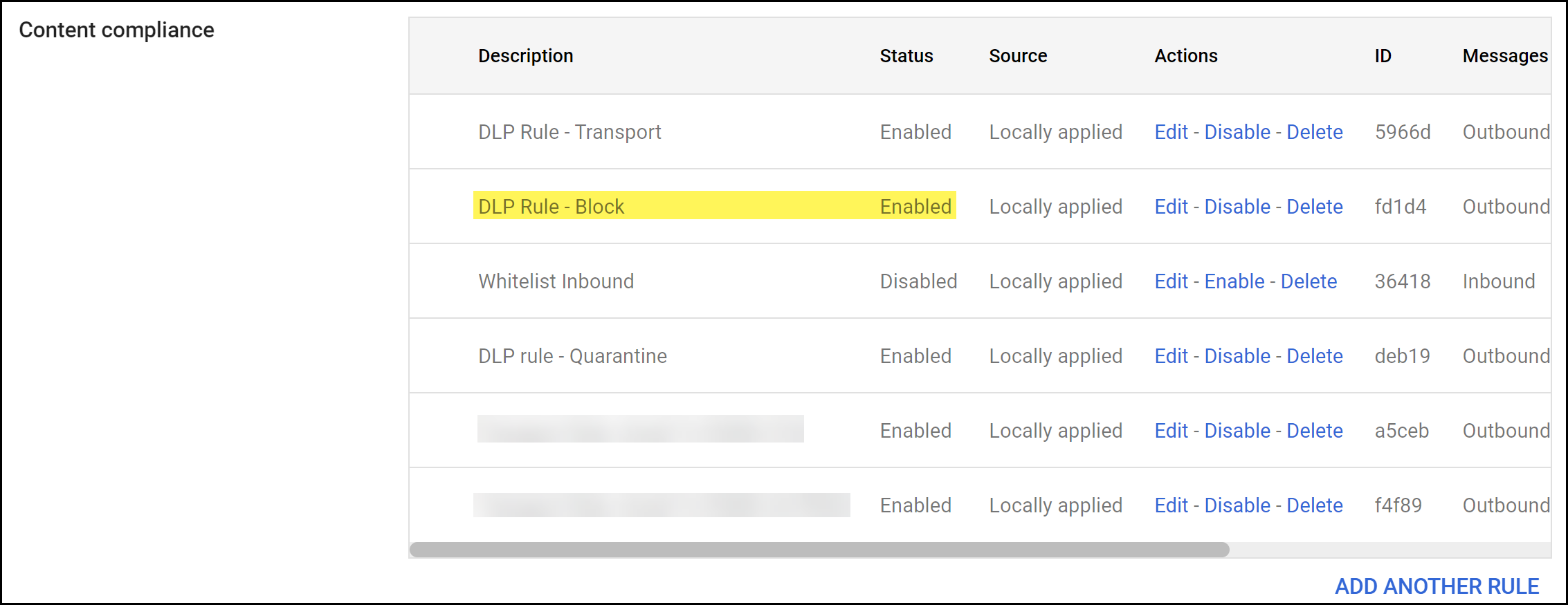
Create a Gmail block transport rule to specify the action Gmail takes when an email contains sensitive data and is blocked.- Log in to the Google Admin portal.In the Dashboard, select AppsGoogle WorkspaceGmailCompliance.In the Content compliance section, Add Another Rule.
![]() Configure the email transport rule.
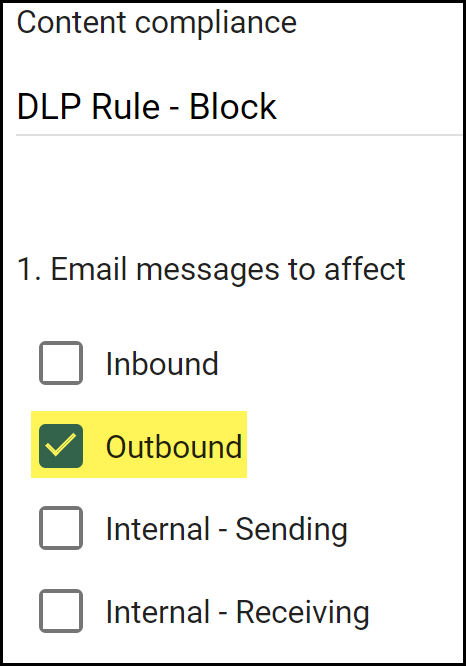
Configure the email transport rule.- In the Content compliance field, enter a descriptive name for the transport rule.For the Email messages to affect, select Outbound.This instructs Gmail to forward the email to Enterprise DLP before it leaves your network when the email recipient is outside your organization.
![]() Configure email forwarding to Enterprise DLP for emails that have not been inspected.
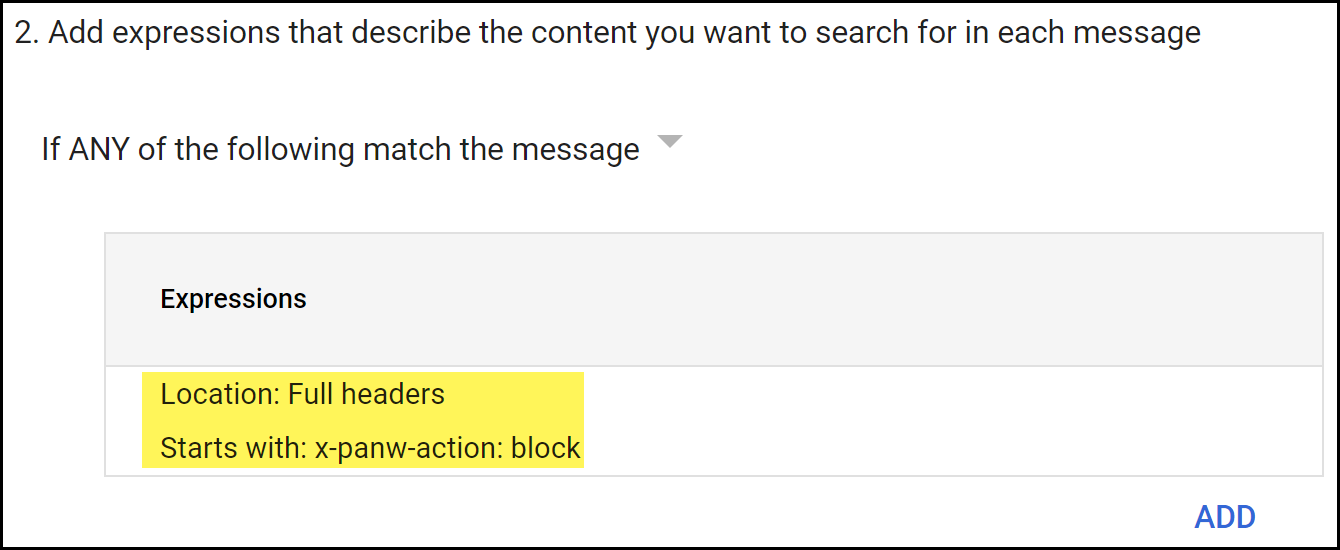
Configure email forwarding to Enterprise DLP for emails that have not been inspected.- In the Add experiences that describe the content you want to search for in each message section, select If ANY of the following match the message.
- Add.
- In the Add setting page, select Advanced content match.
- For the Location, select Full Headers.
- For the Match type, select Starts with.
- For the Content, enter x-panw-action: block.
- Save.
![]() Configure the action Gmail takes for emails that are blocked.
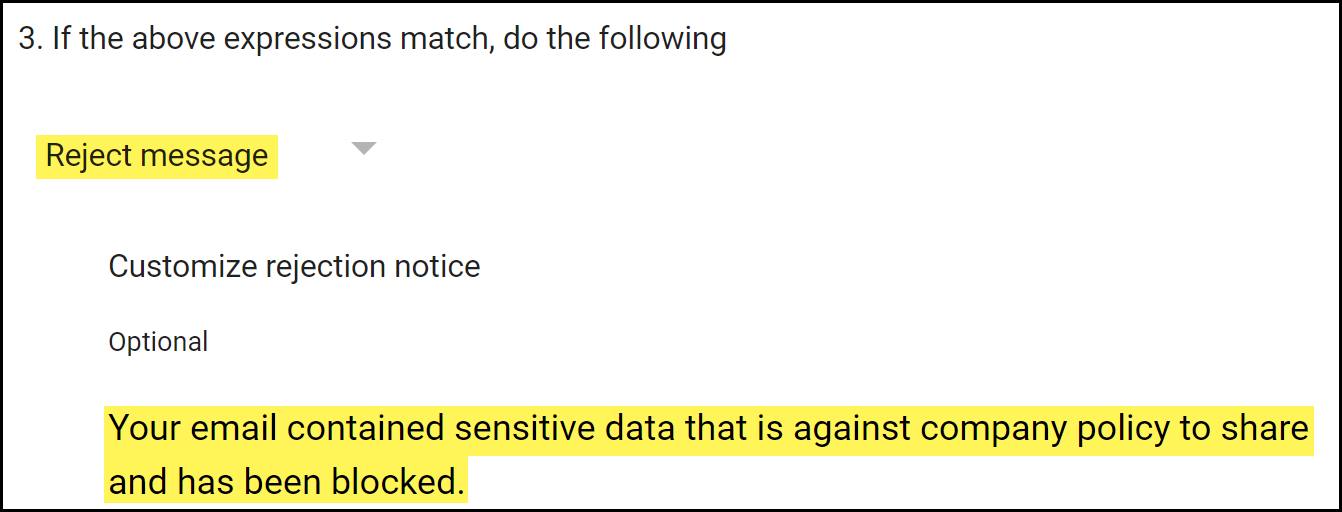
Configure the action Gmail takes for emails that are blocked.- In the If the above expressions match, do the following section, select Reject message.
- (Optional) Enter a customized rejection notice when an email is blocked.
![]() Configure the types of Gmail accounts the transport rule affects.
Configure the types of Gmail accounts the transport rule affects.- Show Options.After you expand the options menu, the button displays Hide Options.
- In the Account types to affect section, select Users, Groups, and Unrecognized / Catch-all.
![]() Save.Verify that the email transport rule was successfully added and that the Status is Enabled.
Save.Verify that the email transport rule was successfully added and that the Status is Enabled.![]()
Create a Gmail Encrypt Transport Rule
Create a Gmail encrypt transport rule to specify the action Gmail takes when an email contains sensitive data and needs to be encrypted before being sent to the recipient.- Log in to the Google Admin portal.In the Dashboard, select AppsGoogle WorkspaceGmailCompliance.In the Content compliance section, Add Another Rule.
![]() Configure the email transport rule.
Configure the email transport rule.- In the Content compliance field, enter a descriptive name for the transport rule.For the Email messages to affect, select Outbound.This instructs Gmail to forward the email to Enterprise DLP before it leaves your network when the email recipient is outside your organization.
![]() Configure email forwarding to Enterprise DLP for emails that have not been inspected.
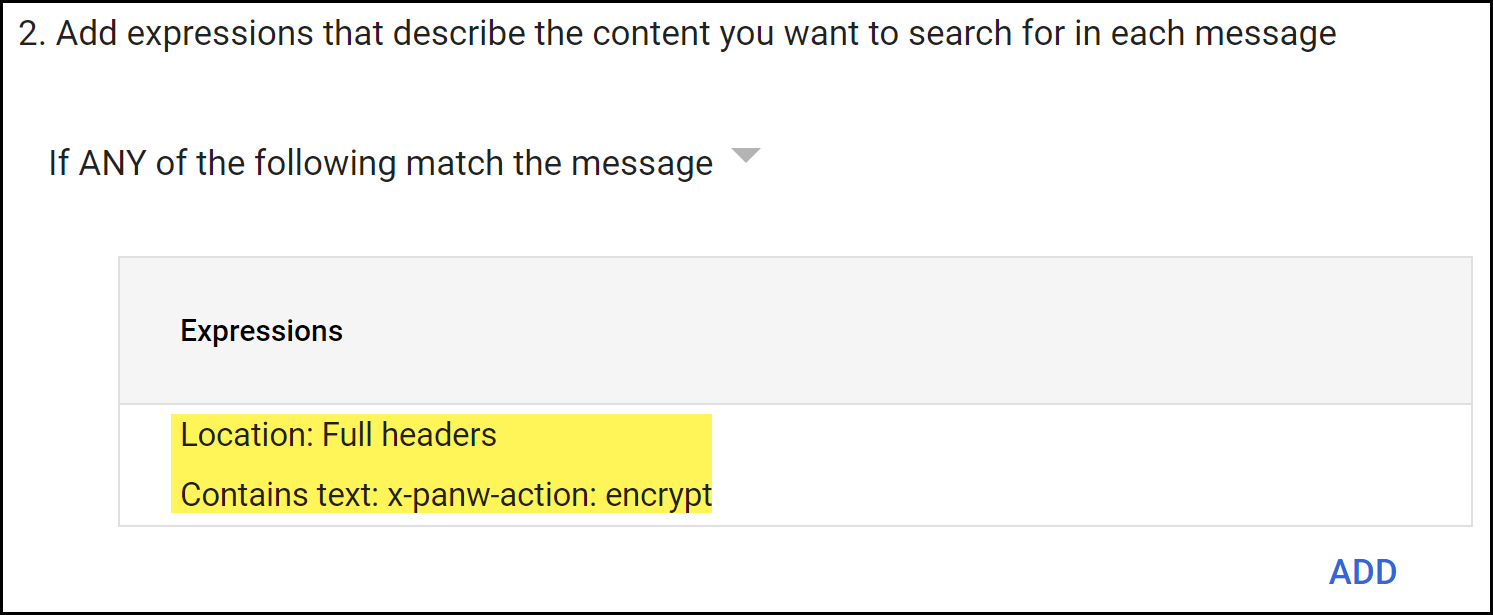
Configure email forwarding to Enterprise DLP for emails that have not been inspected.- In the Add experiences that describe the content you want to search for in each message section, select If ANY of the following match the message.
- Add.
- In the Add setting page, select Advanced content match.
- For the Location, select Full Headers.
- For the Match type, select Contains text.
- For the Content, enter x-panw-action: encrypt.
- Save.
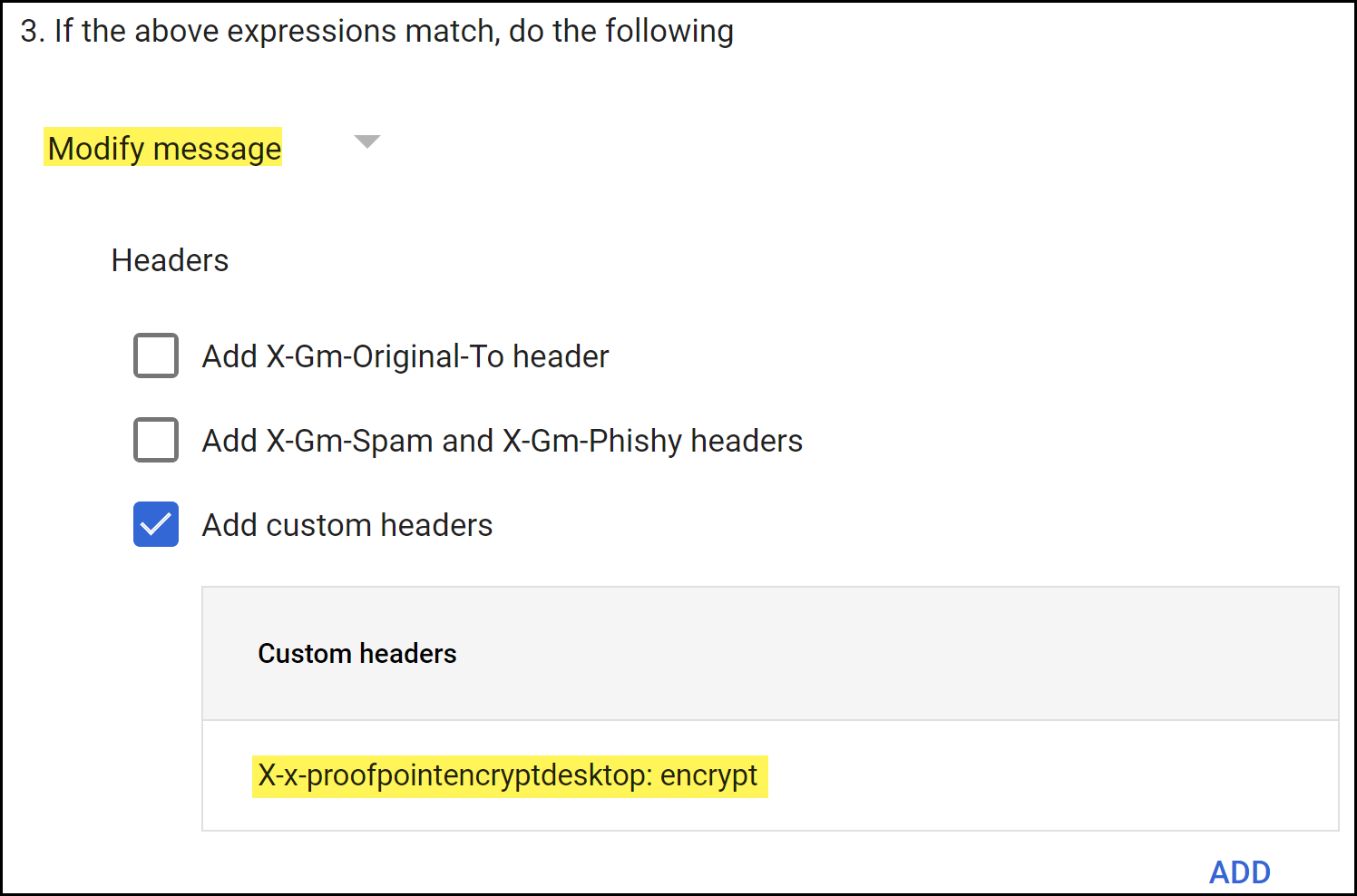
![]() Configure the action Gmail takes for encrypted emails.
Configure the action Gmail takes for encrypted emails.- In the If the above expressions match, do the following section, select Modify message.
- For the Subject, select Modify message.
- For the Headers, select Add customer headers
- Add the custom message header.
- For the Header key, enter x-proof-pointencryptdesktop.
- For the Header value, enter encrypt.
Save to continue.
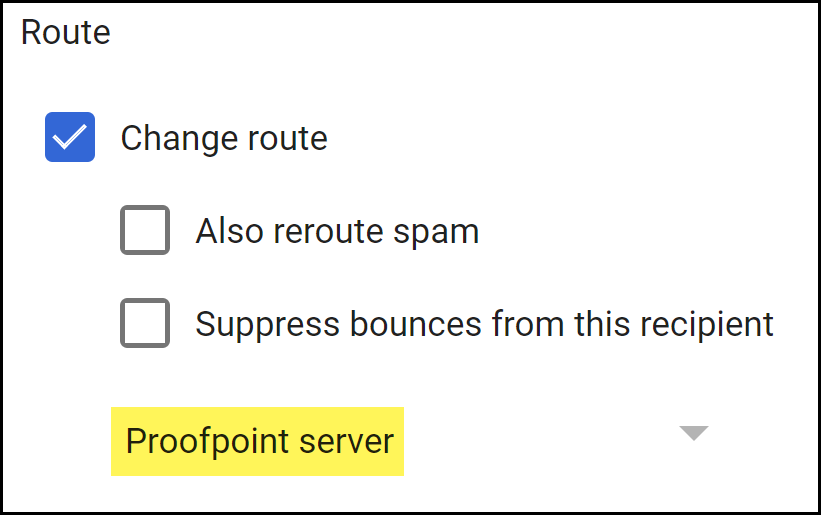
![]() Configure the route to forward emails to your Proofpoint server for encryption.
Configure the route to forward emails to your Proofpoint server for encryption.- In the Route section, select Change route.
- Select the Proofpoint server route you created.
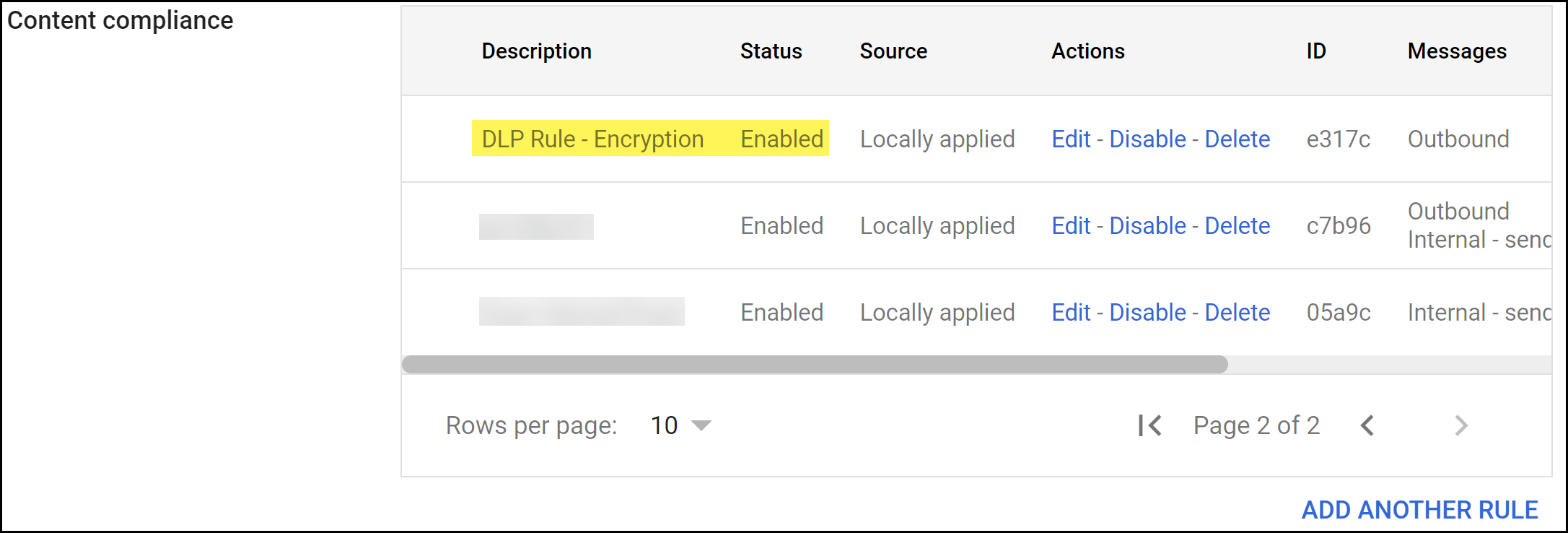
![]() Save.Verify that the email transport rule was successfully added and that the Status is Enabled.
Save.Verify that the email transport rule was successfully added and that the Status is Enabled.![]()