Enterprise DLP
Panorama
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Panorama
Create a security policy rule to prevent exfiltration of sensitive data to ChatGPT on
the Panorama® management server.
- Upgrade Panorama, managed firewalls, and the Enterprise DLP plugin to the minimum required versions.
- Upgrade to PAN-OS 10.2.3 or later release.Upgrade the plugin to 3.0.2 or later release.Upgrade managed firewalls to PAN-OS 10.2.3 or later release.Log in to the Panorama web interface.Create the decryption policy rule required for Enterprise DLP.
- Select ObjectsDecryptionDecryption Profile and specify the Device Group.Add a new decryption profile. The default decryption profile configuration is all that is required for Enterprise DLP to inspect traffic.Do not enable Strip ALPN in the decryption profile. Enterprise DLP cannot inspect egress traffic to ChatGPT if you remove application-layer protocol negotiation (ALPN) headers from decrypted traffic.Select PoliciesDecryption and specify the Device Group.Add a new decryption policy rule. Select Options and assign the decryption profile.
- For the Action, select Decrypt.
- Select the Decryption Profile you created.
- Click OK.
Enable Non-File Inspection.Data filtering profiles configured for non-file detection are required to prevent exfiltration of sensitive data to ChatGPT. You can create a new data filtering profile or use existing data filtering profiles as needed. You can add any combination of custom or predefined data patterns to define the match criteria.Create a data profile on Panorama or Strata Cloud Manager, or use an existing data profile.Attach the data filtering profile to a Security policy rule.- Select PoliciesSecurity.You can select an existing Security policy rule or Add a new Security policy rule.Configure the General and Source as needed.Configure the Destination as needed.For the Application, Add and search for openai-chatgpt.Skip this step if your Security policy rule applies to Any application. ChatGPT is automatically included for a Security policy rule that applies to Any application.Select Actions and configure the Profile Settings.Select Profiles and select the Data Filtering profile you created in the previous step.If the data filtering profile is part of a Security Profile Group (ObjectsSecurity Profile Groups), select Group and select the Security Profile Group the data filtering profile is associated with.Configure the rest of the Security policy rule as needed.The Action you specify in the data filtering profile determines whether egress traffic to ChatGPT is blocked. The Security policy rule Action does not impact whether matched traffic is blocked.For example, if you configured the data filtering profile to Block matching egress traffic but configure the Security policy rule Action to Allow, the matching egress traffic to ChatGPT will be blocked.Click OK.Commit and push the new configuration to your managed firewalls to complete the Enterprise DLP plugin installation.This step is required for Enterprise DLP data filtering profile names to appear in Data Filtering logs.The Commit and Push command isn’t recommended for Enterprise DLP configuration changes. Using the Commit and Push command requires the additional and unnecessary overheard of manually selecting the impacted templates and managed firewalls in the Push Scope Selection.
- Full configuration push from Panorama
- Select CommitCommit to Panorama and Commit.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.
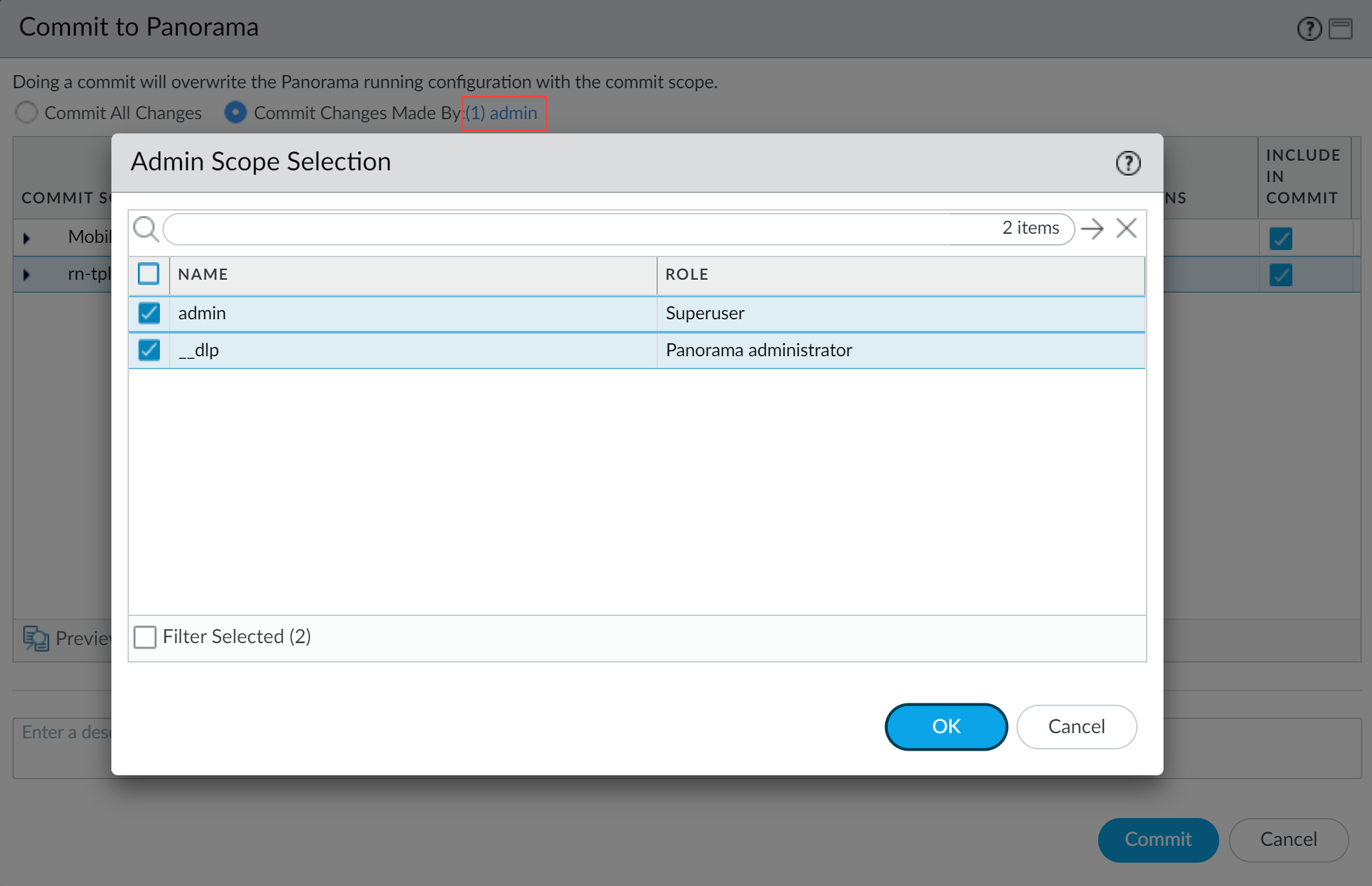
- Partial configuration push from PanoramaYou must always include the temporary __dlp administrator when performing a partial configuration push. This is required to keep Panorama and the DLP cloud service in sync.For example, you have an admin Panorama admin user who is allowed to commit and push configuration changes. The admin user made changes to the Enterprise DLP configuration and only wants to commit and push these changes to managed firewalls. In this case, the admin user is required to also select the __dlp user in the partial commit and push operations.
- Select CommitCommit to Panorama.
- Select Commit Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial commit.In this example, the admin user is currently logged in and performing the commit operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Commit.
- Select CommitPush to Devices.
- Select Push Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial push.In this example, the admin user is currently logged in and performing the push operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.