Enterprise DLP
SaaS Security
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
SaaS Security
Create a security policy rule to prevent exfiltration of sensitive data to ChatGPT
for SaaS Security on Strata Cloud Manager.
- Log into Strata Cloud Manager.Enable Non-File Inspection.Select ConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and create the decryption profile and policy rule required to enable Enterprise DLP on Strata Cloud Manager.Do not enable Strip ALPN in the decryption profile. Enterprise DLP cannot inspect egress traffic to ChatGPT if you remove application-layer protocol negotiation (ALPN) headers from decrypted traffic.(Optional) Create a data pattern.Create a custom regex data pattern to define your own match criteria. You can skip this step if you plan to use predefined or existing data patterns to define match criteria in your data filtering profile.Create a data profile or use an existing data profile.Select ConfigurationData Loss PreventionDLP Rules and in the Actions column, Edit the DLP rule.
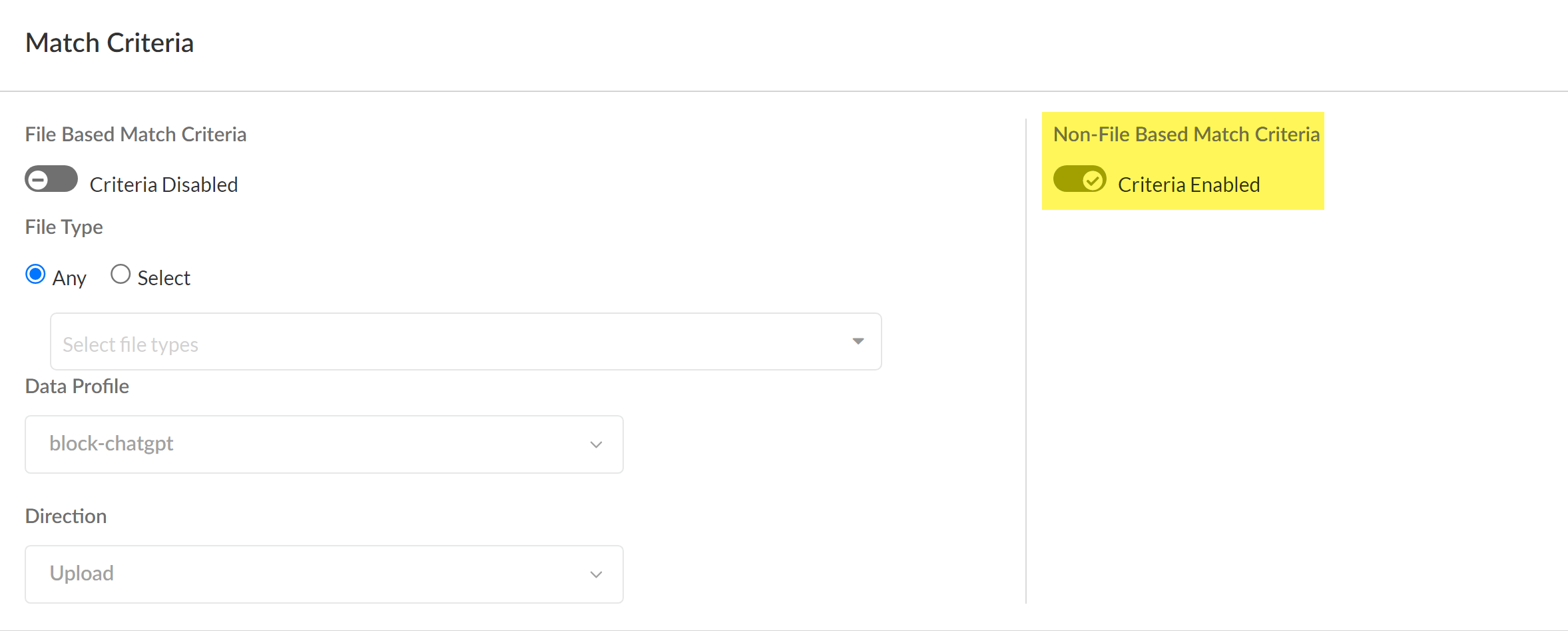
- Enable Non-File Based Match Criteria.DLP rules configured for non-file detection are required to prevent exfiltration of sensitive data to ChatGPT. You can further modify the DLP rule to enforce your organization’s data security standards. The DLP rule has an identical name as the data profile from which it was automatically created.You can keep File Based Matched Criteria enabled or disable as needed. Enabling this setting has no impact on detection of egress traffic to ChatGPT as long as Non-File Based Match Criteria is enabled.
![]() Modify the Action and Log Severity.Modify the rest of the DLP rule as needed.Save.Select ConfigurationSaaS SecurityDiscovered AppsPolicy Recommendations to create a Security policy rule recommendation.A SaaS policy rule recommendation is required to leverage the Enterprise Data Loss Prevention (E-DLP) data profile in SaaS Security.
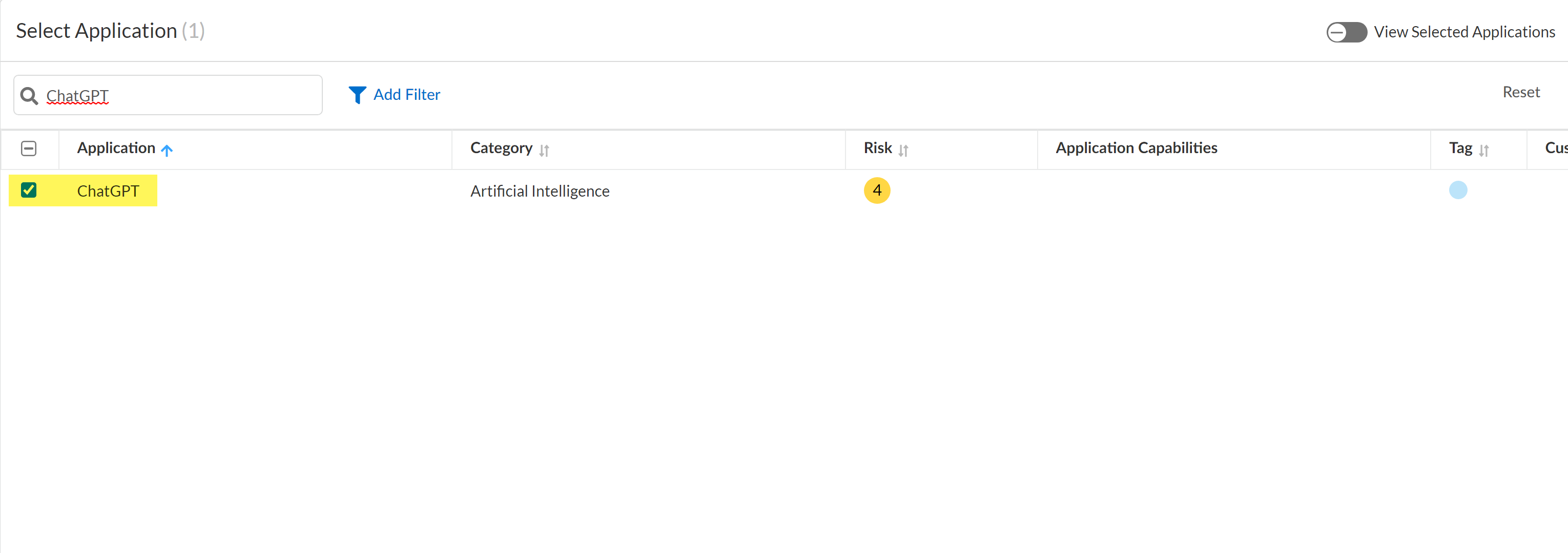
Modify the Action and Log Severity.Modify the rest of the DLP rule as needed.Save.Select ConfigurationSaaS SecurityDiscovered AppsPolicy Recommendations to create a Security policy rule recommendation.A SaaS policy rule recommendation is required to leverage the Enterprise Data Loss Prevention (E-DLP) data profile in SaaS Security.- In the Select Applications section, search for and select ChatGPT.
![]() In the Data Profile section, search for and select the data profile you enabled in the previous step.Configure the policy rule recommendation as needed.Save.
In the Data Profile section, search for and select the data profile you enabled in the previous step.Configure the policy rule recommendation as needed.Save.