Download PDF
GlobalProtect
Set Up GlobalProtect Connectivity to Strata Logging Service
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Set Up GlobalProtect Connectivity to Strata Logging Service
Set up GlobalProtect connectivity so that the GlobalProtect app can authenticate with Strata Logging Service for log collection.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You must set up GlobalProtect connectivity so that the GlobalProtect app can authenticate with
Strata Logging Service for log collection. Only one client certificate is
used per tenant. For example, all the end users endpoints that are hosted by a
Prisma Access tenant will obtain the same certificate pushed from the portal
configuration. The client certificate is valid for 1 year. The GlobalProtect app
uses the client certificate and the Strata Logging Service instance to send
the GlobalProtect App Troubleshooting logs to Strata Logging Service.
Based on the Cloud Services plugin version, you must set up GlobalProtect connectivity to Strata Logging Service by using the command line interface (CLI) or the
Panorama web interface that manages Prisma Access:
- Set Up GlobalProtect Connectivity to Strata Logging Service (Cloud Services Plugin 2.0 Innovation)
- Set Up GlobalProtect Connectivity to Strata Logging Service (Cloud Services Plugin 1.8 and 2.0 Preferred)
With
Cloud Managed Prisma Access, you can enable Log Collection for Troubleshooting for
the GlobalProtect app by using the Prisma Access app on the hub
to generate the certificate and to automatically import it so that
the app can authenticate with Strata Logging Service for log collection.
The certificate is automatically displayed in the Certificate
Management page, and is pushed as the client certificate
to the Prisma Access portal.
Set Up GlobalProtect Connectivity to Strata Logging Service (Cloud Services Plugin 2.0 Innovation)
With the Cloud Services plugin 2.0 Innovation,
if you have a deployment that uses Prisma Access or the next-generation
firewall, you must use the Panorama web interface to set up GlobalProtect
connectivity so that the GlobalProtect app can authenticate with
Strata Logging Service for log collection.
- Use the Strata Logging Service Estimator to calculate the amount of storage you need in Strata Logging Service.Generate a client certificate that is used to establish a connection from the GlobalProtect app to Strata Logging Service.
- Use the Panorama web interface that manages Prisma Access to generate a client certificate.
- Log in to the Panorama that manages Prisma Access.
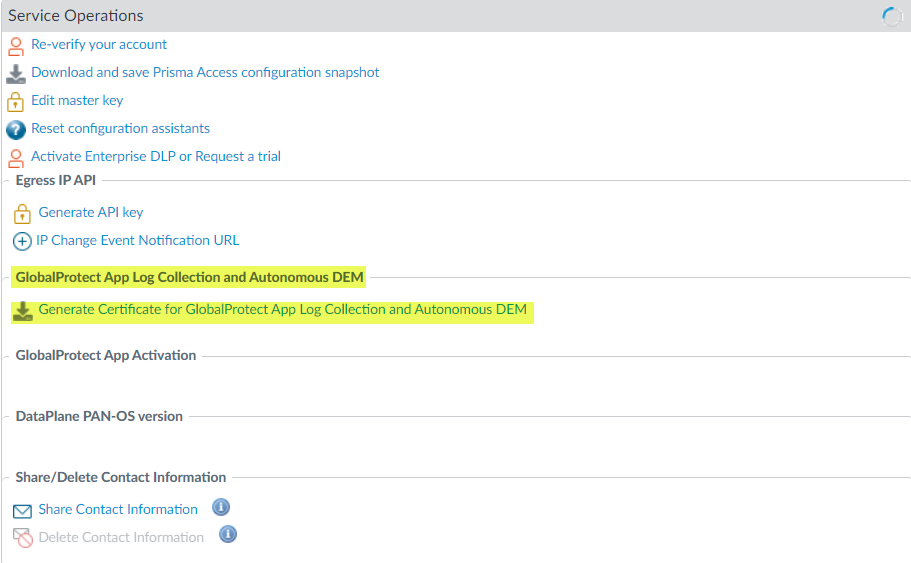
- Select PanoramaCloud ServicesConfigurationService Setup.
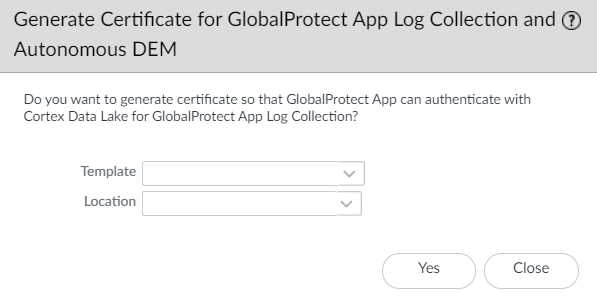
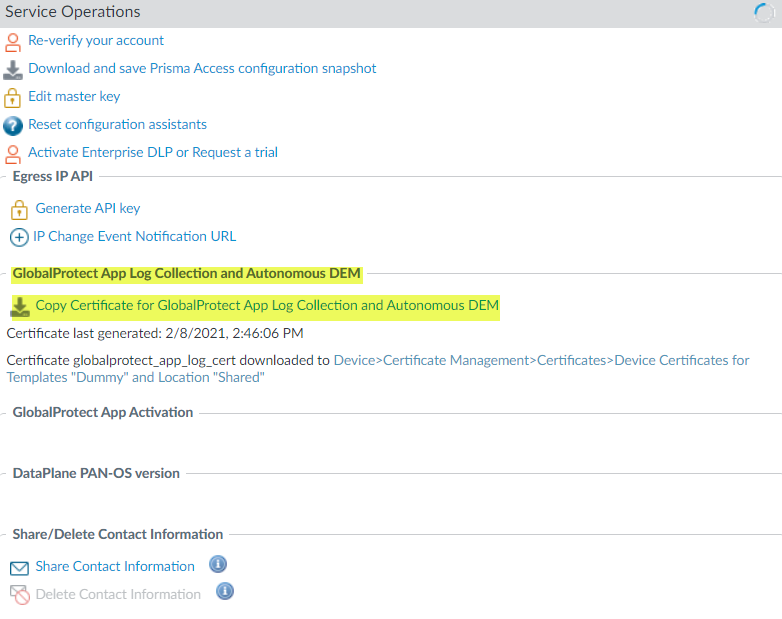
- Select Generate Certificate for GlobalProtect App Log Collection and Autonomous DEM.
![]()
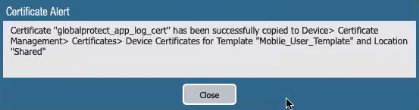
- For Prisma Access deployments, click Yes to generate a client certificate.If you configure Prisma Access to manage a single tenant, the globalprotect_app_log_cert certificate is automatically imported to the Mobile_User_Template and the Shared location.If you configure Prisma Access to manage multiple tenants, the globalprotect_app_log_cert certificate is automatically imported to the second mobile user template after the first and named mu-tpl-tenant. The globalprotect_app_log_cert certificate is imported to the additional tenants.After the globalprotect_app_log_cert certificate has been generated and downloaded to DeviceCertificate ManagementCertificates, you receive a success message. The Mobile_User_Template is selected automatically as the Template and Shared is selected automatically as the Location.
![]()
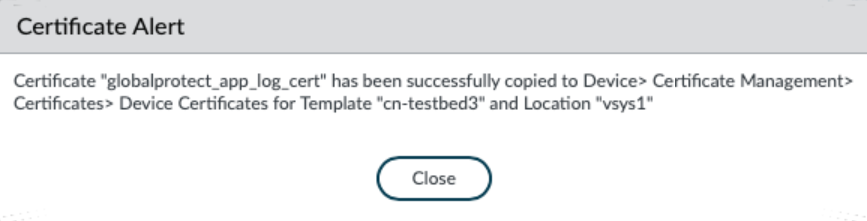
- In next-generation firewall deployments, select any Template from the drop-down and Location from the drop-down.Click Yes to generate a client certificate.
![]() After the globalprotect_app_log_cert certificate has been generated and downloaded to DeviceCertificate ManagementCertificatesDevice Certificates, you receive a success message. The assigned template is selected automatically as the Template and the assigned location is selected automatically as the Location.
After the globalprotect_app_log_cert certificate has been generated and downloaded to DeviceCertificate ManagementCertificatesDevice Certificates, you receive a success message. The assigned template is selected automatically as the Template and the assigned location is selected automatically as the Location.![]()
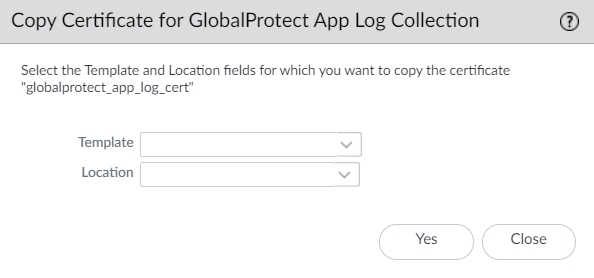
- (Optional) In next-generation firewall deployments, copy the globalprotect_app_log_cert certificate to another template and location.Select Copy Certificate for GlobalProtect App Log Collection and Autonomous DEM.
![]() Select another Template from the drop-down and Location from the drop-down.Click Yes to generate a client certificate.
Select another Template from the drop-down and Location from the drop-down.Click Yes to generate a client certificate.![]() After the globalprotect_app_log_cert certificate has been generated and downloaded to DeviceCertificate ManagementCertificatesDevice Certificates, you receive a success message. The assigned template is selected automatically as the Template and the assigned location is selected automatically as the Location.
After the globalprotect_app_log_cert certificate has been generated and downloaded to DeviceCertificate ManagementCertificatesDevice Certificates, you receive a success message. The assigned template is selected automatically as the Template and the assigned location is selected automatically as the Location.
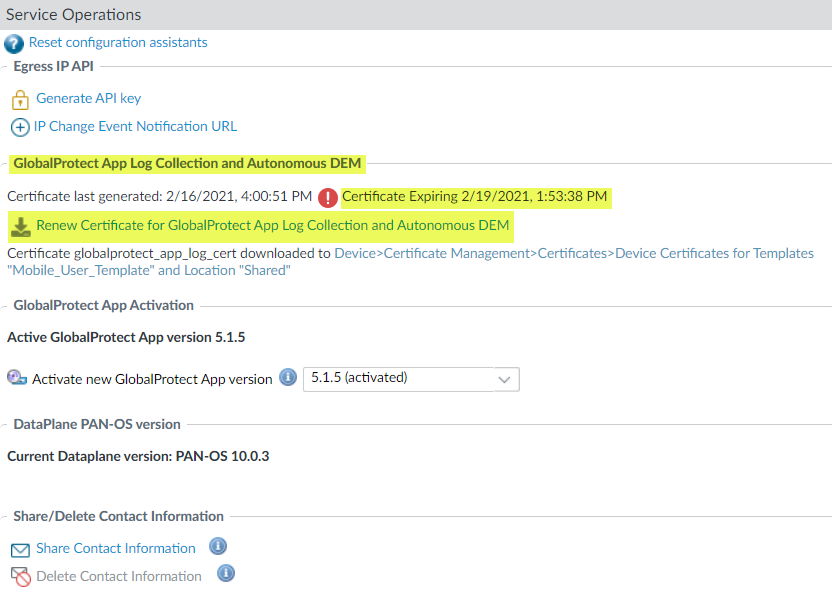
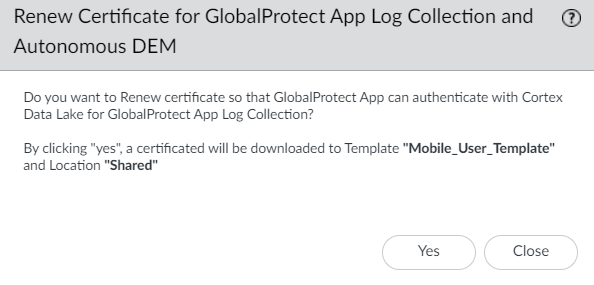
(Optional) Request a new client certificate before the certificate expires.The client certificate has a lifespan of 1 year.- In Panorama, select PanoramaCloud ServicesConfigurationTenantsSelect the tenant you created from the Tenant drop-down.Select PanoramaCloud ServicesConfigurationService Setup.Select Renew Certificate for GlobalProtect App Log Collection and Autonomous DEM.
![]() Click Yes to renew and download another client certificate. The assigned template is associated automatically as the Template and the assigned location is associated automatically as the Location.
Click Yes to renew and download another client certificate. The assigned template is associated automatically as the Template and the assigned location is associated automatically as the Location.![]() Create or modify the existing GlobalProtect agent configuration for a specific group of users.To enable the GlobalProtect app log collection for troubleshooting, you must define the agent configuration for a specific group of users to send the logs to Strata Logging Service.
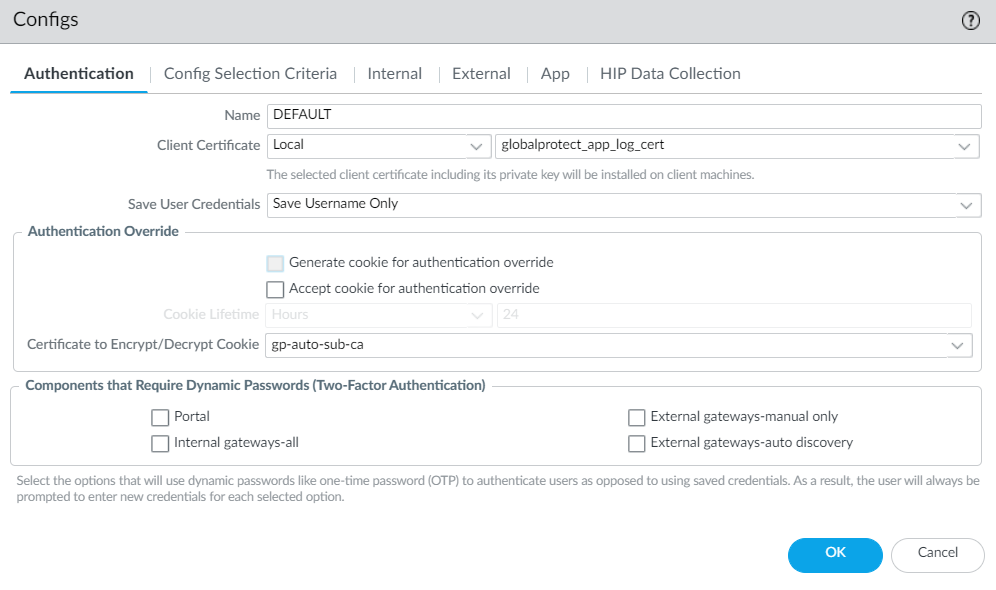
Create or modify the existing GlobalProtect agent configuration for a specific group of users.To enable the GlobalProtect app log collection for troubleshooting, you must define the agent configuration for a specific group of users to send the logs to Strata Logging Service.- In Panorama, select NetworkGlobalProtectPortals.Select the Mobile_User_Template from the Template drop-down.If you set up a deployment that includes multiple instances of Prisma Access on a single Panorama (multi-tenancy), you can select another template associated with the configuration.Select GlobalProtect_Portal to edit the Prisma Access portal configuration.Select the Agent tab.Select the Agent tab and select the agent configuration.Select the Local (default) and DEFAULTglobalprotect_app_log_cert from the Client Certificate drop-down.After you "Enable Autonomous DEM and GlobalProtect Log Collection for Troubleshooting" and push globalprotect_app_log_cert to the client machine, one root CA, two intermediate CAs, and one client certificate, issued by Palo Alto Networks, are installed in the user's Personal store.Palo Alto Networks automatically generates the Strata Logging Service client certificate, so the root CA certificate and intermediate CA certificate must be owned by Palo Alto Networks. Palo Alto Networks can add the root certificate to portal configuration so that the GlobalProtect client can install it as a trusted root CA to the machine if they want to do so.Because the Client Certificate is used to push the Strata Logging Service certificate, you cannot push the client certificate to authenticate to the portal or gateway either using a Local certificate type (default) or Simple Certificate Enrollment Protocol (SCEP).
![]()
Set Up GlobalProtect Connectivity to Strata Logging Service (Cloud Services Plugin 1.8 and 2.0 Preferred)
With the Cloud Services plugin 1.8 and 2.0 Preferred, you must use the commands to set up GlobalProtect connectivity so that the GlobalProtect app can authenticate with Strata Logging Service for log collection.- Use the Strata Logging Service Estimator to calculate the amount of storage you need in Strata Logging Service.Generate a client certificate that is used to establish a connection from the GlobalProtect app to Strata Logging Service.
- Open a CLI session with administrator privileges, using the same IP address that you use to log in to the Panorama that manages Prisma Access.Enter the request plugins cloud_services gpclient_cert fetch command, as shown in the following example:
admin-Panorama>request plugins cloud_services gpclient_cert fetch Success Successfully imported globalprotect_gp_log_cert into candidate configurationIf a client certificate is already generated, the command output is as follows:admin-Panorama> request plugins cloud_services gpclient_cert fetch certificate exists and not expiredCommit your changes on Panorama.Verify the status of the client certificate by entering the following command:admin-Panorama> request plugins cloud_services gpclient_cert status certificate globalprotect_app_log_cert is valid till Oct 22 21:55:39 2021 GMTExport the gp_app_log_cert certificate from the Panorama certificate store.- In Panorama, select PanoramaCertificate ManagementCertificates, select the gp_app_log_cert certificate, and Export Certificate.Select Encrypted Private Key and Certificate (PKCS12) from the File Format drop-down to export the certificate and private key in a single file.Enter a Passphrase and Confirm Passphrase to import the certificate key.Click OK and save the certificate/key file to your computer.Import the gp_app_log_cert certificate to the Panorama template where the GlobalProtect portal configuration resides.If you configure Prisma Access to manage a single tenant, you must import the gp_app_log_cert certificate to the Mobile_User_Template.If you configure Prisma Access to manage multiple tenants, you must import the gp_app_log_cert certificate to the second mobile user template automatically created after the first and named mu-tpl-tenant. You must import the gp_app_log_cert certificate to the additional tenants.
- In Panorama, select DeviceCertificate ManagementCertificates, and then click Import.For the Certificate Type, select Local.Enter gp_app_log_cert as the Certificate Name.Browse for the certificate file that you exported.Enter the Passphrase and Confirm Passphrase used to encrypt the private key.Click OK to import the certificate.Create or modify the existing GlobalProtect agent configuration for a specific group of users.To enable the GlobalProtect app log collection for troubleshooting, you must define the agent configuration for a specific group of users to send the logs to Strata Logging Service.
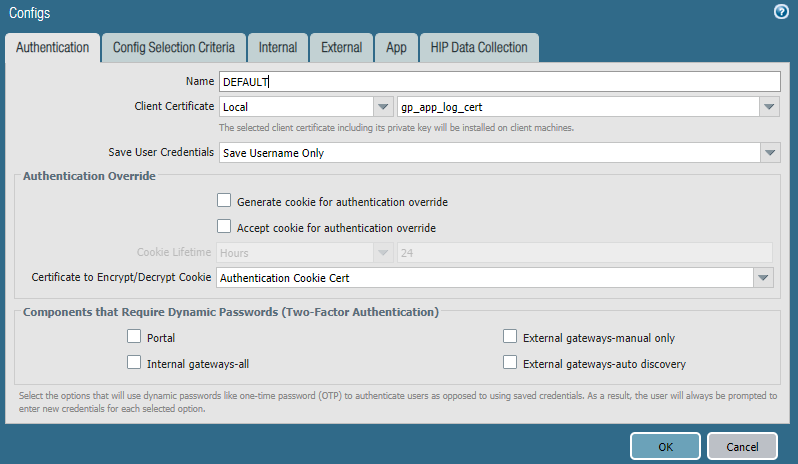
- In Panorama, select NetworkGlobalProtectPortals.Select the Mobile_User_Template from the Template drop-down.If you set up a deployment that includes multiple instances of Prisma Access on a single Panorama (multi-tenancy), you can select another template associated with the configuration.Select GlobalProtect_Portal to edit the Prisma Access portal configuration.Select the Agent tab.Select the Agent tab and select the DEFAULT agent configuration.Select the Local (default) and gp_app_log_cert from the Client Certificate drop-down.Because the Client Certificate is used to push the Strata Logging Service certificate, you cannot push the client certificate to authenticate to the portal or gateway either using a Local certificate type (default) or Simple Certificate Enrollment Protocol (SCEP).
![]()