IoT Security
MDS2 Community
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
MDS2 Community
Share and compare MDS2 documents with other IoT Security users in the MDS2
community.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
If
you want, you can override the automatic MDS2 file selection and
apply a different file of your choice. See the last step below for
instructions.
- View your uploaded MDS2 files and shared community files.
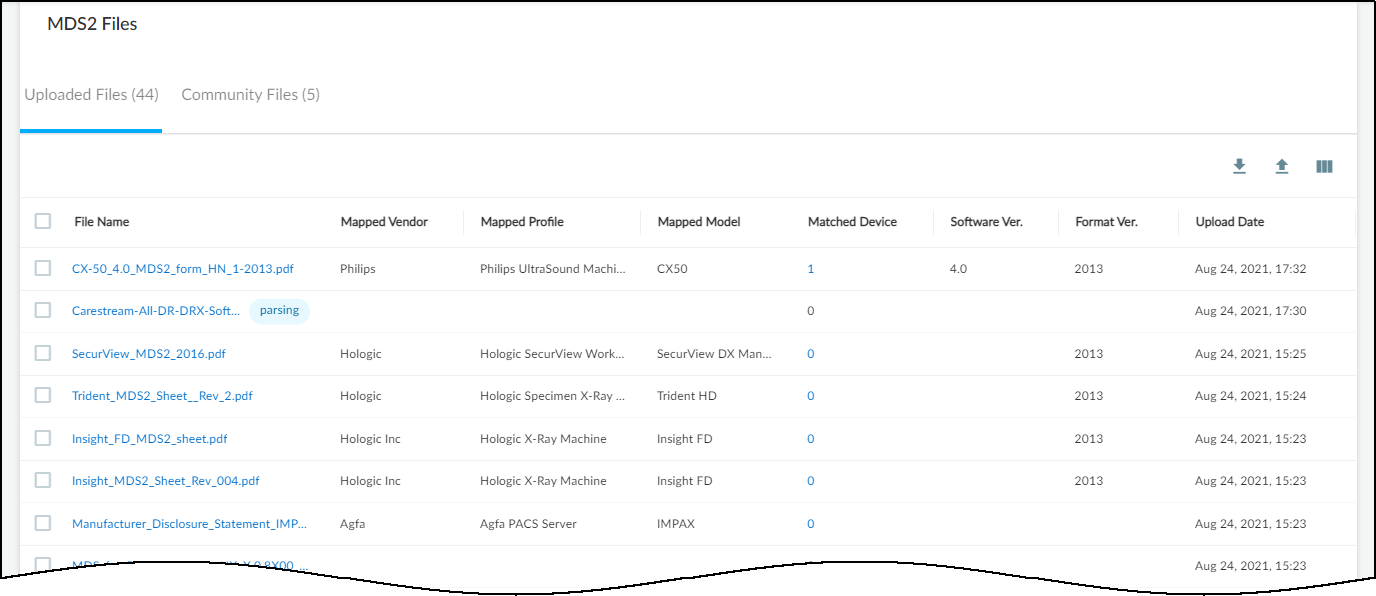
- On the VulnerabilitiesMDS2 page, click <number> Files Available in Community.The VulnerabilitiesMDS2MDS2 Files page opens with two tabs: one for the files you uploaded (Uploaded Files) and one for files shared in the community (Community Files).
![]() The table provides key details about the MDS2 file: the vendor, profile, model, and software version it applies to; how many devices in your inventory it matches; the format version of the MDS2 file; and when it was uploaded to IoT Security.
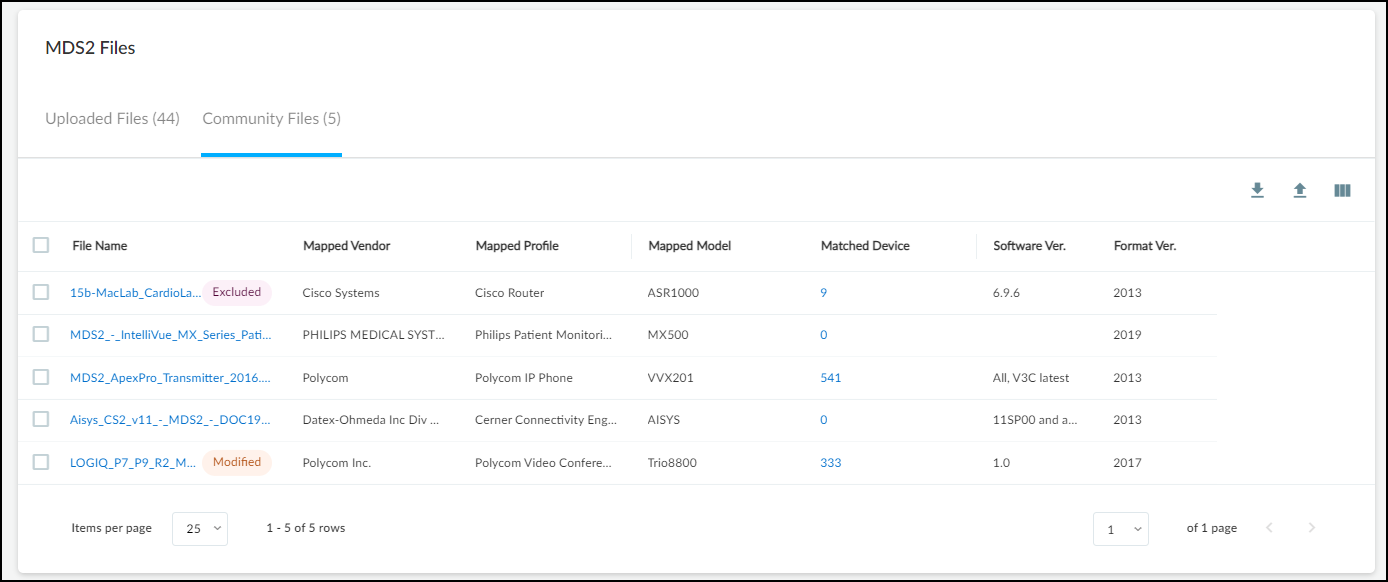
The table provides key details about the MDS2 file: the vendor, profile, model, and software version it applies to; how many devices in your inventory it matches; the format version of the MDS2 file; and when it was uploaded to IoT Security.![]() The table on the Community Files page provides almost all the same information as that on the Uploaded Files page except for the date the file was uploaded.
The table on the Community Files page provides almost all the same information as that on the Uploaded Files page except for the date the file was uploaded.
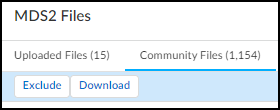
If there are shared MDS2 files that you don’t want IoT Security to apply to your devices, exclude them.You might not want IoT Security to apply one or more community files to your medical IoT devices, perhaps because you prefer a different version for some reason. In this case, you can exclude them from the automatic selection process.- Select VulnerabilitiesMDS2MDS2 FilesCommunity Files, select the check box of an MDS2 file you want to exclude from the automatic selection process.Exclude and Download buttons appear above the table.
![]()
- Click Exclude.If you change your mind, repeat these steps but click Include instead of Exclude. IoT Security displays an Include button for previously excluded MDS2 files.
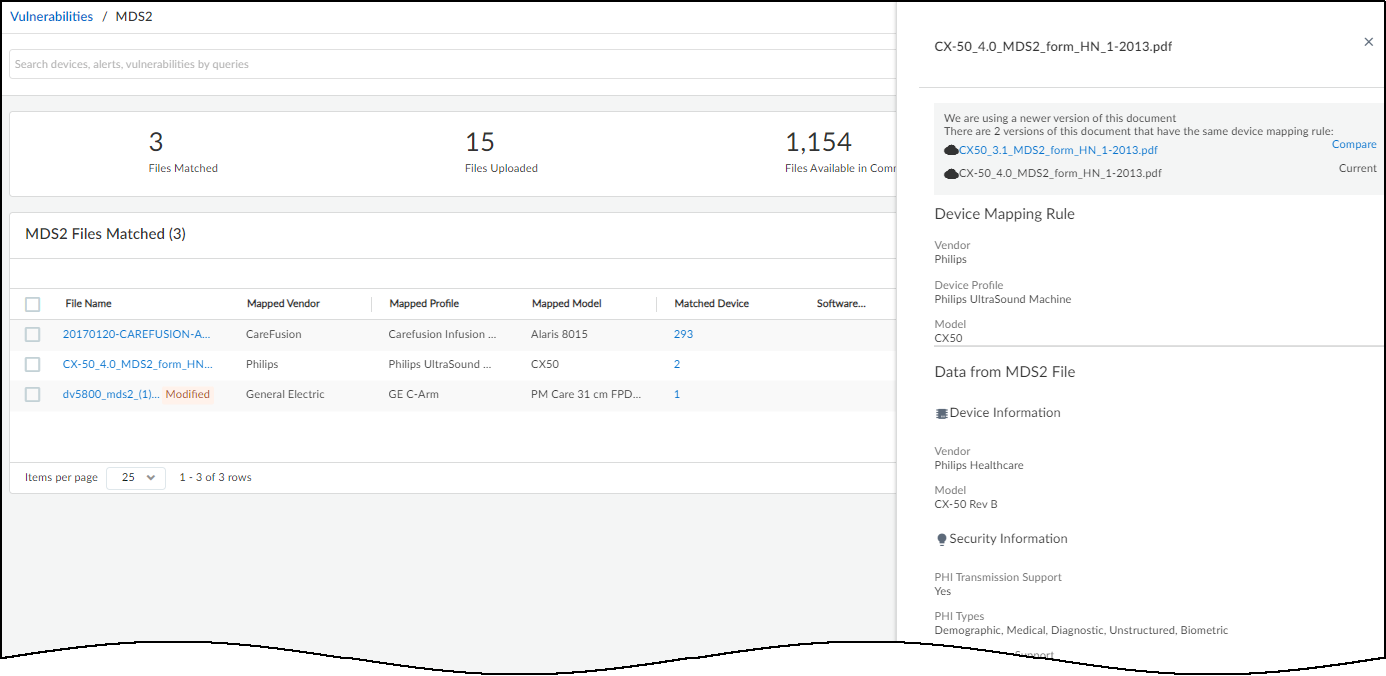
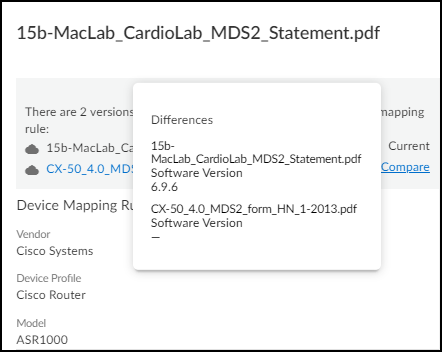
If there are duplicate MDS2 files and you want to use something different from what IoT Security automatically selected, manually override the selection.When more than one MDS2 file applies to the same vendor, profile, and model, you might want IoT Security to apply a different MDS2 file other than the one it automatically selected. For example, you might choose an earlier format version if your medical IoT devices are running earlier software versions and this MDS2 file applies to them more accurately than a later one would.- Click an MDS2 file name on the VulnerabilitiesMDS2 page.The information panel that opens on the right side of the page lists duplicate MDS2 files in order of priority.
![]() The information panel for a file you uploaded includes an Edit option, but the panel for a community-shared file does not.
The information panel for a file you uploaded includes an Edit option, but the panel for a community-shared file does not. - To compare two duplicate files, either click or hover your cursor over Compare. IoT Security compares it with the currently applied file. In the example shown here, you can see that the first MDS2 file is prioritized because it has a software version whereas the second file does not.
![]()
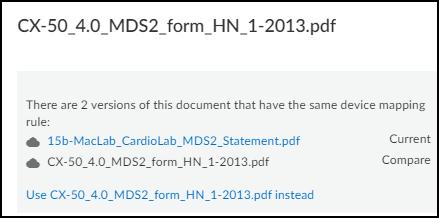
- To use a different file, click its name and then click Use <file-name> instead.
![]() The name of your selected file now appears in the File Name column and is shown as Current in the information panel.
The name of your selected file now appears in the File Name column and is shown as Current in the information panel.