Device Security
Restrict Network Access
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Restrict Network Access
Restrict IoT devices of concern from accessing the network.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
|
Although policy recommendations enforce trusted
behaviors for IoT devices, they only take effect when device behavior
changes. However, if Device Security detects elevated risk on a device,
perhaps caused by business-critical devices running obsolete operating
systems, and you want to take preventive action before an exploit
is launched, you need to take a different approach from behavior-based
policy rules.
Device Security provides another option that lets
you restrict network access to a specific IoT device or group of
IoT devices that have the same issue, such as those susceptible
to or suspected of compromise.
To accomplish this, first create
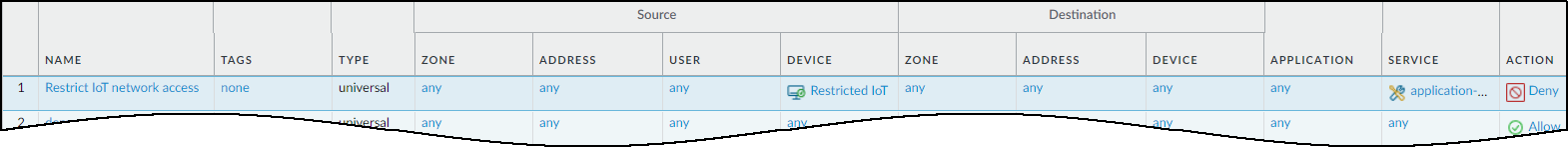
a Security policy rule in which Source Device is any device whose
category is “Restricted” and the action in the rule is Deny. Position
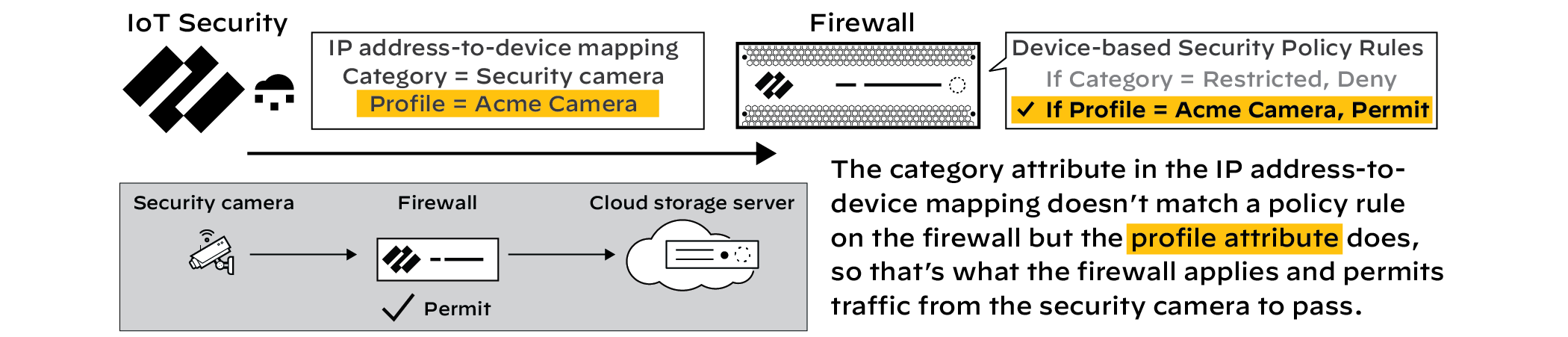
this rule above all other device-based rules in the rules list.
Otherwise, there’s a chance that a rule based on the profile attribute,
or on some other attribute, will occlude it. Similarly, make sure
the “Restricted” rule is above any rule that might occlude
it, even those not using Device-ID.
Then, in the Device Security
portal, enable the network traffic restriction feature but don’t
use it to restrict access yet. Notice that firewalls won’t apply
the new rule because none of the IP address-to-device mappings have
a category attribute that matches “Restricted”.
When
you restrict network access for one or more devices, Device Security
immediately changes the category attribute for them from their real
device categories to “Restricted” and sends firewalls new IP address-to-device
mappings for them. When traffic reaches a firewall from a device
with the “Restricted” category attribute, it applies the security
rule you created, denying it access to the network.
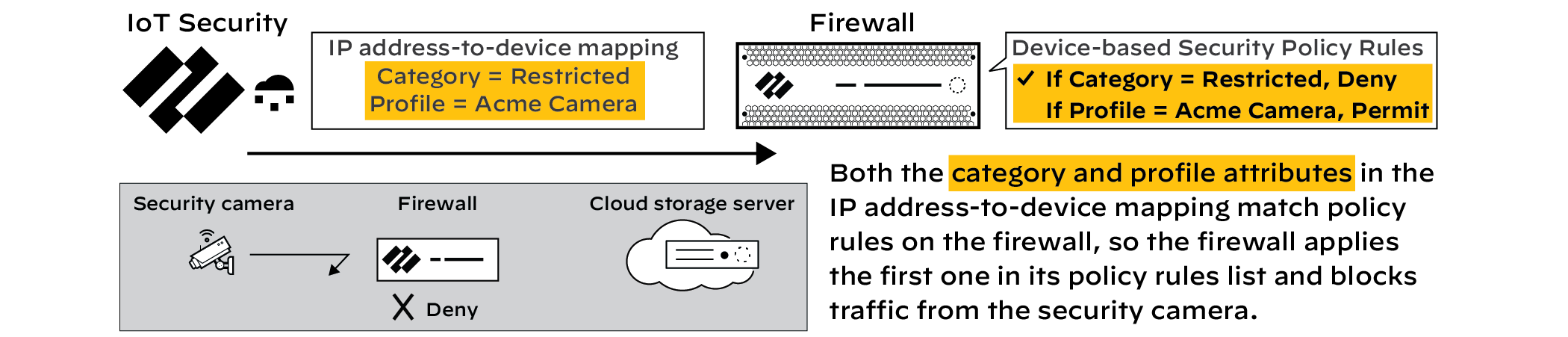
Although
the accompanying illustrations show how a firewall enforces a “category=Restricted”
rule instead of another device-based Security policy rule, it’s
not necessary for the other rule to be device based. You can also
restrict network access for an IoT device even when a firewall permits
its access based on source IP address, service, application, or
any other factor or combination of factors.
Later,
after the security issue is resolved, you derestrict devices, which
returns the IP address-to-device mapping for them to their previous
categories. As a result, their category attributes no longer match
the “Restricted” rule and the devices will be permitted to access
the network as determined by other rules.
Notes:
- To support the traffic restriction feature, firewalls must have device dictionary file 16-253 or later. The device dictionary version appears in the General Information section on the PAN-OS web interface Dashboard.
- Traffic restriction is only applicable for devices with a high identity confidence score of 90 or above.A confidence score indicates the level of confidence Device Security has in its identification of a device. Device Security has three confidence levels based on calculated confidence scores: high (90-100%), medium (70-89%), and low (0-69%).
- This feature restricts network access but doesn’t completely quarantine a device. Depending on network design, a restricted device can still access those parts of the network it can reach without traversing a firewall.
- Only an Device Security user with owner privileges or a superuser role can enable and disable the feature.
Strata Cloud Manager
From Device Security in Strata Cloud Manager, restrict IoT devices of concern from
accessing the network.
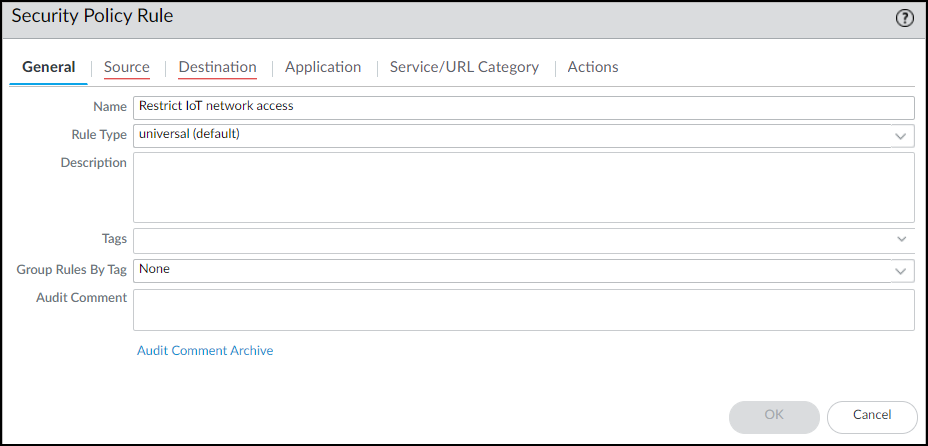
- Configure a Security policy rule that denies traffic from any device whose Device-ID attribute for Category is “Restricted”.These instructions explain how to configure a security policy rule in the PAN-OS web UI. You can also configure it through Panorama.Log in to the web UI on your firewall, click PoliciesSecurity, and then click Add to create a new Security policy rule. On the General tab, enter a name for the rule such as Restrict IoT network access.
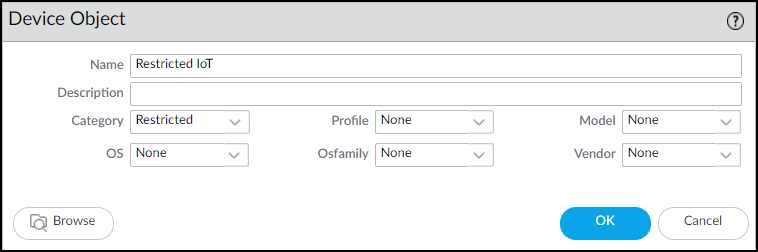
![]() On the Source tab, click Add in the Source Device section and then click Device. In the Device Object dialog box that appears, enter a name, choose Restricted for Category, and then click OK.
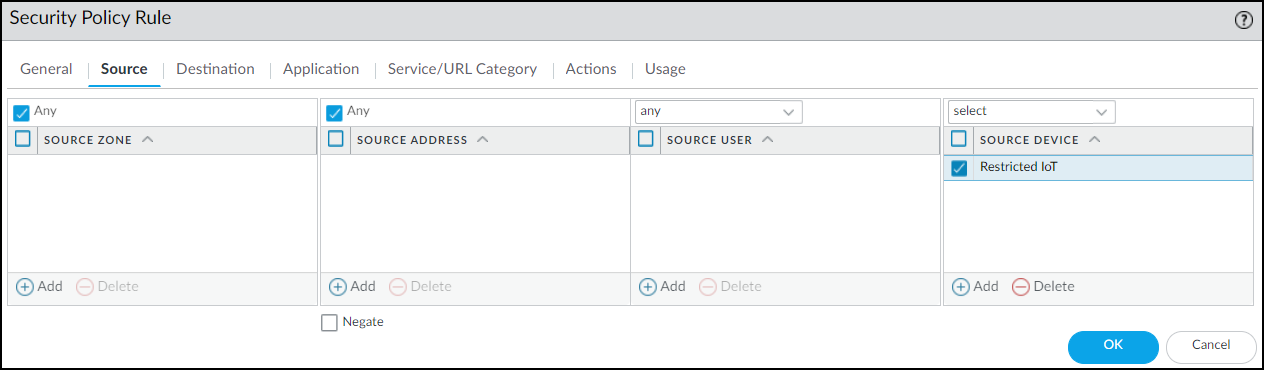
On the Source tab, click Add in the Source Device section and then click Device. In the Device Object dialog box that appears, enter a name, choose Restricted for Category, and then click OK.![]() Select the device object you just created as the source device and select Any for the source zone and address.
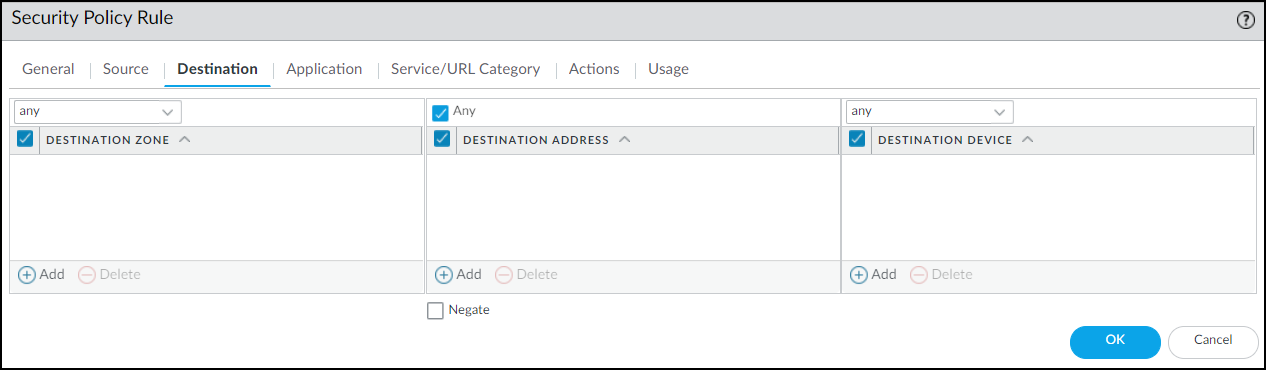
Select the device object you just created as the source device and select Any for the source zone and address.![]() On the Destination tab, select Any for the destination zone, address, and device.
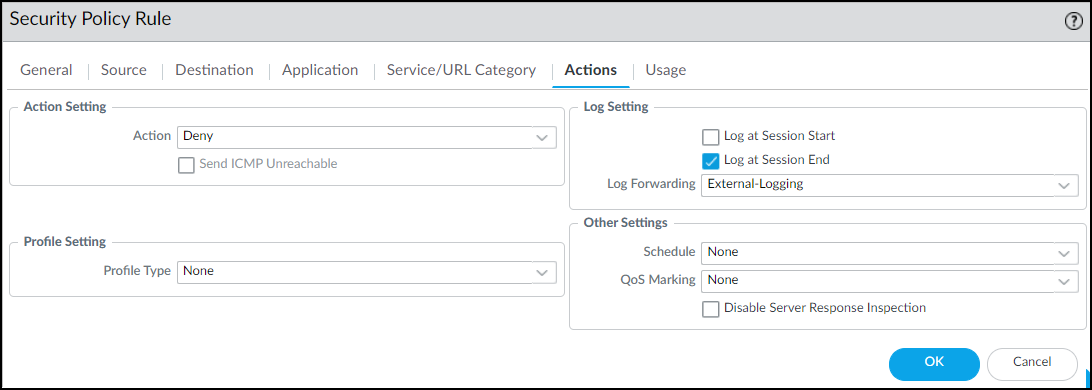
On the Destination tab, select Any for the destination zone, address, and device.![]() On the Actions tab, choose Deny as the action. If the firewall forwards logs to Strata Logging Service, Panorama, or some other external log server, choose a log forwarding profile. Even for a rule that denies traffic, logs provide visibility into what the restricted device was attempting to connect with and are useful during remediation. Click OK to save the Security policy rule configuration.
On the Actions tab, choose Deny as the action. If the firewall forwards logs to Strata Logging Service, Panorama, or some other external log server, choose a log forwarding profile. Even for a rule that denies traffic, logs provide visibility into what the restricted device was attempting to connect with and are useful during remediation. Click OK to save the Security policy rule configuration.![]() Move the rule above other policy rules.
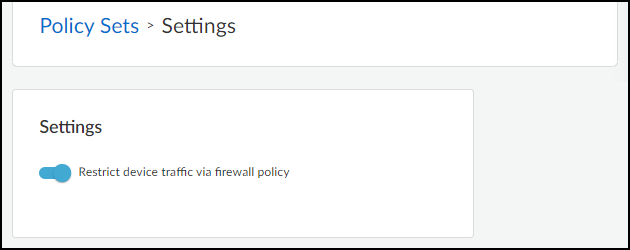
Move the rule above other policy rules.![]() Enable traffic restriction in Device Security in Strata Cloud Manager.Log in to Device Security in Strata Cloud Manager with a superuser role, click PoliciesDevice-ID Policy Configuration, and then toggle Restrict device traffic via firewall policy.
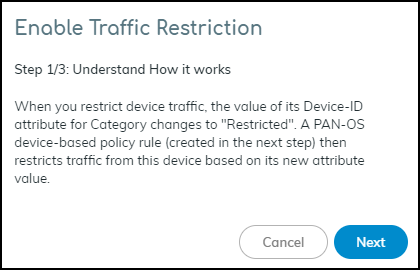
Enable traffic restriction in Device Security in Strata Cloud Manager.Log in to Device Security in Strata Cloud Manager with a superuser role, click PoliciesDevice-ID Policy Configuration, and then toggle Restrict device traffic via firewall policy.![]() A pop-up panel appears. Read how traffic restriction works and then click Next.
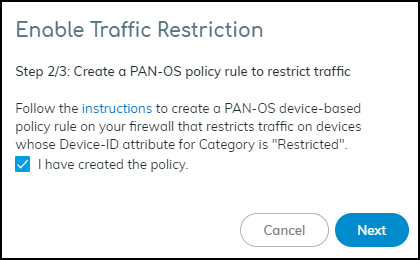
A pop-up panel appears. Read how traffic restriction works and then click Next.![]() Select I have created the policy and then click Next.
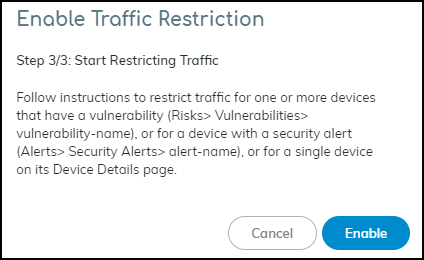
Select I have created the policy and then click Next.![]() Read where to restrict traffic in the Device Security portal and then click Enable.
Read where to restrict traffic in the Device Security portal and then click Enable.![]() Restrict IoT devices.As stated in step 3/3 of the Enable Traffic Restriction panel, there are three places in Device Security in Strata Cloud Manager where you can restrict network traffic: vulnerability instances on a Vulnerability Details page, a Security Alert Details page, and a Device Details page. Each place, or point of restriction, is described below.Vulnerability Instance as the Point of RestrictionTo restrict one or more IoT devices on the Vulnerability Details page, click RisksVulnerabilities and then click a vulnerability name.If the Confidence Level column is hidden, click the Columns icon () and select it. Select one or more vulnerability instances with a high confidence score of 90 or above and then click MoreRestrict Traffic.
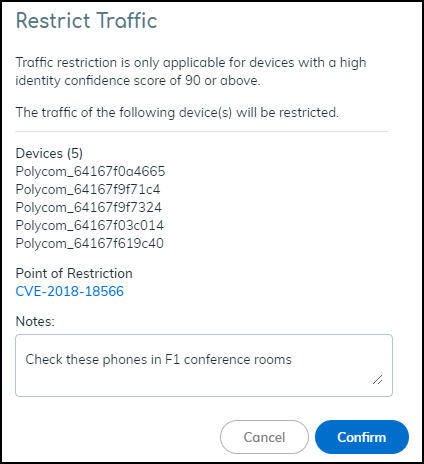
Restrict IoT devices.As stated in step 3/3 of the Enable Traffic Restriction panel, there are three places in Device Security in Strata Cloud Manager where you can restrict network traffic: vulnerability instances on a Vulnerability Details page, a Security Alert Details page, and a Device Details page. Each place, or point of restriction, is described below.Vulnerability Instance as the Point of RestrictionTo restrict one or more IoT devices on the Vulnerability Details page, click RisksVulnerabilities and then click a vulnerability name.If the Confidence Level column is hidden, click the Columns icon () and select it. Select one or more vulnerability instances with a high confidence score of 90 or above and then click MoreRestrict Traffic.![]() Review the list of vulnerable or potentially vulnerable devices whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.
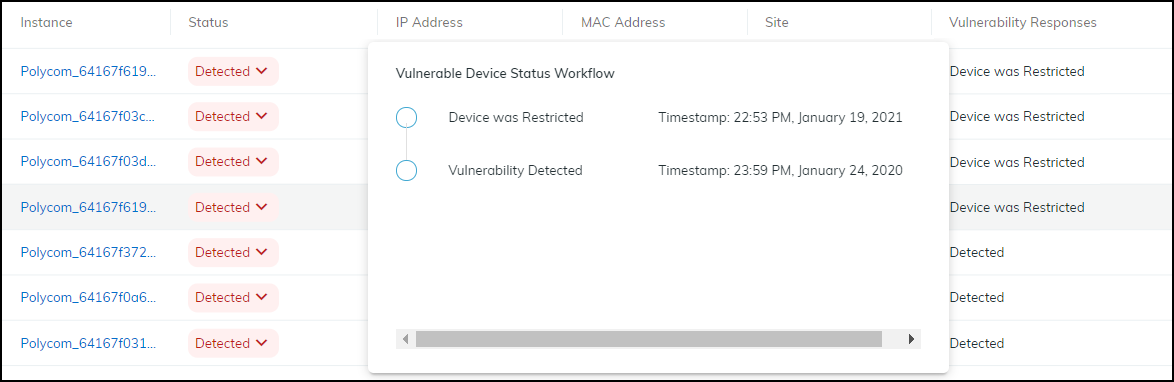
Review the list of vulnerable or potentially vulnerable devices whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.![]() The entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic. A new entry appears in the Vulnerability Responses column. Hover your cursor over the entry to see a history of actions taken.
The entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic. A new entry appears in the Vulnerability Responses column. Hover your cursor over the entry to see a history of actions taken.![]()
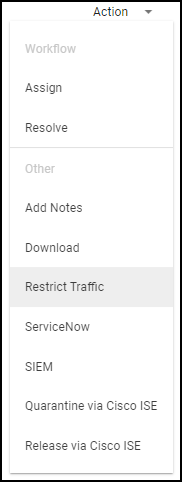
![]() The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. If you hover your cursor over the label, a pop-up appears with the time and point of restriction and a link to a vulnerability, security alert, or device details page. In this case, it would be a link to a Vulnerability Details page. The pop-up also includes any notes you made.Security Alert as the Point of RestrictionTo restrict an IoT device with a specific security alert, click AlertsSecurity Alerts and then click an alert name. On the Alert Details page, click ActionRestrict Traffic.
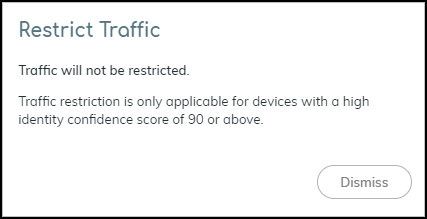
The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. If you hover your cursor over the label, a pop-up appears with the time and point of restriction and a link to a vulnerability, security alert, or device details page. In this case, it would be a link to a Vulnerability Details page. The pop-up also includes any notes you made.Security Alert as the Point of RestrictionTo restrict an IoT device with a specific security alert, click AlertsSecurity Alerts and then click an alert name. On the Alert Details page, click ActionRestrict Traffic.![]() If the confidence score of the impacted device is below 90, the following message appears. The confidence score appears in the Impacted Device section on the Alert Details page.
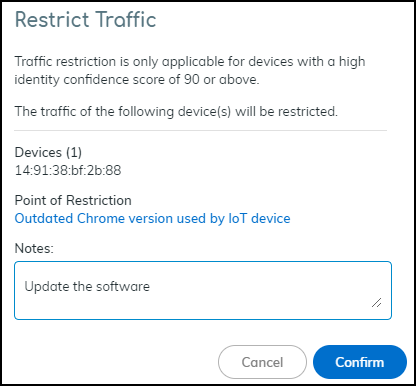
If the confidence score of the impacted device is below 90, the following message appears. The confidence score appears in the Impacted Device section on the Alert Details page.![]() If the confidence score is 90 or above, the Restrict Traffic dialog box appears.
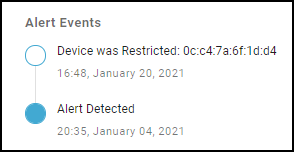
If the confidence score is 90 or above, the Restrict Traffic dialog box appears.![]() Review the device whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.A new label appears at the top of the Alert Details page stating Traffic Restricted Yes and a new entry appears in the Alert Events column.
Review the device whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.A new label appears at the top of the Alert Details page stating Traffic Restricted Yes and a new entry appears in the Alert Events column.![]() The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to a Security Alert Details page; and any notes you made.IoT Device Details as the Point of RestrictionTo restrict a single IoT device on the Device Details page, click AssetsInventory and then the name of one of the devices in the inventory table. In the Identity section at the top of the Device Details page, click the Action icon (three vertical dots) Restrict Traffic.
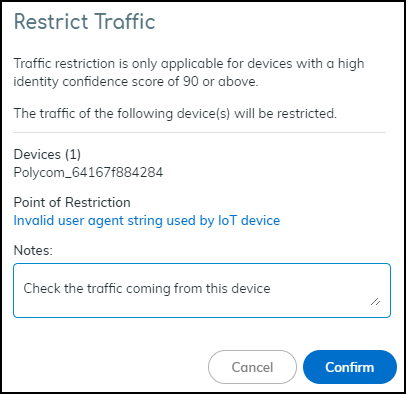
The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to a Security Alert Details page; and any notes you made.IoT Device Details as the Point of RestrictionTo restrict a single IoT device on the Device Details page, click AssetsInventory and then the name of one of the devices in the inventory table. In the Identity section at the top of the Device Details page, click the Action icon (three vertical dots) Restrict Traffic.![]() Check that the device whose traffic will be restricted is correct, optionally add a note for future reference, and then click Confirm.
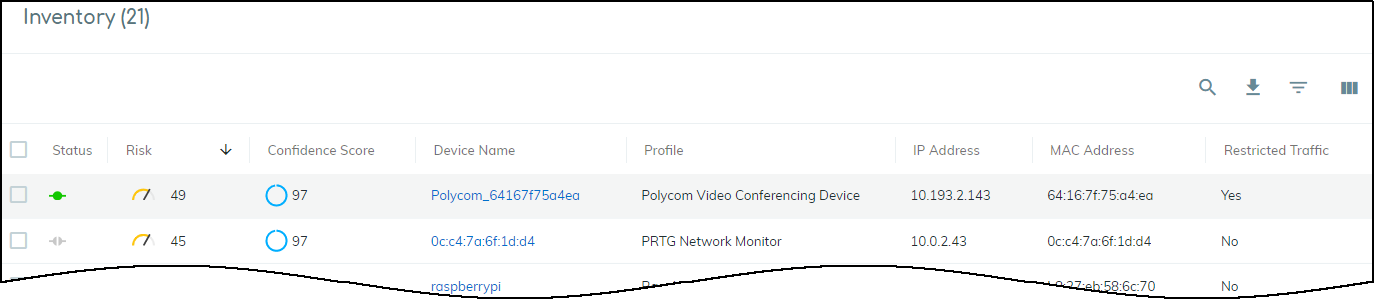
Check that the device whose traffic will be restricted is correct, optionally add a note for future reference, and then click Confirm.![]() The Device Security portal adds a Restricted Device label next to the device name on the Device Details page. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to the same Device Details page you’re already on; and any notes you made.On the Devices page, the entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic in the Traffic section.
The Device Security portal adds a Restricted Device label next to the device name on the Device Details page. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to the same Device Details page you’re already on; and any notes you made.On the Devices page, the entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic in the Traffic section.![]()
![]() After investigating and remediating a traffic-restricted device, derestrict traffic for it.To derestrict traffic for a device, repeat the same process as you did to restrict traffic but click Derestrict Traffic.You can derestrict multiple vulnerability instances in bulk. Select one or more instances on the Vulnerability Details page and then click MoreDerestrict Traffic.For other traffic-restricted devices, view the inventory on the Devices page with the Restricted Traffic filter applied. Then click device names one by one to open the Device Details page for each one and click the Action icon (three vertical dots) Derestrict Traffic.
After investigating and remediating a traffic-restricted device, derestrict traffic for it.To derestrict traffic for a device, repeat the same process as you did to restrict traffic but click Derestrict Traffic.You can derestrict multiple vulnerability instances in bulk. Select one or more instances on the Vulnerability Details page and then click MoreDerestrict Traffic.For other traffic-restricted devices, view the inventory on the Devices page with the Restricted Traffic filter applied. Then click device names one by one to open the Device Details page for each one and click the Action icon (three vertical dots) Derestrict Traffic.Legacy IoT Security
Restrict IoT devices of concern from accessing the network.- Configure a Security policy rule that denies traffic from any device whose Device-ID attribute for Category is “Restricted”.These instructions explain how to configure a security policy rule in the PAN-OS web UI. You can also configure it through Panorama.Log in to the web UI on your firewall, click PoliciesSecurity, and then click Add to create a new Security policy rule. On the General tab, enter a name for the rule such as Restrict IoT network access.
![]() On the Source tab, click Add in the Source Device section and then click Device. In the Device Object dialog box that appears, enter a name, choose Restricted for Category, and then click OK.
On the Source tab, click Add in the Source Device section and then click Device. In the Device Object dialog box that appears, enter a name, choose Restricted for Category, and then click OK.![]() Select the device object you just created as the source device and select Any for the source zone and address.
Select the device object you just created as the source device and select Any for the source zone and address.![]() On the Destination tab, select Any for the destination zone, address, and device.
On the Destination tab, select Any for the destination zone, address, and device.![]() On the Actions tab, choose Deny as the action. If the firewall forwards logs to Strata Logging Service, Panorama, or some other external log server, choose a log forwarding profile. Even for a rule that denies traffic, logs provide visibility into what the restricted device was attempting to connect with and are useful during remediation. Click OK to save the Security policy rule configuration.
On the Actions tab, choose Deny as the action. If the firewall forwards logs to Strata Logging Service, Panorama, or some other external log server, choose a log forwarding profile. Even for a rule that denies traffic, logs provide visibility into what the restricted device was attempting to connect with and are useful during remediation. Click OK to save the Security policy rule configuration.![]() Move the rule above other policy rules.
Move the rule above other policy rules.![]() Enable traffic restriction in the Device Security portal.Log in to the Device Security portal with owner privileges, click PoliciesSettings, and then toggle Restrict device traffic via firewall policy.The following user roles have Device Security owner privileges: account administrator, app administrator, instance administrator, and owner.
Enable traffic restriction in the Device Security portal.Log in to the Device Security portal with owner privileges, click PoliciesSettings, and then toggle Restrict device traffic via firewall policy.The following user roles have Device Security owner privileges: account administrator, app administrator, instance administrator, and owner.![]() A pop-up panel appears. Read how traffic restriction works and then click Next.
A pop-up panel appears. Read how traffic restriction works and then click Next.![]() Select I have created the policy and then click Next.
Select I have created the policy and then click Next.![]() Read where to restrict traffic in the Device Security portal and then click Enable.
Read where to restrict traffic in the Device Security portal and then click Enable.![]() Restrict IoT devices.As stated in step 3/3 of the Enable Traffic Restriction panel, there are three places in the Device Security portal where you can restrict network traffic: vulnerability instances on a Vulnerability Details page, a Security Alert Details page, and a Device Details page. Each place, or point of restriction, is described below.Although only an owner can enable and disable the ability to restrict network traffic, either an owner or an administrator can use the feature to impose a restriction on a device or release one from restriction. For more information about user roles, see Create Device Security Users.Vulnerability Instance as the Point of RestrictionTo restrict one or more IoT devices on the Vulnerability Details page, click VulnerabilitiesVulnerability OverviewAll Vulnerabilities and then click a vulnerability name.If the Confidence Level column is hidden, click the Columns icon () and select it. Select one or more vulnerability instances with a high confidence score of 90 or above and then click MoreRestrict Traffic.
Restrict IoT devices.As stated in step 3/3 of the Enable Traffic Restriction panel, there are three places in the Device Security portal where you can restrict network traffic: vulnerability instances on a Vulnerability Details page, a Security Alert Details page, and a Device Details page. Each place, or point of restriction, is described below.Although only an owner can enable and disable the ability to restrict network traffic, either an owner or an administrator can use the feature to impose a restriction on a device or release one from restriction. For more information about user roles, see Create Device Security Users.Vulnerability Instance as the Point of RestrictionTo restrict one or more IoT devices on the Vulnerability Details page, click VulnerabilitiesVulnerability OverviewAll Vulnerabilities and then click a vulnerability name.If the Confidence Level column is hidden, click the Columns icon () and select it. Select one or more vulnerability instances with a high confidence score of 90 or above and then click MoreRestrict Traffic.![]() Review the list of vulnerable or potentially vulnerable devices whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.
Review the list of vulnerable or potentially vulnerable devices whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.![]() The entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic. A new entry appears in the Vulnerability Responses column. Hover your cursor over the entry to see a history of actions taken.
The entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic. A new entry appears in the Vulnerability Responses column. Hover your cursor over the entry to see a history of actions taken.![]()
![]() The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. If you hover your cursor over the label, a pop-up appears with the time and point of restriction and a link to a vulnerability, security alert, or device details page. In this case, it would be a link to a Vulnerability Details page. The pop-up also includes any notes you made.Security Alert as the Point of RestrictionTo restrict an IoT device with a specific security alert, click AlertsSecurity AlertsAll Alerts and then click an alert name. On the Alert Details page, click ActionRestrict Traffic.
The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. If you hover your cursor over the label, a pop-up appears with the time and point of restriction and a link to a vulnerability, security alert, or device details page. In this case, it would be a link to a Vulnerability Details page. The pop-up also includes any notes you made.Security Alert as the Point of RestrictionTo restrict an IoT device with a specific security alert, click AlertsSecurity AlertsAll Alerts and then click an alert name. On the Alert Details page, click ActionRestrict Traffic.![]() If the confidence score of the impacted device is below 90, the following message appears. The confidence score appears in the Impacted Device section on the Alert Details page.
If the confidence score of the impacted device is below 90, the following message appears. The confidence score appears in the Impacted Device section on the Alert Details page.![]() If the confidence score is 90 or above, the Restrict Traffic dialog box appears.
If the confidence score is 90 or above, the Restrict Traffic dialog box appears.![]() Review the device whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.A new label appears at the top of the Alert Details page stating Traffic Restricted Yes and a new entry appears in the Alert Events column.
Review the device whose traffic will be restricted, optionally add a note for future reference, and then click Confirm.A new label appears at the top of the Alert Details page stating Traffic Restricted Yes and a new entry appears in the Alert Events column.![]() The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to a Security Alert Details page; and any notes you made.IoT Device Details as the Point of RestrictionTo restrict a single IoT device on the Device Details page, click AssetsDevices and then the name of one of the devices in the inventory table. In the Identity section at the top of the Device Details page, click the Action icon (three vertical dots) Restrict Traffic.
The Device Details page for the traffic-restricted device adds a Restricted Device label next to the device name. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to a Security Alert Details page; and any notes you made.IoT Device Details as the Point of RestrictionTo restrict a single IoT device on the Device Details page, click AssetsDevices and then the name of one of the devices in the inventory table. In the Identity section at the top of the Device Details page, click the Action icon (three vertical dots) Restrict Traffic.![]() Check that the device whose traffic will be restricted is correct, optionally add a note for future reference, and then click Confirm.
Check that the device whose traffic will be restricted is correct, optionally add a note for future reference, and then click Confirm.![]() The Device Security portal adds a Restricted Device label next to the device name on the Device Details page. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to the same Device Details page you’re already on; and any notes you made.On the Devices page, the entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic in the Traffic section.
The Device Security portal adds a Restricted Device label next to the device name on the Device Details page. When you hover your cursor over the label, a pop-up appears with the time you started restricting traffic; a link to the point of restriction, which in this case would be to the same Device Details page you’re already on; and any notes you made.On the Devices page, the entry for this device in the Restricted Traffic column changes from No to Yes, indicating that its traffic is being restricted. If you don’t see the Restricted Traffic column, click the Columns icon () and select Restricted Traffic in the Traffic section.![]()
![]() After investigating and remediating a traffic-restricted device, derestrict traffic for it.To derestrict traffic for a device, repeat the same process as you did to restrict traffic but click Derestrict Traffic.You can derestrict multiple vulnerability instances in bulk. Select one or more instances on the Vulnerability Details page and then click MoreDerestrict Traffic.For other traffic-restricted devices, view the inventory on the Devices page with the Restricted Traffic filter applied. Then click device names one by one to open the Device Details page for each one and click the Action icon (three vertical dots) Derestrict Traffic.
After investigating and remediating a traffic-restricted device, derestrict traffic for it.To derestrict traffic for a device, repeat the same process as you did to restrict traffic but click Derestrict Traffic.You can derestrict multiple vulnerability instances in bulk. Select one or more instances on the Vulnerability Details page and then click MoreDerestrict Traffic.For other traffic-restricted devices, view the inventory on the Devices page with the Restricted Traffic filter applied. Then click device names one by one to open the Device Details page for each one and click the Action icon (three vertical dots) Derestrict Traffic.