Next-Generation Firewall
New Features in November 2023
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
New Features in November 2023
These are the new features introduced in November 2023 for AIOps for NGFW Free, and
for AIOps for NGFW Premium.
These are the new features introduced in November 2023 for AIOps for NGFW Free, and for
AIOps for NGFW Premium (use Strata Cloud Manager app). AIOps for NGFW Premium updates
include new features to support Cloud Management for NGFWs. See New Features in November 2023 in Strata Cloud
Manager to review the latest feature updates for all the products supported
with Strata Cloud Manager.
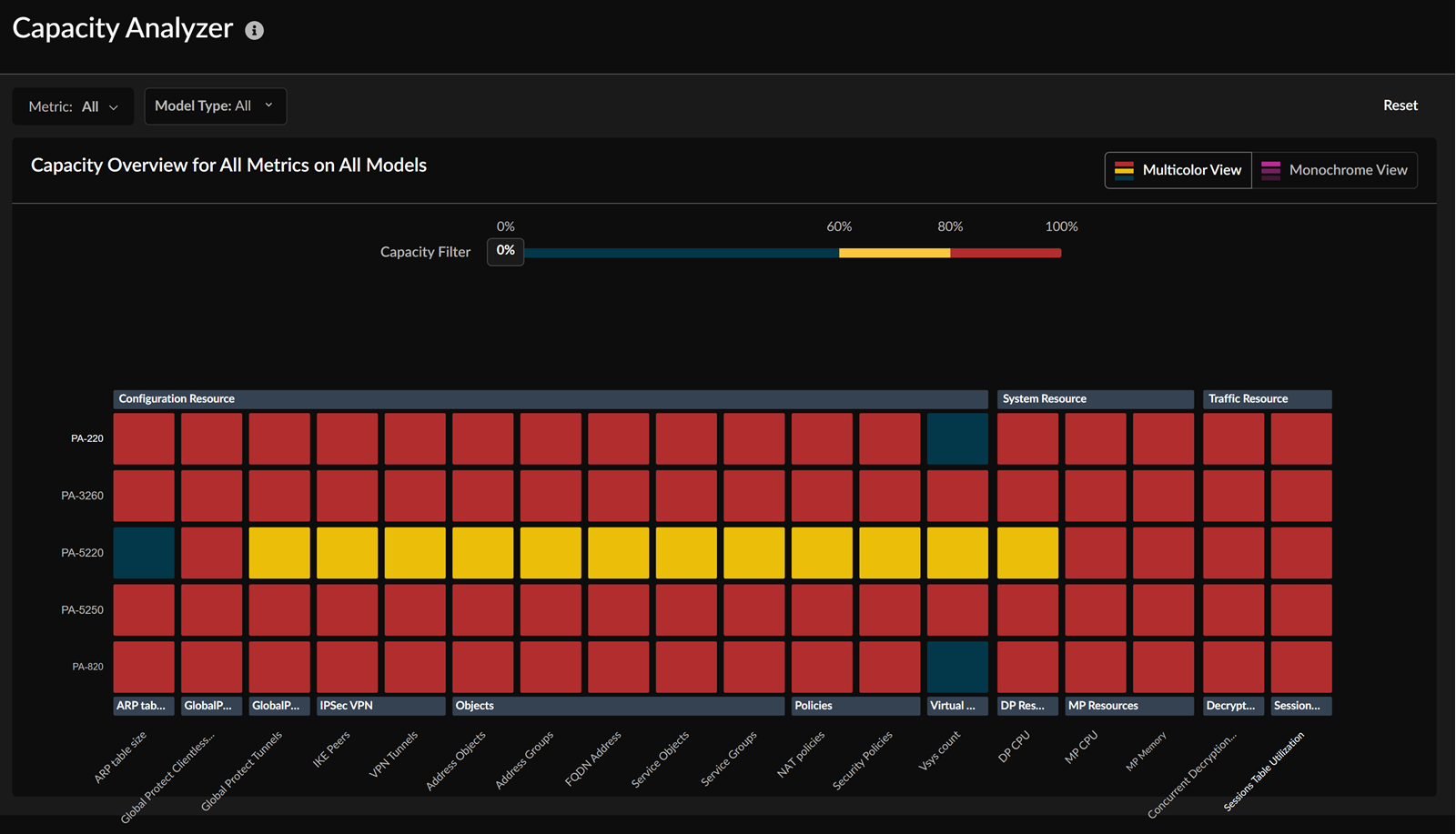
Cloud Management for NGFWs: Capacity Analyzer Alerts
|
November 20, 2023
Capacity Analyzer has been enhanced to include support for
alerts, assisting you in the following:
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Sometimes, you can encounter a predicament where particular features on
your Next-Generation Firewalls (NGFW) approach their capacity thresholds, resulting
in diminished system performance and operational disruptions. Dealing with
capacity-related issues can be time-consuming, and unfortunately, these issues tend
to come to light only after the limits are breached.
The Capacity Analyzer feature allows
monitoring of device resource capacity by tracking metrics usage based on model
types. This feature includes a heatmap visualization to display resource consumption
rates and locations for each metric. It also enables planning for upgrading to
higher capacity firewalls based on specific needs. This proactive approach ensures
that you know about potential capacity constraints, allowing you to take preemptive
action to safeguard your business operations.
AIOps for NGFW Premium: Application Name Update
|
November 8, 2023
This application tile name change to Strata Cloud Manager applies
only to AIOps for NGFW premium instances. AIOps for NGFW Free
remains a standalone app.
|
The application tile names on the hub for Prisma Access, Prisma SD-WAN, and
AIOps for NGFW (the premium app only) are now changed to Strata Cloud
Manager. With this update, the application URL has also changed to stratacloudmanager.paloaltonetworks.com, and
you’ll also now see the Strata Cloud Manager logo on the left navigation
pane.

Moving forward, continue using the Strata Cloud Manager app to manage and
monitor your deployments.
Cloud Management for NGFWs: IPSec VPN Monitoring
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
You can now view the status of the IPSec VPN tunnels
to know whether or not valid IKE and IPSec SAs have been established, and whether
the tunnel interface is up and available for passing traffic.
Because the tunnel interface is a logical interface, it can’t indicate a
physical link status. Therefore, you must use IPSec tunnel monitoring so that the
tunnel interface can verify connectivity to an IP address and determine if the path
is still usable. If the IP address is unreachable, the firewall will either wait for
the tunnel to recover or failover. When a failover occurs, the existing tunnel is
torn down, and routing changes are triggered to set up a new tunnel and redirect
traffic.
With the IPSec VPN tunnel monitoring feature, you can view the tunnel status:
- VPN cluster tunnel status
- IPSec tunnel status
- IKE gateway status
- VPN tunnel status
View the overall status of all the IPSec tunnels, IPSec tunnel status per device, and
detailed status of each IPSec tunnel.
Cloud Management for NGFWs: PA-450R Next-Generation Firewall Support
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
Introduced with PAN-OS 11.1
|
The PA-450R is a new rugged firewall appliance
that upgrades the PA-220R firewall. The PA-450R is designed for industrial,
commercial, and government deployments. The hardware is suited for installation in
harsh environments with extreme temperatures and high humidity levels.
The PA-450R is supported on PAN-OS 11.1 and later versions. The
firewall features two SFP/RJ-45 combo ports and six RJ-45 ports. The RJ-45 ports
include two fail-open ports that can be configured to provide a pass-through
connection in the event of a power failure.
The PA-450R is powered by DC power and optionally supports power
redundancy. The device has a fanless design and can be installed on a flat surface,
wall, and equipment rack. The hardware is compliant with ICS/SCADA system
architecture.
Cloud Management for NGFWs: PA-5445 Next-Generation Firewall
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
Introduced with PAN-OS 11.1
|
The PA-5445 adds the highest performance fixed
form-factor model to the Palo Alto Networks® Next-Generation Firewall lineup. This
firewall, supported on PAN-OS 11.1 and later versions, features hardware resources
dedicated to networking, security, signature matching, and management. The PA-5445
is ideal for deployments in enterprise data centers, headquarters, and regional
offices.
The PA-5445 has the highest App-ID speed (93Gbps), L7 threat
inspection rate (70Gbps), and session count (48M) in a fixed form-factor
firewall.
The PA-5445 features eight RJ-45 ports, twelve SFP+ ports, four
SFP28 ports, and four form-factor pluggable QSFP28 ports that support breakout mode.
The firewall also features dedicated HSCI and HA1 ports for high availability
control.
The PA-5445 can be powered by AC or DC power supplies and
optionally supports power redundancy. The hardware takes up 2RU of rack space and
should be mounted in a 19” equipment rack.
Cloud Management for NGFWs: VM-Series Device Management
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
Introduced with PAN-OS 11.1
|
This release adds support for a bootstrapping process that allows you to configure
newly deployed firewalls without manually configuring them prior to deployment.
Previously, a firewall image was created for your cloud environments that required
you to manually include information such as DNS entries and IP addresses in the
init.cfg file.
This new process associates the firewall with a Panorama management host to automate
the onboarding and configuration of your software firewall. With this functionality,
the bootstrapping process:
- Automatically instantiates, onboards, and configures the firewall instance without prior knowledge of the firewall serial number.
- Automatically onboards the Strata Cloud Manager tenant, from which the tenant receives the initial configuration and becomes fully operational without manual intervention.
Create the bootstrap package with the following fields:
- panorama-server. Use this field to specify cloud management for your Panorama host. This field initiates a TLS connection to the Strata Cloud Manager service edge. For example, panorama-server=cloud. Values other than cloud are interpreted as a Panorama Internet Protocol or FQDN, and will initiate a Panorama management connection. A value defined for panorama-server-2 is ignored when panorama-server=cloud.
- dgname. This field is used to define the Cloud Management folder in which the firewall is mapped.
- vm-series-auto-registration-pin-id. Include the VM-Series registration PIN ID. This automates the process of instantiating the firewall instance by establishing the connection to the Strata Cloud Manager service edge.
- vm-series-auto-registration-pin-value. Include the VM-Series
registration PIN VALUE to automate the process of instantiating the firewall
instance by establishing the connection to the Strata Cloud Manager service
edge.The PIN ID and PIN VALUE fields are use to request a Thermite certificate. This certificate is used to authenticate the device and build a secure connection to the cloud service, such as Strata Cloud Manager.
Cloud Management for NGFWs: IP Protocol Scan Protection
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
Introduced with PAN-OS 11.1
|
Palo Alto Networks now offers reconnaissance protection for IP protocol
scans. IP protocol scans cycle through IP protocol numbers to determine the IP
protocols and services supported by target machines. Malicious actors use this
scanning technique to identify and exploit open and insecure protocols. This feature
enables your firewall to detect and block, allow, or alert on these scans. For
example, you can configure the firewall to drop subsequent packets from a host
exhibiting behavior consistent with IP protocol scans.
You can configure protection against IP protocol scans in the Reconnaissance
Protection settings of a Zone Protection profile. The firewall identifies IP
protocol scans based on the specified number of scan events that occurs within a
specified interval. If necessary, you can exclude the IP addresses of trusted
internal groups performing vulnerability testing from reconnaissance protection.
Details of each detected scan are available in the Threat logs.
Cloud Management for NGFWs: TLSv1.3 Support for SSL/TLS Service Profiles (Administrative Access)
|
November 7, 2023
Supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
Introduced with PAN-OS 11.1
|
You can now configure TLSv1.3 in SSL/TLS service profiles to secure
administrative access to management interfaces. TLSv1.3 delivers several performance
and security enhancements, including shorter SSL/TLS handshakes and more secure
cipher suites. In an SSL/TLS service profile, you can select TLSv1.3 as the minimum
or maximum supported protocol version for connections to the management interface.
Selecting TLSv1.3 automatically enables the following TLSv1.3 cipher suites:
-
TLS-AES-128-GCM-SHA256
-
TLS-AES-256-GCM-SHA384
-
TLS-CHACHA20-POLY1305-SHA256TLS-CHACHA20-POLY1305-SHA256 is not supported in FIPS-CC mode.
However, you can deselect any key exchange algorithms, encryption algorithms,
or authentication algorithms as needed. In addition to offering TLSv1.3 support, SSL/TLS
service profiles now enable customization of the key exchange algorithms, encryption
algorithms, and authentication algorithms supported.
