Set Up File Blocking
Table of Contents
End-of-Life (EoL)
Set Up File Blocking
File
Blocking Profiles allow you to identify specific file types
that you want to want to block or monitor. For most traffic (including
traffic on your internal network), block files that are known to
carry threats or that have no real use case for upload/download.
Currently, these include batch files, DLLs, Java class files, help
files, Windows shortcuts (.lnk), and BitTorrent files. Additionally,
to provide drive-by download protection, allow download/upload of
executables and archive files (.zip and .rar), but force users to
acknowledge that they are transferring a file so that they notice
that the browser is attempting to download something they were not
aware of. For policy rules that allow general web browsing, be stricter
with your file blocking because the risk of users unknowingly downloading
malicious files is much higher. For this type of traffic, attach
a more strict file blocking profile that also blocks portable executable
(PE) files.
You can define your own custom File Blocking profiles
or choose one of the following predefined profiles when applying
file blocking to a Security policy rule. You can clone and edit
the predefined profiles, which are available with content release
version 653 and later, and then follow File Blocking profile safe transition
steps to preserve application availability as you transition
to best practice file blocking settings:
- basic file blocking—Attach this profile to the Security policy rules that allow traffic to and from less sensitive applications to block files that are commonly included in malware attack campaigns or that have no real use case for upload/download. This profile blocks upload and download of PE files ( .scr, .cpl, .dll, .ocx, .pif, .exe) , Java files (.class, .jar), Help files (.chm, .hlp) and other potentially malicious file types, including .vbe, .hta, .wsf, .torrent, .7z, .rar, .bat. Additionally, it prompts users to acknowledge when they attempt to download encrypted-rar or encrypted-zip files. This rule alerts on all other file types to give you complete visibility into all file types coming in and out of your network.
- strict file blocking—Use this stricter profile on the Security policy rules that allow access to your most sensitive applications. This profile blocks the same file types as the other profile, and additionally blocks flash, .tar, multi-level encoding, .cab, .msi, encrypted-rar, and encrypted-zip files.
These
predefined profiles are designed to provide the most secure posture
for your network. However, if you have business-critical applications
that rely on some of the applications that are blocked in these
default profiles, you can clone the profiles and modify them as
necessary. Make sure you only use the modified profiles for those
users who need to upload and/or download a risky file type. Additionally,
to reduce your attack surface, make sure you are using other security
measures to ensure that the files your users are uploading and downloading
do not pose a threat to your organization. For example, if you must
allow download of PE files, make sure you are sending all unknown PE files to WildFire foranalysis.
Additionally, maintain a strict URL filtering policy to ensure that
users cannot download content from web sites that have been known
to host malicious content.
- Create the file blocking profile.
- Select ObjectsSecurity ProfilesFile Blocking and Add a profile.Enter a Name for the file blocking profile such as Block_EXE.(Optional) Enter a Description, such as Block users from downloading exe files from websites.(Optional) Specify that the profile is Shared with:
- Every virtual system (vsys) on a multi-vsys firewall—If cleared (disabled), the profile is available only to the Virtual System selected in the Objects tab.
- Every device group on Panorama—If cleared (disabled), the profile is available only to the Device Group selected in the Objects tab.
(Optional—Panorama only) Select Disable override to prevent administrators from overriding the settings of this file blocking profile in device groups that inherit the profile. This selection is cleared by default, which means administrators can override the settings for any device group that inherits the profile.Configure the file blocking options.- Add and define a rule for the profile.Enter a Name for the rule, such as BlockEXE.Select Any or specify one or more specific Applications for filtering, such as web-browsing.Only web browsers can display the response page (continue prompt) that allows users to confirm their Choosing any other application results in blocked traffic for those applications because there is no prompt displayed to allow users to continue.Select Any or specify one or more specific File Types, such as exe.Specify the Direction, such as download.Specify the Action (alert, block, or continue). For example, select continue to prompt users for confirmation before they are allowed to download an executable (.exe) file. Alternatively, you could block the specified files or you could configure the firewall to simply trigger an alert when a user downloads an executable file.Click OK to save the profile.Apply the file blocking profile to a security policy rule.
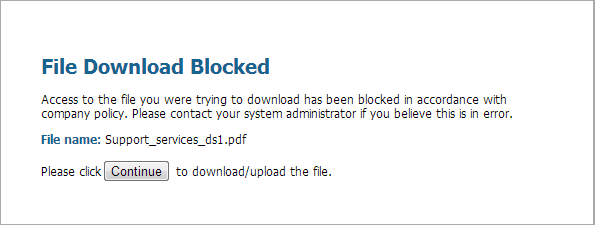
- Select PoliciesSecurity and either select an existing policy rule or Add a new rule as described in Set Up a Basic Security Policy.On the Actions tab, select the file blocking profile you configured in the previous step. In this example, the profile name is Block_EXE.Commit your configuration.To test your file blocking configuration, access an endpoint PC in the trust zone of the firewall and attempt to download an executable file from a website in the untrust zone; a response page should display. Click Continue to confirm that you can download the file. You can also set other actions, such as alert or block, which do not provide an option for the user to continue the download. The following shows the default response page for File Blocking:
![]() (Optional) Define custom file blocking response pages (DeviceResponse Pages). This allows you to provide more information to users when they see a response page. You can include information such as company policy information and contact information for a Helpdesk.When you create a file blocking profile with the continue action, you can choose only the web-browsing application. If you choose any other application, traffic that matches the security policy will not flow through the firewall because users are not prompted with an option to continue. Additionally, you need to configure and enable a decryption policy for HTTPS websites.Check your logs to determine the application used when you test this feature. For example, if you are using Microsoft SharePoint to download files, even though you are using a web-browser to access the site, the application is actually sharepoint-base, or sharepoint-document. (It can help to set the application type to Any for testing.)
(Optional) Define custom file blocking response pages (DeviceResponse Pages). This allows you to provide more information to users when they see a response page. You can include information such as company policy information and contact information for a Helpdesk.When you create a file blocking profile with the continue action, you can choose only the web-browsing application. If you choose any other application, traffic that matches the security policy will not flow through the firewall because users are not prompted with an option to continue. Additionally, you need to configure and enable a decryption policy for HTTPS websites.Check your logs to determine the application used when you test this feature. For example, if you are using Microsoft SharePoint to download files, even though you are using a web-browser to access the site, the application is actually sharepoint-base, or sharepoint-document. (It can help to set the application type to Any for testing.)