Troubleshoot Unsupported Cipher Suites
Table of Contents
End-of-Life (EoL)
Troubleshoot Unsupported Cipher Suites
Find issues with unsupported cipher suites so you can
decide whether to allow the traffic by excluding it from decryption.
Identifying and troubleshooting unsupported
cipher suites in the Decryption log is an aspect of version error investigation
that is worth examining on its own.
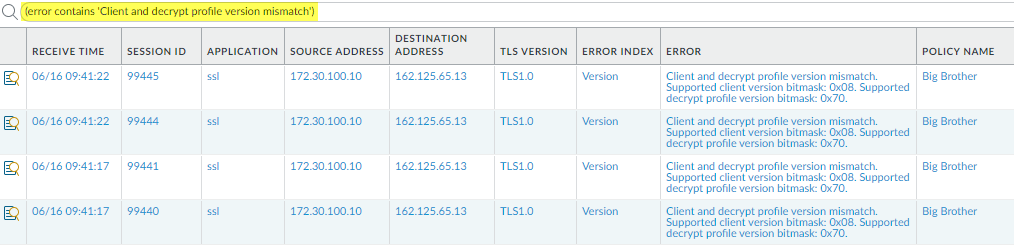
- In the Decryption log (MonitorLogsDecryption), use the query (error contains ‘Client and decrypt profile mismatch’ to identify all cipher suite version mismatches.Filtering the logs for these mismatches identifies finds all instances where the client and the Decryption profile cipher suite support don’t match.
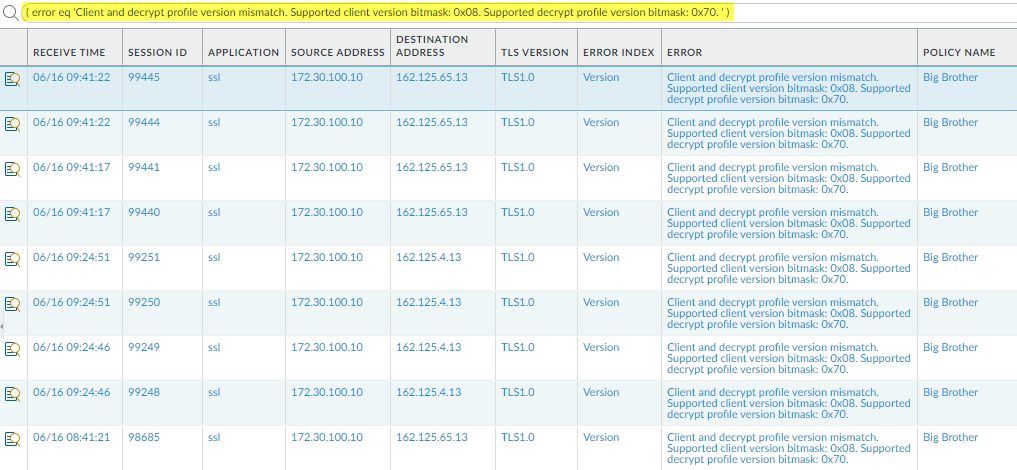
![]() To find all Decryption sessions that experienced the same error, click the error message to add it to the query and remove the original query, for example:
To find all Decryption sessions that experienced the same error, click the error message to add it to the query and remove the original query, for example:![]() The hexadecimal codes identify the exact version that the client supports and the exact version that the Decryption profile supports.Log in to the CLI and look up the bitmask values.The errors show a client and Decryption profile mismatch. The supported client bitmask is 0x08 and the supported Decryption profile bitmask is 0x70:
The hexadecimal codes identify the exact version that the client supports and the exact version that the Decryption profile supports.Log in to the CLI and look up the bitmask values.The errors show a client and Decryption profile mismatch. The supported client bitmask is 0x08 and the supported Decryption profile bitmask is 0x70:admin@vm1>debug dataplane show ssl-decrypt bitmask-version 0x08TLSv1.0
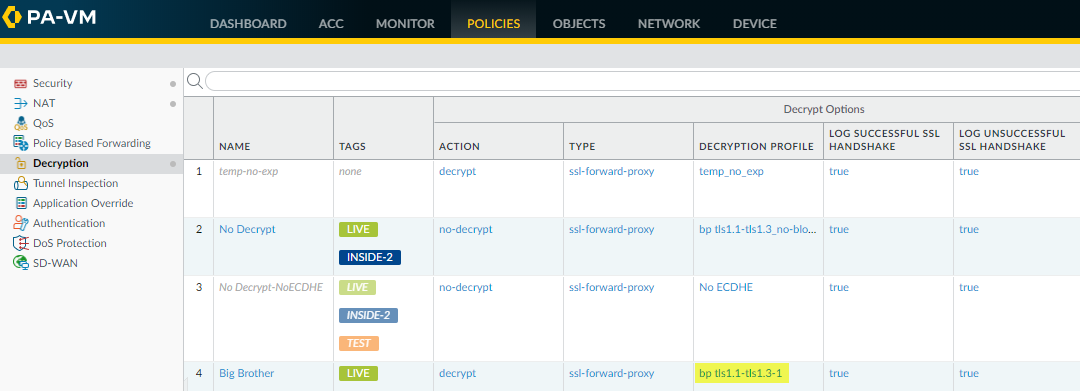
This output shows that the client supports only TLSv1.0.admin@vm1>debug dataplane show ssl-decrypt bitmask-version 0x70TLSv1.1TSLv1.2TLSv1.3This output shows that the Decryption profile supports TLSv1.1, TLSv1.2, and TLSv1.3, but not TLSv1.0. Now you know that the client only supports an old version of the TLS protocol and the Decryption profile attached to the Decryption policy rule that controls the traffic does not allow that version.Decide what action to take.You could update the client so that it accepts a more secure TLS version. If the client requires TLSv1.0 for some reason, you can continue let the firewall continue to block the traffic, or you can update the Decryption profile to allow all TLSv1.0 traffic (not recommended), or you can create a Decryption policy and profile that allow TLSv1.0 and apply it only to the client devices that must use TLSv1.0 and cannot support a more secure protocol (most secure option for allowing the traffic).If you choose to edit the Decryption profile, to find the Decryption policy that controls the session traffic, check the Policy Name column in the log (or click the magnifying glass iconnext to the Decryption log to see the information in the General section of the Detailed Log View).![]()
- In this example, the Decryption policy name is Big Brother; to find the Decryption profile, go to PoliciesDecryption and check the Decryption Profile column.
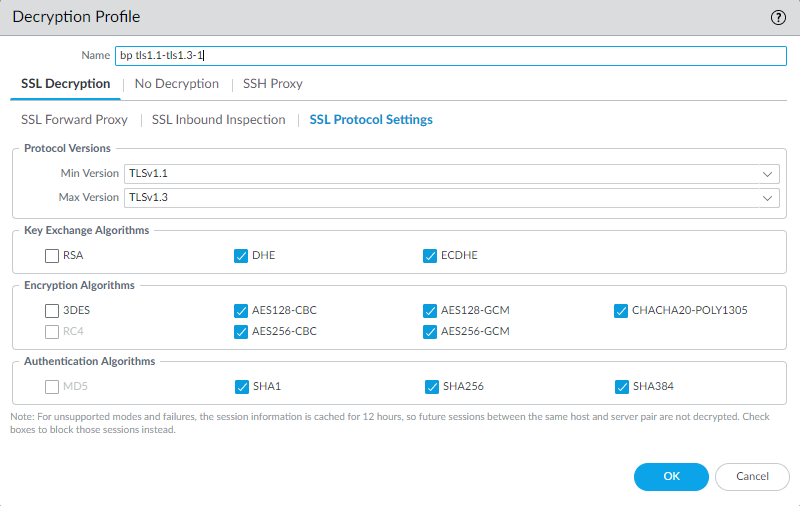
![]() The name of the Decryption profile is bp tls1.1-tls1.3-1. You can also select the Big Brother policy and then select the Options tab to see the name of the Decryption profile.Go to ObjectsDecryptionDecryption Profile, select the appropriate Decryption profile, and edit it to address the version issue.Go to ObjectsDecryptionDecryption Profile.Select the bp tls1.1-tls1.3-1 Decryption profile and click the SSL Protocol Settings tab.
The name of the Decryption profile is bp tls1.1-tls1.3-1. You can also select the Big Brother policy and then select the Options tab to see the name of the Decryption profile.Go to ObjectsDecryptionDecryption Profile, select the appropriate Decryption profile, and edit it to address the version issue.Go to ObjectsDecryptionDecryption Profile.Select the bp tls1.1-tls1.3-1 Decryption profile and click the SSL Protocol Settings tab.![]() The minimum TLS protocol version (Min Version) that the profile supports is TLSv1.1. To allow the traffic that the version mismatch blocks, you could change the Min Version to TLSv1.0. However, a more secure option is to update the client to use a recent TLS protocol version. If you can’t update the client, you can create a Decryption policy and profile that apply only to that user, device, or source address (and to any similar users, devices, or source addresses so that one policy and profile control all of this traffic) instead of applying a general Decryption policy that allows TLSv1.0 traffic.
The minimum TLS protocol version (Min Version) that the profile supports is TLSv1.1. To allow the traffic that the version mismatch blocks, you could change the Min Version to TLSv1.0. However, a more secure option is to update the client to use a recent TLS protocol version. If you can’t update the client, you can create a Decryption policy and profile that apply only to that user, device, or source address (and to any similar users, devices, or source addresses so that one policy and profile control all of this traffic) instead of applying a general Decryption policy that allows TLSv1.0 traffic.