Configure Exemptions for Explicit Proxy Authentication
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
- Cloud Management of NGFWs
- PAN-OS 10.0 (EoL)
- PAN-OS 10.1
- PAN-OS 10.2
- PAN-OS 11.0 (EoL)
- PAN-OS 11.1 & Later
- PAN-OS 9.1 (EoL)
-
- PAN-OS 10.1
- PAN-OS 10.2
- PAN-OS 11.0 (EoL)
- PAN-OS 11.1 & Later
-
-
- Cloud Management and AIOps for NGFW
- PAN-OS 10.0 (EoL)
- PAN-OS 10.1
- PAN-OS 10.2
- PAN-OS 11.0 (EoL)
- PAN-OS 11.1
- PAN-OS 11.2
- PAN-OS 8.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 9.1 (EoL)
Configure Exemptions for Explicit Proxy Authentication
Learn how you can exempt proxy traffic from authentication using a source,
destination, or both.
Using a web proxy allows you to use the
information from the proxy devices in your network through a unified interface.
However, resources such as printers or other IoT devices can't respond to
authentication requests from the proxy or support a certificate or PAC file.
You can exempt these devices from the authentication request from the proxy
using an address object for the source, a custom URL category exception list as the
destination, or both. Configuring an authentication exemption for the explicit proxy
ensures that traffic from these key resources isn't interrupted and allows traffic
from these trusted devices to pass through the proxy in compliance with your network
architecture.
You can create up to 20 web proxy
exemptions in your authentication policy.
- If you have not already done so, Configure Explicit Proxy then define the type of proxy traffic that you want to exempt from authentication requests.You can exempt traffic based on the source, the destination domain, or both.
- Configure an address object (ObjectsAddresses) that contains the source IP addresses of your trusted devices. The source IP can be an address or address group.
- Configure a custom URL category exception list ( ObjectsCustom ObjectsURL Category) that contains the destination URL domain or domains of the web services you want to allow.
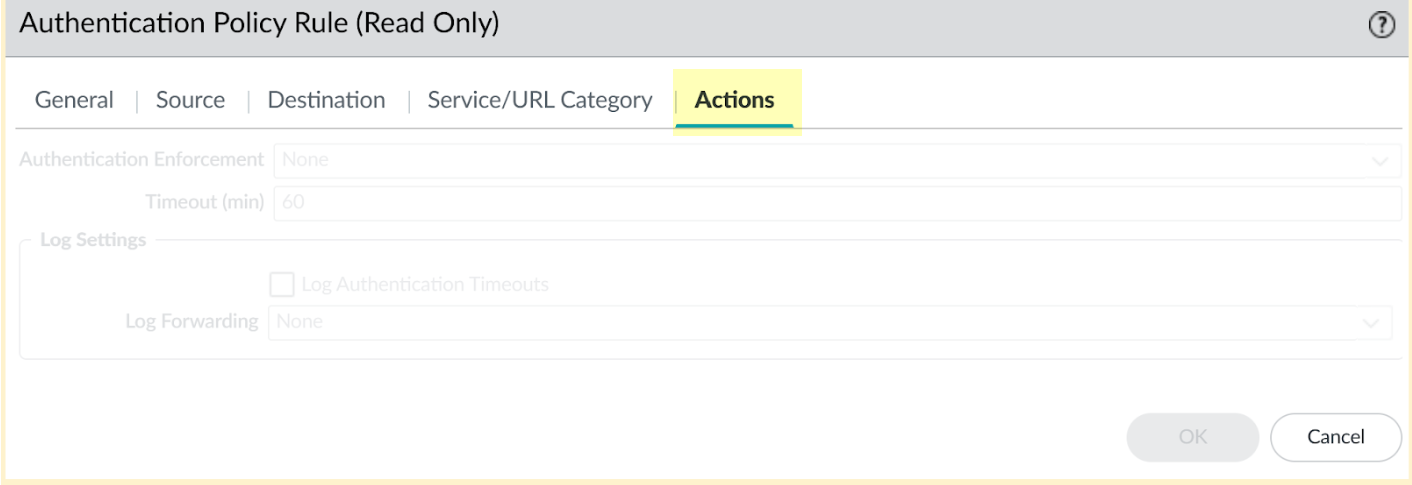
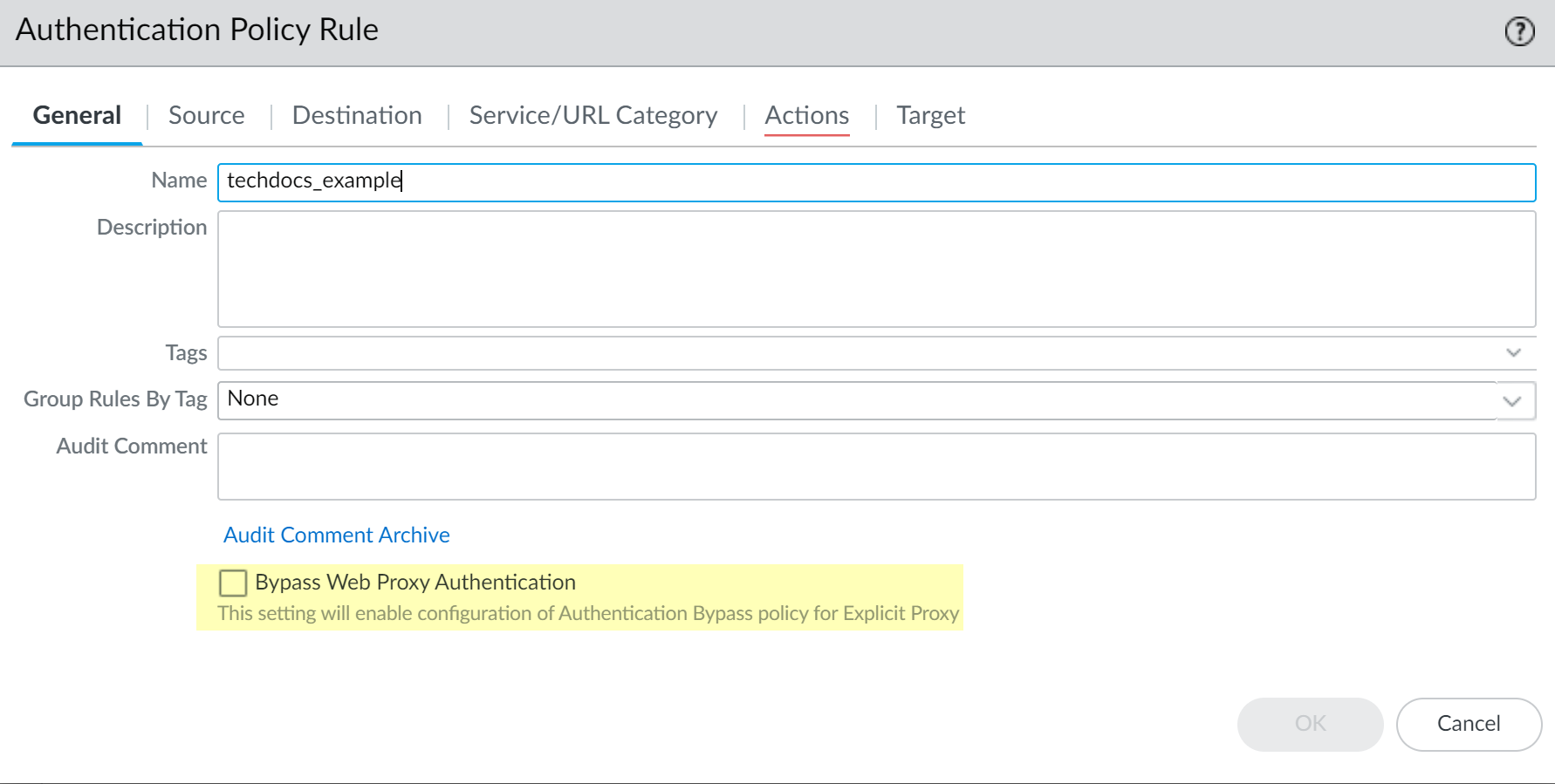
Enable the Authentication Portal if you have not already done so.This step is required to enforce the policy rule.Edit or create your authentication policy rule (PoliciesAuthentication) and select Bypass Web Proxy Authentication.When you enable the Bypass Web Proxy Authentication option, the Authentication Enforcement option on the Action tab is set to None; you cannot change this setting while the Bypass Web Proxy Authentication option is enabled.![]()
![]() Define the type of proxy traffic that you want to exempt from authentication in your authentication policy rule and Commit your changes.You can exempt a source, a destination, or both.
Define the type of proxy traffic that you want to exempt from authentication in your authentication policy rule and Commit your changes.You can exempt a source, a destination, or both.- Select the Source tab then select the address object you configured in the first step as the Source Address and click OK.
- Select the Destination tab then select the URL
category you configured in the first stepYou must create the custom URL category exception list before you can select it as a destination. You can't create a new custom URL category exception list as a destination during this step.
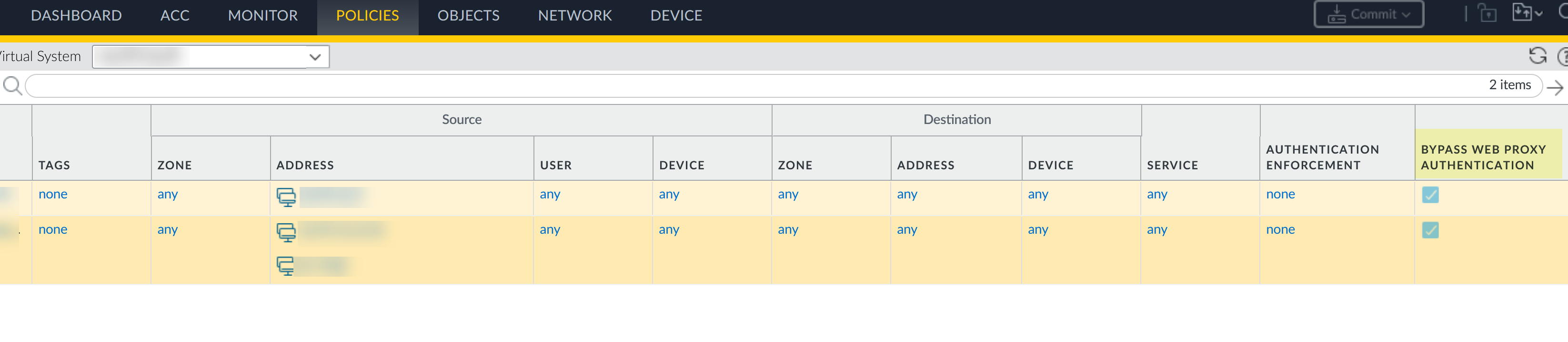
Commit your changes and verify your configuration.- View your policy rules (Policies Authentication) and confirm that a checkmark displays in the Bypass Web Proxy Authentication column for the rules where you enabled the exemption.
![]() Depending on your authentication method, use the CLI commands to view the exemptions for proxy traffic.
Depending on your authentication method, use the CLI commands to view the exemptions for proxy traffic.- If you're using the SAML authentication method, you can use the show counter global name ctd_eproxy_skip_auth_url_match command to verify the configuration. This command displays the number of SAML authentication exemptions for proxy traffic.
- If you're using the Kerberos authentication service type, you can use the show counter global name flow_swg_ep_kerberos_skip_auth command to verify the configuration. This command displays the number of Kerberos authentication exemptions for proxy traffic.