Prisma Access
Dynamic DNS Registration Support for Remote Troubleshooting and Updates
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Dynamic DNS Registration Support for Remote Troubleshooting and Updates
Learn how you can use the dynamic DNS update service with GlobalProtect mobile users
to remotely troubleshoot issues.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
When a mobile user connects remotely to Prisma Access using GlobalProtect Agent,
the GlobalProtect gateway assigns an IP address and endpoint FQDN to the user.
However, Prisma Access does not update the DNS servers in your enterprise with
this information. Since DNS servers don't have the mobile user's assigned IP address
and FQDN information, your IT administrator and the apps in your network can't
identify and update remote endpoints using FQDN.
Using dynamic DNS registration, you can integrate Prisma Access with IP Address
Management (IPAM) vendors to dynamically create A and PTR records in the DNS servers
using nsupdate, offering these benefits:
- Direct integration with leading IPAM vendors such as InfoBlox, BlueCat, and Windows.
- DDNS updates are performed using either transaction signature (TSIG) or Kerberos as the authentication protocol, ensuring secure updates to the DNS database.
- Real-time DDNS updates are done from Prisma Access to the DNS server using batched nsupdate calls based on GlobalProtect connect and disconnect events. These updates use a DDNS service on the Mobile Users Security Processing Node (MU-SPN).
After you set this solution up, you can perform the following actions:
- You can use software tools such as Microsoft Endpoint Configuration Manager (MECM) to push software updates to GlobalProtect endpoints.
- IT and help desk staff can connect and manage the GlobalProtect endpoint using the FQDN of the device.
- You can implement customer applications (such as banking applications) that rely on DNS reverse lookups to allow access from approved GlobalProtect endpoints.
This DDNS solution isn't compatible with the Dynamic DNS Registration Support for Mobile
Users—GlobalProtect solution that uses Strata Logging Service to
push the DDNS updates to the server. If you have the existing solution using Strata Logging Service implemented and then deploy this solution, Prisma Access uses this solution and disables the existing solution using Strata Logging Service.
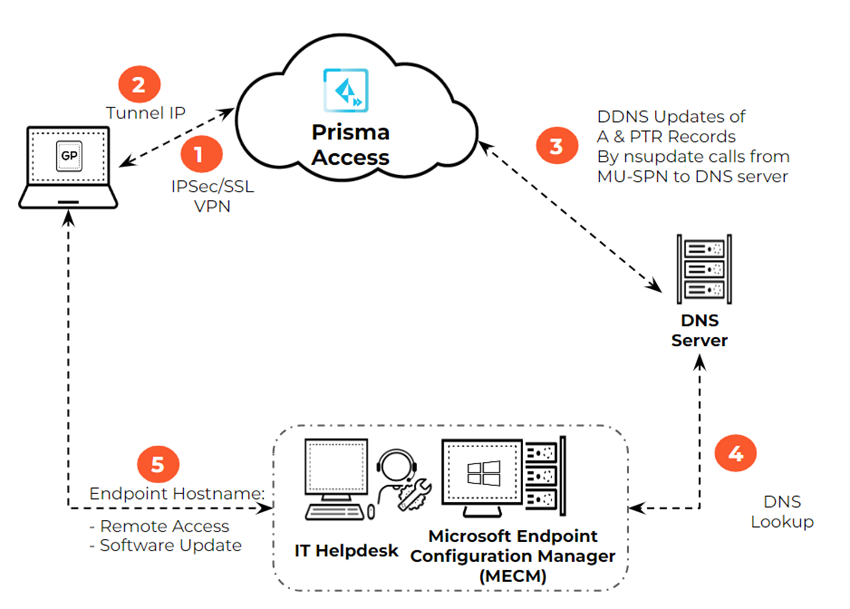
Dynamic DNS Registration Support Use Case
The following diagram illustrates a typical use case for the Prisma Access
DDNS solution. In this example, you want to update GlobalProtect endpoints using
MECM or would like the IT help desk to be able to log in to the GlobalProtect
endpoint remotely for troubleshooting.
- GlobalProtect establishes an SSL tunnel between the GlobalProtect endpoint the Prisma Access gateway.
- GlobalProtect sends the mobile user device’s hostname, domain name, and tunnel IP address information through the tunnel to the on-premises or Prisma Access gateway.
- Prisma Access provides DDNS updates of A and PTR records using nsupdate to the DNS server. Prisma Access provides these secure updates in real-time when it processes login and logout events.
- The IT administrator or an enterprise software uses these records through a DNS or RDNS lookup and resolves the endpoint name or IP address.
- The IT administrator or the endpoint management software uses this information to manage the endpoint or push software updates.
Network Connectivity Requirements
Before you implement this solution, make sure that your network has the following
requirements in place:
- You have added routes to ensure connectivity to the DNS server from the
MU-SPN and from Prisma Access service connections.Do do this, add routes from the Prisma Access Infrastructure Subnet, which you can find in ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessPrisma Access InfrastructureInfrastructure Subnet and the Mobile Users—GlobalProtect IP address pool, which you can find in ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructureClient IP Pool.
- You have established connectivity by creating a service connection between Prisma Access and the IPSec termination device (for example, a next-generation firewall or router) that has connectivity to the DNS server.
- You have made sure that your DNS server is accessible over the service connection IPSec tunnel.
- You have verified that nsupdate commands sent from Prisma Access Mobile
Users—GlobalProtect security processing nodes (SPNs) are allowed and can
reach the DNS server.The steps you perform to achieve this connectivity differ based on the location and the type of the DNS server that is used. For example:
- If the DNS server is in the data center, you can set up connectivity using IPSec tunnels from the Mobile Users—GlobalProtect SPN to service connections, and then from the service connection to the gateway router (for example, a next-generation firewall configured as a VM) behind which the DNS server exists.
- If the DNS server is in the cloud, you can achieve connectivity to the DNS server from the Mobile Users—GlobalProtect SPN using appropriate Security policy rules.
- You have configured forward and reverse lookup zones on the DNS servers.
- You have implemented an Infoblox, Bluecat, or Windows DNS server that supports nsupdate.
- If you maintain permissions for zones individually, make sure that you've created security policy rules to allow nsupdates from devices that have the correct TSIG or Kerberos key.
To configure this solution, use one of the following procedures, based on your
deployment type.
Configure Dynamic DNS Updates for Prisma Access (Managed by Strata Cloud Manager)
Configure dynamic DNS updates for Prisma Access Strata Cloud Manager.
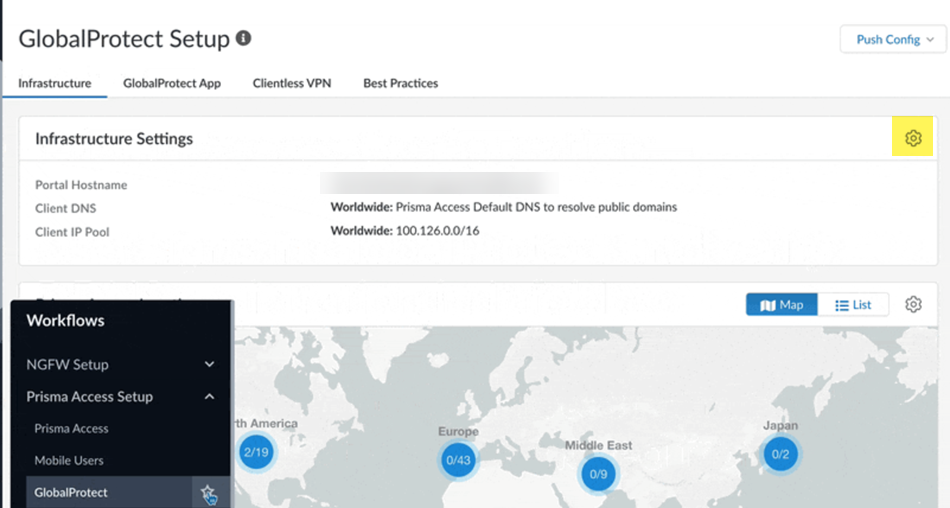
- From Strata Cloud Manager, go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtect and click the gear to edit the Infrastructure Settings.
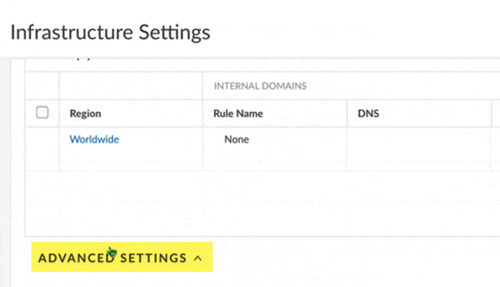
![]() Select Advanced Settings.
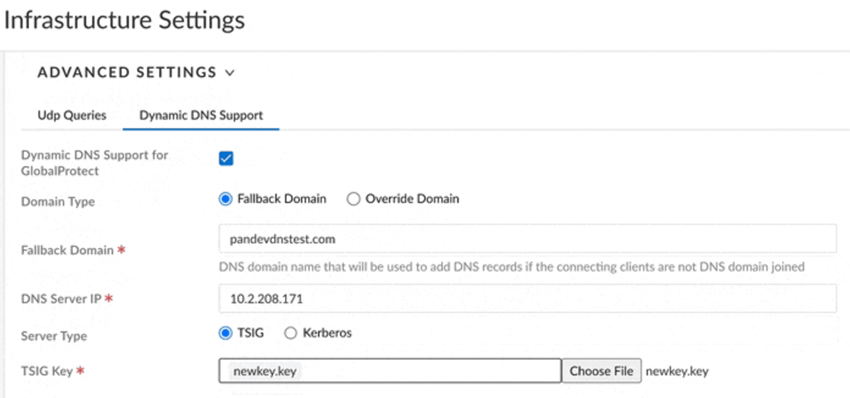
Select Advanced Settings.![]() Configure the Dynamic DNS Support settings.
Configure the Dynamic DNS Support settings.- Select Dynamic DNS Support for GlobalProtect.Select the Domain Type.
- Fallback Domain—The domain used for the
nsupdate events falls back to the domain you specify in the
Fallback Domain area. Use this choice
if the GlobalProtect clients are not joined to any domain, or if
they are domain-joined to the same domain that the DDNS service
uses to update the records on the DNS server. If you select Fallback Domain and users who are not connected to a domain log into GlobalProtect, their information is added under the fallback domain zone that's created on the DNS server.If GlobalProtect clients that are logging in to GlobalProtect belong to an unexpected domain that isn't configured on the DNS server, nsupdate might fail; in this case; select Override Domain to override the unknown domain with the domain that is known to the DNS server.
- Override Domain—Prisma Access uses only the domain you specify to update the DNS server and overrides all other domains. If GlobalProtect clients log in to another domain, the DDNS service uses the domain you specify here to update the DNS A and PTR records.
Select the domain that is used to update the PTR records for either fallback or override domains in the Fallback Domain field.Select the DNS Server IP address.Select the Server Type (either TSIG or Kerberos).(TSIG Deployments Only) Select the TSIG Key to use with TSIG.Make sure that the TSIG file is in the correct format and has a filetype of .key.If you choose a Kerberos authentication type, upload an auth key through a .key file that has the unencoded Kerberos keytab file retrieved from the DNS server.The TSIG file should be in the following format:key "ddns-gp" { algorithm hmac-sha256; secret "aBCDEFGhiJklMNO89PQR+8stUVWX+YZAbcdeFgHI5J="; };(Kerberos Deployments Only) Specify the Kerberos options to use.- Enter the IP address of the Kerberos Domain Controller.
- Enter the IP address of the Kerberos Admin Server.
- Enter the Kerberos User Name.
- Enter the Kerberos Key (the keytab) to
use. Be sure that the Kerberos key is in the correct format.
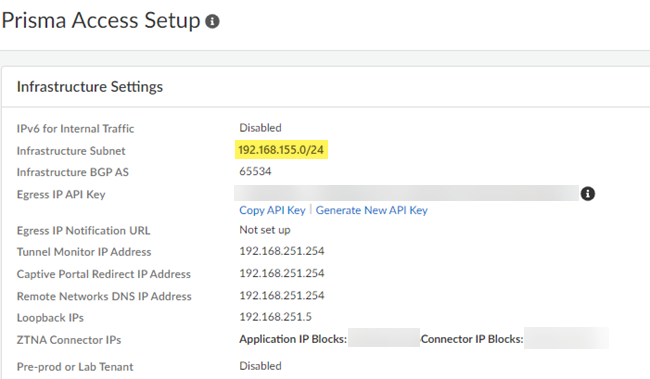
![]() Save your changes.Set up forward lookup and reverse lookup zones on your DNS server.Refer to the documentation for your IPAM vendor to set up these zones. This step requires that you enter the Infrastructure Subnet and Client IP Pool from Prisma Access.
Save your changes.Set up forward lookup and reverse lookup zones on your DNS server.Refer to the documentation for your IPAM vendor to set up these zones. This step requires that you enter the Infrastructure Subnet and Client IP Pool from Prisma Access.- To find the infrastructure subnet, go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessPrisma Access Infrastructure and make a note of the Infrastructure
Subnet.
![]()
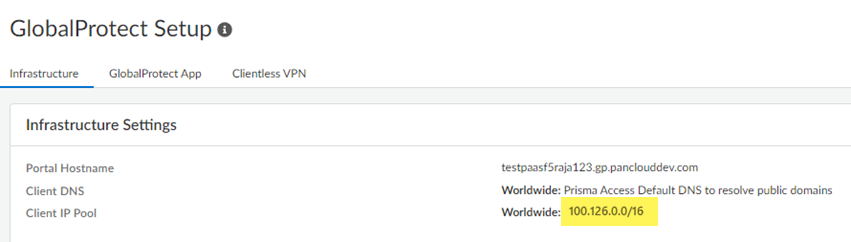
- To find the GlobalProtect mobile user IP address pool, go to
ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtect and make a note of the Client IP
Pool.
![]()
Verify that DNS records are being updated on the IPAM DNS server.- Open a client machine and connect to a Prisma Access GlobalProtect gateway.
![]() Select GlobalProtect Settings and verify the GlobalProtect IP address that Prisma Access assigned to the user.
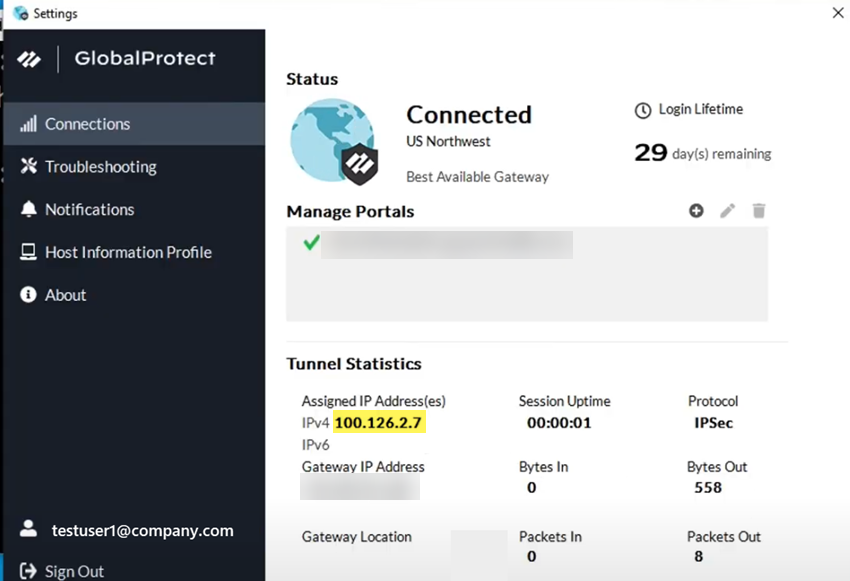
Select GlobalProtect Settings and verify the GlobalProtect IP address that Prisma Access assigned to the user.![]() The Assigned IP Address(es) (100.126.2.7) shows that the IP address comes from the GlobalProtect IP address pool (100.126.0.0/16).
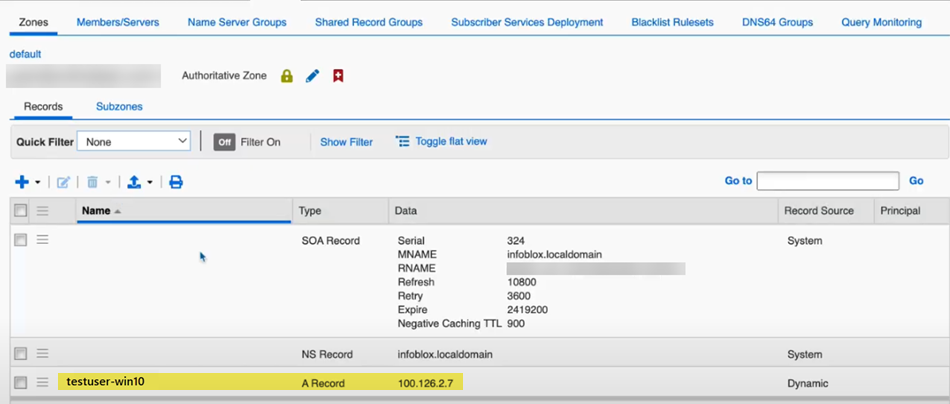
The Assigned IP Address(es) (100.126.2.7) shows that the IP address comes from the GlobalProtect IP address pool (100.126.0.0/16).![]() From the IPAM DNS server, view the user's record.In this example, the user is named testuser1-win10.
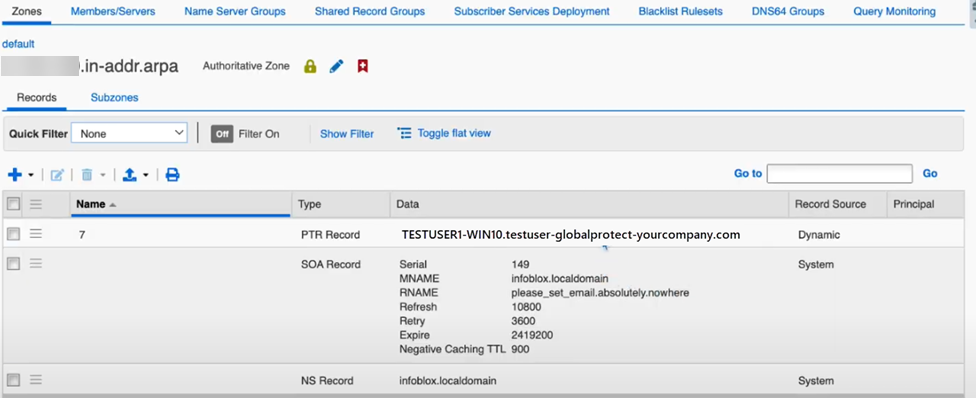
From the IPAM DNS server, view the user's record.In this example, the user is named testuser1-win10.![]() The DNS reverse lookup also displays the username in the PTR record.
The DNS reverse lookup also displays the username in the PTR record.![]() Log the user off from GlobalProtect and check the records to make sure that the DNS server has deleted the records for the user.
Log the user off from GlobalProtect and check the records to make sure that the DNS server has deleted the records for the user.Configure Dynamic DNS Updates for Prisma Access (Managed by Panorama)
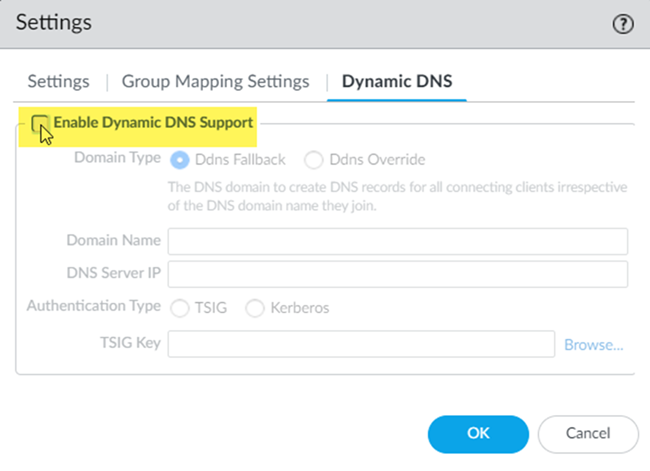
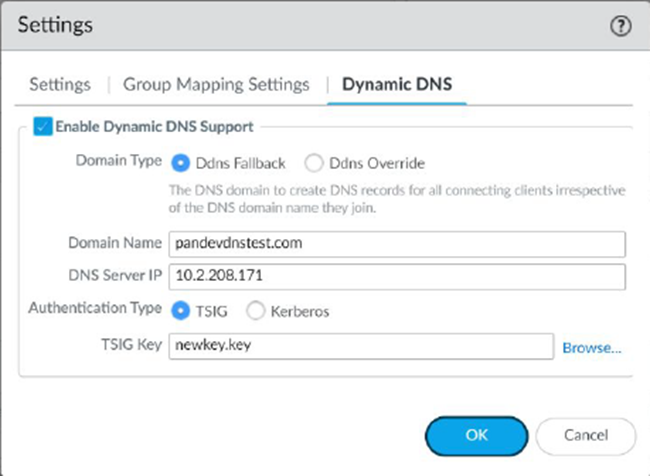
Configure dynamic DNS updates for Prisma Access Strata Cloud Manager.To configure dynamic DNS updates for Prisma Access (Managed by Panorama), complete these steps. - From Panorama, go to Cloud ServicesConfigurationMobile Users—GlobalProtect and click the gear to edit the Settings.Select Dynamic DNS.Enable Dynamic DNS Support.
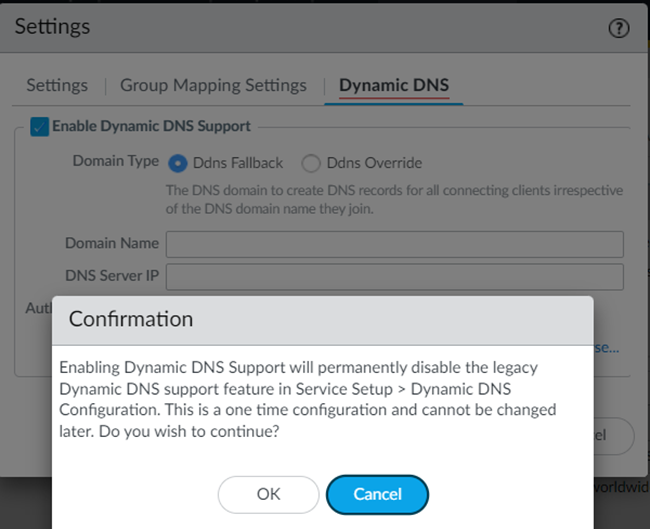
![]() You are prompted that, if you have the legacy Dynamic DNS support enabled, enabling the updated support permanently disables the legacy support. Click OK to continue.
You are prompted that, if you have the legacy Dynamic DNS support enabled, enabling the updated support permanently disables the legacy support. Click OK to continue.![]() Configure the Dynamic DNS settings.
Configure the Dynamic DNS settings.- Select Enable Dynamic DNS Support.Select the Domain Type.
- Ddns Fallback—The domain used for the
nsupdate events falls back to the domain you specify in the
Domain Name area. Use this choice if
the GlobalProtect clients are not joined to any domain, or if
they are domain-joined to the same domain that the DDNS service
uses to update the records on the DNS server. If you select Ddns Fallback and users who are not connected to a domain log into GlobalProtect, their information is added under the Ddns Fallback zone that's created on the DNS server.If GlobalProtect clients that are logging in to GlobalProtect belong to an unexpected domain that isn't configured on the DNS server, nsupdate might fail; in this case; select Ddns Override to override the unknown domain with the domain that is known to the DNS server.
- Ddns Override—Prisma Access uses only the domain you specify to update the DNS server and overrides all other domains. If GlobalProtect clients log in to another domain, the DDNS service uses the domain you specify here to update the DNS A and PTR records.
Select the domain that is used to update the PTR records for either fallback or Domain Names in the Domain Name field.Select the DNS Server IP address.Select the Authentication Type (either TSIG or Kerberos).(TSIG Deployments Only) Select the TSIG Key to use with TSIG.Make sure that the TSIG file is in the correct format and has a filetype of .key.- If you are running a Panorama Managed deployment with a plugin version of 5.2.0 version or greater and you choose a Kerberos authentication type, upload an auth key through a .key file that has the base64 encoded string of the Kerberos key retrieved from the DNS server, for example: "ABCDEFGHIJKLMNOPQRSTUV5WXYZOUy5DT00ADUFabcDluaXN0cmF0b3IAAAABAAAAAAEAEgAg3aBcdE3Fg4IAaQOWMUpzN4hCtNnVcrjbFndYPQVvYVg=
- If you are running a Panorama Managed deployment with a plugin version less than 5.1.0 and you choose a Kerberos authentication type, upload an auth key through a .key file that has the unencoded Kerberos keytab file retrieved from the DNS server.
The TSIG file should be in the following format:key "ddns-gp" { algorithm hmac-sha256; secret "aBCDEFGhiJklMNO89PQR+8stUVWX+YZAbcdeFgHI5J="; };(Kerberos Deployments Only) Specify the Kerberos options to use.- Enter the IP address of the Kerberos Domain Controller.
- Enter the IP address of the Kerberos Admin Server.
- Enter the Kerberos User Name.
- Enter the Kerberos Key (the keytab) to
use. Use base64 encoding on the Kerberos key before uploading it.
![]() Save your changes.Set up forward lookup and reverse lookup zones on your DNS server.Refer to the documentation for your IPAM vendor to set up these zones. This step requires that you enter the Infrastructure Subnet and Client IP Pool from Prisma Access.
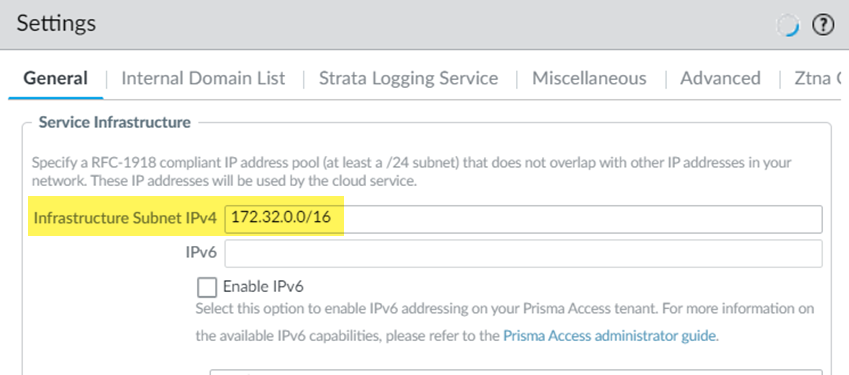
Save your changes.Set up forward lookup and reverse lookup zones on your DNS server.Refer to the documentation for your IPAM vendor to set up these zones. This step requires that you enter the Infrastructure Subnet and Client IP Pool from Prisma Access.- To find the infrastructure subnet, go to PanoramaCloud ServicesConfigurationService Setup, click the gear to edit the
Settings and make a note of the
Infrastructure Subnet IPv4.
![]()
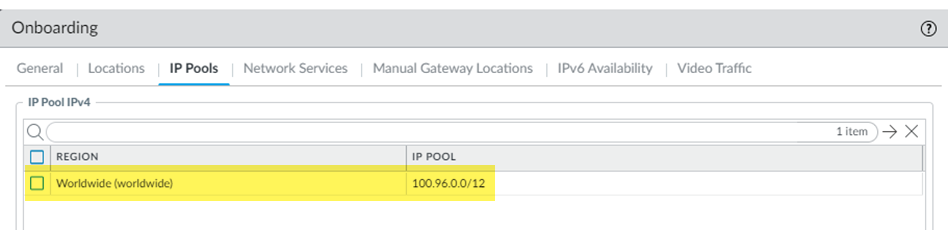
- To find the GlobalProtect mobile user IP address pool, go to PanoramaCloud ServicesMobile Users—GlobalProtect, select the Hostname, select
IP Pools and make a note of the IP
Pool IPv4.
![]()
Verify that DNS records are being updated on the IPAM DNS server.- Open a client machine and connect to a Prisma Access GlobalProtect gateway.
![]() Select GlobalProtect Settings and verify the GlobalProtect IP address that Prisma Access assigned to the user.
Select GlobalProtect Settings and verify the GlobalProtect IP address that Prisma Access assigned to the user.![]() The Assigned IP Address(es) (100.126.2.7) shows that the IP address comes from the GlobalProtect IP address pool (100.126.0.0/16).
The Assigned IP Address(es) (100.126.2.7) shows that the IP address comes from the GlobalProtect IP address pool (100.126.0.0/16).![]() From the IPAM DNS server, view the user's record.In this example, the user is named testuser1-win10.
From the IPAM DNS server, view the user's record.In this example, the user is named testuser1-win10.![]() The DNS reverse lookup also displays the username in the PTR record.
The DNS reverse lookup also displays the username in the PTR record.![]() Log the user off from GlobalProtect and check the records to make sure that the DNS server has deleted the records for the user.
Log the user off from GlobalProtect and check the records to make sure that the DNS server has deleted the records for the user.