Prisma Access
Configure Proxy Chaining with Blue Coat Proxy
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Proxy Chaining with Blue Coat Proxy
Here's how you configure proxy chaining with Prisma Access
Explicit Proxy and Blue Coat Proxy.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Proxy chaining creates a multihop internet pathway by cascading multiple proxy
servers for an additional layer of security or due to compliance. Each server
forwards your traffic to the next, ultimately reaching the internet. This technique
uses your existing network infrastructure and enables connecting to an upstream
proxy for secure HTTP and HTTPS communication. The integration preserves user
browser settings while enhancing security and control.
Why enterprises use the proxy chaining feature:
- Enhanced Privacy and Anonymity by offering multilayered protection and bypassing geo-restrictions.
- Security and Control by filtering malicious content, spam, and phishing attempts by adding an extra layer of security to the user’s browsing experience.
- Companies can use proxy chaining to enforce internal policy rules by restricting access to certain websites or services based on user roles or locations.
- Instead of deploying a new system, proxy chaining allows you to utilize your existing network infrastructure by connecting to an upstream proxy server for specific tasks. This can be a cost-effective and efficient solution.
Here’s the scenario when customers want to proxy chain the traffic from the
on-premises Blue Coat proxy to the Prisma Access Explicit Proxy. The on-premises
Blue Coat proxy authenticates users and passes the username to Prisma Access
Explicit Proxy using X-Authenticated-User (XAU) header insertion on the Blue Coat
proxy.
The static route and destination NAT for the Explicit Proxy IP addresses are
required in no default route networks.
- Configure Prisma Access.
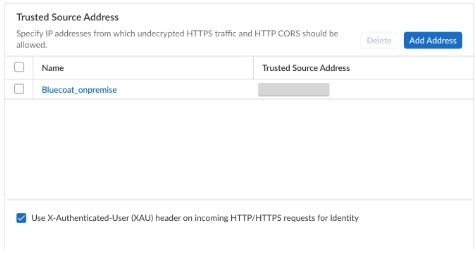
- Set up Explicit Proxy.Add Blue Coat Explicit Proxy as a Trusted Source Address.
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyAdvanced Security SettingsAdd Address.
- Enter the IP address for the Blue Coat Explicit Proxy.You can add either IP addresses or subnets.
- Select Use X-Authenticated-User (XAU) header on incoming HTTP/HTTPS requests for Identity.
![]() Perform configuration on Blue Coat Proxy.
Perform configuration on Blue Coat Proxy.- Enforce authentication.
![]()
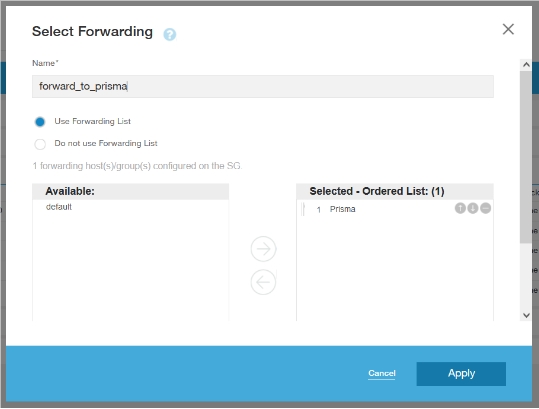
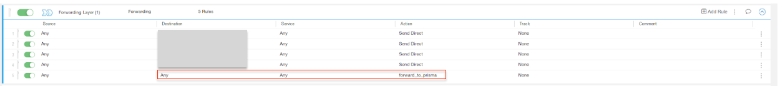
![]() Configure the forwarding layer.
Configure the forwarding layer.![]()
- Obtain the IP address of Prisma Access Explicit
Proxy.
- In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyPrisma Access InfrastructureInfrastructure Settings.
- Copy the Proxy FQDN.
![]()
![]()
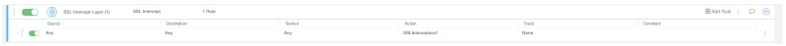
- Enable HTTPS decryption for header insertion.Decryption is mandatory for header insertion.
![]()
![]()
- Configure header forwarding.
![]()
![]()
![]() The client IP address received through the XFF header is simply logged and can't be leveraged for policy.
The client IP address received through the XFF header is simply logged and can't be leveraged for policy. - Set header value encoding to
base64:define action Encode_All_XFF set( request.x_header.X-Authenticated-User, "$(user:encode_base64)" ) end define action x-authenticate set( request.x_header.X-Authenticated-User, "WinNT://($$domain)/($$user):encode_base64" ) end
- Verify the configuration.
- In Strata Cloud Manager, select Log ViewerCheck the X-Forwarded-For and the Users columns to verify that the user and IP address information is visible on Prisma Access.Consider these points:
- The Blue Coat proxy requires authentication and decryption to insert XAU header information.The X-Authenticated-User authentication header value should be in Base64 format.Prisma Access Explicit Proxy can see the user identity for the decrypted traffic.