Prisma Access
Integrate Prisma Access with On-Premises GlobalProtect Gateways
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate Prisma Access with On-Premises GlobalProtect Gateways
Learn how to integrate Prisma Access with On-Premises GlobalProtect gateways.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access enables you to extend the Palo Alto Networks security platform out to
your remote network locations and your mobile users without having to build out your own
global security infrastructure and expand your operational capacity. In cases where you
have already deployed GlobalProtect gateways in regions where you already have the
infrastructure to manage it, you can leverage this investment by configuring Prisma Access to direct mobile users to your existing external gateways when
appropriate.
You can manage priorities for , which allow you to specify priorities for on-premises
and Prisma Access gateways. Administrators cannot specify mobile users to connect to
a specific Prisma Access gateway; however administrators can allow mobile users to manually select
specific using the GlobalProtect app.
You cannot use your own portal with Prisma Access. You can only use the portal
that is deployed when your Prisma Access for mobile users is provisioned.
Integrate Prisma Access with On-Premises GlobalProtect Gateways (Prisma Access (Managed by Strata Cloud Manager))
- Add your on-premises gateway to the list of gateways in the agent configuration.
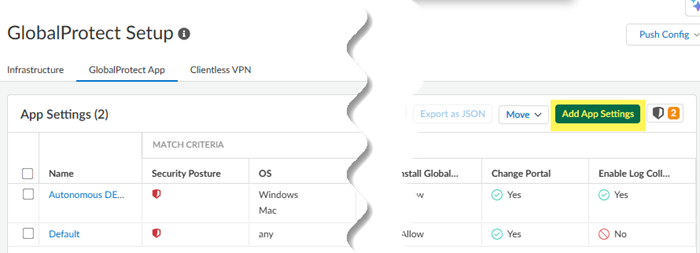
- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtect and select the GlobalProtect App tab.Add App Settings.
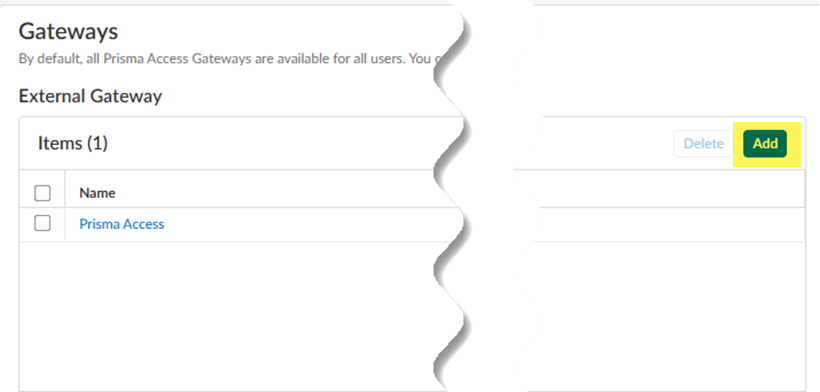
![]() Add an external gateway.
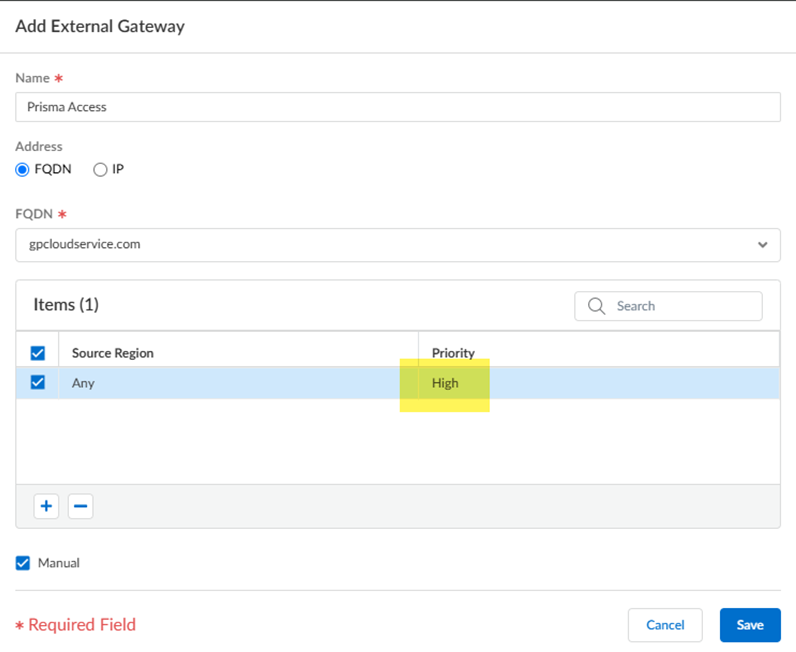
Add an external gateway.![]() If you add a new agent configuration and you want to add the Prisma Access gateways to the list of external gateways in that configuration, you must set the Name to Prisma Access and the Address to gpcloudservice.com. Enter these values exactly as shown, and you can’t use either of these values for non-Prisma Access gateways.Enter the Name of the gateway and specify either the FQDN or IP address of the gateway in the Address field; this value must exactly match the Common Name (CN) in the gateway certificate.(Optional) If you want mobile users to only connect to the gateway when they are in the corresponding region, Add the Source Region to restrict the gateway to. For example, if you have a gateway in France, you would select FR (France). If you have a gateway in Sweden, you would select (SE) Sweden.One benefit of this is that users will then be able to access a gateway that enables access to internet resources in their own language.(Optional) Specify priorities in your gateway configuration.You can set the on-premises gateway to a higher priority, or to a lower priority.
If you add a new agent configuration and you want to add the Prisma Access gateways to the list of external gateways in that configuration, you must set the Name to Prisma Access and the Address to gpcloudservice.com. Enter these values exactly as shown, and you can’t use either of these values for non-Prisma Access gateways.Enter the Name of the gateway and specify either the FQDN or IP address of the gateway in the Address field; this value must exactly match the Common Name (CN) in the gateway certificate.(Optional) If you want mobile users to only connect to the gateway when they are in the corresponding region, Add the Source Region to restrict the gateway to. For example, if you have a gateway in France, you would select FR (France). If you have a gateway in Sweden, you would select (SE) Sweden.One benefit of this is that users will then be able to access a gateway that enables access to internet resources in their own language.(Optional) Specify priorities in your gateway configuration.You can set the on-premises gateway to a higher priority, or to a lower priority.- To set the on-premises gateway to a lower priority than the
default Prisma Access gateway, set the
Priority to
High or
Medium.If you add more gateways and want to set different priorities for each gateway, you can set the Priority to High, Medium, Low, or Lowest.
- To set the on-premises gateway to a higher priority than the
default, set the Priority to
Highest.If you want to set the on-premises gateway to a higher priority, you must also edit the default Prisma Access gateway and set the priority to a Priority that’s lower than Highest.
![]()
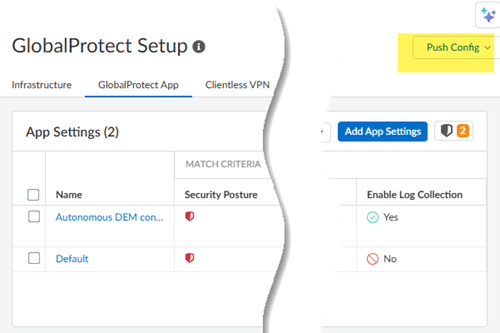
Select Manual.Selecting this check box allows GlobalProtect users to manually select this external gateway in their GlobalProtect app.Save your changes.Push Config.![]()
Integrate Prisma Access with On-Premises GlobalProtect Gateways (Prisma Access (Managed by Panorama)
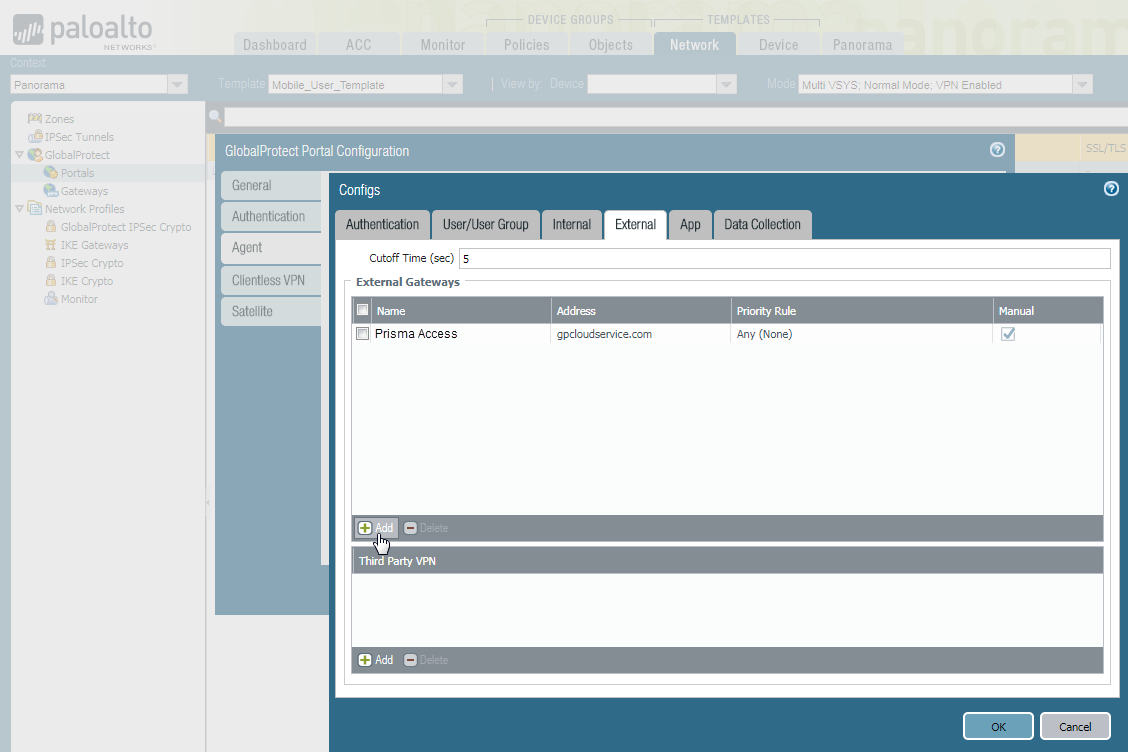
To configure one of these hybrid Prisma Access deployments, you must edit the GlobalProtect_Portal configuration within the Mobile_User_Template to add your on-premises gateways to the appropriate regions.- Edit the Prisma Access portal configuration.
- To add an existing gateway to the list of available gateways, select NetworkGlobalProtectPortals.Select Mobile_User_Template from the Template drop-down.Select GlobalProtect_Portal to edit the Prisma Access portal configuration.Add your on-premises gateway to the list of gateways in the agent configuration.
- Select the Agent tab and select the DEFAULT agent configuration or Add a new one.Select the External tab and Add your on-premises gateway.
![]() If you add a new agent configuration and you want to add the Prisma Access gateways to the list of external gateways in that configuration, you must set the Name to Prisma Access and the Address to gpcloudservice.com. You must enter these values exactly as shown, and you cannot use either of these values for non-Prisma Access gateways.Enter the Name of the gateway and specify either the FQDN or IP address of the gateway in the Address field; this value must exactly match the common name (CN) in the gateway certificate.(Optional) If you want mobile users to only connect to the gateway when they are in the corresponding region, Add the Source Region to restrict the gateway to. For example, if you have a gateway in France, you would select FR (France). If you have a gateway in Sweden, you would select (SE) Sweden.One benefit of this is that users will then be able to access a gateway that enables access to internet resources in their own language.(Optional) Set the priority of the gateway.Configure other agent settings as necessary to complete the agent configuration.Click OK to save the portal configuration.Commit all your changes to Panorama and push the configuration changes to Prisma Access.
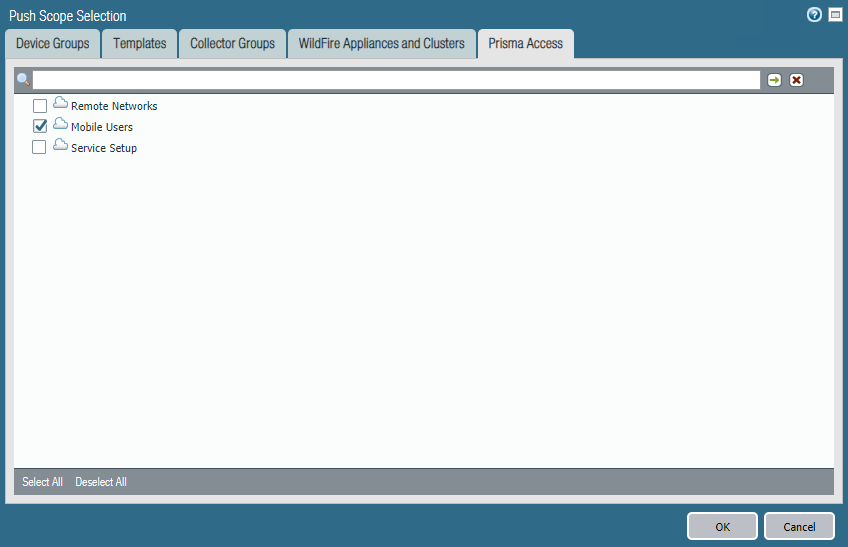
If you add a new agent configuration and you want to add the Prisma Access gateways to the list of external gateways in that configuration, you must set the Name to Prisma Access and the Address to gpcloudservice.com. You must enter these values exactly as shown, and you cannot use either of these values for non-Prisma Access gateways.Enter the Name of the gateway and specify either the FQDN or IP address of the gateway in the Address field; this value must exactly match the common name (CN) in the gateway certificate.(Optional) If you want mobile users to only connect to the gateway when they are in the corresponding region, Add the Source Region to restrict the gateway to. For example, if you have a gateway in France, you would select FR (France). If you have a gateway in Sweden, you would select (SE) Sweden.One benefit of this is that users will then be able to access a gateway that enables access to internet resources in their own language.(Optional) Set the priority of the gateway.Configure other agent settings as necessary to complete the agent configuration.Click OK to save the portal configuration.Commit all your changes to Panorama and push the configuration changes to Prisma Access.- Click CommitCommit to Panorama.Click CommitPush to Devices and click Edit Selections.On the Prisma Access tab, make sure Prisma Access for users is selected and then click OK.
![]() Click Push.
Click Push.