Features in Prisma Access 3.0
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Features in Prisma Access 3.0
This section lists the new features that are available
in Prisma Access 3.0, along with upgrade information and considerations
if you are upgrading from a previous Prisma Access version.
- Cloud Services Plugin 3.0
- Upgrade Considerations for 3.0 Prisma Access Releases
- Determine Your Prisma Access 3.0 Version
- Minimum Required Software Versions
- New Features—Prisma Access 3.0 Preferred
- New Features—Prisma Access 3.0 Innovation
Cloud Services Plugin 3.0
Prisma Access 3.0 uses a single plugin for both 3.0
Preferred or 3.0 Innovation. The version that the plugin activates
is dependent on the dataplane version of Prisma Access 3.0 you are
running.
- Cloud Services Plugin 3.0 Preferred runs on the PAN-OS version 10.0 dataplane, which is the same dataplane as that running on Prisma Access 2.2 Preferred.
- Cloud Services Plugin 3.0 Innovation runs on the PAN-OS 10.1 dataplane and unlocks the latest features available with the PAN-OS 10.1 dataplane, in addition to other new features.
Upgrade Considerations for 3.0 Prisma Access Releases
The following upgrade considerations apply to deployments
upgrading to 3.0 Innovation and Preferred:
- Upgrades to 3.0 Preferred:Prisma Access 2.2 Preferred is a prerequisite for Prisma Access 3.0 Preferred. If your deployment is on an earlier version of Prisma Access, you must first upgrade to Prisma Access 2.2 before you can upgrade to 3.0. Prisma Access will make the 3.0 plugin available to you after your deployment has been upgraded to 2.2 Preferred.Be sure that you have signed up for email alerts in the Prisma Access app. You will receive an email notification via Prisma Access Insights when the 3.0 plugin becomes available to you. Upgrades from 2.0 or 2.1 versions of Prisma Access are not supported.
- Upgrades to 3.0 Innovation:To upgrade to 3.0 Innovation, reach out to your Palo Alto Networks account representative and submit a request. The request will be reviewed internally and, if approved, your deployment will be upgraded to 3.0-Innovation. The upgrade to Prisma Access 3.0 Innovation requires a dataplane upgrade; after the dataplane is fully upgraded, the plugin will be made available to you.
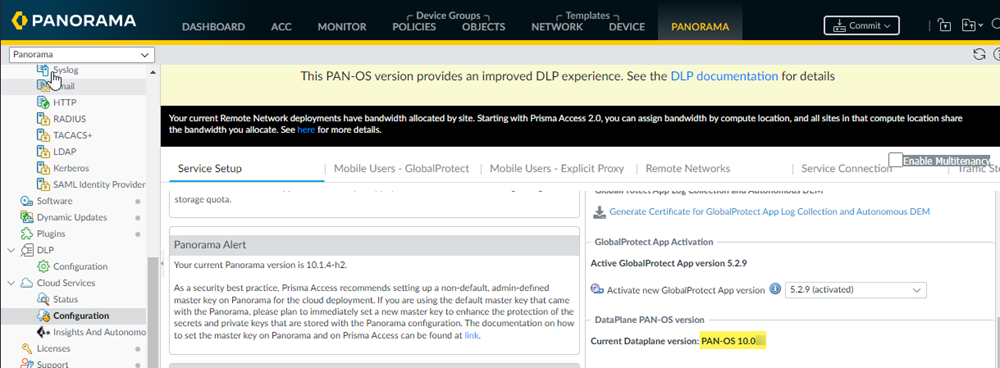
Determine Your Prisma Access 3.0 Version
After you install or upgrade
the Cloud Services plugin, determine the Prisma Access 3.0
version your deployment is running (either Preferred or Innovation)
by selecting PanoramaCloud
ServicesConfigurationService
Setup and viewing the Current
Dataplane version in the DataPlane PAN-OS
version area.
- If the dataplane version is 10.0.x, you are running version 3.0 Preferred.If the dataplane version is 10.1.x, you are running version 3.0 Innovation.
Minimum Required Software Versions
For the minimum Panorama version that is supported with
Prisma Access 3.0, see Prisma Access and Panorama Version
Compatibility in the Palo Alto Networks Compatibility
Matrix.
If you have a Cloud Managed Prisma Access deployment, plugin
upgrades are not required; however, the GlobalProtect versions apply
to both Panorama and Cloud Managed versions of Prisma Access.
Any release later than PAN-OS 10.1
is not supported on Panorama appliances that manage Prisma Access
3.0.
Prisma Access supports any GlobalProtect version that is not End-of-Life (EoL). A minimum GlobalProtect
version of 5.2.6 (5.2.8 recommended) is required to use Autonomous Digital Experience Management
(Autonomous DEM) and a minimum of GlobalProtect 5.2.5 is required for
GlobalProtect App Log Collection for
Troubleshooting.
New Features—Prisma Access 3.0 Preferred
The following table describes the new features that
are available with Prisma Access 3.0 Preferred.
Feature | Description |
|---|---|
| QoS Support for Remote Networks | Prisma Access supports Quality of Service (QoS)
for remote networks that allocate bandwidth by compute
location. If you are using the bandwidth allocation per compute location
model, you can add QoS profiles to prioritize traffic per site. If
you have a deployment that allocates bandwidth by location and uses
QoS, do not migrate to a deployment that allocates bandwidth by
compute location; migrations with QoS are not supported. |
| IP Allow Listing of Prisma Access Public IP Addresses from the Prisma Access UI | You can indicate whether or not you use Prisma
Access public IP addresses for IP allow listing. You can retrieve
the Prisma Access public IP addresses from Panorama (for Panorama Managed
Prisma Access deployment) or the Cloud Managed Prisma Access UI
(for Cloud Managed Prisma Access deployments) for allow listing
purposes. After you make a note of the IP addresses, you add them
to your organization's allow lists, then return to Panorama or the Prisma
Access UI and mark them as added. You can also note any IP addresses
that have not been added to your organization’s allow lists. In this
way, Prisma Access uses only the IP addresses you have added to
your allow lists in case of an autoscale event or infrastructure upgrade. |
| Google IdP Support for Cloud Identity Engine | To simplify the retrieval of user and group information
for deployments that use Google Identity for cloud identity services,
Prisma Access supports Google Identity integration with the Cloud
Identity Engine. |
| Mobile User Regional Redundancy | To ensure that your mobile users always have
access to the services and applications that are accessible from
service connections, you can enable network redundancy during mobile
user setup. This feature provides redundant network paths between
the mobile user dataplane and service connections that may be in
different compute locations. Enabling redundancy provides
you with more resilient access to resources behind service connections
in a data center or headquarters location. Because a service connection
is required for mobile users to access resources from remote networks,
you also have more resiliency in accessing resources in remote network
locations. For either a Cloud Managed or Panorama Managed
Prisma Access deployment, the following prerequisites are required
before this feature is enabled:
|
| Prisma SD-WAN CloudBlade Thin Client Integration with Cloud Services Plugin | For Prisma SD-WAN integrations
with Prisma Access, the Cloud Services plugin includes a built-in
CloudBlade thin client that eliminates the requirement to have a
Docker container host or Kubernetes environment to host a separate
CloudBlade. This integration enables easier onboarding of Prisma SD-WAN
devices using remote network connections. |
| Maximum Size Increase for External Dynamic Lists | To allow you to use existing firewall security
policy rules and related objects with Prisma Access to implement
a consistent security posture across your network, Prisma Access
increases the maximum size for External Dynamic Lists (EDLs) to
the following maximums:
To
activate this feature on your service tenant, reach out to your
Palo Alto Networks account representative and submit a request. |
| Protect from Web-Based Threats with RBI Using Proofpoint | To support a larger range of use cases and prevent
malware, phishing, cryptomining, and other threats, Prisma Access
has added Proofpoint as a technology partner to
implement Remote Browser Isolation (RBI) using URL response page redirect to
the RBI cloud. The RBI integration helps with isolating all active, untrusted
web content from endpoints that your users use to access business-critical
internet services and internal networks, and ensure that the corporate
network remains safe. |
| WildFire India Cloud Support | To allow you to adhere to data sovereignty and
residency laws as well as established data protection and privacy
regulations, Prisma Access supports the use of the WildFire India Cloud
(in.wildfire.paloaltonetworks.com). The following locations map
to the WildFire India Cloud:
|
| WildFire API Support | You can extend the malware detection capabilities
of WildFire using the WildFire API. You can
use the WildFire API to query WildFire for verdicts, samples, and
reports, and to automate the submission of files and links to WildFire
for analysis. |
| Explicit Proxy Enhancements | Prisma Access provides the following enhancements
for Explicit Proxy:
|
| New Prisma Access Compute Locations | To optimize performance, reduce latency, and
adhere to data sovereignty rules, Prisma Access adds the following
compute locations, and the following locations map to these compute
locations:
In addition, the existing Canada
Central compute location is renamed to Canada
Central (Montreal). The Canada East location continues
to be mapped to this compute location. If you add the locations
after you install the Cloud Services 3.0 plugin, Prisma Access associates
the new compute locations automatically. For Explicit
Proxy, these new compute locations are supported for new deployments
only. If you are upgrading from an existing Prisma
Access deployment and you have already onboarded these locations,
complete the following steps to take advantage of the new compute
location:
Since
you need to allow time to delete and add the existing location and
change your allow lists, Palo Alto Networks recommends that you schedule
a compute location change during a maintenance window or during
off-peak hours. |
| EDL Custom Category End Token Support | If you use URLs in custom URL categories or external dynamic lists (EDLs) and
do not append a forward slash (/)
to the URL, it is possible to allow more URLs than you intended. For
example, entering example.com as a matching
URL instead of example.com/ would also match
example.com.website.info or example.com.br. Prisma Access
allows you to set an ending token to URLs in EDLs or custom URL
categories so that, if you enter example.com,
Prisma Access treats it as it would treat example.com/ and only
matches that URL. |
New Features—Prisma Access 3.0 Innovation
Version 3.0 Innovation includes all the features
in 3.0 Preferred and adds the following features.
Feature | Description |
|---|---|
| Support for PAN-OS 10.1 | Cloud Services 3.0 Innovation uses a dataplane
version of PAN-OS 10.1 and you are able to take advantage of PAN-OS
10.1 features up to PAN-OS 10.1, including the following features:
|
| SaaS Security Inline Enforcement | In addition to the SaaS Visibility feature
that was introduced with Prisma Access 2.2 Preferred, you can import SaaS policy recommendations from SaaS Security Inline to
gain control of the applications in the policy recommendation. |
| Commit Error Reporting Improvements | When you receive configuration-related errors
during commits, Prisma Access has replaced generic messages you
previously received with messages that more clearly communicate
the cause of the misconfiguration. For example, authentication objects
without authentication profiles receive a message indicating the
object with the missing profile instead of a generic message indicating
an issue with the commit. Other message improvements include:
|
