SaaS Security
Monitor and Investigate User Activity
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Monitor and Investigate User Activity
Learn how to monitor and investigate user activity across
all assets or a single asset on Data Security.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
On Data Security, you can view user activity
across all assets, depending on your
SaaS app. Using an API integration model, Data Security
connects to each service and retrieves the user activity logs.
- User activity is not the same as Administrator activity.
- Currently, even after you delete users in Identity & Access Management (I&AM), those users continue to remain in the Data Security application dashboard. Synchronizing I&AM database with onboarded applications will happen in the near future.
These
logs enable you to monitor and investigate a variety of actions
taken (activity or events) by your end users, including:
- file and folder downloads
- file and folder uploads
- failed login attempts
- sharing and collaboration
There are two different approaches to monitoring user activity: you can view the details of
monitored users or explore user activities. The work flow you choose depends on your
scope of investigation, but the filters and facets provided to
explore the data are available at all times. Before you begin, however, determine if
any of your SaaS apps have unique user activity requirements. Additionally, you can create a
user activity policies to receive activity alerts.
Monitored Users
Learn how to identify risky users.
Data Security enables you to identify monitored users.
- To view the list of monitored users, select Data SecurityUser & ActivityMonitored Users.(Optional) Apply a Cloud App filter.(Optional) Apply a User Type filter to view whether the user is an Internal or External user.Observe columns for Data Assets Owned and Data Assets Collaborated.Click on the name or email field to view the following:
- Basic Information
- Sanctioned App Access
- Risk Analysis Charts
- Risk Events Trend
- Risky Events
- Risk Trends
(Optional) Click the download icon to export a CSV file with a list of all monitored users and their details.Explore User Activities
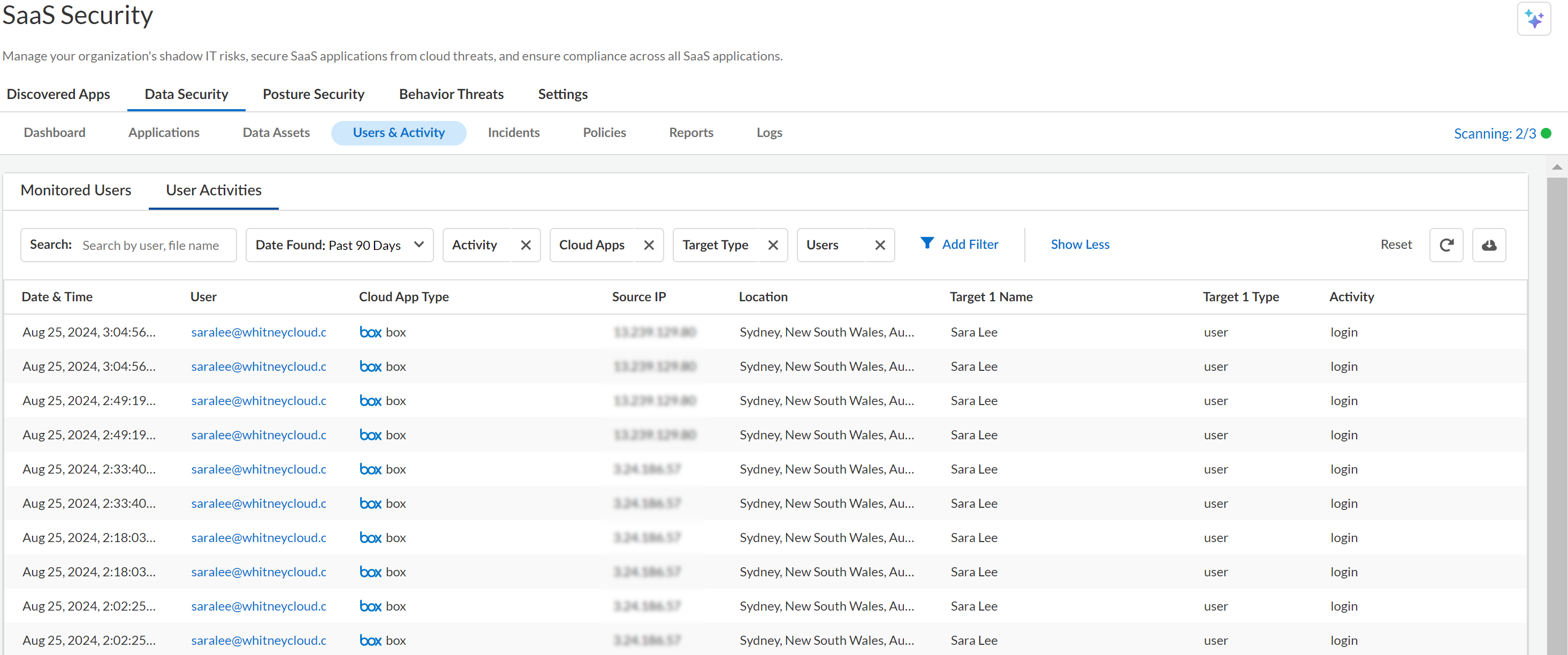
Use the filters and facets provided under User Activities to narrow and expand the results to meet your audit needs. To view User Activities, select Data SecurityUsers & ActivityUser Activities.![]()
- Search—Find an item using part of the filename or find a user by the full email address. Because the user activity logs include information on the email address of the user who logged in, the source IP address and location of the user who performed the action, and the name of the item being modified or created, you can match on a phrase or email address.
- Date—Time frame when the user activity occurred. For example:
- Past 1 hour
- Past 3 hours
- Past 24 hours
- Past 7 days
- Past 30 days
- Past 90 days
- Activity—Activity the user initiated. A total of 36 actions are listed here. For example, download, view, sync, share, upload, delete, and copy a file or folder, login, and so on.
- Cloud Apps—SaaS application on which the user activity occurred. For example, Box.
- Target Type—Location, user, or asset where an activity or change occurred. It allows you to learn about who did what, for example which user initiated an action on a file, space, or folder, or added a user, created a space, performed work on a report, or used the API.
- Users—Users who have performed some activity. Select
the user to view the following:
- Basic Information
- Sanctioned App Access
- Risk Analysis Charts
- Risk Events Trend
- Risky Events
- Risk Trends
User Activity Requirements
Data Security supports user activity, depending on your cloud app. Some cloud apps have unique requirements to enable user activity.SaaS AppRequirementGoogle DriveGoogle Apps Unlimited or Google Apps for Education subscription to enable the retrieval of all event logs. Without this additional subscription, only login and logout events are available to Data Security.SalesforceUser Event Monitoring license to enable the retrieval of all event logs. Without this additional license, only log in and log out events are available to Data Security.Office 365Microsoft TeamsYou must turn on audit logs in Office 365 to record user and administrator activity.