Advanced Threat Prevention Powered by Precision AI®
Learn More About Threat Signatures
Table of Contents
Learn More About Threat Signatures
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Firewall Threat logs record all threats the
firewall detects based on threat signatures (Set Up Antivirus, Anti-Spyware, and Vulnerability Protection)
and the ACC displays an overview of the top threats on your network.
Each event the firewall records includes an ID that identifies the
associated threat signature.
You can use the threat ID found
with a Threat log or ACC entry to:
- Easily check if a threat signature is configured as an exception to your security policy (Create Threat Exceptions).
- Find the latest Threat Vault information about a specific threat. Because the Threat Vault is integrated with the firewall, you can view threat details directly in the firewall context or launch a Threat Vault search in a new browser window for a threat the firewall logged.
If a signature has been
disabled, the signature UTID might be reused for a new signature.
Review
the content update release notes for notifications regarding new
and disabled signatures. Signatures might disabled in cases where:
the activity the signature detects has fallen out of use by attackers,
the signature generated significant false positives, or the signature
was consolidated with other like signatures into a single signature
(signature optimization).
- Confirm the firewall is connected to the Threat Vault.Select DeviceSetupManagement and edit the Logging and Reporting setting to Enable Threat Vault Access. Threat vault access is enabled by default.Find the threat ID for threats the firewall detects.
- To see each threat event the firewall detects based on threat signatures, select MonitorLogsThreat. You can find the ID for a threat entry listed in the ID column, or select the log entry to view log details, including the Threat ID.
- To see an overview of top threats on the network, select ACCThreat Activity and take a look at the Threat Activity widget. The ID column displays the threat ID for each threat displayed.
- To see details for threats that you can configure as threat exceptions (meaning, the firewall enforces the threat differently than the default action defined for the threat signature), select ObjectsSecurity ProfilesAnti-Spyware/Vulnerability Protection. Add or modify a profile and click the Exceptions tab to view configured exceptions. If no exceptions are configured, you can filter for threat signatures or select Show all signatures.
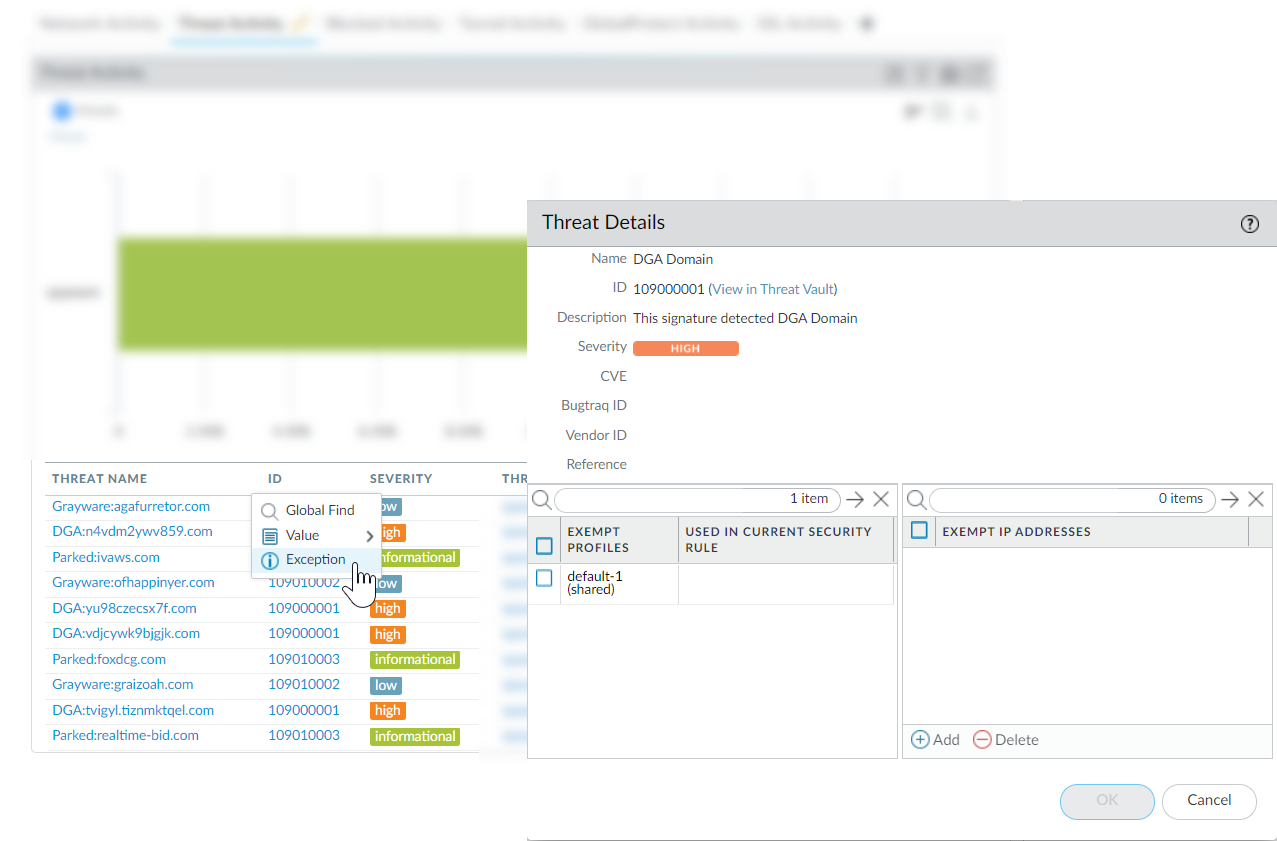
Hover over a Threat Name or the threat ID to open the drop-down, and click Exception to review both the threat details and how the firewall is configured to enforce the threat.For example, find out more about a top threat charted on the ACC:![]() Review the latest Threat Details for the threat and launch a Threat Vault search based on the threat ID.
Review the latest Threat Details for the threat and launch a Threat Vault search based on the threat ID.- Threat details displayed include the latest Threat Vault information for the threat, resources you can use to learn more about the threat, and CVEs associated with the threat.
- Select View in Threat Vault to open a Threat Vault search in a new window and look up the latest information the Palo Alto Networks threat database has for this threat signature.
Check if a threat signature is configured as an exception to your security policy.- If the Used in current security rule column is clear, the firewall is enforcing the threat based on the recommended default signature action (for example, block or alert).
- A checkmark anywhere in the Used in current security rule column indicates that a security policy rule is configured to enforce a non-default action for the threat (for example, allow), based on the associated Exempt Profiles settings.
The Used in security rule column does not indicate if the Security policy rule is enabled, only if the Security policy rule is configured with the threat exception. Select PoliciesSecurity to check if an indicated security policy rule is enabled.Add an IP address on which to filter the threat exception or view existing Exempt IP Addresses.Configure an exempt IP address to enforce a threat exception only when the associated session has either a matching source or destination IP address; for all other sessions, the threat is enforced based on the default signature action.