Advanced WildFire Powered by Precision AI™
View WildFire Appliance Logs and Analysis Reports
Table of Contents
View WildFire Appliance Logs and Analysis Reports
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
WildFire logs contain information on samples (files and email links)
analyzed by WildFire. It includes artifacts, which are properties, activities, or
behaviors associated with the logged event, such as the application type or the IP
address of an attacker as well as WildFire-specific qualities, such as high-level
analysis results including categorization of the sample as malware, phishing,
grayware, or benign and details sample information. Reviewing the WildFire
Submissions logs can also indicate whether a user in your networks downloaded a
suspicious file. The WildFire analysis report displays detailed sample information,
as well as information on targeted users, email header information (if enabled), the
application that delivered the file, and all URLs involved in the
command-and-control activity of the file. It informs you if the file is malicious,
if it modified registry keys, read/wrote into files, created new files, opened
network communication channels, caused application crashes, spawned processes,
downloaded files, or exhibited other malicious behavior.
- Forward Files For WildFire Appliance Analysis.Configure WildFire Submissions Log Settings.To view samples submitted by a firewall to a WildFire public, private, or hybrid cloud, select MonitorLogsWildFire Submissions. When WildFire analysis of a sample is complete, the results are sent back to the firewall that submitted the sample and are accessible in the WildFire Submissions logs. The submission logs include details about a given sample, including the following information:
- The Verdict column indicates whether the sample is benign, malicious, phishing, or grayware.
- The Action column indicates whether the firewall allowed or blocked the sample.
- The Severity column indicates how much of a threat a sample poses to an organization using the following values: critical, high, medium, low, and informational.The values for the following severity levels are determined by a combination of verdict and action values.
- Low—Grayware samples with the action set to allow.
- High—Malicious samples with the action set to allow.
- Informational:
- Benign samples with the action set to allow.
- Samples with any verdict with the action set to block.
![]() For any entry, select the Log Details icon to open a detailed log view for each entry:
For any entry, select the Log Details icon to open a detailed log view for each entry:![]() The detailed log view displays Log Info and the WildFire Analysis Report for the entry. If the firewall has packet captures (PCAPs) enabled, the sample PCAPs are also displayed.
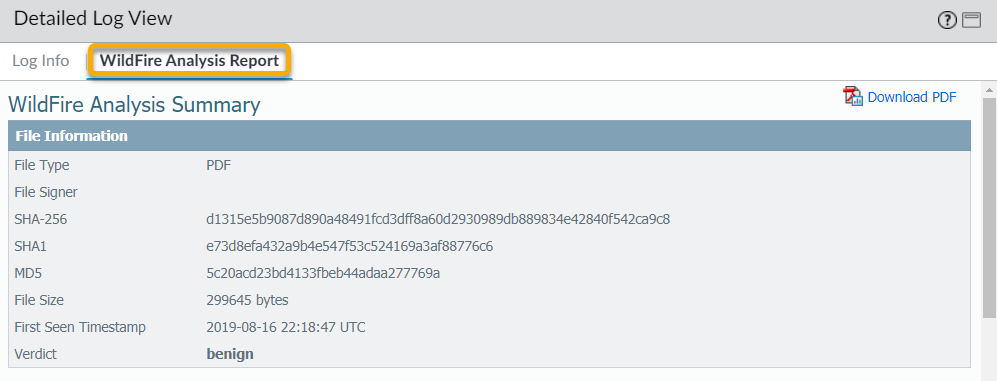
The detailed log view displays Log Info and the WildFire Analysis Report for the entry. If the firewall has packet captures (PCAPs) enabled, the sample PCAPs are also displayed.![]() For all samples, the WildFire analysis report displays file and session details. For malware samples, the WildFire analysis report is extended to include details on the file attributes and behavior that indicated the file was malicious.
For all samples, the WildFire analysis report displays file and session details. For malware samples, the WildFire analysis report is extended to include details on the file attributes and behavior that indicated the file was malicious.![]() (Optional) Download PDF of the WildFire Analysis Report.
(Optional) Download PDF of the WildFire Analysis Report.