Autonomous DEM
Identify When a Security Profile is Blocking User Access
Table of Contents
Expand All
|
Collapse All
Autonomous DEM Docs
-
-
- AI-Powered ADEM
- Autonomous DEM for China
-
-
Identify When a Security Profile is Blocking User Access
Use Access Analyzer to quickly find out whether a security profile is blocking user
access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Use Access Analyzer to quickly determine whether a security profile is hindering or blocking
user access to a resource due to real-time threats identified in specific logs so
that you don't have to manually investigate all logs.
- Start a query for users whose access you’re interested in. For example, the following query allows admins to determine whether a user has hindered or blocked access for a particular application.Can mobile user <name> access <application> from prisma access location <location-name> using device <device name>Access Analyzer supports five Security Profiles subtypes. If Access Analyzer detects a profile block on any of these profile subtypes, it will appear on Access Analyzer's multidomain analysis view on the top of the screen:
- URL Filtering
- WildFire
- Antivirus
- Anti-Spyware
- Vulnerability Protection
You can click on Submit Query to view query results.Analyze the access issue.- If the user is hindered from accessing an application due to a Security Profile, the query results will tell you which profiles attached to which policy rules are hindering user access. For example:
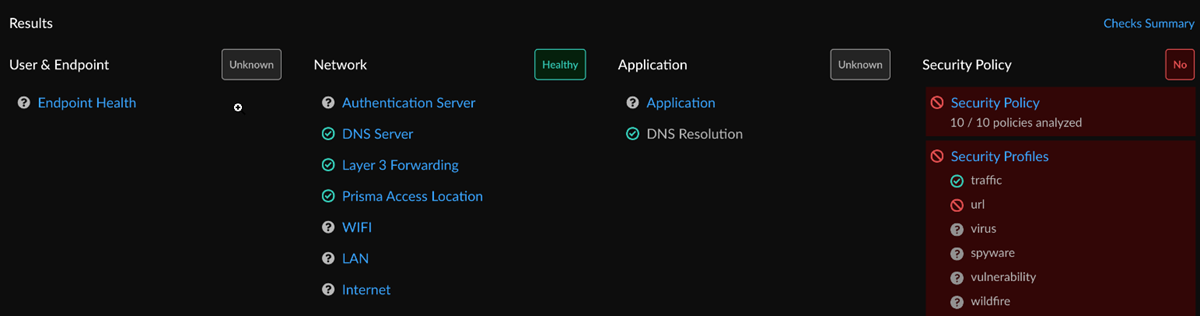
![]() Assess whether a user has hindered access to an application by selecting a query name to view its multidomain analysis. Under Results, you can view User & Endpoint health, Network level, Application Performance level, and Security Policy level.
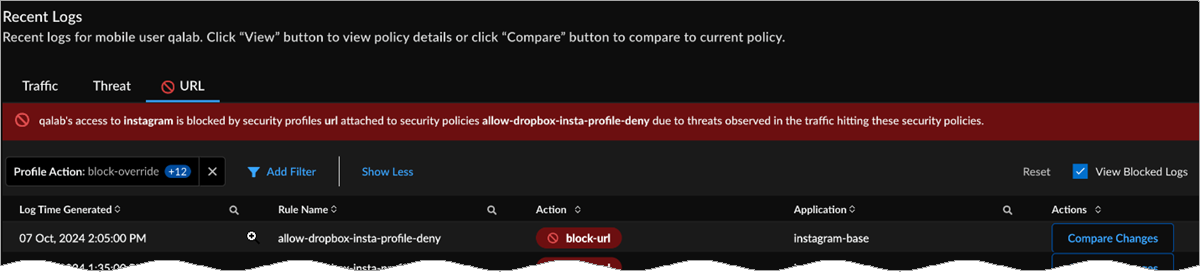
Assess whether a user has hindered access to an application by selecting a query name to view its multidomain analysis. Under Results, you can view User & Endpoint health, Network level, Application Performance level, and Security Policy level.![]() Under Security Profiles, admins can indicate that users were blocked or hindered due to real-time threats identified in the logs. Threat logs indicate real-time threats due to Virus, Vulnerability, Spyware, and WildFire, and URL Logs show hindrances or blocks due to URL Filtering.Click on Security Profiles. If there is a profile block, a block symbol is present next to the log title.Access Analyzer automatically filters the logs according to the Profile Subtype causing the access issue and the Profile Action blocking the traffic. For example, the following image shows these logs were filtered by View Blocked Logs.Under URL, you can view a Security Policy rule, Profile Subtype, Profile Action, and Application. Select Compare Changes to see the differences between the current matched security policy rule and the rule at the time of the log, or select View Details if no changes have been made to the rule.
Under Security Profiles, admins can indicate that users were blocked or hindered due to real-time threats identified in the logs. Threat logs indicate real-time threats due to Virus, Vulnerability, Spyware, and WildFire, and URL Logs show hindrances or blocks due to URL Filtering.Click on Security Profiles. If there is a profile block, a block symbol is present next to the log title.Access Analyzer automatically filters the logs according to the Profile Subtype causing the access issue and the Profile Action blocking the traffic. For example, the following image shows these logs were filtered by View Blocked Logs.Under URL, you can view a Security Policy rule, Profile Subtype, Profile Action, and Application. Select Compare Changes to see the differences between the current matched security policy rule and the rule at the time of the log, or select View Details if no changes have been made to the rule.![]() Based on your findings, you can understand that the user is blocked due to a real-time threat seen in traffic and, if necessary, escalate the issue to a security administrator.
Based on your findings, you can understand that the user is blocked due to a real-time threat seen in traffic and, if necessary, escalate the issue to a security administrator.