Prisma AIRS
Organize Security Scans with Custom Labels
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Organize Security Scans with Custom Labels
Custom Labels enables you to attach arbitrary key-value string labels to model scan
results through SDK/APIs and web interface.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Model Scan Labels provide a foundational organizational capability that empowers security
teams to categorize, manage, and efficiently navigate their scan results through a
flexible custom labeling system. This feature enables you to attach arbitrary key-value
string labels to model scan results through SDK/APIs and web interface, creating
powerful filtering and organizational capabilities that align with their specific
operational needs.
Whether organizing by deployment environment, team ownership, compliance requirements, or
custom workflows, labels offer the metadata structure necessary to manage scan results
at scale. The system supports full CRUD (Create, Read, Update, Delete) operations for
label management and provides advanced filtering capabilities in the web interface,
allowing security teams to structure their scan data according to their organizational
model. Our expanded API suite includes new endpoints and enhanced existing functionality
to support comprehensive label management across all scan operations.
All label APIs follow these validation rules:
| Property | Specification/Validation Rule |
|---|---|
| Label Keys | 1-128 characters, alphanumeric with _ and - allowed |
| Label Values | 1-256 characters, alphanumeric with _ and - allowed |
A maximum of 50 labels can be applied for one scan.
Labels should contain organizational metadata
only (such as, environment, team, and region). Do not include sensitive data such as
PII, credentials, or confidential business information.
- Include Label while Scan Creation
- Add Labels
- Replace Labels
- Remove Labels
- Filter and View Labels
- Scan Filtering using Labels
Include Label while Scan Creation
Include labels during scan creation by providing the labels
parameter.
CreateScan API with Labels
Include labels during scan creation by providing the labels
parameter:
Using CLI
model-security scan \ --security-group-uuid "your-security-group-uuid" \ --model-uri "https://huggingface.co/microsoft/DialoGPT-medium" \ -l env=production \ -l team=ml-platform \ -l region=us-west \ -l compliance=soc2
Using Python
SDK
from uuid import UUID from model_security_client.api import ModelSecurityAPIClient client = ModelSecurityAPIClient( base_url="https://api.sase.paloaltonetworks.com/aims" ) # Scan with labels attached result = client.scan( security_group_uuid=UUID("your-security-group-uuid"), model_uri="https://huggingface.co/microsoft/DialoGPT-medium", labels={ "env": "production", "team": "ml-platform", "region": "us-west", "compliance": "soc2" } ) print(f"Scan {result.uuid} created with labels") print(f"Labels: {result.labels}")
Add Labels
Add new labels or modify existing ones on a scan.
AddLabels API
Add new labels or modify existing ones on a scan. When a label key already exists,
the previous value will be replaced:
Using
CLI
model-security add-labels 550e8400-e29b-41d4-a716-446655440000 \ -l owner=alice \ -l priority=high \ -l reviewed=true
Using Python
SDK
from uuid import UUID scan_uuid = UUID("550e8400-e29b-41d4-a716-446655440000") # Add new labels or update existing ones client.add_scan_labels( scan_uuid=scan_uuid, labels={ "owner": "alice", "priority": "high", "reviewed": "true" } )
Replace Labels
Replace the complete set of existing labels on the scan with the new provided
labels.
SetLabels API
Replace the complete set of existing labels on the scan with the new provided
labels.
Using
CLI
model-security set-labels 550e8400-e29b-41d4-a716-446655440000 \ -l env=staging \ -l version=v2-0 \ -l deployed=false
Using Python
SDK
from uuid import UUID scan_uuid = UUID("550e8400-e29b-41d4-a716-446655440000") # Replace all existing labels client.set_scan_labels( scan_uuid=scan_uuid, labels={ "env": "staging", "version": "v2-0", "deployed": "false" } ) print(f"Labels set for scan {scan_uuid} (all previous labels removed)")
Remove Labels
Remove specific labels from a scan using their keys. Keys that do not exist on the
scan are ignored.
RemoveLabels API
Remove specific labels from a scan using their keys. Keys that do not exist on the
scan are ignored.
Using
CLI
model-security delete-labels 550e8400-e29b-41d4-a716-446655440000 \ -k temporary \ -k draft \ -k old-label
Using Python
SDK
from uuid import UUID scan_uuid = UUID("550e8400-e29b-41d4-a716-446655440000") # Remove specific labels by key client.delete_scan_labels( scan_uuid=scan_uuid, keys=["temporary", "draft", "old-label"] ) print(f"Labels removed from scan {scan_uuid}")
Filter and View Labels
Using Strata Cloud Manager, view the complete set of labels for each scan in the
console.
Using Strata Cloud Manager, view the complete set of labels for each scan in the
console.
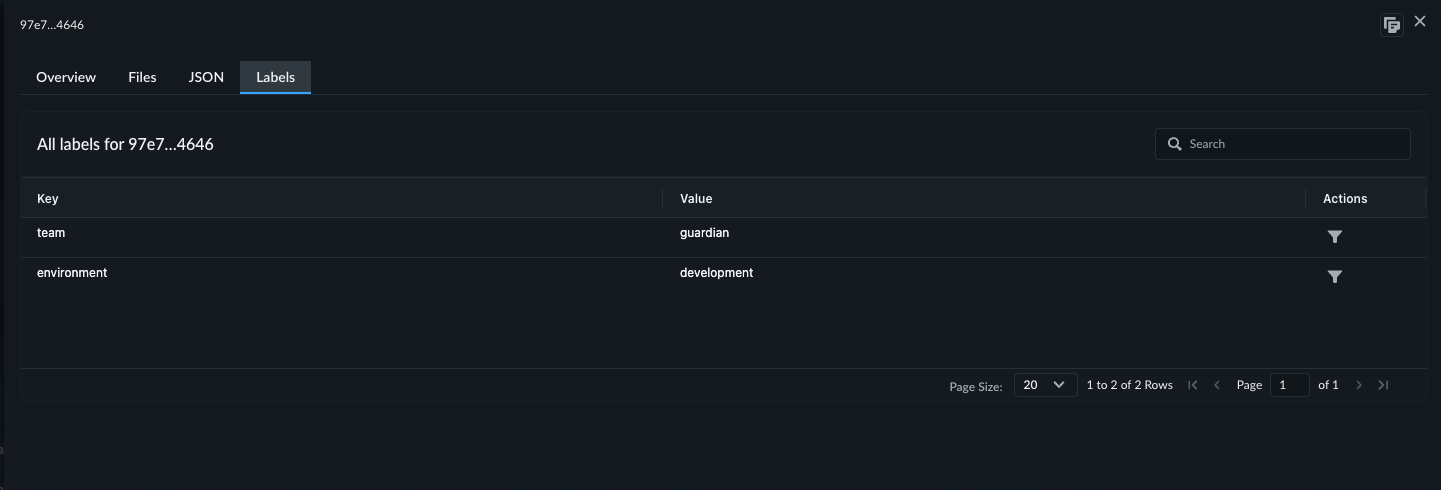
Labels enable advanced scan filtering based on custom attributes. Follow these steps
to filter using labels:
- Login to Strata Cloud Manager.
- Navigate to the AI SecurityAI Model SecurityScans.
- Select Labels filter option.
- Create a list of label criteria to filter by, then select
Done.
![]()
Scan Filtering using Labels
The ListScans API includes a labels_query parameter
that enables scan filtering based on labels.
Using ListScans API with labels_query
The ListScans API includes a labels_query parameter
that enables scan filtering based on labels. This parameter supports AND/OR logic
with grouping functionality.
The labels_query syntax combines label filters with logical
operators.
Label Filters
A label filter follows the format key:value_type where:
- key:value—Match exact key-value pair (for example, env:prod).
- key:*—Match any value for the specified key (for example, env:*)
Operators
Valid operators are:
- AND—Logical AND operation (for example, env:prod AND team:guardian).
- OR—Logical OR operation (for example, env:prod OR env:staging).
- ( )—Single-level grouping for precedence (for example,
(env:prod OR env:staging) AND team:platform).Nested subqueries are not supported (for example, ((env:prod OR env:dev) AND team:ml) OR region:us-west).
Using CLI
model-security list-scans \ --labels-query "(env:production OR env:staging) AND (team:ml-platform OR team:security)"
Using Python
SDK
from model_security_client.api import ModelSecurityAPIClient client = ModelSecurityAPIClient(base_url="https://api.sase.paloaltonetworks.com/aims") # List scans that have a label key 'env' with value 'production' or 'staging' and have a label key 'team' with value 'ml-platform' or 'security' scans = client.list_scans( labels_query="(env:production OR env:staging) AND (team:ml-platform OR team:security)" ) for scan in scans.scans: print(f"Scan {scan.uuid}: {scan.model_uri}") print(f" Labels: {scan.labels}") print(f" Outcome: {scan.eval_outcome}")

