Create Internet-to-Data-Center DoS Protection Policy Rules
Table of Contents
10.1
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
Create Internet-to-Data-Center DoS Protection Policy Rules
Protect your data center web servers and the firewall
from DoS attacks to prevent attackers from taking down your data
center network.
One method attackers use to disrupt a network
is a Denial-of-Service (DoS) attack intended to overwhelm targeted
systems that are connected to the internet, take them down, and
make them unavailable to all of your legitimate users and services.
Data center web servers are an attractive target because taking
them down prevents most legitimate access to the data center.
Protect
the data center web server tier by applying a classified DoS Protection Policy to internet traffic
destined for those servers. A classified DoS Protection policy applies
a classified DoS Protection Profile that controls the
number of incoming connections to the traffic defined in the policy.
In
addition, configure packet buffer protection for
each zone to protect the firewall from single-session DOS attacks
that can overwhelm the firewall’s packet buffer and cause legitimate
traffic to drop, especially on firewalls that protect critical services.
- Create a classified DoS Protection Profile that
protects data center web servers from DoS attacks by limiting the
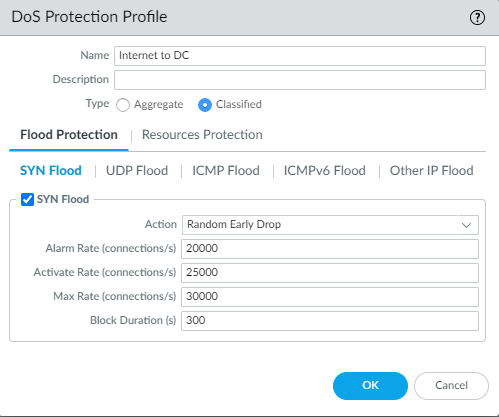
number of connections-per-second to prevent a SYN flood attack. This DoS Protection profile limits the number of connections-per-second (CPS) for the traffic defined in the DoS Protection Policy rules to which you attach the profile, to prevent a DoS attack from taking down your web servers. The profile sets progressive CPS thresholds to alert you, to activate Random Early Drop (RED) packet drop, and to block new connections, as well as a duration during which new connections remain blocked. The CPS thresholds you configure to protect your data center web servers depends on the capacity of your web servers.
![]() To create this profile:
To create this profile:- At ObjectsSecurity ProfilesDoS Protection, Add a classified DoS Protection Profile.
- Name the profile, select Classified as the profile Type, set the CPS values to alert ( Alarm Rate), activate RED ( Activate Rate), begin blocking new sessions ( Max Rate), and set the amount of time in seconds to block new sessions ( Block Duration) when the CPS rate reaches the Max Rate threshold.
If you don’t use protocols such as UDP or other IP protocols, restrict them using a combination of Security policy rules to allow applications and Zone Protection Profiles to block unused protocols by setting flood protection CPS to zero packets for protocols you want to block. - Create a classified DoS Protection policy rule to define
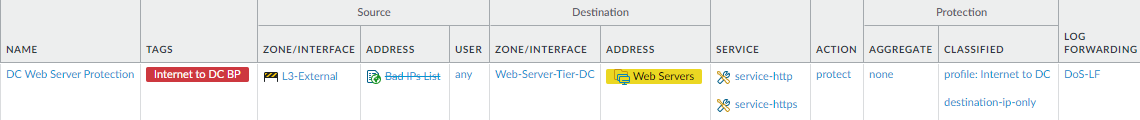
the servers you want to protect from a DoS attack and attach the
DoS Protection profile to it.This rule prevents a SYN flood attack from taking down your data center web server tier. This example applies the classified DoS Protection profile to external traffic allowed to connect to the web server tier.
![]() To create this rule:
To create this rule:- To apply DoS protection to traffic destined for the web server tier, the DoS Protection policy must apply to the same traffic as the Security Policy rule that allows the traffic. In this example, this DoS rule protects the traffic we allowed in Create Internet-to-Data-Center Application Allow Rules.
- On the Option/Protection tab, specify the web services ( service-http and service-https), set the Action to protect to apply the DoS Protection profile’s SYN flood thresholds to the traffic, set the Log Forwarding method (assuming that you have configured log forwarding), and select the classified DoS Protection profile we configured for the traffic in the preceding step ( Internet to DC).
To protect against SYN flood attacks from internal sources, create a separate DoS Protection policy rule that specifies your internal zones as the source zone instead of L3-External. Creating separate rules for external and internal attack sources provides separate reporting that makes investigating attack attempts easier.