Decrypt Traffic for Full Visibility and Threat Inspection
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Decrypt Traffic for Full Visibility and Threat Inspection
Decrypt all traffic except sensitive categories, which include URL categories such as
financial-services, health-and-medicine, government, and other traffic that you
don’t decrypt for business, legal, or regulatory reasons. Use URL categories, custom URL categories, and External Dynamic Lists (EDLs) to specify
the traffic you don't decrypt.
Use decryption exceptions only where required. Be precise to ensure that you limit exceptions to
specific applications or users based on need:
- If decryption breaks an important application, create an exception for the specific IP address, domain, or common name in the certificate associated with the application.
- If you need to exclude a specific user for regulatory, business, or legal reasons, create an exception for just that user.
To ensure that certificates presented during decryption are valid, perform CRL/OCSP checks.
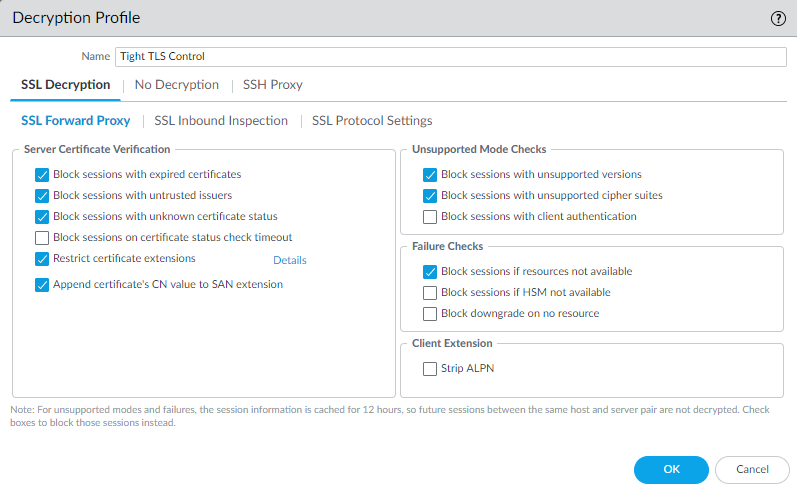
Add a strict Decryption profile to Decryption policy rules. Before you configure SSL Forward Proxy, create a best
practice Decryption Profile (ObjectsDecryption Profile) to attach to your Decryption policy rules, and follow general decryption best practices:
- Configure the SSL DecryptionSSL Forward Proxy settings to block exceptions during TLS negotiation and block sessions that can’t be decrypted:
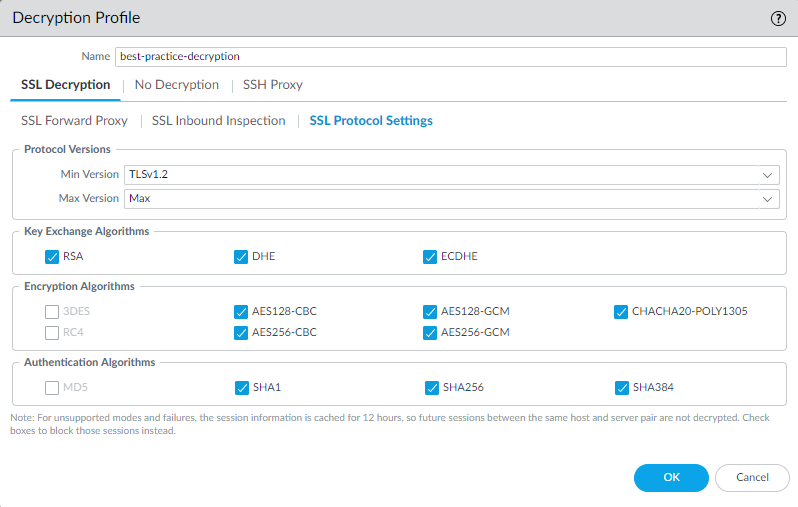
![]() Block sessions if resources not available prevents allowing potentially dangerous connections when the firewall doesn't have the resources to perform decryption, but blocking traffic that you can't decrypt for this reason might affect user experience.Configure SSL DecryptionSSL Protocol Settings to block the use of vulnerable SSL/TLS versions (TLSv1.0, TLSv1.1, and SSLv3) and to avoid weak algorithms (MD5, RC4, and 3DES):
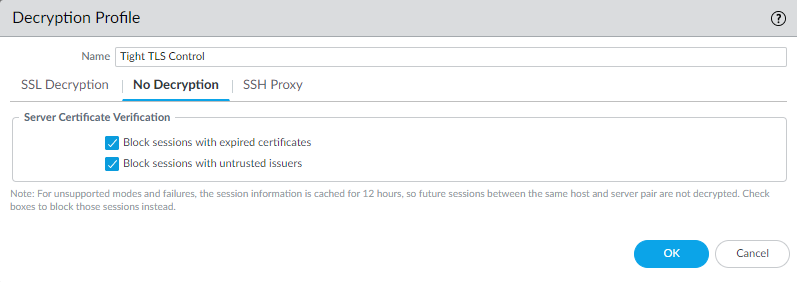
Block sessions if resources not available prevents allowing potentially dangerous connections when the firewall doesn't have the resources to perform decryption, but blocking traffic that you can't decrypt for this reason might affect user experience.Configure SSL DecryptionSSL Protocol Settings to block the use of vulnerable SSL/TLS versions (TLSv1.0, TLSv1.1, and SSLv3) and to avoid weak algorithms (MD5, RC4, and 3DES):![]() Use TLSv1.3 (the most secure protocol) when you can. Many mobile applications use certificate pinning that prevents decryption and causes the firewall to drop traffic. For that traffic, use TLSv1.2.Review the sites you need to access for business purposes. If any of them use TLSv1.1, create a separate Decryption policy and profile for those sites so that only sites you must access for business purposes can use the less secure protocol.Don't allow the SHA1 authentication algorithm unless you must. Create a separate Decryption policy rule and profile for sites that use SHA1 that you must access for business purposes.For traffic that you don't decrypt, configure the No Decryption settings to block encrypted sessions to sites with expired certificates or untrusted issuers:
Use TLSv1.3 (the most secure protocol) when you can. Many mobile applications use certificate pinning that prevents decryption and causes the firewall to drop traffic. For that traffic, use TLSv1.2.Review the sites you need to access for business purposes. If any of them use TLSv1.1, create a separate Decryption policy and profile for those sites so that only sites you must access for business purposes can use the less secure protocol.Don't allow the SHA1 authentication algorithm unless you must. Create a separate Decryption policy rule and profile for sites that use SHA1 that you must access for business purposes.For traffic that you don't decrypt, configure the No Decryption settings to block encrypted sessions to sites with expired certificates or untrusted issuers:![]() Only use a No Decryption profile for TLSv1.2 and earlier versions. Do not attach a No Decryption profile to TLSv1.3 traffic that you don’t decrypt. TLSv1.3 encrypts certificate information that was not encrypted in previous versions, so the firewall cannot block sessions based on certificate information.
Only use a No Decryption profile for TLSv1.2 and earlier versions. Do not attach a No Decryption profile to TLSv1.3 traffic that you don’t decrypt. TLSv1.3 encrypts certificate information that was not encrypted in previous versions, so the firewall cannot block sessions based on certificate information.