What Is a Best Practice Internet Gateway Security Policy?
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
What Is a Best Practice Internet Gateway Security Policy?
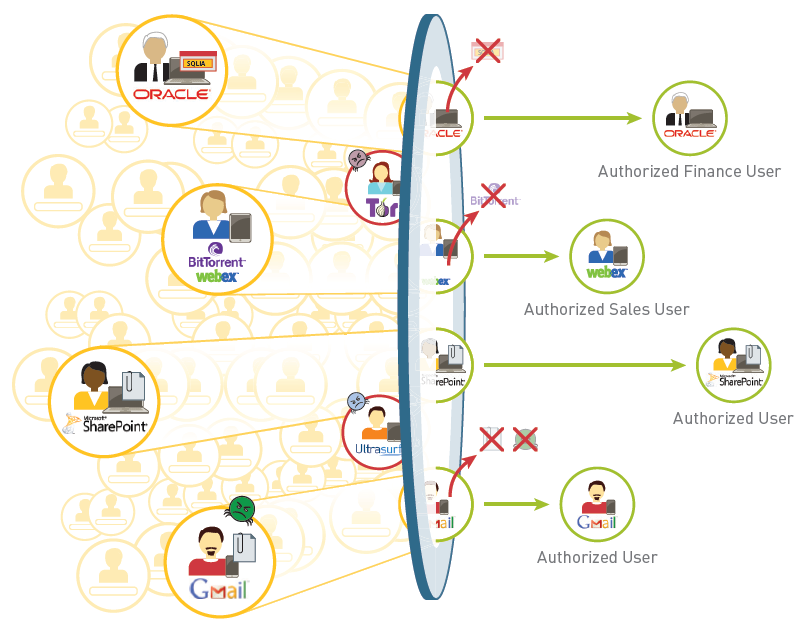
A best practice internet gateway security policy has
two main security goals:
- Minimize the chance of a successful intrusion—Unlike legacy port-based security policies that either block everything in the interest of network security or enable everything in the interest of your business, a best practice security policy leverages App-ID, User-ID, Content-ID, and Device-ID (for IoT Security, which is beyond the scope of this book) to ensure safe enablement of applications across all ports, for all users, all the time, while simultaneously scanning all traffic for both known and unknown threats.
- Identify the presence of an attacker—A best practice internet gateway security policy provides built-in mechanisms to help you identify gaps in the rulebase and detect alarming activity and potential threats on your network.
To achieve these goals, a best practice internet gateway security policy uses application-based
rules to allow user access to specific applications, scans all traffic to detect and
block all known threats, and sends unknown files to WildFire to identify new threats and
generate signatures to block them.
The best practice policy is based on the following methodologies, which ensure detection and
prevention at multiple stages of the attack life cycle.
Best Practice Methodology | Why is this important? |
|---|---|
Inspect All Traffic for Visibility | Because you cannot protect against threats you cannot see, make sure you have full visibility
into all traffic across all users and applications all the time:
With full visibility, the firewall can inspect all traffic—applications, threats, and content—and
tie it to users, regardless of location or device type, port,
encryption, or evasive techniques employed, thanks to native App-ID,
Content-ID, and User-ID technologies. Complete visibility into the applications, content, and users on your network is the first step
toward informed policy control. |
Reduce the Attack Surface | After you gain context into the applications, content, and users on your network, create
application-based Security policy rules to allow critical business
applications and to block high-risk applications that have no
legitimate business use case. To further reduce your attack surface, attach File Blocking and URL Filtering profiles to all
rules that allow application traffic to prevent users from visiting
threat-prone web sites and to prevent them from uploading or
downloading dangerous file types (either knowingly or unknowingly).
To prevent attackers from executing successful phishing attacks,
configure credential phishing prevention. |
Prevent Known Threats |
Attach Security profiles to all allow rules so the firewall can
detect and block network and application layer vulnerability
exploits, buffer overflows, DoS attacks, port scans, and known
malware variants, (including those hidden within compressed files or
compressed HTTP/HTTPS traffic). To enable inspection of encrypted
traffic, enable decryption. In addition to application-based Security
policy rules, create rules for blocking known malicious IP addresses
based on threat intelligence from Palo Alto Networks and reputable
third-party feeds. |
Detect Unknown Threats | Forward all unknown files to WildFire for analysis. WildFire identifies unknown or targeted
malware (also called advanced persistent threats or
APTs) hidden within files by directly observing and
executing unknown files in a virtualized environment in the cloud or
on the WildFire appliance. If WildFire detects malware, it
automatically develops a signature and can deliver it to you in
real-time or at a time interval of your choice. |
