Migrate to Application-Based Policy Using Policy Optimizer
Table of Contents
9.1 (EoL)
Expand all | Collapse all
End-of-Life (EoL)
Migrate to Application-Based Policy Using Policy Optimizer
Convert legacy port-based Security policy rules to application-based rules
to gain visibility into and control over applications.
After using Expedition to migrate a like-for-like configuration
to a PAN-OS appliance, the next phase is using Policy Optimizer
to simplify the migration to App-ID based Security policy rules.
Policy Optimizer makes the conversion from legacy port-based rules
much easier because it automates presenting application information
for each rule with the context you need to understand the information and
create intelligent application-based rules in a single view. Policy
Optimizer:
- Learns and remembers all applications seen in traffic for each rule automatically, which eliminates the need to comb through and analyze reams of log data. Even if logs roll over, Policy Optimizer retains the application information, so you can be confident you’re seeing all of the applications on a rule.
- Enables you to safely migrate to App-ID without risking application availability.
- Is a tool native to and supported on PAN-OS appliances, so you don’t have to move configurations and data between the appliance and a non-native tool.
- Provides easy, intuitive sorting and filtering options to help you identify and prioritize which rules are easiest and safest to convert first.
- Runs on Panorama appliances as well as on individual next-generation firewalls. If you manage your next-generation firewalls running PAN-OS 8.1 with Panorama, you only have to upgrade Panorama (and any Log Collectors connected to the managed firewalls) to PAN-OS 9.0 to use and gain the benefits of Policy Optimizer, so you can qualify and adopt Policy Optimizer faster than if you had to qualify all your firewalls.
These capabilities result in an easy-to-use tool that saves time
and prevents errors when converting port-based rules to App-ID based
rules. Policy Optimizer provides several methods of converting rules:
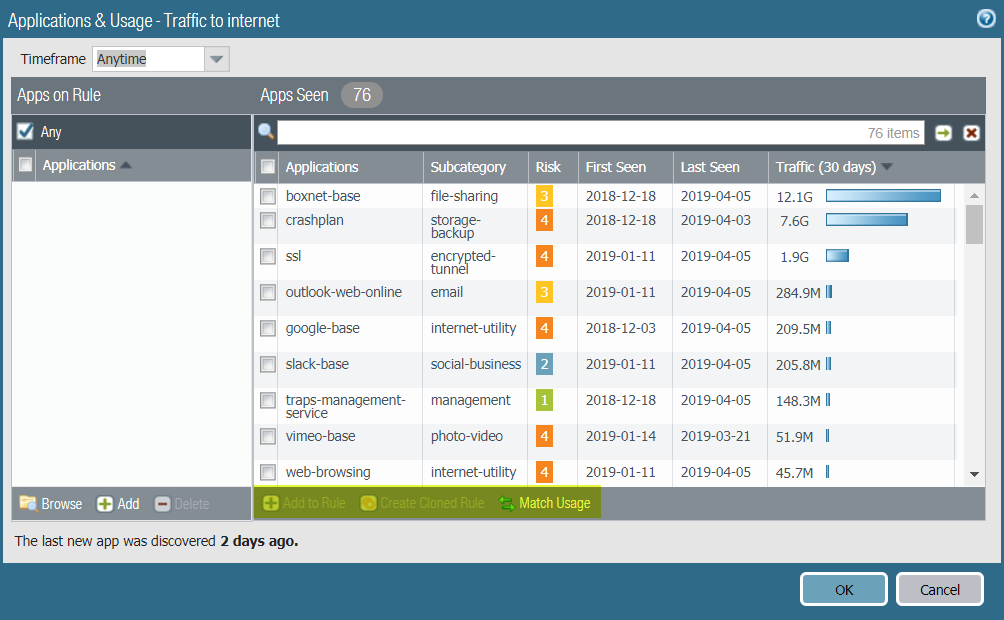
- Create Cloned Rule—Cloning a rule preserves the original port-based rule and places the new App-ID based rule above the cloned rule. You can clone multiple App-ID based rules from one port-based rule. For example, you can clone multiple App-ID rules based on application subcategories from a general web-browsing rule to group applications that require similar access and threat treatment instead of trying to control all web access for all users in all places in one general, unsecure rule.There’s no risk to application availability because the port-based rule below the cloned rule acts like a safety net. If the cloned (App-ID) based rule doesn’t match all the applications you need to allow, you’ll see those applications hit the port-based rule below the cloned rule and you can make adjustments. You can remove the port-based rule when no traffic you want to allow matches the port-based rule for a reasonable period of time, completing the conversion of that rule to an App-ID based rule.
- Add to Rule—Adding applications to a rule replaces the port-based rule with an App-ID based rule, which removes the port-based rule from the rulebase and doesn’t provide the safety net that cloning provides. Use Add to Rule only when you’re sure you know all the applications you want the rule to control. Rules that have seen only a few applications and for which you’re confident you know the required applications for your business are candidates for Add to Rule. It’s safest to clone rules that have seen many applications and rules that may see more applications you need to allow. If you miss adding an application to a rule, you lose availability to that application unless another rule allows it, while cloning the rule retains the port-based rule as a safety net.
- Match Usage—Matching a port-based rule’s usage replaces the port-based rule with an App-ID based rule that contains all of the applications seen on that rule. Use Match Usage only when the rule has seen a small number of well-known applications that have legitimate business purposes. A good example is TCP port 22, which should allow only SSH traffic. If SSH is the only application seen on a port-based rule for port 22, you can safely Match Usage and convert the rule to an App-ID rule.
To Create Cloned Rule or Add
to Rule, you must select at least one application from Apps Seen.
Applications used only for quarterly or yearly events may
not appear in the application information if the history isn’t long
enough to capture their latest activity. Be aware of these types
of applications when you convert rules.
When you convert a port-based rule to an application-based rule,
Policy Optimizer makes no other changes to the rule aside from converting
services to App-IDs. In most cases, after you convert a rule, you
should change the Service to application-default so
only the applications that legitimately use the port can access
it and prevent evasive applications from gaining network access
by using a non-standard port.
If business needs require allowing applications such as
internal custom applications on non-standard ports between particular
clients and servers, restrict the exception to only the required
applications, sources, and destinations. Consider rewriting custom
applications to use application-default ports.
Before you use Policy Optimizer to convert port-based rules to
App-ID based rules:
- Complete the like-for-like migration of the legacy configuration to a Palo Alto Networks next-generation firewall or Panorama appliance from Expedition.
- Run the PAN-OS 9.0 appliance in your production network for about a week before you start converting rules to App-ID so the appliance can begin to learn and categorize the applications on the network. You can convert some simple rules quickly (for example, a port 22 rule should only allow SSH traffic and is easy to convert), while you need to allow the firewall to gather application data from traffic for a longer period of time for other rules, such as your internet access (port 80/433) rule.
- Run the Best Practice Assessment (BPA) to set a baseline against which to compare progress.
- Set realistic goals. Think about what you want the end result to look like. When you reach the goal, run the BPA again to confirm that you reached the goal, and then reevaluate whether you can go farther and make your network even safer. With Policy Optimizer, you don’t sacrifice availability for security, you just improve security.
Convert rules in phases. You can convert some simple port-based
rules that allow well-known applications to App-ID based rules after
the PAN-OS appliance has as little as one week of logs (Policy Optimizer
discovers the applications seen on rules by reading logs). For other
rules that see many applications, such as a general web access rule,
wait at least 30 days to gather application information.
Professional Services has
a wealth of migration experience. You can engage the Professional
Services team to help you move a configuration from your legacy
appliances to Palo Alto Networks next-generation firewalls and Panorama
appliances.
