Download PDF
Cloud NGFW for AWS
Cloud NGFW for AWS Enterprise Data Loss Prevention (E-DLP) Integration
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Cloud NGFW for AWS Enterprise Data Loss Prevention (E-DLP) Integration
Learn how to use Enterprise Data Loss Prevention (E-DLP) with Cloud NGFW for
AWS.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Enterprise Data Loss Prevention (E-DLP) is a set of tools and processes
that allow you to protect sensitive information against unauthorized access, misuse,
extraction, or sharing. For more information, see About Enterprise DLP.
You can integrate E-DLP with Cloud NGFW for AWS and use the Panorama
console to add data filtering profiles to your Security
Policy rules.
Minimum Requirements
The following are the combination of Panorama and Panorama plugin version
requirements to integrate E-DLP with your Cloud NGFW service:
| Panorama Version (PAN-OS) | DLP Plugin | AWS Plugin |
|---|---|---|
|
10.0.2 and above
|
1.0.9
|
5.2.0
|
|
10.2.4 and above
|
3.0.7
|
5.2.0
|
|
11.0.2 and above
|
4.0.3
|
5.2.0
|
|
11.1.0 and above
|
5.0.1
|
5.2.0
|
Provisioning New E-DLP Tenant on Cloud NGFW for AWS
If you have an existing DLP tenant on your Customer Support Portal
(CSP) account that is provisioned in Panorama, the Cloud NGFW service will use
that DLP tenant to integrate DLP with Cloud NGFW.
If you do not have a DLP tenant on your customer support portal
account, then the Cloud NGFW service will create a new DLP tenant.
Use the following steps to enable a new DLP tenant on Cloud NGFW console:
- Log in to the Cloud NGFW console.Select Integrations.
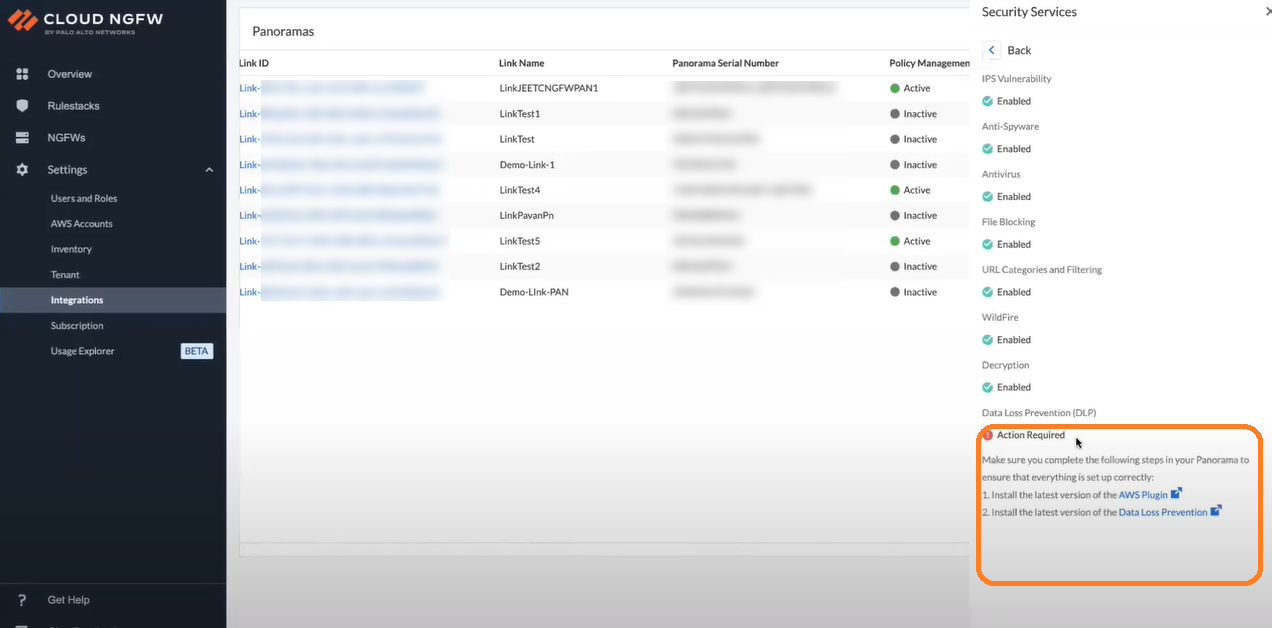
![]() In the Security Service column, click Check Details.
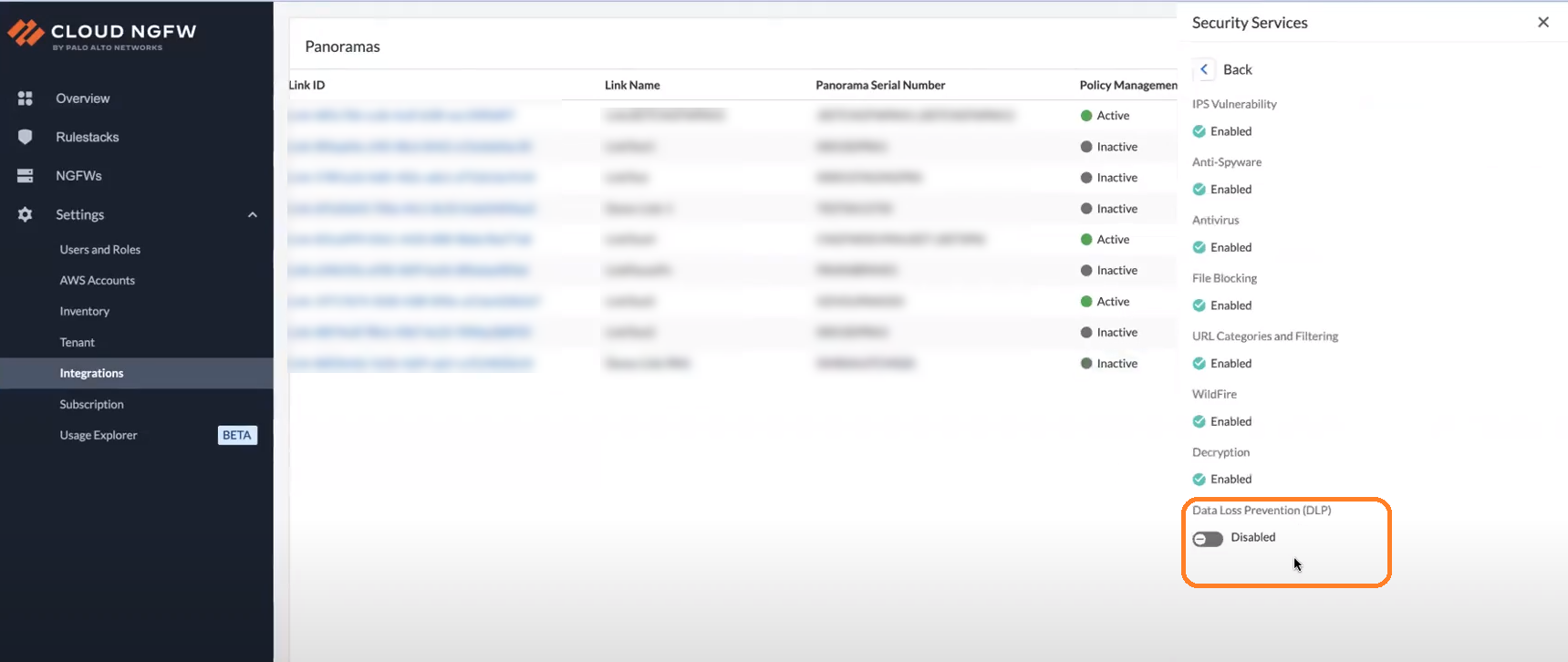
In the Security Service column, click Check Details.![]() You can also click Link ID of a linked Panorama, and then click Check Details.On the Security Services panel, click Data Loss Prevention (DLP) toggle.
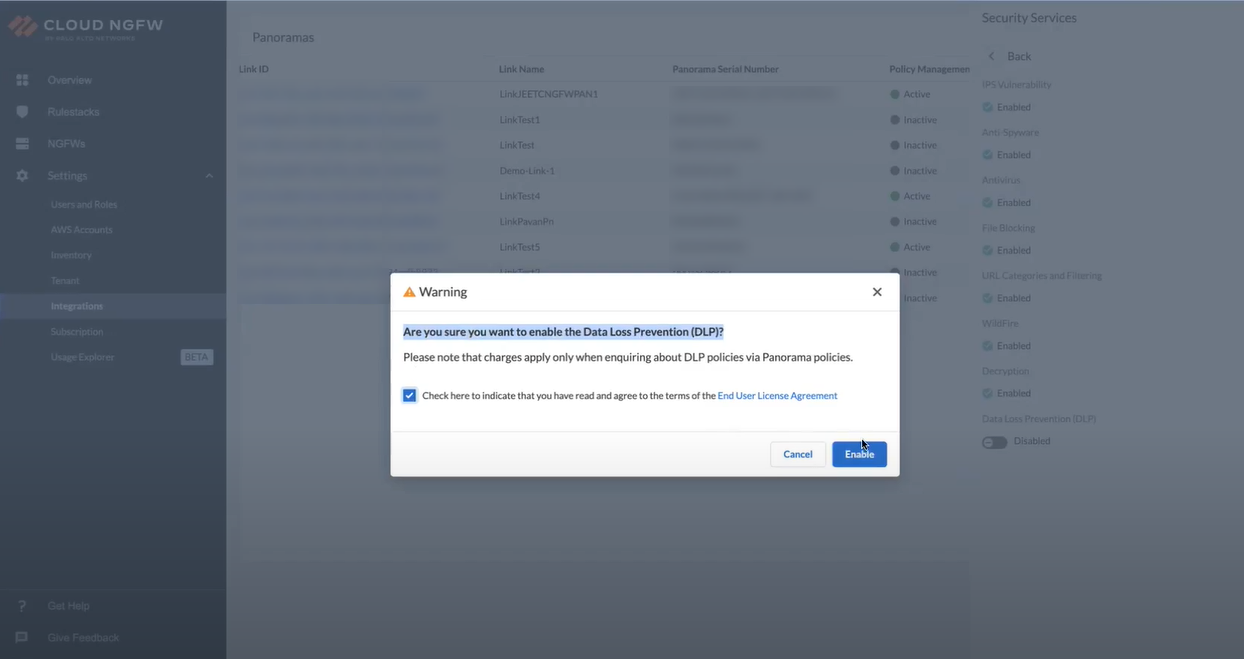
You can also click Link ID of a linked Panorama, and then click Check Details.On the Security Services panel, click Data Loss Prevention (DLP) toggle.![]() Select the check box to accept the End User License Agreement, and then click Enable.
Select the check box to accept the End User License Agreement, and then click Enable.![]() Review the Action Required on the linked Panorama.
Review the Action Required on the linked Panorama.![]() Ensure that the linked Panorama meets the minimum system requirements noted earlier on this page to integrate DLP with your Cloud NGFW service.After you install the required AWS and DLP plugin on your Panorama, the DLP tenant on a Cloud NGFW console gets enabled.On the Cloud NGFW console, go to the Integrations page, select linked Panorama, and then click Check Details under the Security Services column.
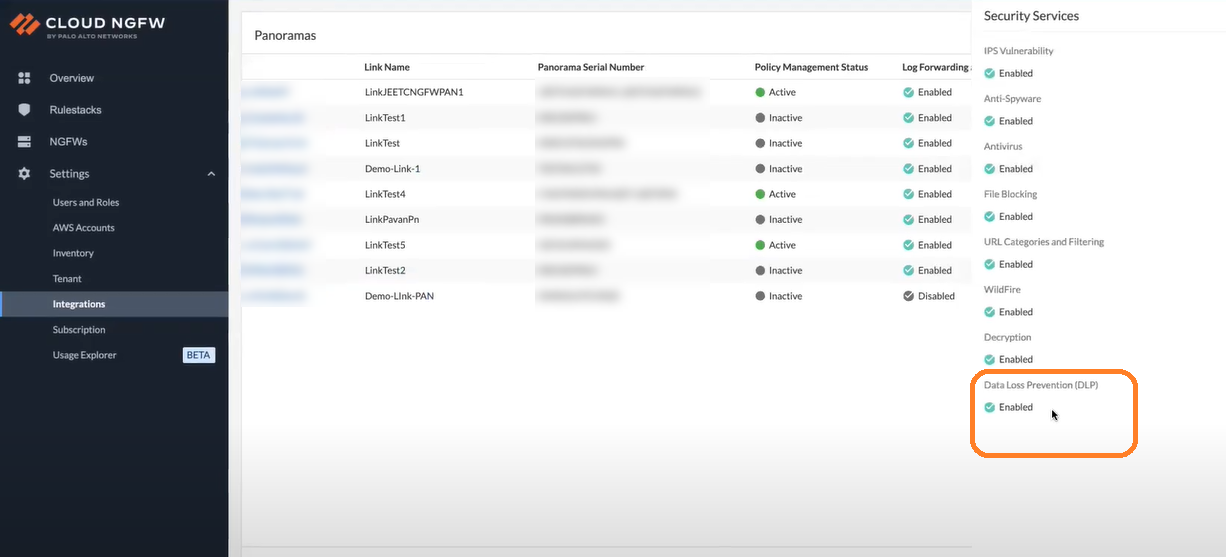
Ensure that the linked Panorama meets the minimum system requirements noted earlier on this page to integrate DLP with your Cloud NGFW service.After you install the required AWS and DLP plugin on your Panorama, the DLP tenant on a Cloud NGFW console gets enabled.On the Cloud NGFW console, go to the Integrations page, select linked Panorama, and then click Check Details under the Security Services column.![]() You can now see the enabled Data Loss Prevention (DLP).After you enable the DLP tenant on the Cloud NGFW console successfully, firewalls associated with the linked Panorama can start using the DLP services.You can add a DLP filtering profile to your Security Policy Rule for your firewall in Panorama.
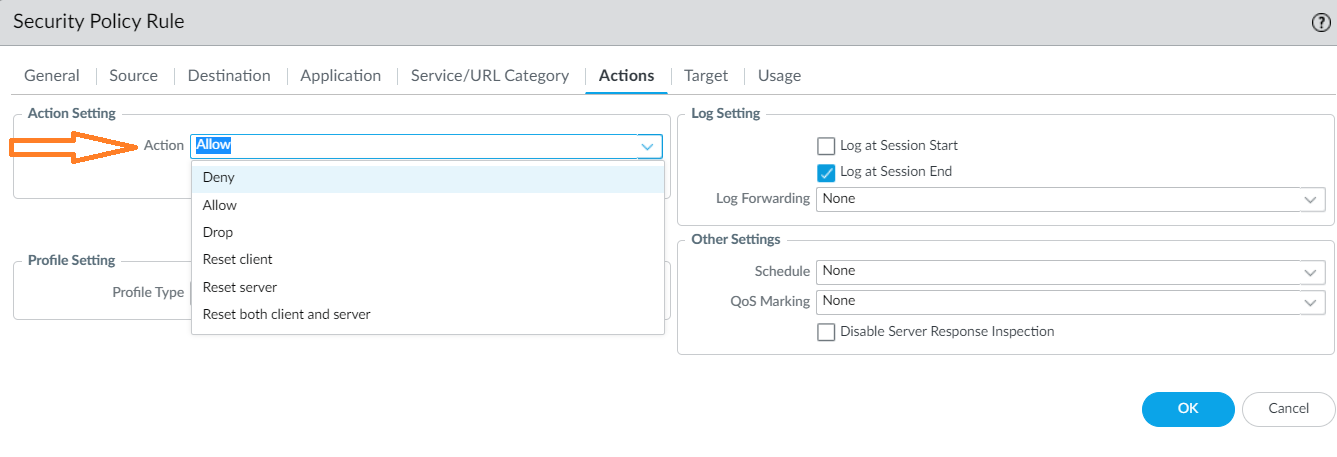
You can now see the enabled Data Loss Prevention (DLP).After you enable the DLP tenant on the Cloud NGFW console successfully, firewalls associated with the linked Panorama can start using the DLP services.You can add a DLP filtering profile to your Security Policy Rule for your firewall in Panorama.![]() In the Security Policy Rule screen, go to the Actions tab, and then select the action to take (for example, allow or deny).
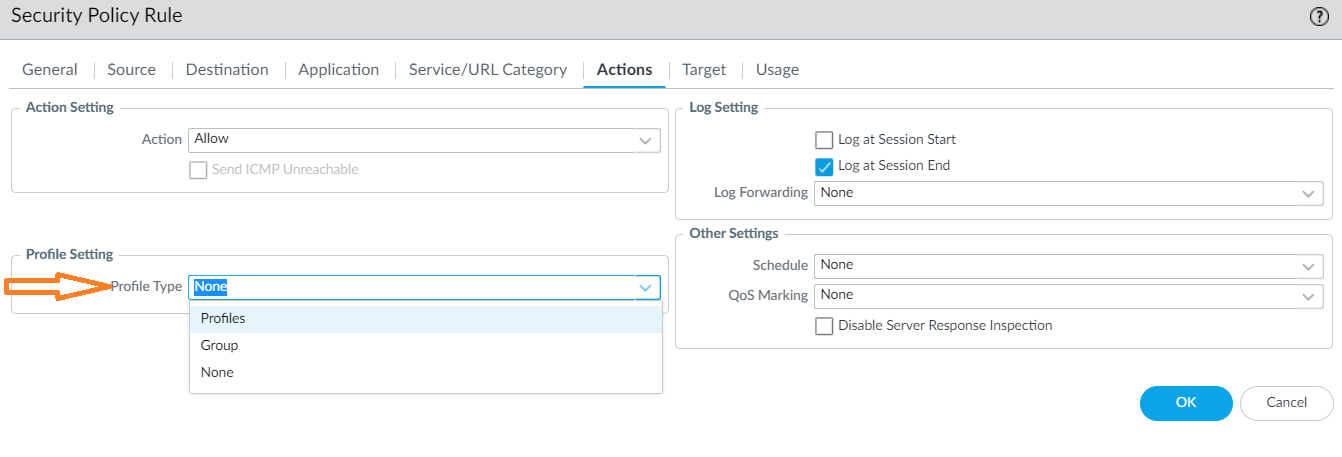
In the Security Policy Rule screen, go to the Actions tab, and then select the action to take (for example, allow or deny).![]() Determine the Profile Setting.
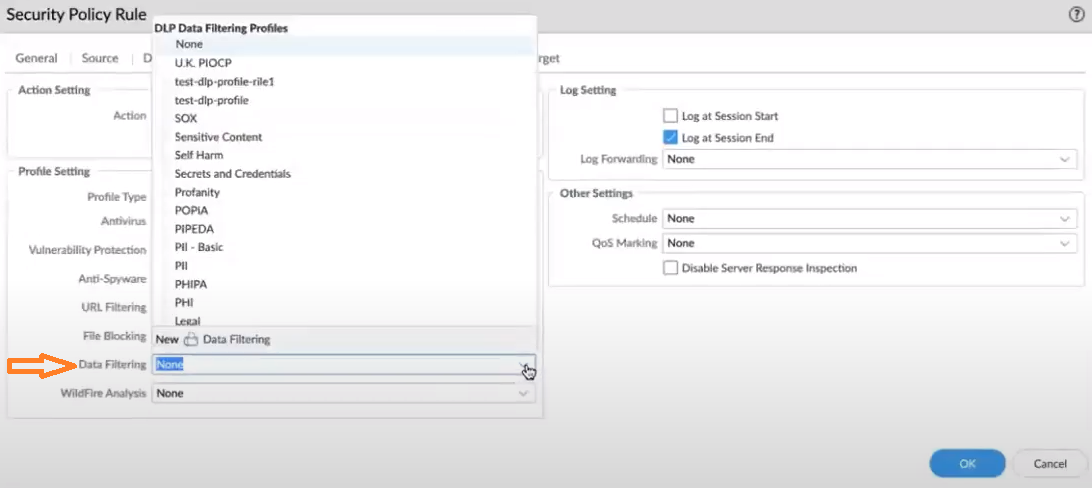
Determine the Profile Setting.![]() Select a DLP data filtering profile.
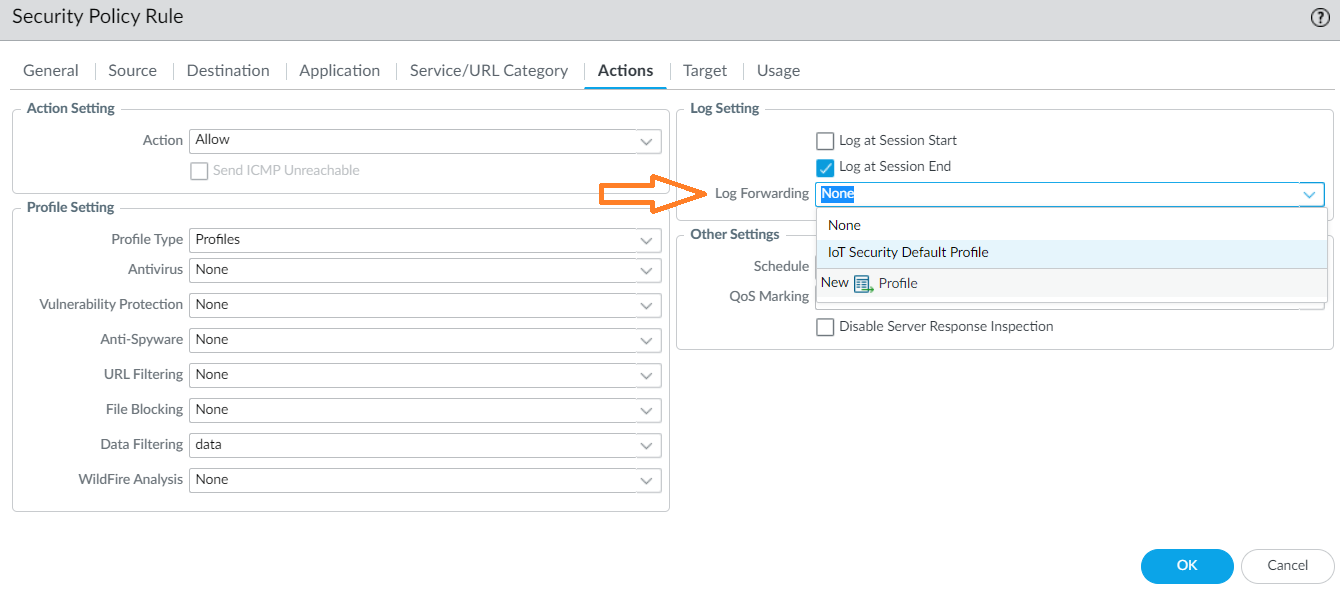
Select a DLP data filtering profile.![]() Configure the Log Setting and other settings.
Configure the Log Setting and other settings.![]() For more information, see Use Panorama for Cloud NGFW Policy Management.After pushing the Security policy rule to your firewall, you can view existing Data Filtering Profiles and Data Filtering Patterns that you can use for your DLP tenant.
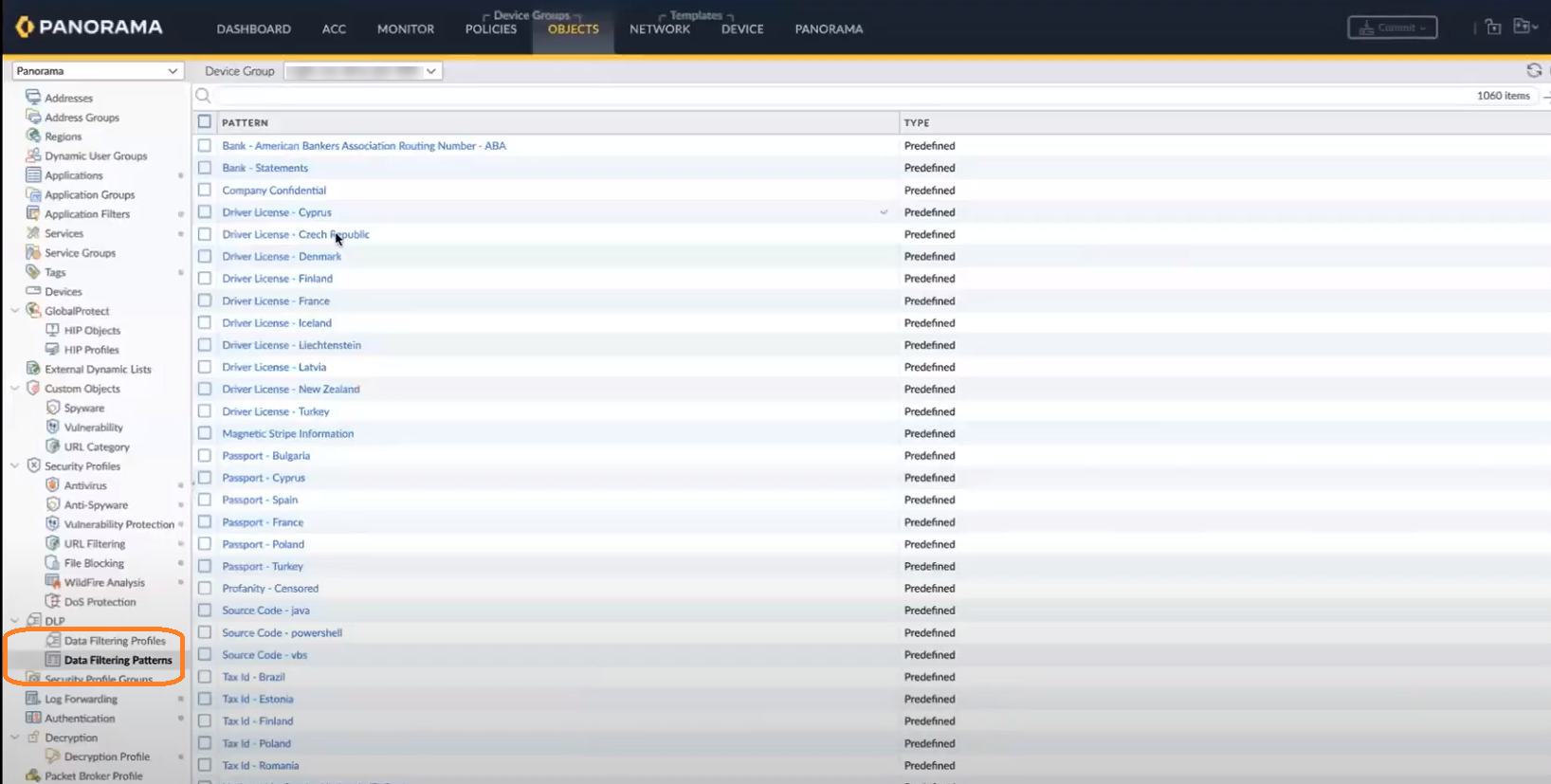
For more information, see Use Panorama for Cloud NGFW Policy Management.After pushing the Security policy rule to your firewall, you can view existing Data Filtering Profiles and Data Filtering Patterns that you can use for your DLP tenant.![]()
Monitoring DLP Log Details
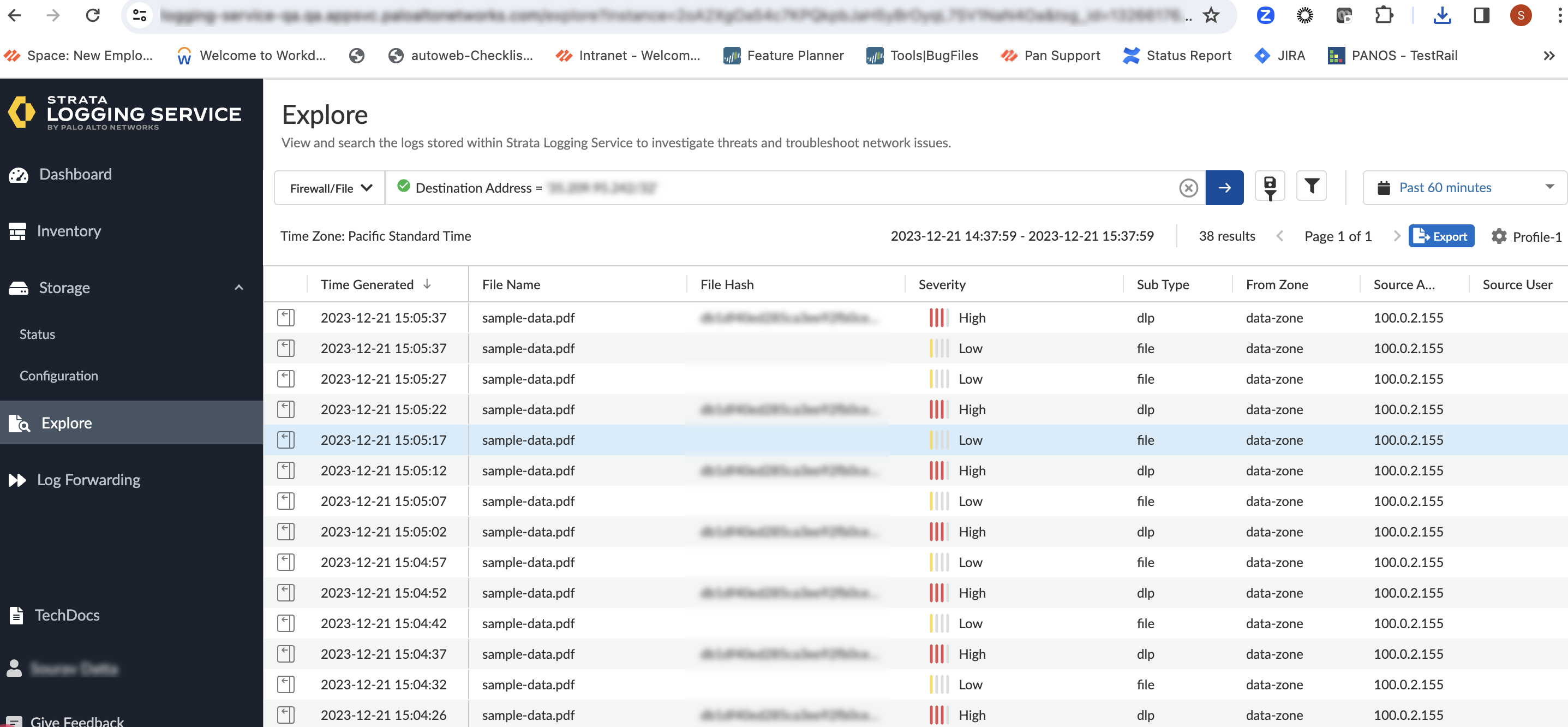
To view your DLP logs in Panorama, click the Monitor tab, and then go to Logs > Data Filtering. For more information, see View Enterprise DLP Log Details on Panorama.![]() To view your Strata Logging Service logs for DLP, go to the Explore tab, and select the Firewall or File option. For more information, see View Log Details on Strata Logging Service.
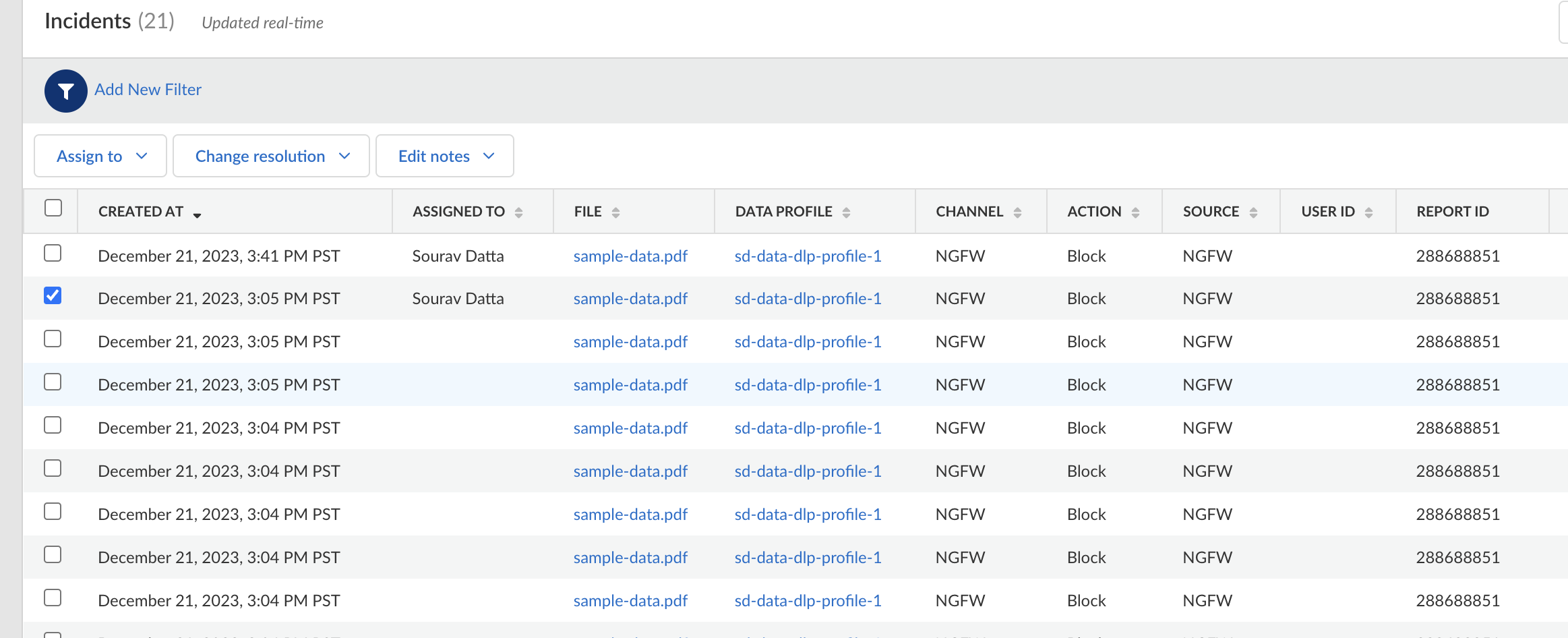
To view your Strata Logging Service logs for DLP, go to the Explore tab, and select the Firewall or File option. For more information, see View Log Details on Strata Logging Service.![]() To view your DLP tenant incidents logs on SCM, see View Enterprise DLP Log Details on Strata Cloud Manager.
To view your DLP tenant incidents logs on SCM, see View Enterprise DLP Log Details on Strata Cloud Manager.![]() For more information on AWS destinations on DLP logs, see Amazon CloudWatch Logs.
For more information on AWS destinations on DLP logs, see Amazon CloudWatch Logs.