Enterprise DLP
Create a Microsoft Exchange Outbound Connector
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create a Microsoft Exchange Outbound Connector
Create an outbound Microsoft Exchange Online Connector to connect Microsoft Exchange
with Enterprise Data Loss Prevention (E-DLP) for inline inspection of emails.
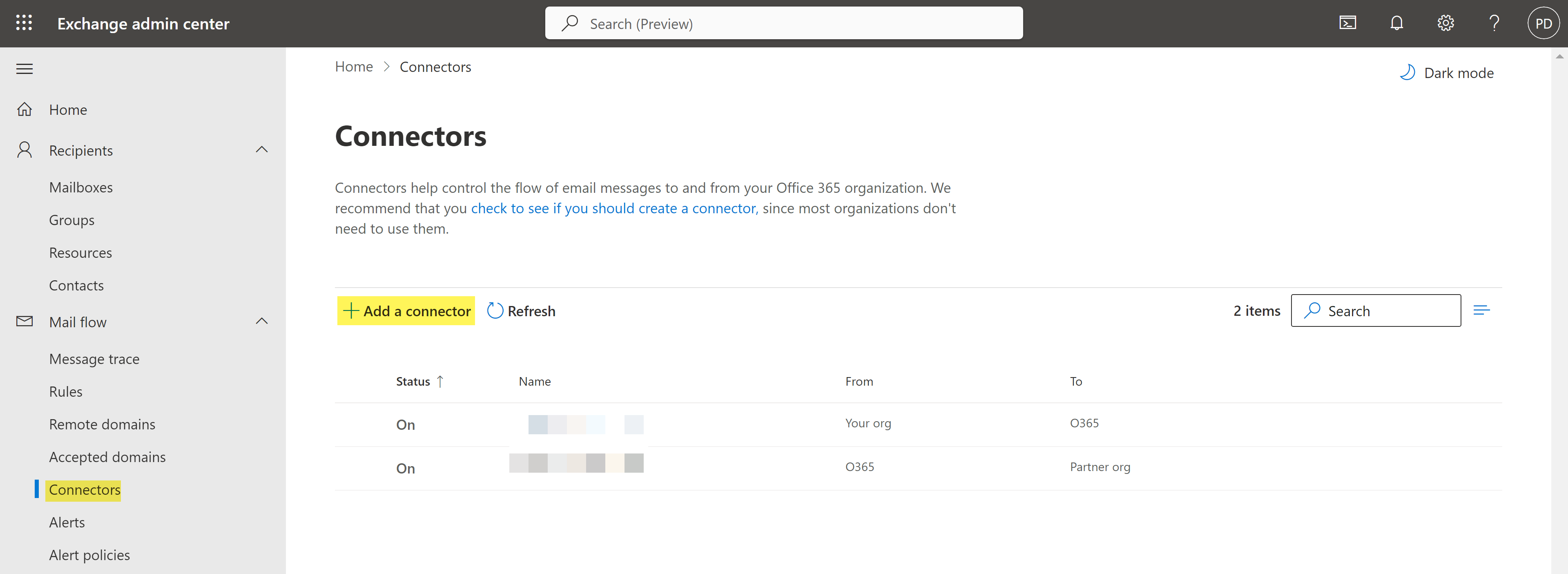
- Log in to the Microsoft Exchange Admin Center.Select Mail flowConnectors and Add a connector to launch the Microsoft Exchange Connector wizard.
![]() Specify the connector source and destination.
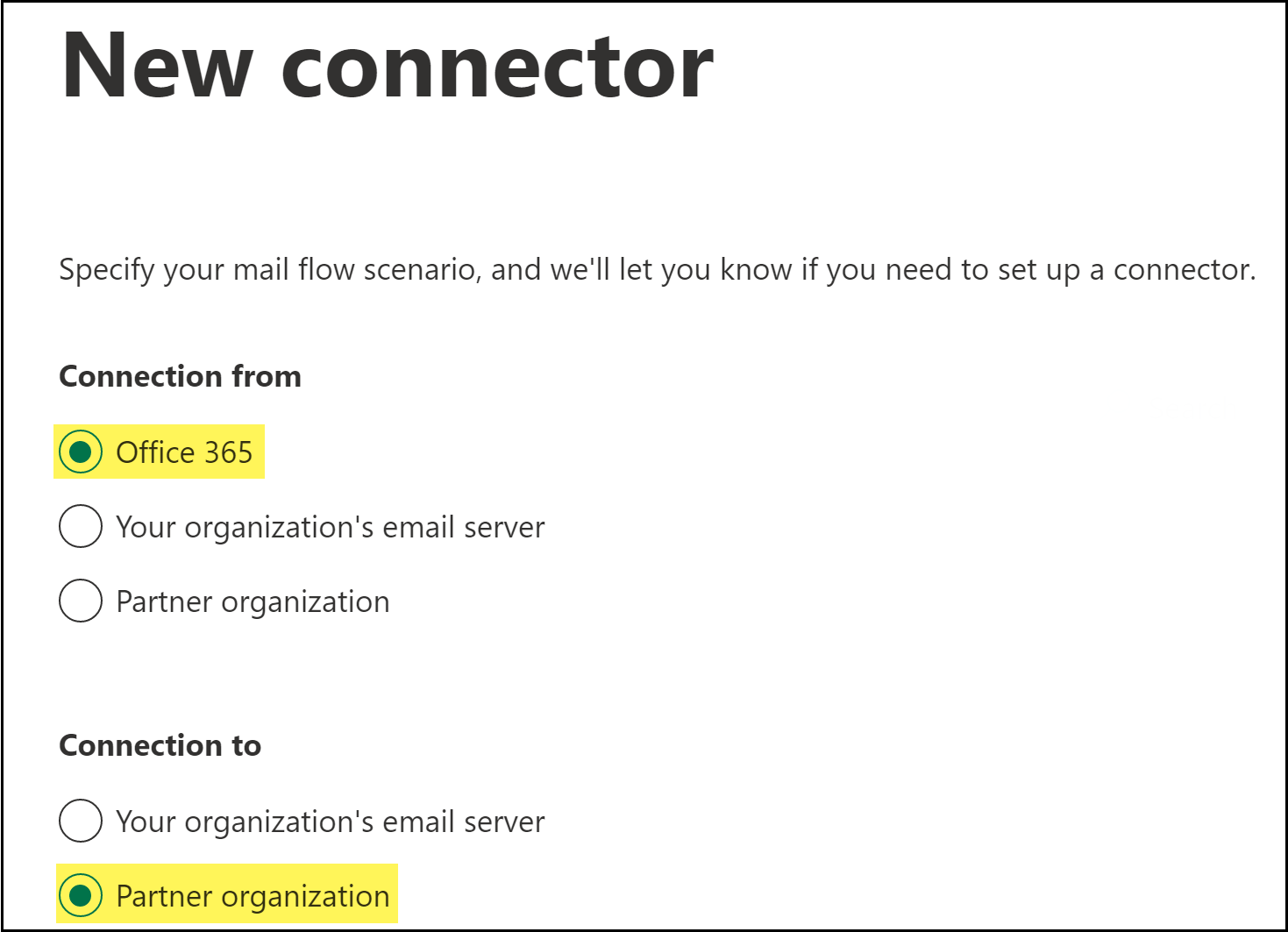
Specify the connector source and destination.- For Connection from, select Office 365.For Connection to, select Partner organization.A partner can be any third-party cloud service that provides services such as services, such as data protection. In this case, the third-party partner organization is Palo Alto Networks.Click Next.
![]() Name the Microsoft Exchange connector.
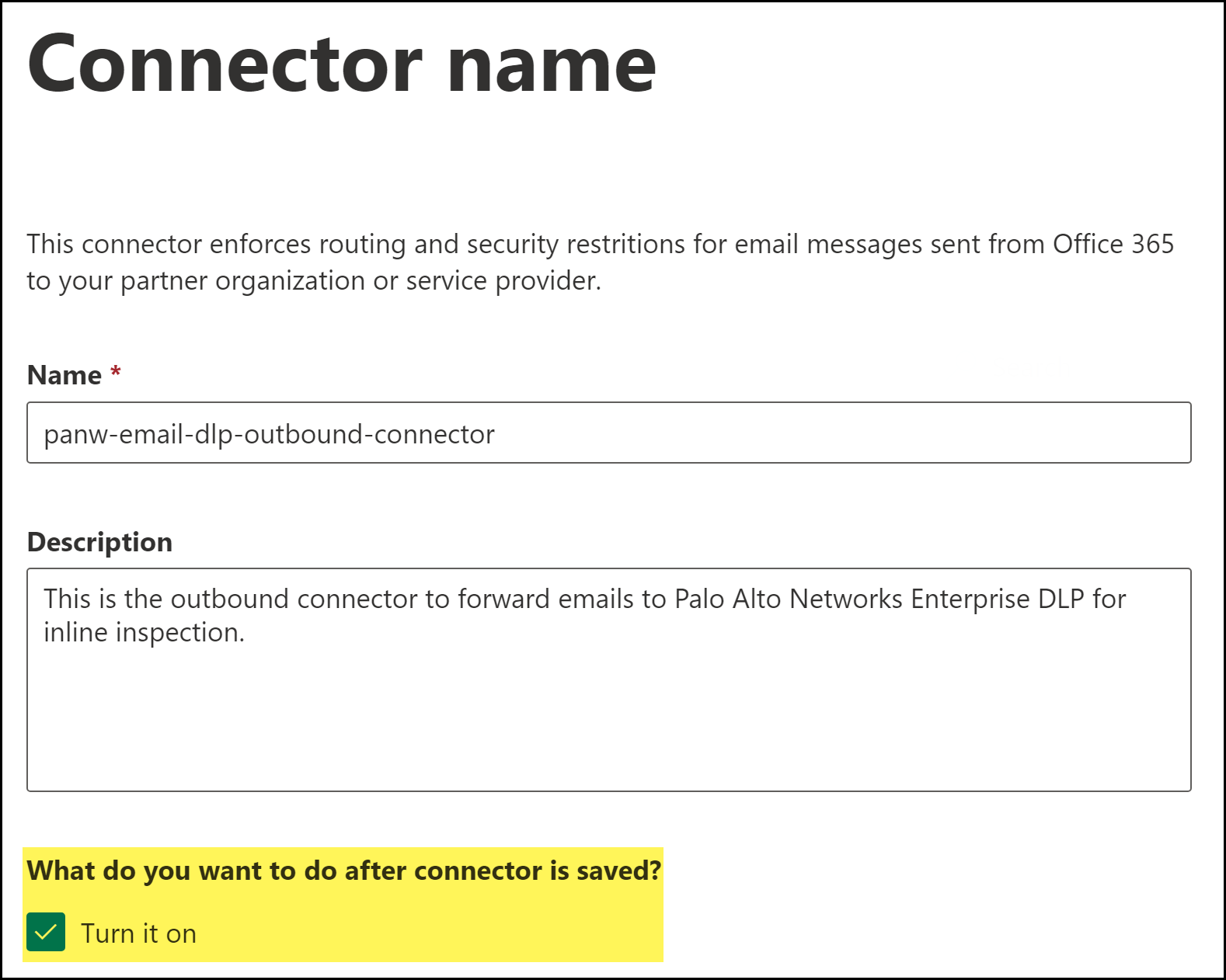
Name the Microsoft Exchange connector.- Enter a descriptive Name for the connector.(Optional) Enter a Description for the connector.(Best Practices) For What do you want to do after connector is saved?, check (enable) Turn it on.Enable this to automatically turn on the connector after you have finished creating and saved the new Microsoft Exchange connector.Click Next.
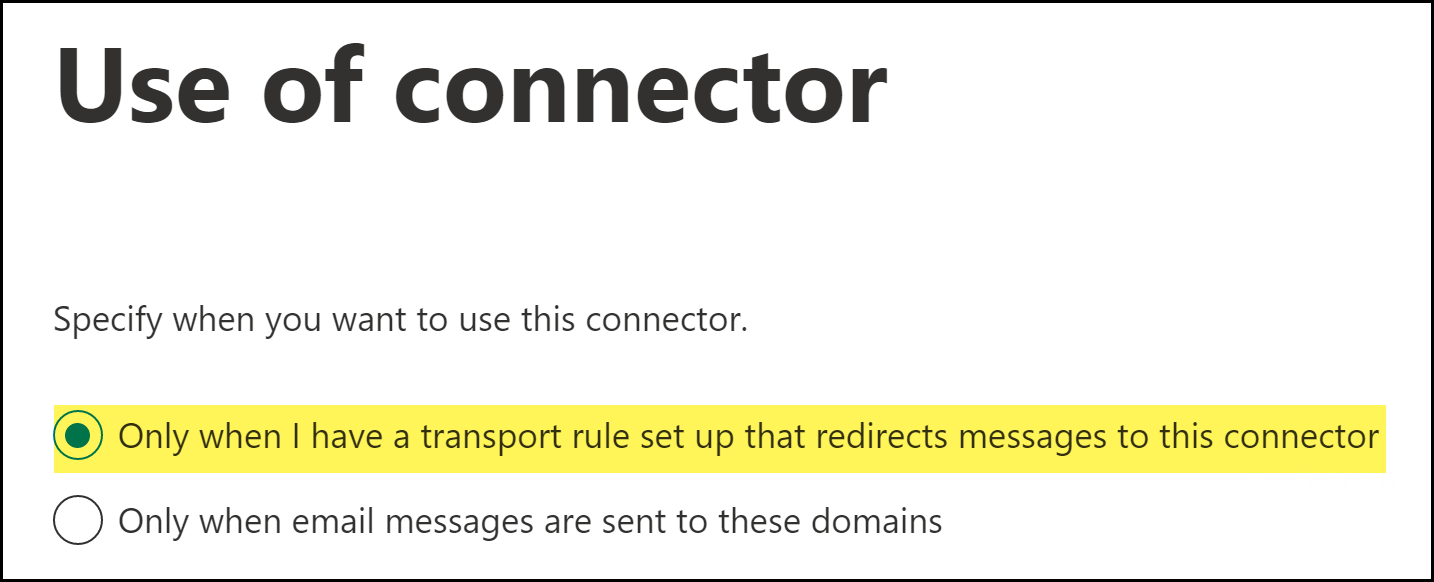
![]() To specify when the connector should be used, select Only when I have a transport rule set up that redirects messages to this connector and click Next.Using the connector only when a transport rule exists enables fine-grained control of what action to take when an email contains sensitive data. By selecting this option, Microsoft Exchange enforces action on emails based on the action specified in the Enterprise DLP data profile.
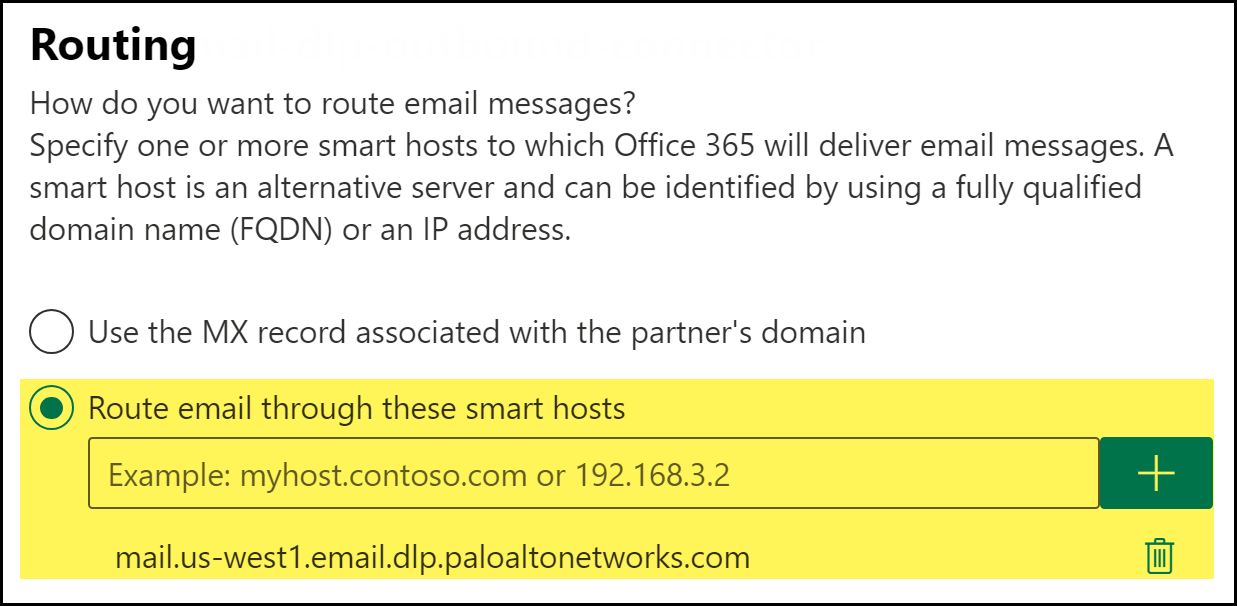
To specify when the connector should be used, select Only when I have a transport rule set up that redirects messages to this connector and click Next.Using the connector only when a transport rule exists enables fine-grained control of what action to take when an email contains sensitive data. By selecting this option, Microsoft Exchange enforces action on emails based on the action specified in the Enterprise DLP data profile.![]() To configure the route settings for emails, check (enable) Route email through these smart hosts to add the following smart host Fully Qualified Domain Name (FQDN) and click Next.The FQDN specifies the region where emails are forwarded to Enterprise DLP for inspection and verdict rendering. This also generates and displays Email DLP incidents in the specified region. All processes and data related to Email DLP occur and are stored in this region.
To configure the route settings for emails, check (enable) Route email through these smart hosts to add the following smart host Fully Qualified Domain Name (FQDN) and click Next.The FQDN specifies the region where emails are forwarded to Enterprise DLP for inspection and verdict rendering. This also generates and displays Email DLP incidents in the specified region. All processes and data related to Email DLP occur and are stored in this region.- APACmail.asia-southeast1.email.dlp.paloaltonetworks.comAustraliamail.australia-southeast1.email.dlp.paloaltonetworks.comEuropemail.europe-west3.email.dlp.paloaltonetworks.comIndiamail.asia-south1.email.dlp.paloaltonetworks.comJapanmail.asia-northeast1.email.dlp.paloaltonetworks.comUnited Kingdommail.europe-west2.email.dlp.paloaltonetworks.comUnited Statesmail.us-west1.email.dlp.paloaltonetworks.com
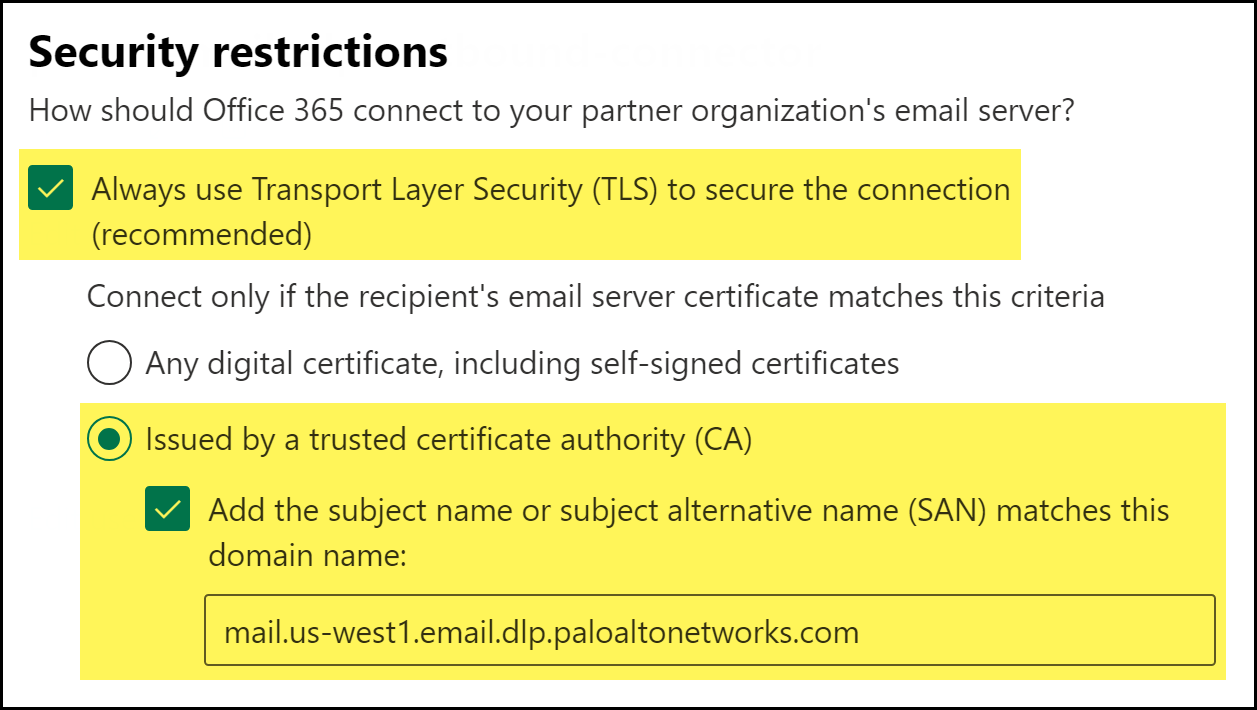
![]() Specify the security restrictions for the connector.
Specify the security restrictions for the connector.- Check (enable) Always use Transport Layer Security (TLS) to secure the connection.Enterprise DLP requires this setting to successfully forward emails for inspection. Enterprise DLP rejects the connect connection if you disable this setting.Select Issued by a trusted certificate authority (CA).Check (enable) Add the subject name or subject alternative (SAM) matches to this domain: and add the following domain name.Enterprise DLP requires you add the subject name for positive identification of the Enterprise DLP cloud service. The CA issuer FQDN you add must match the email routing FQDN you added in the previous step.
- APACmail.asia-southeast1.email.dlp.paloaltonetworks.comAustraliamail.australia-southeast1.email.dlp.paloaltonetworks.comEuropemail.europe-west3.email.dlp.paloaltonetworks.comIndiamail.asia-south1.email.dlp.paloaltonetworks.comJapanmail.asia-northeast1.email.dlp.paloaltonetworks.comUnited Kingdommail.europe-west2.email.dlp.paloaltonetworks.comUnited Statesmail.us-west1.email.dlp.paloaltonetworks.comClick Next.
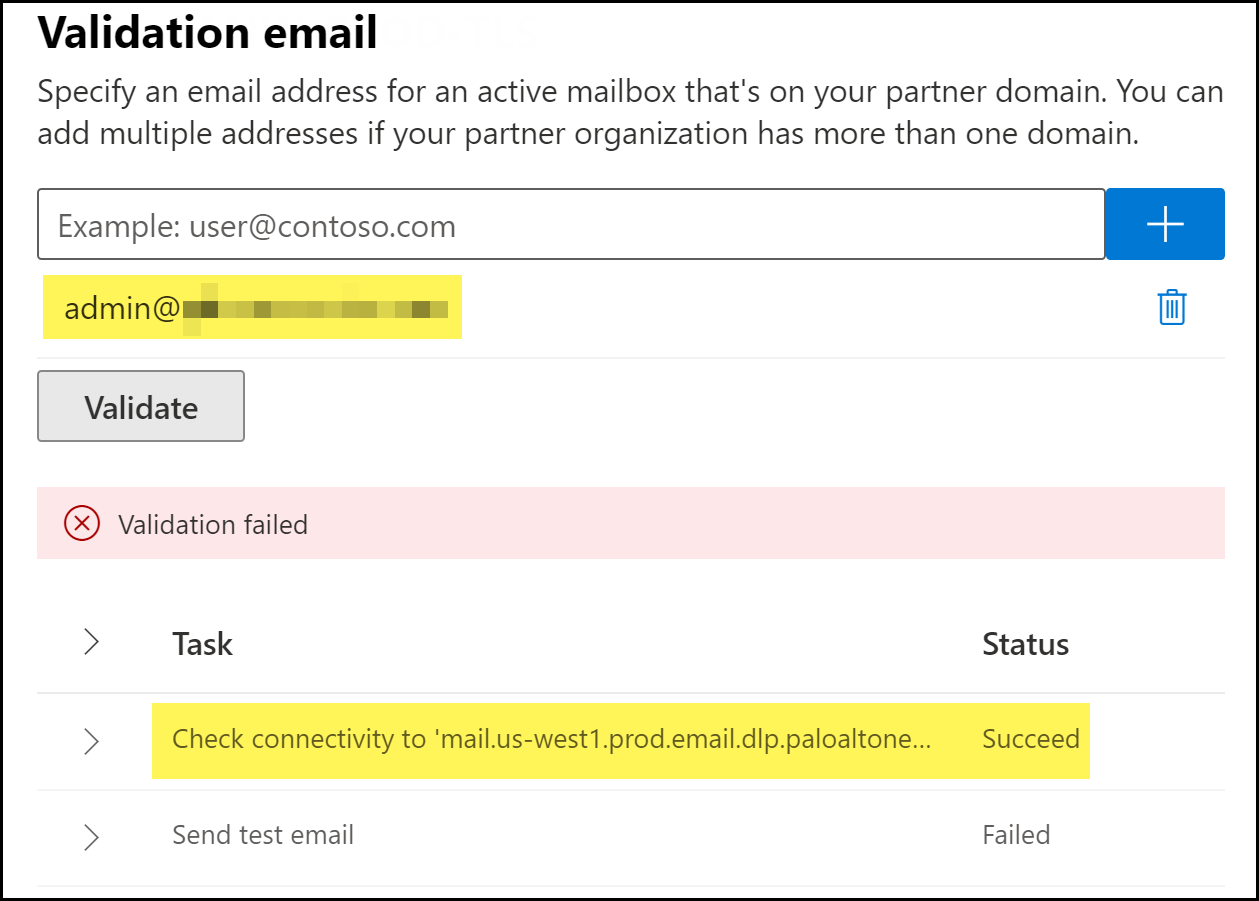
![]() Add a validation email.A valid email address associated with the email domain used by your organization. This is required to validate connectivity between the Microsoft Exchange Admin Center and the Palo Alto Networks smart host, and that emails can be successfully delivered.
Add a validation email.A valid email address associated with the email domain used by your organization. This is required to validate connectivity between the Microsoft Exchange Admin Center and the Palo Alto Networks smart host, and that emails can be successfully delivered.- Add a valid email address for validation.Validate.The Microsoft Exchange validation tests take a few minutes to complete.Under the Task, verify that the Check connectivity validation test status to the Enterprise DLP FQDN displays Succeed.It's expected that the following errors occur when adding the validation email.
- Validation failed error is displayed.
- The Send test email validation test status displays Failed.
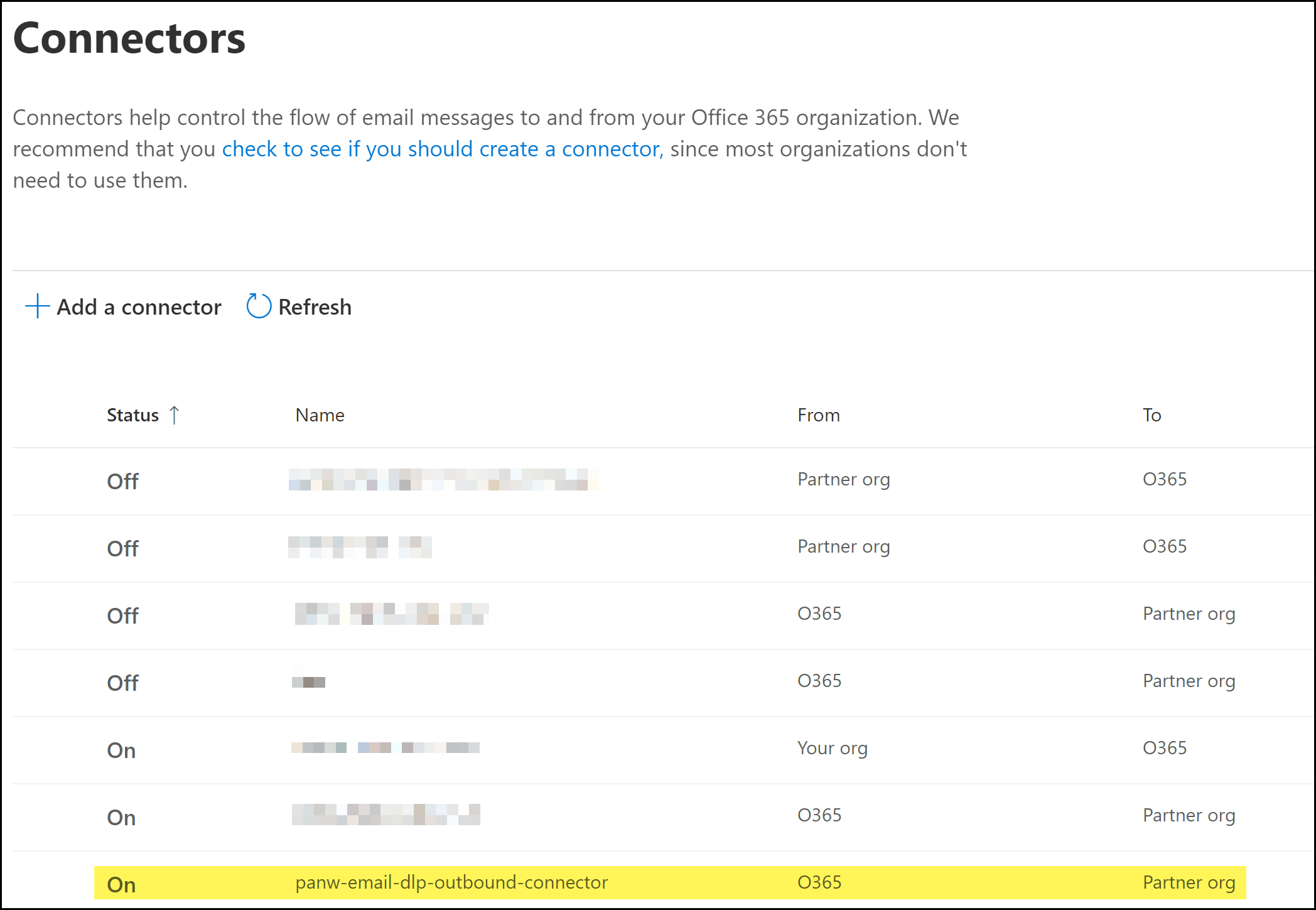
![]() Click Done.When prompted to confirm whether to proceed without successful validation, click Yes, proceed.Review the connector details and Create Connector.Click Done when prompted that the outbound connector was successfully created.Back in the Connectors page, verify the outbound connector is displayed and that the Status is On.
Click Done.When prompted to confirm whether to proceed without successful validation, click Yes, proceed.Review the connector details and Create Connector.Click Done when prompted that the outbound connector was successfully created.Back in the Connectors page, verify the outbound connector is displayed and that the Status is On.![]() Create the Microsoft Exchange inbound connector if not already created.Enterprise DLP requires the inbound connector to return emails forwarded to Enterprise DLP for inspection back to Microsoft Exchange.Skip this step if you have already created the inbound connector.Create Microsoft Exchange Transport Rules.After you successfully created the Microsoft Exchange connectors, you must create Microsoft Exchange transports rule to forward emails to and from Enterprise DLP, and to specify what actions Microsoft Exchange takes based on the Enterprise DLP verdicts.
Create the Microsoft Exchange inbound connector if not already created.Enterprise DLP requires the inbound connector to return emails forwarded to Enterprise DLP for inspection back to Microsoft Exchange.Skip this step if you have already created the inbound connector.Create Microsoft Exchange Transport Rules.After you successfully created the Microsoft Exchange connectors, you must create Microsoft Exchange transports rule to forward emails to and from Enterprise DLP, and to specify what actions Microsoft Exchange takes based on the Enterprise DLP verdicts.