Enterprise DLP
Create a Microsoft Exchange Proofpoint Encrypt Transport Rule
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create a Microsoft Exchange Proofpoint Encrypt Transport Rule
Create a Microsoft Exchange Encrypt transport rule to forward an email to your
Proofpoint server for encrypting after inspection by Enterprise Data Loss Prevention (E-DLP).
This procedure assumes you have already setup your Proofpoint server and created the
required Proofpoint connector.
- Log in to the Microsoft Exchange Admin Center.Create the required Microsoft Exchange connectors.Skip this step if you have already created both the outbound, inbound, and Proofpoint server connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the encrypt transport rule conditions.
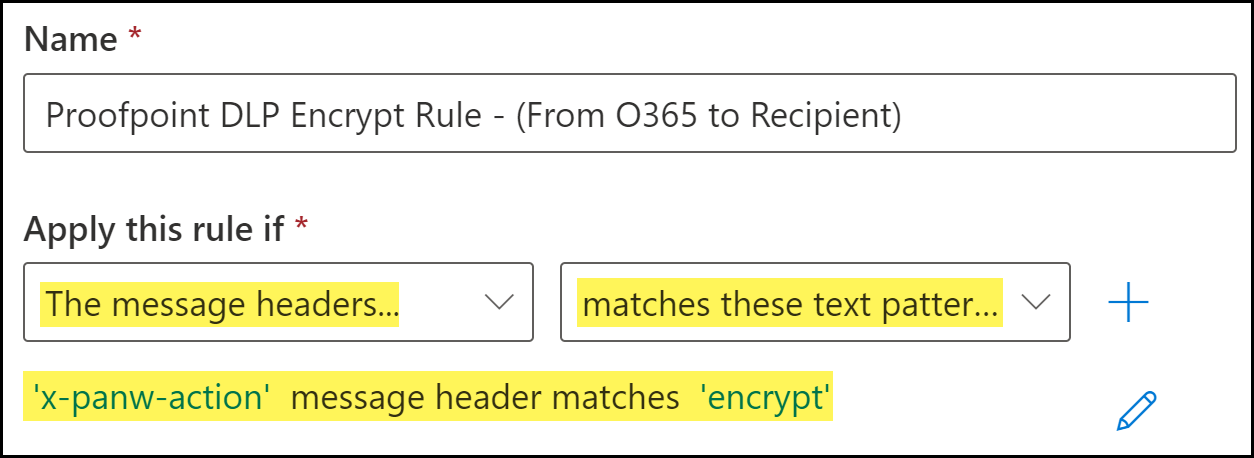
Configure the encrypt transport rule conditions.- Enter a Name for the Proofpoint encrypt transport rule.Add the encrypt email message header.The encrypt header is added by the DLP cloud service when an email contains sensitive information that should be encrypted.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:encryptSelect the word you added. Click Save to continue.
![]() Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.
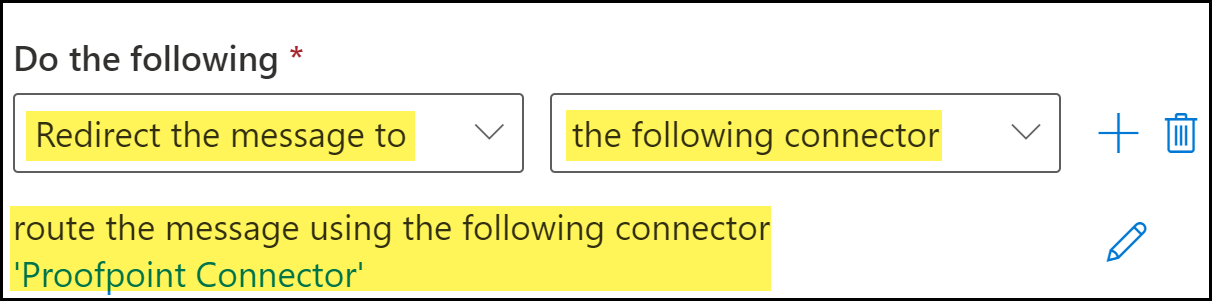
Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.- For Do the following, select Redirect the message to.
- Select the following connector.
- Select the Proofpoint connector and Save.
![]()
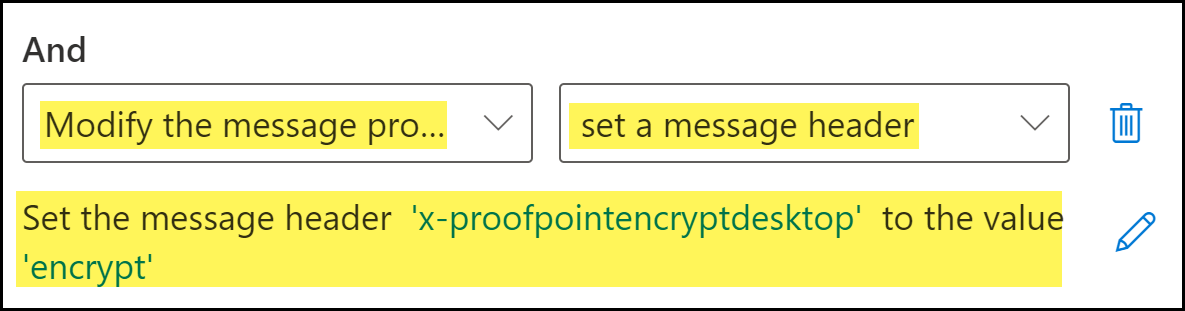
Click the Add Action icon (+) to add an additional rule condition.Instruct Microsoft Exchange to further modify the email header.- For Do the following, select Modify the message properties.
- Select set a message header.
- Click Enter Text. When promoted, enter the following.x-proofpointencryptdesktopClick Save to continue.Click Enter words. When prompted, enter the following and Add:encryptSelect the word you added. Click Save to continue.
![]() Click Next to continue.Configure the Proofpoint encrypt transport rule settings.
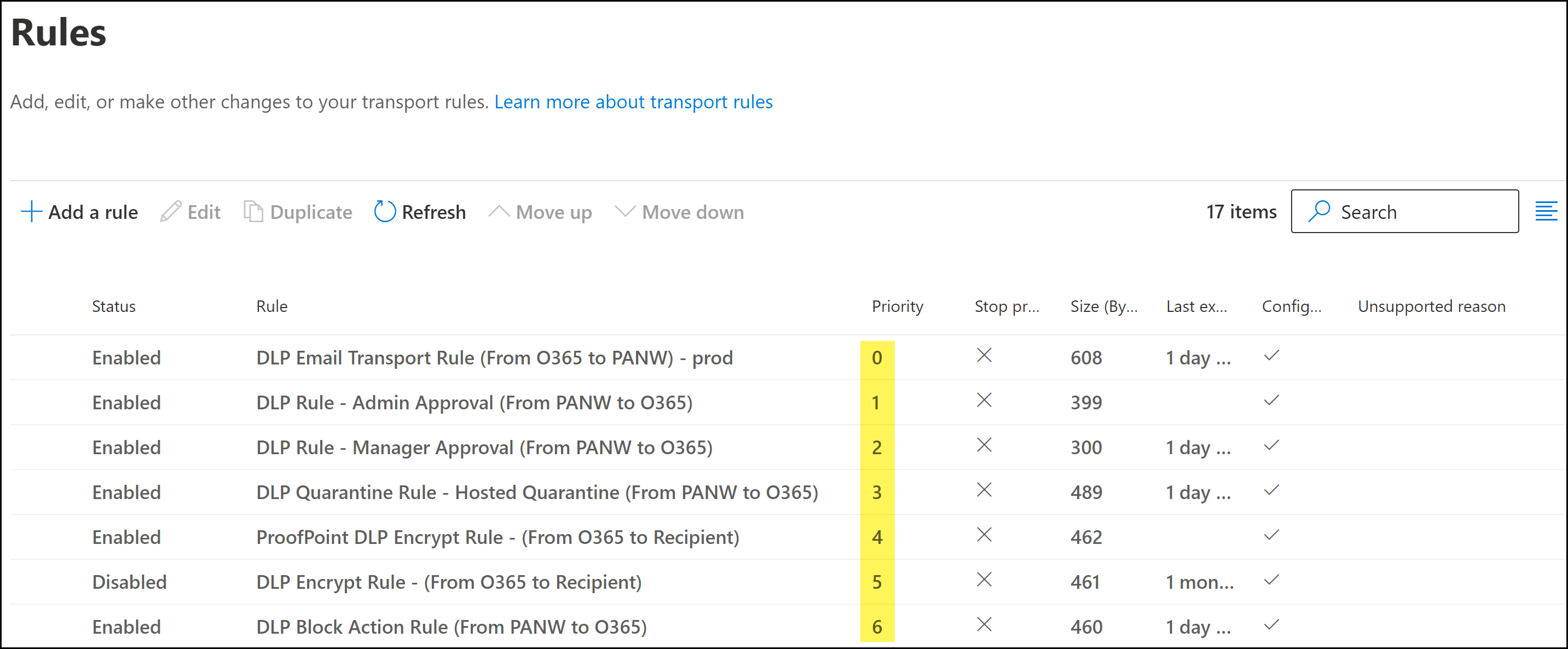
Click Next to continue.Configure the Proofpoint encrypt transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the encrypt transport rule settings as needed.Click Next to continue.Review the encrypt transport rule configuration and click Finish.Click Done when prompted that the encrypt transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
- If you want to ensure emails are forwarded to your Proofpoint server for encryption, Palo Alto Networks recommends disabling your existing Encrypt or assigning a higher priority to the Proofpoint encrypt rule.You can forward an email for encryption to either your Proofpoint server or to Microsoft Exchange for encryption, but not both.
![]()