Enterprise DLP
Enterprise DLP Limitations
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Enterprise DLP Limitations
Review the Enterprise Data Loss Prevention (E-DLP) cloud service and plugin limitations.
The following are limitations associated with Enterprise Data Loss Prevention (E-DLP) cloud
service, plugin, and Endpoint DLP.
Enterprise DLP Cloud Service and Plugin
|
Issue ID
|
Description
|
|---|---|
|
—
|
The following NGFW do not support Enterprise DLP.
|
|
—
|
When using Enterprise DLP on Hub 1.0, the DLP app on the hub
supports only Superuser administrative privileges. Role based access
control for Enterprise DLP is supported on Hub
2.0 only.
|
|
—
|
A custom block response page for matched traffic blocked by Enterprise DLP is not supported for NGFW and
Prisma Access managed by Strata Cloud Manager or Panorama.
|
|
SCA-9870
|
Audit logs (ConfigurationData Loss PreventionAudit Log) generated when a user views an Data Security incident (ConfigurationSaaS SecurityData SecurityIncidentsData Asset Incidents) snippet display the User
as UNKNOWN.
|
|
WIF-484
|
Detection of floating images is not supported when Optical Character
Recognition is enabled on NGFW or Prisma Access (Managed by Panorama or Strata Cloud Manager).
|
|
WIF-215
|
On Panorama, the original connection to the Service URL
FQDN is terminated before the connection to the new Service URL
FQDN can be established after reconfiguring the Service URL
Setting (DeviceSetupContent-ID).
|
|
PLUG-12944
|
After you upgrade Panorama and managed NGFW to PAN-OS 11.0.2, the Panorama plugin
for Enterprise DLP 4.0.1 you downloaded on Panorama prior to upgrade does not automatically install.
Workaround: After you successfully upgrade Panorama to PAN-OS 11.0.2, manually install the
downloaded Enterprise DLP plugin (PanoramaPlugins).
|
|
PLUG-12756
This limitation is addressed in Enterprise DLP version
3.0.4.
|
Predefined data filtering profile (ObjectsDLPData Filtering Profiles) File Direction
displays Default instead of
Upload.
|
|
PLUG-11837
|
On Panorama, downgrading from the following PAN-OS releases does not restore the default
Upload
File Direction for data filtering
profiles (ObjectsDLPData Filtering Profiles).
|
|
PLUG-10323
|
After you downgrade Panorama and NGFW to
PAN-OS 10.2.0 and Enterprise DLP plugin
3.0.0, the Non-File Based (ObjectsDLPData Filtering Profiles) setting for a data filtering profile configured
for non-file traffic data inspection erroneously displays as
enabled on the managed firewall CLI.
Workaround: Disable the Non-File Based setting on the data
filtering profile before downgrading to PAN-OS
10.2.0 and Enterprise DLP plugin 3.0.0.
|
|
PLUG-10172
|
On Panorama, the commit fails if the same profile (ObjectsDLPData Filtering Profiles) is being edited on Panorama and the DLP
app at the same time.
Workaround: If you experience a commit failure when
editing the data filtering profile on Panorama, you
must discard the edits, reset the Enterprise DLP plugin,
and reconfigure the data filtering profile.
|
|
PLUG-6159
|
On the Panorama, all Enterprise DLP
data profiles (ObjectsDLPData Filtering Profiles) are not displayed if you Remove
Config (PanoramaPlugins) for the Enterprise DLP plugin and install
the Cloud Services plugin.
Workaround: After you successfully Enterprise DLP
plugin configuration, log in to the Panorama
CLI and reset the Enterprise DLP plugin to
display the DLP data profiles.
|
|
PLUG-6121
|
On Panorama, Enterprise DLP data patterns and
profiles do not function as expected after you load or revert a
firewall configuration.
Workaround: After you successfully load or revert a NGFW configuration, log in to the Panorama
CLI and reset the Enterprise DLP plugin.
|
|
PAN-215405
|
File uploads to the Box application exceeding 20MB create
multiple sessions if the data filtering profile (Objects DLPData Filtering Profile Action is set to Block.
This results in the Box application requiring multiple retries
before the file upload is successfully attempted and blocked by
Enterprise DLP.
|
|
PAN-211913
|
Enterprise DLP does not support maintaining a session
connection to continue inspection if a file download is paused.
Enterprise DLP inspection is terminated for the file if
the download operation is paused.
|
|
PAN-206877
| The Gmail file attachment operation may sometimes get stuck or fail after multiple attempts if Enterprise DLP already scanned and blocked the file. |
|
PAN-142785
|
Enterprise DLP does not support custom response pages on Panorama and uses the default File Blocking Block Page
response page (DeviceResponse Pages).
|
|
PAN-140057
|
Enterprise DLP and IoT logs share log severity levels and
cannot be configured individually.
|
|
DIT-53549
|
Adding the predefined
Address - Cyprus data pattern to a
data profile that
includes National Id - US Social Security Number -
SSN data pattern results in inaccurate SSN
detections.
|
|
DIT-27539
|
(Enterprise DLP 3.0.3 only) Increasing the max file
size for the Enterprise DLP data filtering
settings to 21 MB or greater is supported only from
the Panorama CLI.
|
|
DOCS-7604
|
For structured data processing, Enterprise DLP doesn't
support detection of sensitive data in supported file types if
the sensitive data wraps due to the following:
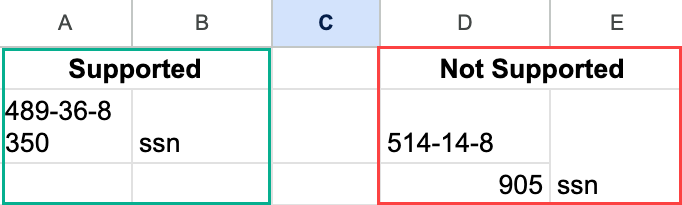
Consider the example below. Enterprise DLP can successfully
detect 489-36-8350 because the text
wrapping applied is through the spreadsheet app. Conversely, Enterprise DLP can't detect
514-14-895 because
895 was manually added to the
next cell.
|
|
DSS-25808
|
Enterprise DLP doesn't support detection of full Japanese
names written in Katakana script using the predefined
Names - Japan Full Name data
pattern.
|
|
DSS-24255
|
Audit logs (ConfigurationData Loss PreventionAudit Log) generated when a user views an Email DLP
incident (ConfigurationData Loss PreventionDLP Incidents snippet display the User
as UNKNOWN.
|
Endpoint DLP
|
Issue ID
|
Description
|
|---|---|
|
—
|
For endpoint devices running macOS, the Prisma Access Agent
inspects file movement within a USB peripheral device connected
to the endpoint device due to a macOS limitation that prevents
macOS from being able to determine the file operation source
path.
For example, you move a file from the endpoint device to
Folder A in the connected USB
device and the Prisma Access Agent inspects the file for
sensitive data. A few minutes later you move the same file from
Folder A to
Folder B. In this case, the Prisma Access Agent once again inspects the file for
sensitive data.
|
|
—
|
Printing from a Windows device only
If you have Evidence Storage
configured, Enterprise DLP gives you the option to
Download a file of the matched
traffic for further investigation when viewing your Endpoint DLP
incidents. The file downloaded from your evidence
storage bucket to the endpoint device will not contain the
.pdf file extension and as a
result you will not be able to open the downloaded file.
To open the file, navigate to the location on the endpoint where
the file was downloaded and edit the file name to append
.pdf. Editing the file name to
add the .pdf file extension will
allow you to open the file.
|
|
PANG-5687
|
Multiple DLP Incidents (ManageConfigurationData Loss PreventionDLP Incidents) can be generated for a single file move
operation from the endpoint and peripheral device. Some examples
of when this may occur are:
To prevent exfiltration of sensitive data, Enterprise DLP
inspects every file associated with the file move operation from
the endpoint to the peripheral device. This ensures that all
impacted files are captured in your logs and analyzed. However,
this may result in creation of unnecessary DLP Incidents.
|
|
PANG-5578
|
(Block policy rule for USB and Network Share Peripherals on
macOS only) The Prisma Access Agent automatically
moves a blocked file to the
following local folder on the endpoint for quarantine for 90
days when Endpoint DLP detects and blocks a file containing
sensitive data. The Prisma Access Agent automatically
deletes the file after 90 days.
/Library/Application
Support/PaloAltoNetworks/DLP/quarantine/
This applies to all file movement operations available on macOS.
Navigate to the local folder on the endpoint and move the file
to a different folder on the endpoint to recover the file.
|
|
PANG-5530
|
Installing the Prisma Access Agent on an endpoint device
with Cortex 8.3.0 or earlier installed generates an error titled
cytray.exe - Bad Image and
alerts the user that DLP is either not designed to run on
Windows or it contains an error.
This error can be ignored. It has no impact on the Prisma Access Agent installation or Endpoint DLP policy
rule enforcement. Click OK when prompted
to Finish the Prisma Access Agent installation.
|
|
PANG-5122
|
The Prisma Access Agent is unable to enforce policy rules
when the endpoint on which it is installed is in Safe Mode. As a
result, the Prisma Access Agent is unable to inspect and
block files moved between the endpoint and the peripheral device
if the endpoint is in Safe Mode.
|
|
DSS-17434
|
For printer peripheral devices, a data profile (ConfigurationData Loss PreventionData Profile) that includes an IDM document type (ConfigurationData Loss PreventionDocument Types) with a high matching value results in
Enterprise DLP being unable to render a match verdict for
inspected traffic.
Workaround: In your data profile, configure a low
matching value for IDM document
types to increase the likelihood of successful match verdicts
for printer peripheral devices.
|
