Download PDF
GlobalProtect
View the GlobalProtect App Troubleshooting and Diagnostic Logs on the Explore App
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
View the GlobalProtect App Troubleshooting and Diagnostic Logs on the Explore App
The chapter provides view the GlobalProtect app troubleshooting and diagnostic logs on
the explore app.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You must use the Explore app to view all GlobalProtect app
troubleshooting reports and diagnostic logs that are forwarded to Strata Logging Service from the end user’s endpoint. The details within the GlobalProtect app
troubleshooting and diagnostic logs help you to identify the root cause
and to resolve connectivity, network access, or performance issues.
- Retrieve the GlobalProtect app troubleshooting and log records forwarded to Strata Logging Service.
- Log in to the Palo Alto Networks hub and select Explore.Select Endpoint/GlobalProtect App Troubleshooting.View the entire troubleshooting or diagnostics log record.
- Click theicon next to the row.
![]() You can change the fields that are displayed in the log table, their order, which fields are pinned, and to use the Search field to quickly find specific fields in the troubleshooting log from the end user’s endpoint. For example, you can retrieve the endpoint serial number, hostname, username, or the endpoint’s unique host ID.
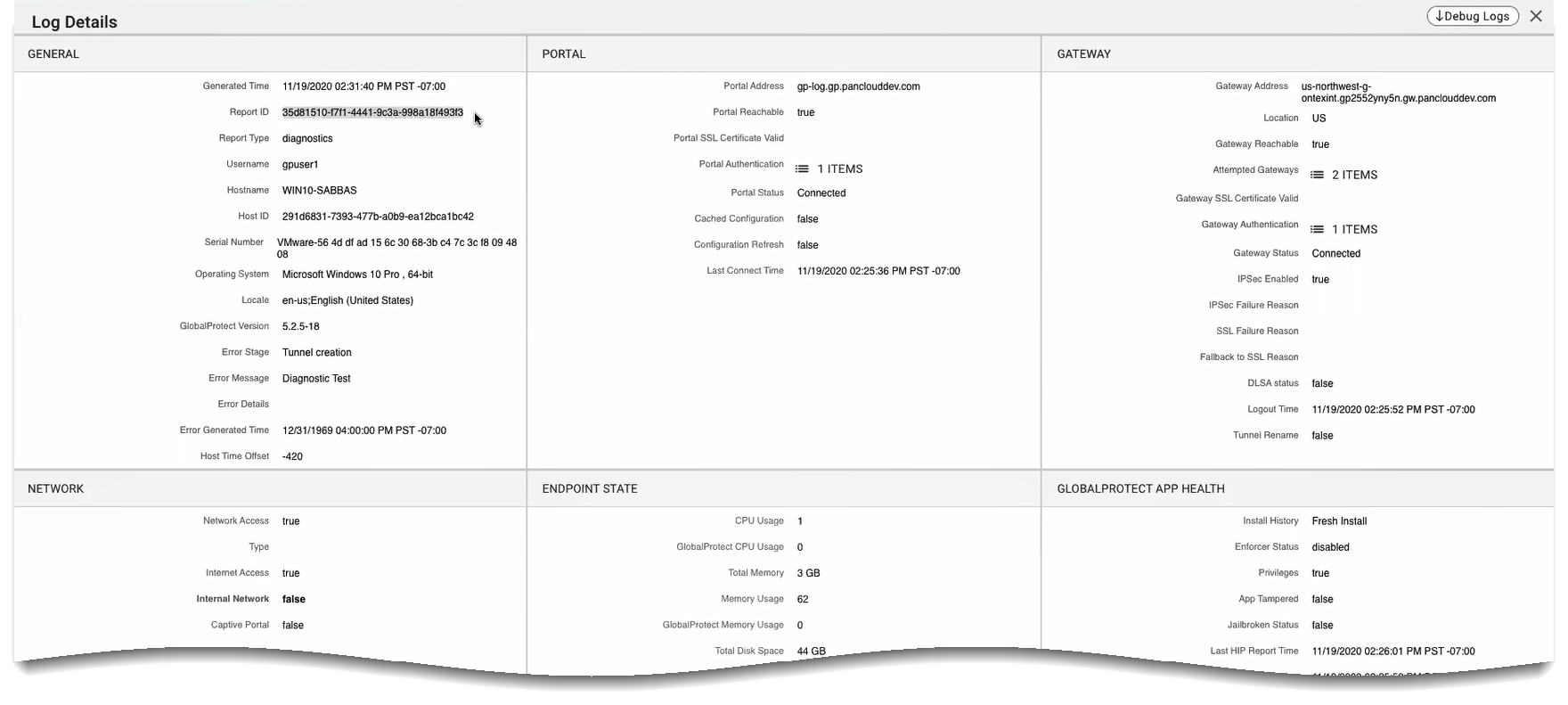
You can change the fields that are displayed in the log table, their order, which fields are pinned, and to use the Search field to quickly find specific fields in the troubleshooting log from the end user’s endpoint. For example, you can retrieve the endpoint serial number, hostname, username, or the endpoint’s unique host ID.![]() Verify the entire troubleshooting and diagnostics log record in the Log Details window. The log record may only include troubleshooting information or diagnostic log based on user consent.The individual log fields are placed into logical groupings. If you did not enable the app to run diagnostic tests and to include diagnostic logs, the log fields for the Endpoint State, GlobalProtect App Health, Gateway Network Impairments, and App Access Performance groups are empty.(Optional) If end users have consented to run diagnostic tests on the GlobalProtect app, click Debug Logs to download the GlobalProtect debug log files to your desktop for further analysis.You can unzip the GlobalProtect debug log files from the reportid_GlobalProtectLogs.zip zip package. You can enter the reportid search criteria in the Search field to quickly find reportid_GlobalProtectLogs.zip zip package.
Verify the entire troubleshooting and diagnostics log record in the Log Details window. The log record may only include troubleshooting information or diagnostic log based on user consent.The individual log fields are placed into logical groupings. If you did not enable the app to run diagnostic tests and to include diagnostic logs, the log fields for the Endpoint State, GlobalProtect App Health, Gateway Network Impairments, and App Access Performance groups are empty.(Optional) If end users have consented to run diagnostic tests on the GlobalProtect app, click Debug Logs to download the GlobalProtect debug log files to your desktop for further analysis.You can unzip the GlobalProtect debug log files from the reportid_GlobalProtectLogs.zip zip package. You can enter the reportid search criteria in the Search field to quickly find reportid_GlobalProtectLogs.zip zip package.![]()