IoT Security
Upload a List of Subnets with Only Static IP Addresses
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Upload a List of Subnets with Only Static IP Addresses
Assist IoT Security in discovering static IP devices
by uploading a CSV file containing a list of subnets with static
IP addresses.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In the case where an entire subnet consists
of static IP addresses, it’s more efficient to add a subnet and
define it as having static IP addresses than adding numerous static
IP devices individually. When you have multiple subnets with static
IP addresses, you can upload all of them in a CSV file at once.
There
is a limit of 10,000 subnets for each uploaded CSV file. If you
need to upload more than 10,000, upload multiple CSV files.
After
you provide IoT Security with a subnet configuration specifying
that it has static IP addresses and then IoT Security detects traffic
from a device in that subnet, it considers the device a static IP
device. Using the IP address as the device ID (instead of a MAC
address), it adds the device to its inventory. IoT Security adds
static IP devices to its inventory in this manner only for devices
that are not discovered through other detection mechanisms such
as ARP logs.
If you later remove a static IP subnet
after IoT Security added static IP devices for this subnet to its
inventory, IoT Security reverses this action and automatically removes
them from its inventory.
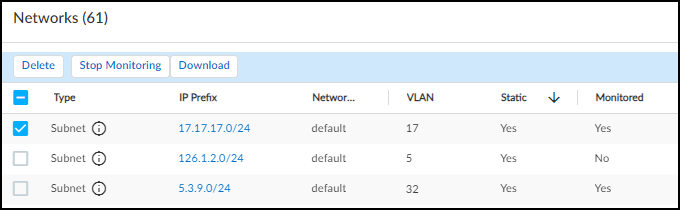
- Navigate to the Networks page (NetworksNetworks and SitesNetworks) and then click AddUpload Subnets.
- Click the link to download the CSV template.
- Fill out the template with subnet information.Enter the following for each subnet you want to upload:prefix: Enter the IP address of the subnet in dot-decimal notation and its netmask in CIDR notation (example, 10.1.1.0/24). This appears on the Subnets page, and for a device in this subnet, the subnet and netmask appear on the Devices and Device Details pages.vlan: (Optional) Enter a VLAN ID. If entered, this also appears on the Subnets page, and for a device in this subnet, it appears on the Devices and Device Details pages.description: (Optional) Enter a description of the subnet/VLAN, perhaps noting the type of devices for which it’s intended. These special characters are not allowed in the description field: ~ ` ! # $ % ^ & * + = { } [ ] | \ < > ? This description only appears on the Subnets page.static: Enter yes to define this as a subnet containing static IP addresses. When IoT Security discovers a device from a user-configured static IP subnet in a different L2 domain from the firewall and adds it to its inventory, the Source column on the Devices page shows User-Configured. (Leave it blank if you do not want the subnet to be static).monitored: Enter yes if you want IoT Security to provide device profiling, behavioral analysis, and risk monitoring of the devices in this subnet. Leave it blank if you only want IoT Security to detect the devices in the subnet and perform a simplified device identity analysis. Based on this field, the IoT Security portal displays Yes or No in the Monitored column in the Networks table on NetworksNetworks and SitesNetworks tab and provides the appropriate level of device monitoring, analysis, and protection.The Add a subnet option does not provide an option to specify a subnet as monitored or unmonitored. IoT Security automatically classifies an added subnet as monitored. However, you can change its classification after you add it by selecting the subnet and clicking Stop Monitoringabove the Networks table. You can also make multiple selections to stop monitoring multiple subnets at the same time. Later you can select unmonitored subnets and click Start Monitoring above the table.

- Upload the CSV file.On the Networks page, click AddUpload Subnets, choose or drag the completed CSV file onto the space in the dialog box, and then click Upload.If IoT Security previously detected network activity from an IP address in one of the uploaded subnets, it now considers it a static IP address and automatically adds a static IP device to the inventory on the Devices page. Similarly, if IoT Security later detects traffic from an IP address in one of these subnets, it automatically adds an entry to the inventory at that time.It can take several minutes for new entries to appear on the Devices page.