IoT Security
Firewall Deployment for Device Visibility
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Firewall Deployment for Device Visibility
Deploy your firewall so it can log network traffic data for DHCP flows and forward the
logs to Strata Logging Service.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The Palo Alto Networks IoT Security app uses machine learning to classify IoT
devices based on the network traffic for which these devices are either a source or
destination. To accomplish this, it relies on Enhanced Application logs (EALs) generated
by the Palo Alto Networks Next-Generation Firewall.
DHCP traffic is of particular importance to the IoT Security solution. DHCP
provides a way to create an IP address-to-device mapping (that is, an IP address-to-MAC
address mapping) that is required for classification to take place. However, a firewall
typically only generates an EAL entry when it receives a unicast DHCP message; for
example, when there is centralized Internet Protocol address management (IPAM) and
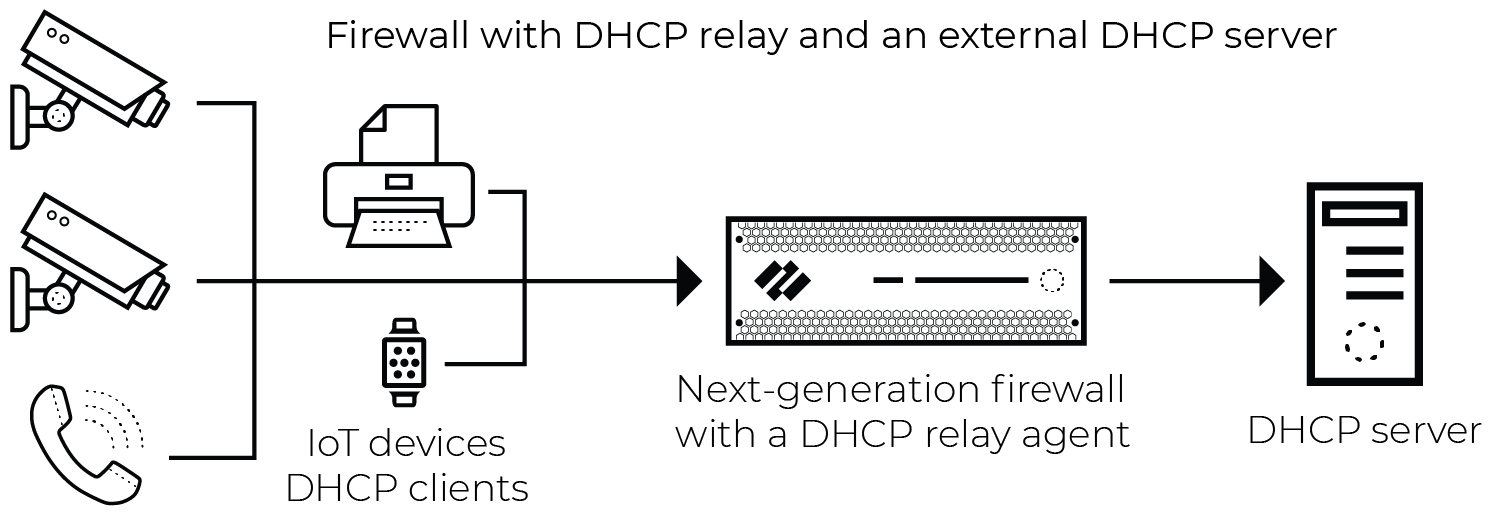
either the firewall or another local device acts as a DHCP relay agent. Below is an
example architecture that illustrates a common case where the firewall generates EALs
for unicast DHCP traffic.
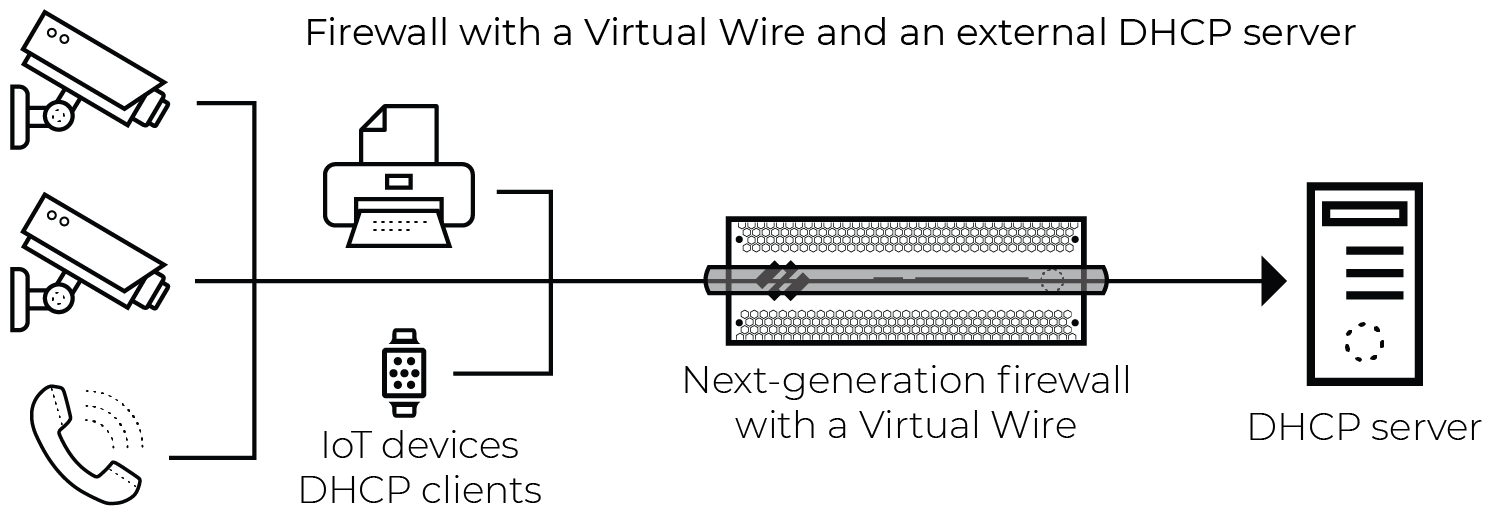
The firewall generates an EAL entry for broadcast DHCP traffic when the packet is seen
on a virtual wire (vWire) interface with multicast firewalling enabled, as shown below.
DHCP Data Collection by Traffic Type
Enhanced Application log (EAL) coverage differs when the firewall receives unicast and
broadcast DHCP traffic.
The tables below show Enhanced Application log (EAL) coverage when the firewall
interface receiving unicast and broadcast DHCP traffic is in different modes.
Unicast DHCP Traffic
| Firewall Interface Deployment Mode | DHCP EAL Generated |
|---|---|
| Virtual Wire | Yes |
| Tap | Yes |
| Layer 2 | Yes |
| Layer 3 | Yes |
Broadcast DHCP Traffic
| Firewall Interface Deployment Mode | DHCP EAL Generated |
|---|---|
| Virtual Wire | Yes |
| Tap | No |
| Layer 2 | No |
| Layer 3 | No |
| DHCP server on the firewall (L3, L2 with VLAN interface) | Yes* |
| DHCP relay agent on the firewall (L3, L2 with VLAN interface) | Yes |
A firewall running a PAN-OS 10.0 release or later natively generates EALs when a
DHCP server is configured on an interface,
DHCP Broadcast Session is enabled, and there’s a Security
policy rule that allows DHCP traffic to reach the server and has EAL forwarding
enabled. For more information, see
Prepare Your Firewall for IoT Security and
Configure Policies for Log Forwarding.
