IoT Security
Sites and Site Groups
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Sites and Site Groups
Create and manage sites for IoT Security protection and
organize them into groups.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Only users with owner privileges can create and
manage sites, organize sites into groups, and assign access to sites
and site groups to other users.
Log in as a user with owner privileges and select NetworksNetworks and Sites Sites. There you can add, view, edit, and delete sites with devices under
IoT Security protection.
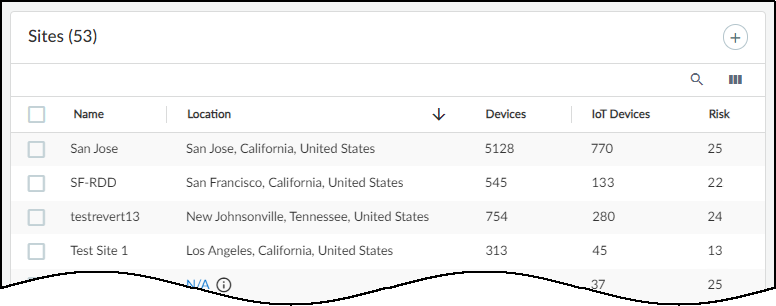
There are three sections on the Sites page:
- At the top is a title bar with titles for the Networks, Network Segments Configuration, and Sites tabs. There is also a global filter that controls the content displayed on the page by site and time range.
- The Organization section shows the hierarchical structure of sites in your organization.
- The Sites section is a table with useful information about individual sites.
The Default site is where IoT Security initially assigns IP address blocks and
subnets. You can later reassign them to user-defined sites.
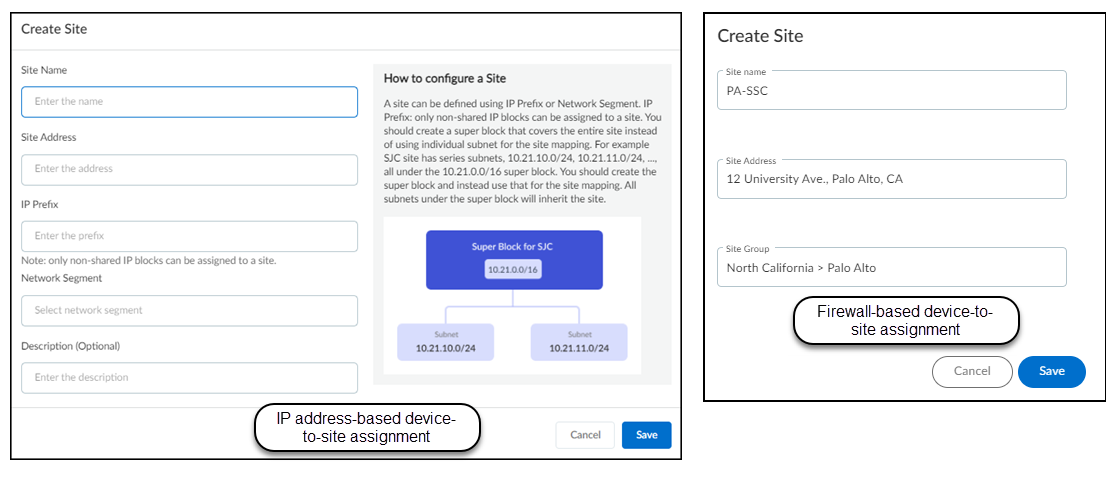
To add a new site, click + above the table. There are different settings
based on the device-to-site assignment method
that’s in use. When assigning devices to sites by IP address, enter a site name,
optionally enter a site address and description, choose either the IP prefix of an
non-shared IP block or previously defined network segment, and then
Save. When assigning devices to sites by firewall, enter a
site name, optionally enter an address for the site and (if you’re organizing sites into
groups) choose a site group, and then Save.
To edit or delete a site, click the three vertical dots at the
far right of a site row and then click one of the actions that appear.
When assigning devices to sites based on firewalls, there are two
additional options. You can assign one or more firewalls to a site
or unassign a site from a group.
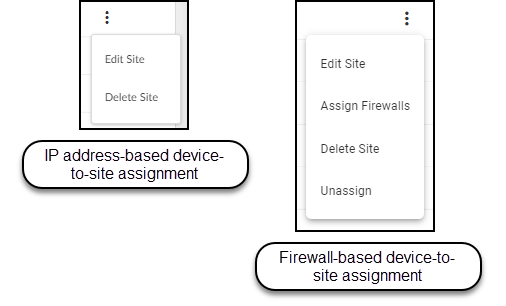
Before you can delete a site, you must first remove all
firewalls from it or reassign them to different sites.
Organize Sites into Groups
You have the option to organize your sites into groups
within a hierarchical structure and then set controls at different
levels within the structure to define what administrative users
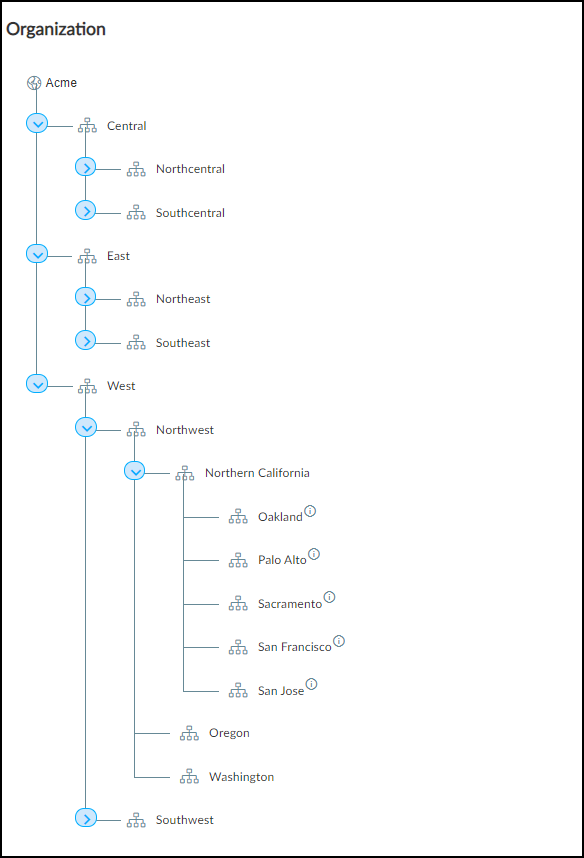
see and do. For example, in the tree structure shown below, you
might give a user access to data at an individual site level, or
for all sites in a city, or in a state, or within a broader region.
You don’t have to organize sites into groups. In fact, by default, the Organization panel is
hidden on the NetworksNetworks and SitesSites page. If you want, you can assign users access on a per-site basis
without the use of site groups. However, if you want to see the Organization panel
and use this feature, click Show Organization and then click
Organize Sites.
Add Groups to the Tree and Add Sites to Groups
Only a user with owner privileges can add, edit,
and delete groups and add sites to them.
There can be five levels in a group hierarchy. The root node
forms the top-level group (“Acme” in the examples here) and is the
group to which all sites belong by default. By default, it’s the
name of the tenant account and cannot be removed, but it can be
renamed. All other groups below the root are completely owner-defined.
To add a group to the organization, hover your cursor over an
existing group, click the Add group icon,
and then enter a new name. To change its name, click the three dots
(...) next to the Add group icon and then
click Rename.

The global filter has priority over page-level filters.
When creating the tree structure, be sure that the global filter
at the top of the page is set to All Sites.
If it’s set to anything else, the Organization panel will keep collapsing
to show only whatever site or sites were selected in the global
filter.
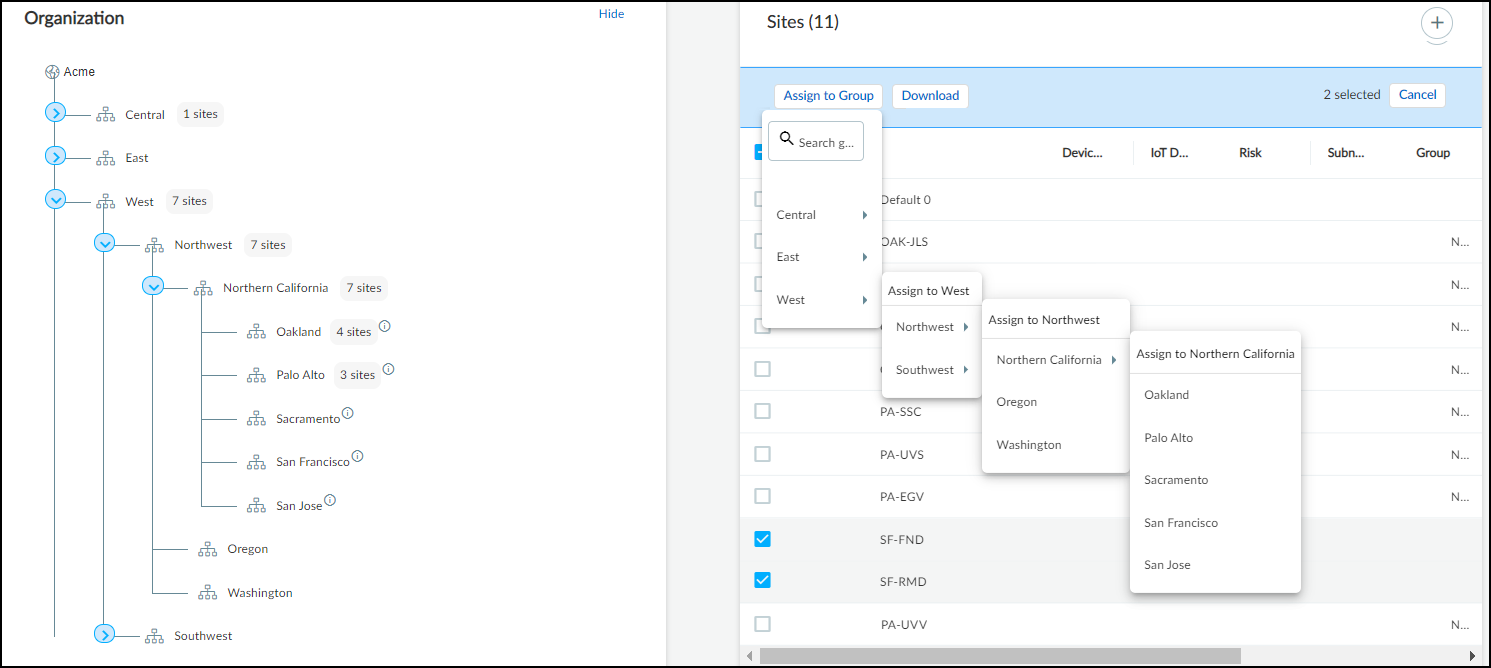
Add groups and subgroups as needed to reflect the structure of
your organization. After adding the groups you need, add sites to
them. Select the check box for one or more sites in the Sites panel,
click Assign to Group, and then choose the
one to put them in.
You can search for a group by typing its name in the Search
groups field at the top of the Assign to Group drop-down menu.
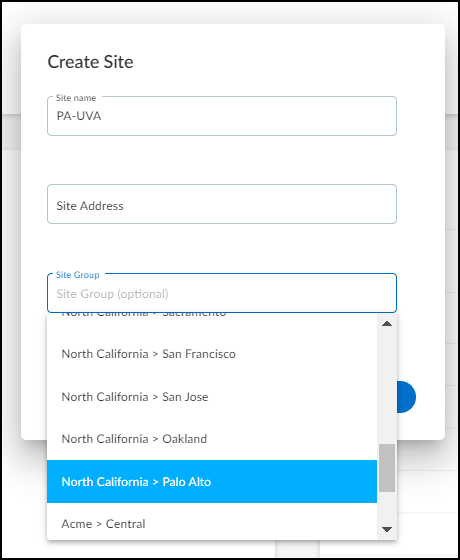
In addition to adding existing sites to groups, you can also add new sites to groups. When
creating a new site (NetworksNetworks and SitesSites+), the Site Group option lets you assign the site to an existing
group, thereby combining site creation and group assignment in a convenient
one-step process.
Reassign Sites and Delete Groups
If you later want to reassign a site from one group
to another, use the same process for adding it to a group but select
the other group from the list.
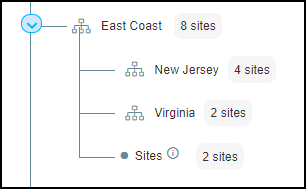
When you assign a site to a group that also has subgroups, a
node labeled Sites appears in the tree under its assigned group
at the same level as the subgroups. For example, notice how the
group named East Coast has two subgroups—New Jersey and Virginia—and
it also has a node called Sites for two sites assigned to the East
Coast group.
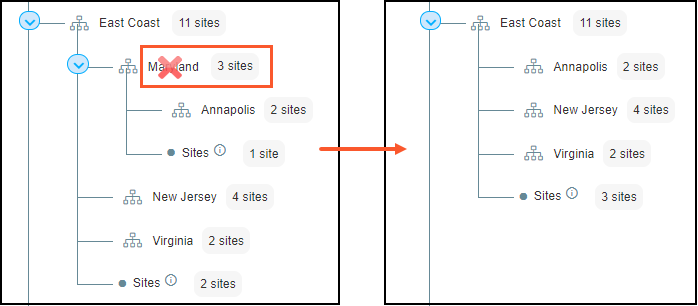
If you delete a group, IoT Security reassigns all its sites
and child groups to its parent group. For instance, look at what
happens when the Maryland group is deleted. The site that belonged
to Maryland now belongs to East Coast, and its child group Annapolis
becomes a child group of East Coast.
To avoid IoT Security automatically reassigning a site when its
group is deleted or simply to remove it from a group, click the
three vertical dots at the far right of its row in the Sites panel,
and either click Edit Site to reassign it
to another group or click Unassign to remove
it from its current group and put it into the root node.
Use Groups to Filter and Control Access to Data
After you finish creating the organizational structure
and assigning sites to groups, you can use the tree to filter what
to display on the Sites page. Click any group name in the tree to
display sites belonging to it in the Sites panel on the right. The
sites that are displayed either belong directly to the group or
are in one of its child groups. (To remove the filter, click the
X to the right of its name at the top of the Sites table.)
Not only can you use groups to filter the sites displayed on the NetworksNetworks and SitesSites page, but you can also filter by group on the
Devices page.

In the drop-down list for the sites global filter, click a group
name (in blue) and then click either Select All to
see devices at all sites in the selected group or click a specific
site to see devices just at that site.
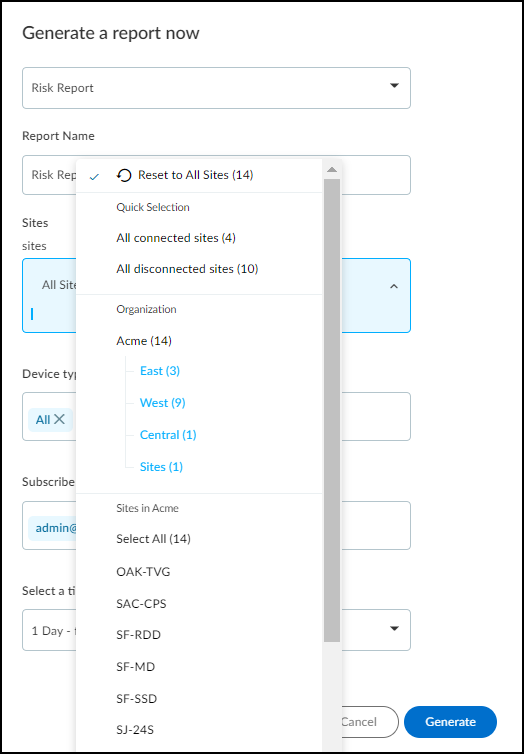
You can also select a group or site when defining the scope of
a report at ReportsFiles
and Settings+ and
clicking Generate a report now or Schedule
a report for later.
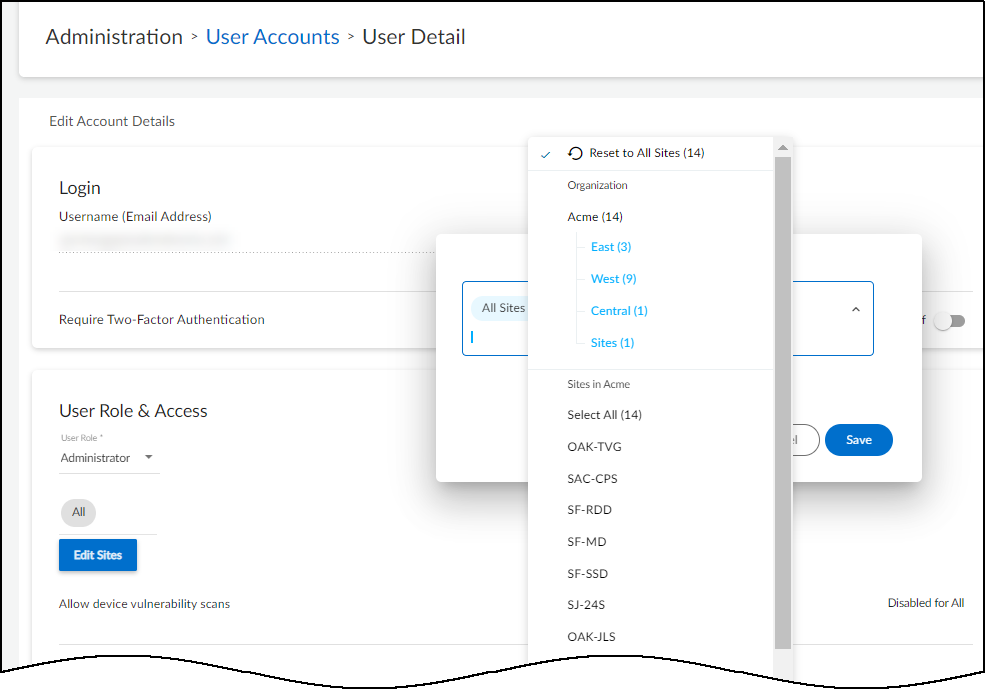
When logged in as a user with owner privileges, you can use groups
to control which sites other users are allowed to access. Do this
in the User Role & Access section on the user account settings
for a user by clicking AdministrationUser Accounts > username.
By default, all users have access to all groups and sites.
However, after a user with owner privileges gives other users access
to one site or group, that’s all they can access. If that site or
group is ever deleted, these users won’t return to having default
access to everything. Instead, they won’t be able to access anything;
that is, until they’re given access to something else. On the other
hand, users with owner privileges always have access to all groups
and sites in their account.
