IoT Security
IoT Security Solution Setup
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
IoT Security Solution Setup
Set up the multiple components that constitute the IoT Security solution.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The following is an overview of the main steps involved
in setting up the IoT Security solution with particular focus on
the following three components:
- Palo Alto Networks Next-Generation Firewalls with or without Panorama management
- Logging service with or without a Strata Logging Service instance
- IoT Security application
The solution also makes use of the update server for device dictionary file updates and
the Customer Support Portal and hub for IoT Security
user management. Optionally, IoT Security integrates with Prisma Access and SD-WAN and, through XSOAR,
with third-party products.
Learn about the main steps involved in the IoT Security solution
setup:
1 - Check Firewall Support and Prerequisites
2 - Onboard IoT Security
3 - Prepare Firewalls
4 - Install Certificates and Licenses
5 - Configure Logging
1 - Check Firewall Support and Prerequisites
Most current Palo Alto Networks firewall models support IoT Security with a few
exceptions.
Although IoT Security is a cloud application and is always running its latest software version,
make sure the firewall models and PAN-OS versions on them support the level of
functionality you want.
In addition, there are several prerequisites. For example,
each firewall that integrates with IoT Security must have an IoT Security
subscription. Not all firewalls on your network must subscribe to IoT Security; only
those that collect network traffic and forward logs to it and those after PAN-OS
10.0 that receive policy rule recommendations and IP address-to-device mappings from
it.
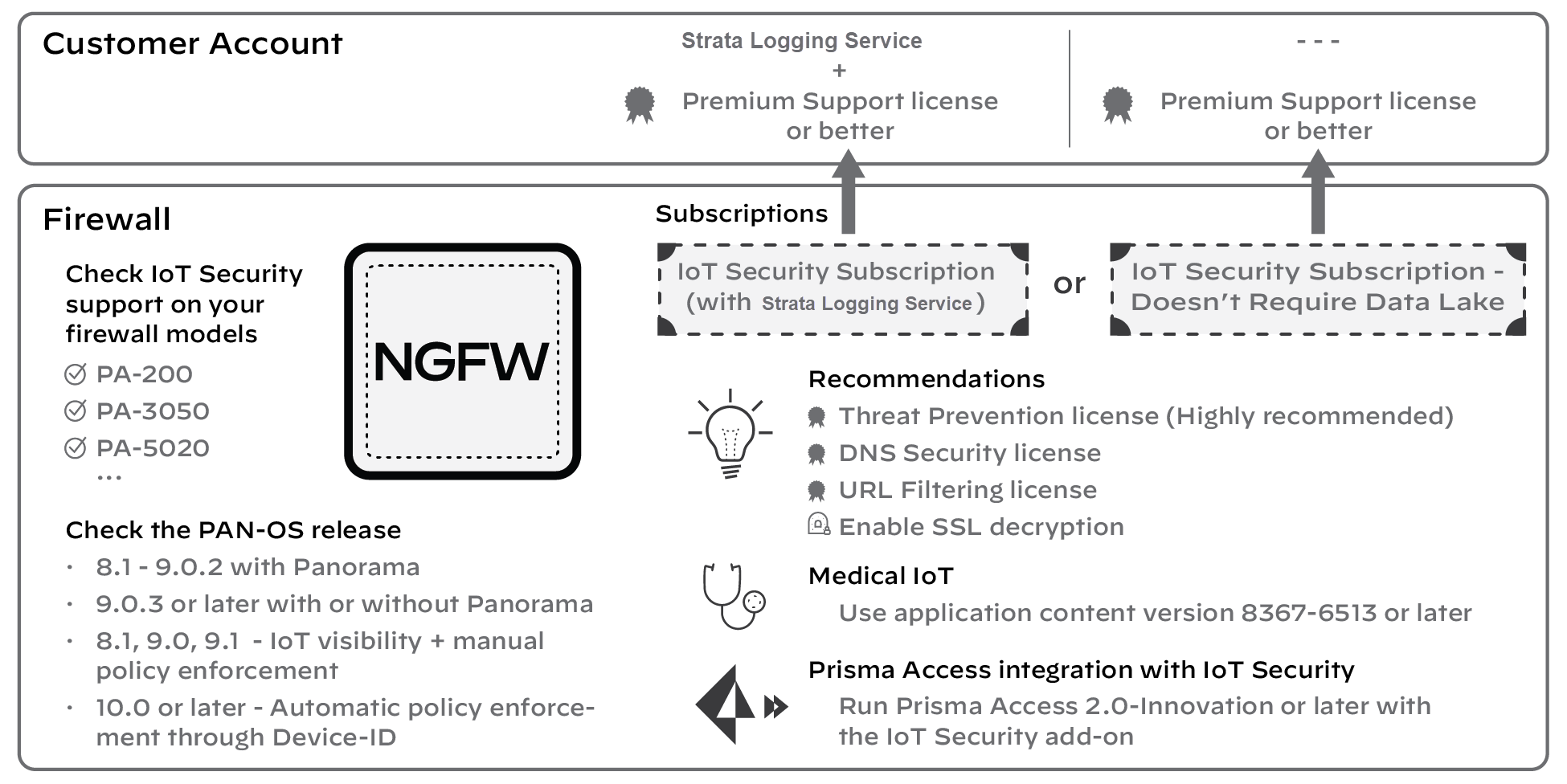
Detailed Instructions
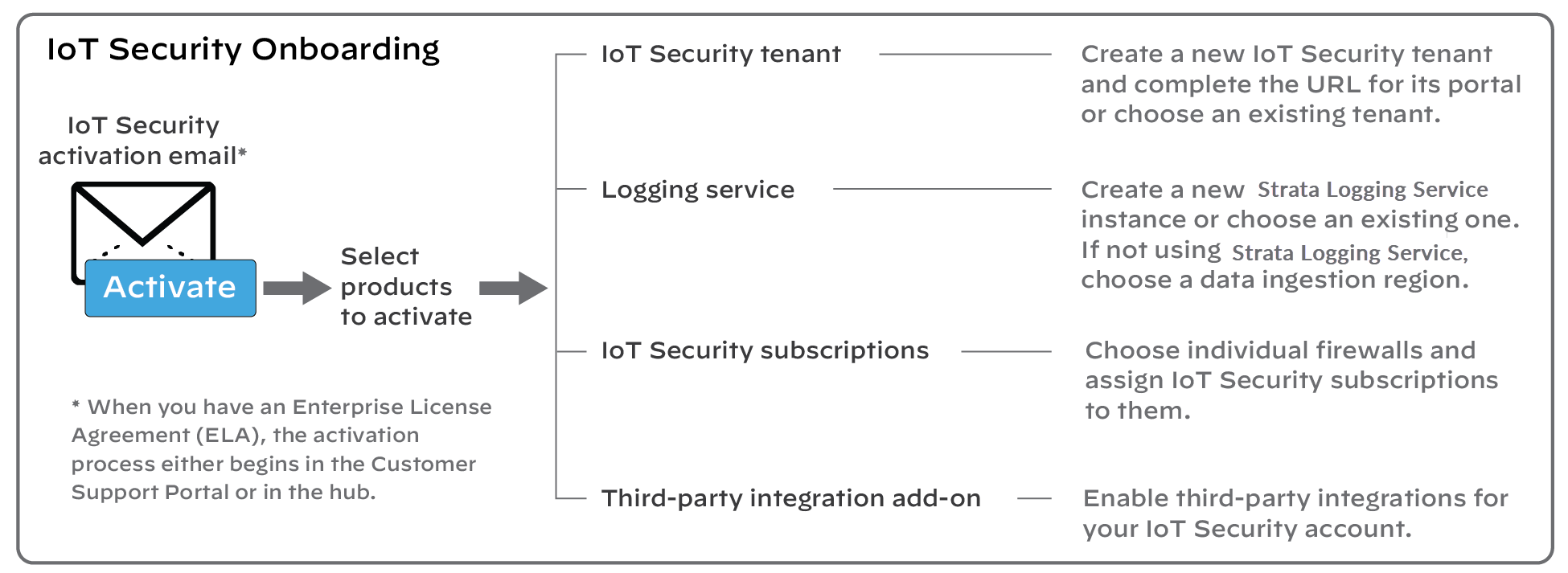
2 - Onboard IoT Security
IoT Security onboarding is a six-step process that starts
from an Activate link in an email from Palo
Alto Networks. (If you have an Enterprise License Agreement, it
starts either in the Customer Support Portal or in the hub). During
the IoT Security onboarding process, do the following depending
on what you’re activating:
- Create an IoT Security tenant
- (IoT Security Subscription) Activate a new Strata Logging Service instance or associate an existing one with your IoT Security tenantor(IoT Security Subscription - Doesn’t Require Data Lake) Specify the data ingestion region
- Subscribe firewalls to IoT Security services
- Optionally activate a third-party integrations add-on

Detailed Instructions
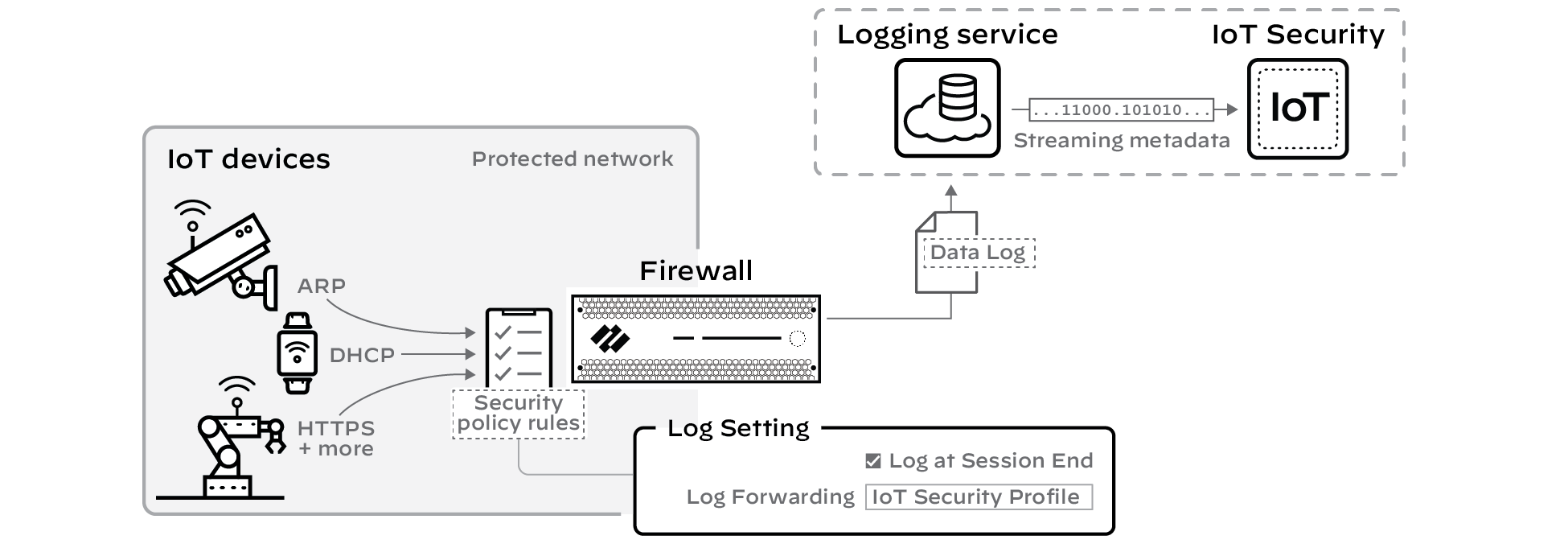
3 - Prepare Firewalls
For IoT Security to discover network-connected devices
and assess their network behavior patterns, it needs quality network
metadata from next-generation firewalls. Therefore, it’s essential
that firewalls are placed on the network and configured to collect
metadata from traffic and forward it for IoT Security to access.
In particular, DHCP traffic is important because it links dynamically
assigned IP addresses to device MAC addresses, making them trackable
over time.

Firewalls must also provide IoT Security with metadata for other
types of traffic that devices generate. They do this by enforcing
policy on network traffic, creating logs, and then forwarding them
to the logging service, which then streams the metadata to IoT Security.
Detailed Instructions
4 - Install Certificates and Licenses
Logging service and device licenses permit next-generation
firewalls to connect to the logging service and IoT Security. Logging
service and device certificates authenticate these connections.
Firewalls need these licenses and certificates to integrate with
IoT Security.

Firewalls running PAN-OS 8.1–10.0 use logging service certificates
to secure communications with the logging service so they can forward
various logs to
it. From PAN-OS 10.0, when Device-ID was
introduced, firewalls use device certificates to secure communications
with IoT Security to get IP address-to-device mappings and recommended
policy rules. (Note: Panorama-managed firewalls can get recommended
policy rules either directly from IoT Security or indirectly from
IoT Security through Panorama.) From PAN-OS 10.1, firewalls use
just one device certificate to secure connections to both the logging
service and IoT Security. Panorama also uses a device certificate
to secure communications with IoT Security.
Detailed Instructions
5 - Configure Logging
Configure Security policy rules on firewalls to log traffic and forward logs to the logging
service where IoT Security accesses it. The more network traffic metadata IoT Security has for analysis, the more quickly and confidently it identifies devices
and establishes a baseline of their normal network behaviors. This results in a
broader application of Security policy rules based on Device-ID (IoT Security sends
firewalls IP address-to-device mappings only when it has a high confidence in their
identities and the devices have sent or received traffic within the past hour) and
broader and deeper insight into device risk and real and potential security
threats.
Detailed Instructions