IoT Security
MDS2
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
MDS2
Upload MDS2 files that IoT Security can use to detect
vulnerabilities and security alerts in medical IoT
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Medical device vendors often list the security-related features of their
products in Manufacturer Disclosure Statement for Medical Device Safety (MDS2) forms,
which they share with their customers. Vendors issue these MDS2 documents for each
version of a medical device and include valuable information such as whether a device
processes PHI (personal health information); if it stores PHI and, if so, if it's
encrypted; and if antivirus software is installed on the device.
Over time, healthcare providers can collect thousands of MDS2 documents for
thousands of medical devices. When used as intended, MDS2 documents can greatly enhance
your security posture and incident response (IR). However, absorbing the details from
these documents for the specific version of the software running on their connected
devices is a daunting task. As a result, MDS2 files often go unused.
IoT Security simplifies the management and use of the MDS2 files you
have. If you upload an MDS2 file for a device to IoT Security, it then includes
this data along with other environmental factors when assessing the risk to the device.
For example, if the software version of a device specified in an MDS2 file has a known
vulnerability, IoT Security more precisely identifies it as a vulnerability
instead of just a potential vulnerability. IoT Security supports MDS2 files in
2004, 2008, 2013, and 2019 formats.
You can upload MDS2 files to IoT Security and use files shared by other IoT Security
users through the MDS2 community. To join, select VulnerabilitiesMDS2, click Learn More, read about how the MDS2
community works, and then click Join Now. After that, IoT Security scans the community and shows previously uploaded MDS2 files from
other community members that match your devices. At the same time, Palo Alto Networks
security engineers review any MDS2 files that you've already uploaded. If they are
approved, IoT Security then shares your files with other community members. In
this spirit of cooperation, everyone benefits from the files shared with each other.
If members upload duplicate MDS2 files (that is, more than one file applies to the same
vendor, profile, and model), IoT Security uses the following logic in order from
the top to prioritize one over another and automatically apply it to your devices:
- If an MDS2 file is excluded, do not use it.
- Use a manually selected MDS2 file over an automatically selected file.
- Use an MDS2 file that you uploaded.
- Use an MDS2 file that’s shared in the community.
- Use a version of an MDS2 file released later than another version.
- Use a later format version of an MDS2 file over an earlier format; for example, use a 2017 MDS2 file instead of a 2013 format version.
When you select VulnerabilitiesMDS2 after joining the MDS2 community, IoT Security displays the MDS2
Files Matched page. This lists the MDS2 files that match medical IoT devices in the IoT Security inventory. You can navigate from here to a page with MDS2 files that
you previously uploaded, a page with files uploaded by other IoT Security
customers, and a page listing medical IoT devices that match the MDS2 files here.
On VulnerabilitiesMDS2, you can view files that match medical IoT devices in the inventory,
download them, and exclude them if you don't want IoT Security to apply them to
your medical IoT devices. You can also download a complete list of all uploaded MDS2
files or a list of one or more selected files.

To upload a file, click the Upload icon
(
 ), navigate to an MDS2 file in
PDF format, and then select and upload it.
), navigate to an MDS2 file in
PDF format, and then select and upload it.
IoT Security matches the uploaded MDS2 file with devices that
share the same model, vendor, and profile as those specified in
the file. Although you can upload an MDS2 file on the Device Details
page, IoT Security only applies the MDS2 file to that individual
device. On the other hand, if you upload an MDS2 file on the MDS2
page, IoT Security searches its inventory for all devices with the
same model, vendor, and profile attributes and applies the MDS2
file to all matched devices. Furthermore, if new devices are added
to the inventory later, IoT Security will apply the MDS2 file to
those devices as well.
Clicking a number in the Matched Device column opens the Devices
page with a filter applied to show just those devices that match
the MDS2 file.
The number in the Matched Device column on the MDS2 page
is the total for all sites. If you have administrative access to
device data for a subset of sites, the number of matched devices
on the Devices page might be smaller than the number on the MDS2
page.
To view some details about an MDS2 file, click the entry in the
File Name column. An information panel slides open on the right
side of the main window listing the three attributes that IoT Security
uses to map the MDS2 file to devices. Below this, it lists several
key points about the device, the document, and security.
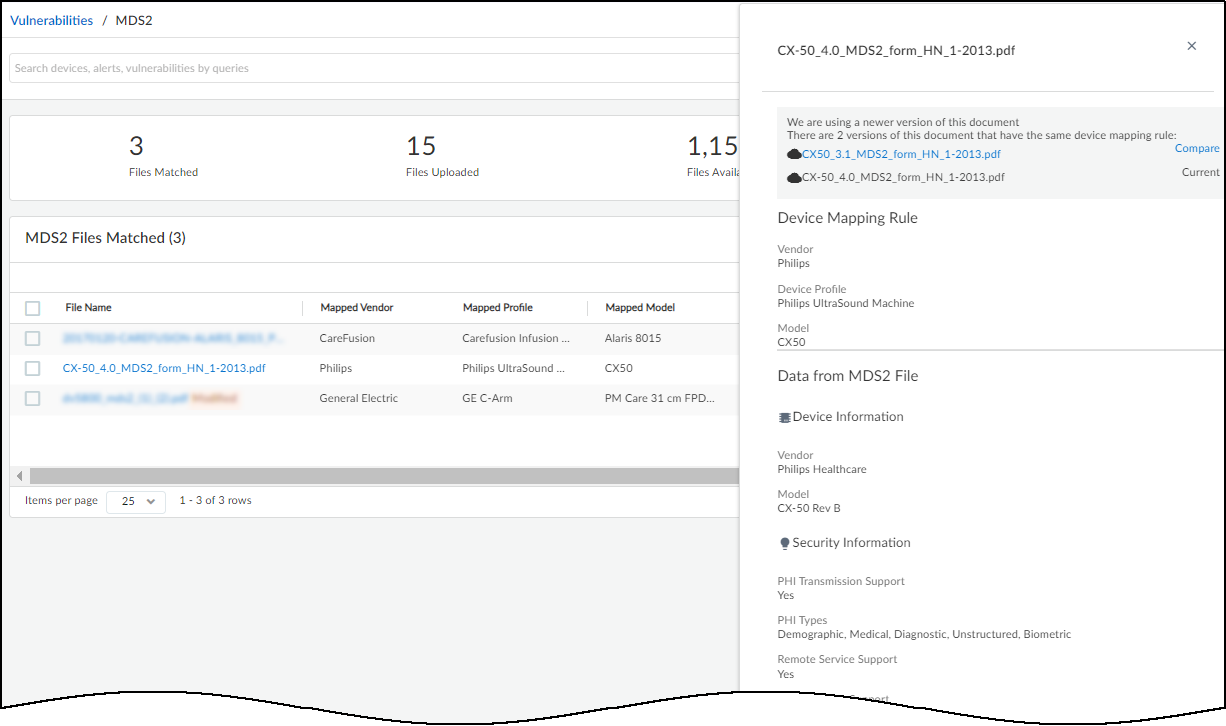
When you upload a MDS2 file, check if there are any inaccuracies among the device mapping rule
values. It’s possible that text alignment issues in the PDF cause characters to be
parsed incorrectly. If that happens, IoT Security won’t be able to match the MDS2
file with devices. In such cases, click Edit to the right of
Device Mapping Rule, modify the text as necessary, and then click
Update.
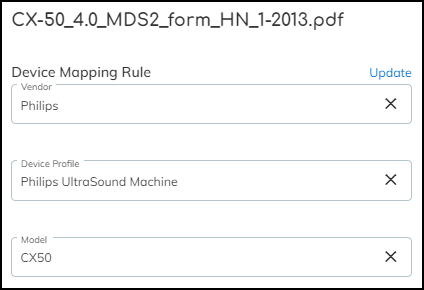
In addition to the values in the Device Mapping Rule, you can
edit other attributes in the MDS2 file if they were parsed incorrectly
as well. Whenever you click Update—either
for changes to Device Mapping Rule or Data from MDS2 File—IoT Security
immediately removes any previous matches for the MDS2 document and
runs the matching process again.
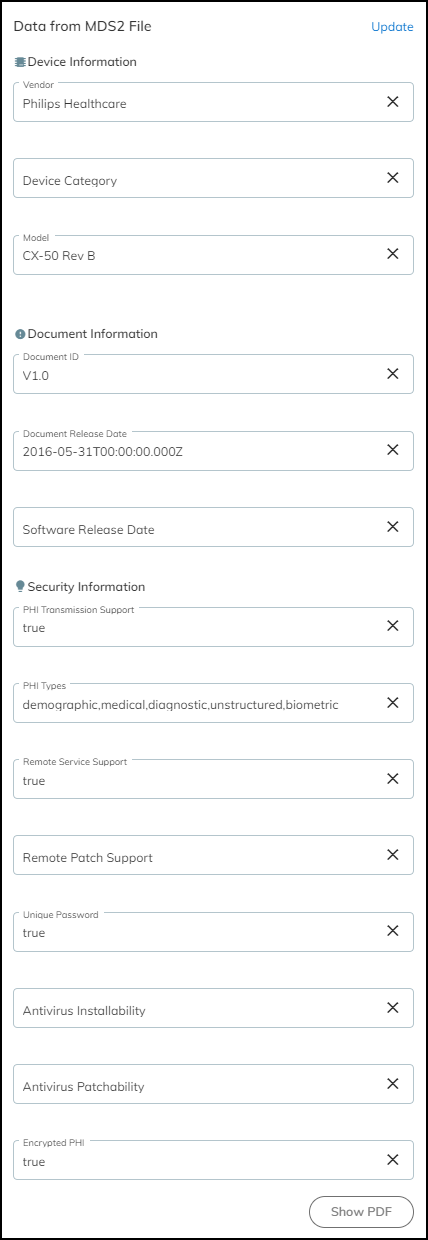
To view an entire MDS2 file in PDF format, click Show
PDF in the information panel.
To download the PDF, click the Download icon
(
 ) at the top of the PDF viewer.
) at the top of the PDF viewer.
To close the information panel (and PDF viewer if it’s also open),
either click the X in the upper right corner or click the file name
again.
To download a list of all uploaded MDS2 files in a .csv file,
click the Download icon (
 ) above the MDS2
table. To download a list of one or more MDS2 files in a .csv file,
select check boxes of the ones you want to download and then click Download.
) above the MDS2
table. To download a list of one or more MDS2 files in a .csv file,
select check boxes of the ones you want to download and then click Download.
To delete one or more previously uploaded MDS2 files, select
the check boxes of the files to delete and then click Remove.
