IoT Security
Utilization Dashboard
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Utilization Dashboard
The Utilization dashboard provides quick access to statistics
about medical IoT device operations.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
When the IoT Security
portal theme is
Medical IoT Security, you can see the Utilization dashboard. IoT Security gathers utilization statistics and metrics about the medical
IoT devices it is monitoring and displays them on this dashboard.
You can then leverage this data to minimize device downtime, reduce
total cost of ownership (TCO), and increase revenue through better
capital planning. In addition to minimizing downtime and maintenance,
you can also use the gathered data to identify unused assets (possibly
broken or misplaced) and ensure safe and secure device disposal
at the end of the IoT device life cycle.
Make sure the application content version on
your firewalls is 8367-6513 or later; that is, the major version,
which is identified by the first four digits, is 8367 or above (8368,
8369, 8370, and so on), starting from 8367-6513. These versions
include healthcare-specific applications that allow IoT Security
to discover medical equipment and provide utilization data. They
also allow firewall security policy rules to include healthcare-specific
applications.
To view the Utilization dashboard, select Dashboards and then choose
Utilization from the Manage Dashboards
drop-down list.
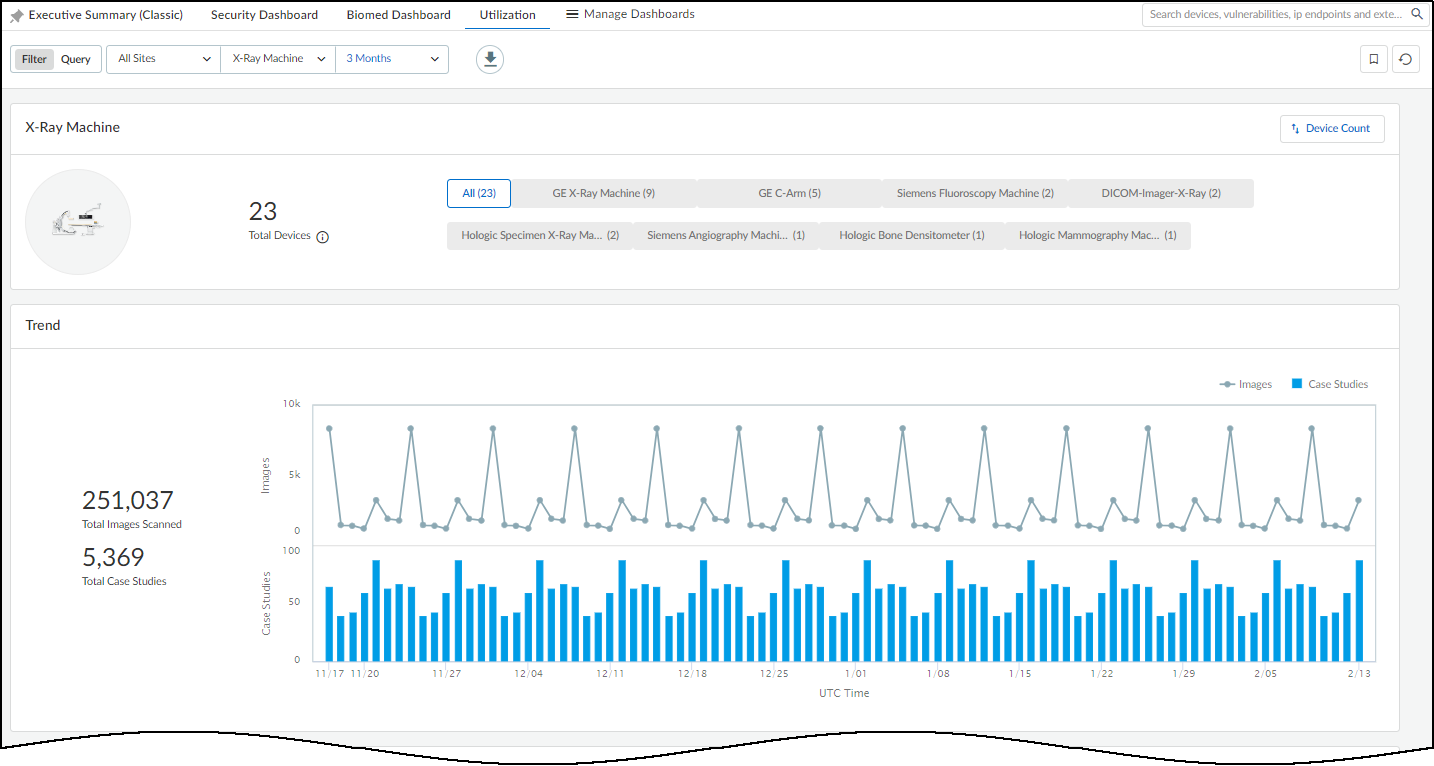
The dashboard is organized into two broad sections. At the top
is a set of filters for
sites, medical IoT device categories, and time ranges that control what
appears on the page. Below the filters are information panels that
display various types of information about how medical IoT devices
are being utilized.
In addition to viewing the dashboard in the IoT Security portal,
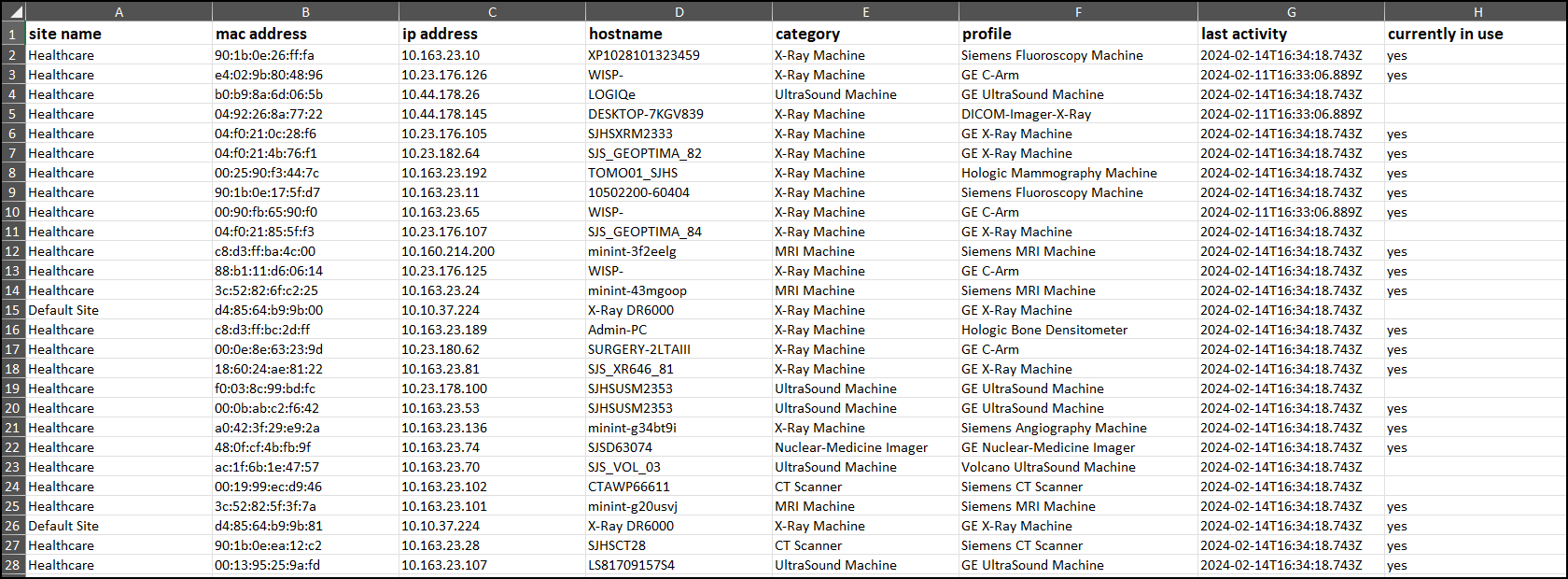
you can download its data as an Excel spreadsheet. Click the Download icon
to the right of the top filters, set the filters to include the
data you want to save, and then click Download.

IoT Security creates an Excel file with the details you specified
on multiple tabs and makes it available for download.