IoT Security
Create a Policy Set in IoT Security
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Create a Policy Set in IoT Security
Recommend an automatically generated policy set for permitted
IoT device network behaviors to your firewall.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
IoT Security provides the automatic generation
of policy rule recommendations to
control IoT device traffic. The recommendations are based on the network behaviors of
all the high-confidence IoT devices in the same device profile in
your local network environment as well as that of devices in the
same profile in other IoT Security tenant environments.
High-confidence
devices are those whose identity IoT Security is highly confident
about and has calculated a confidence score of 90-100%. IoT Security
has three confidence levels based on calculated confidence scores:
high (90-100%), medium (70-89%), and low (0-69%).
After
allowing sufficient time for IoT Security to collect the full behaviors
of IoT devices in a profile, you’re ready to create a set of policy
rule recommendations for it.
From PAN-OS 11.1, there's a different process for recommending
Security policy rules to next-generation firewalls from that described here. The
following workflow remains applicable to firewalls running PAN-OS versions prior
to PAN-OS 11.1.
- Log in to the IoT Security portal and select AssetsProfiles > profile_name > Behaviors.
- Review the data on the Behaviors page, choose Outbound Behaviors, and then click Create Policy.For a description of the content on the Behaviors page for a device profile, see Device Profile Behaviors.You can also create a policy set by navigating to the Profiles page, hovering your cursor over a profile name, and then clicking Create Policy Set in the information pop-up that appears.
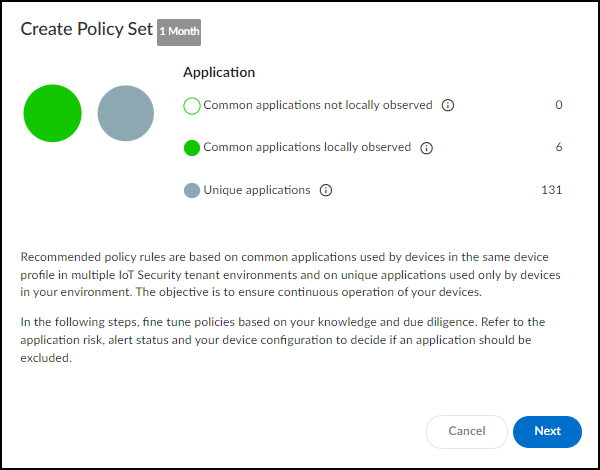
- Read the introduction to the creation of a Security policy rule set that IoT Security can recommend to next-generation firewalls and then click Next.

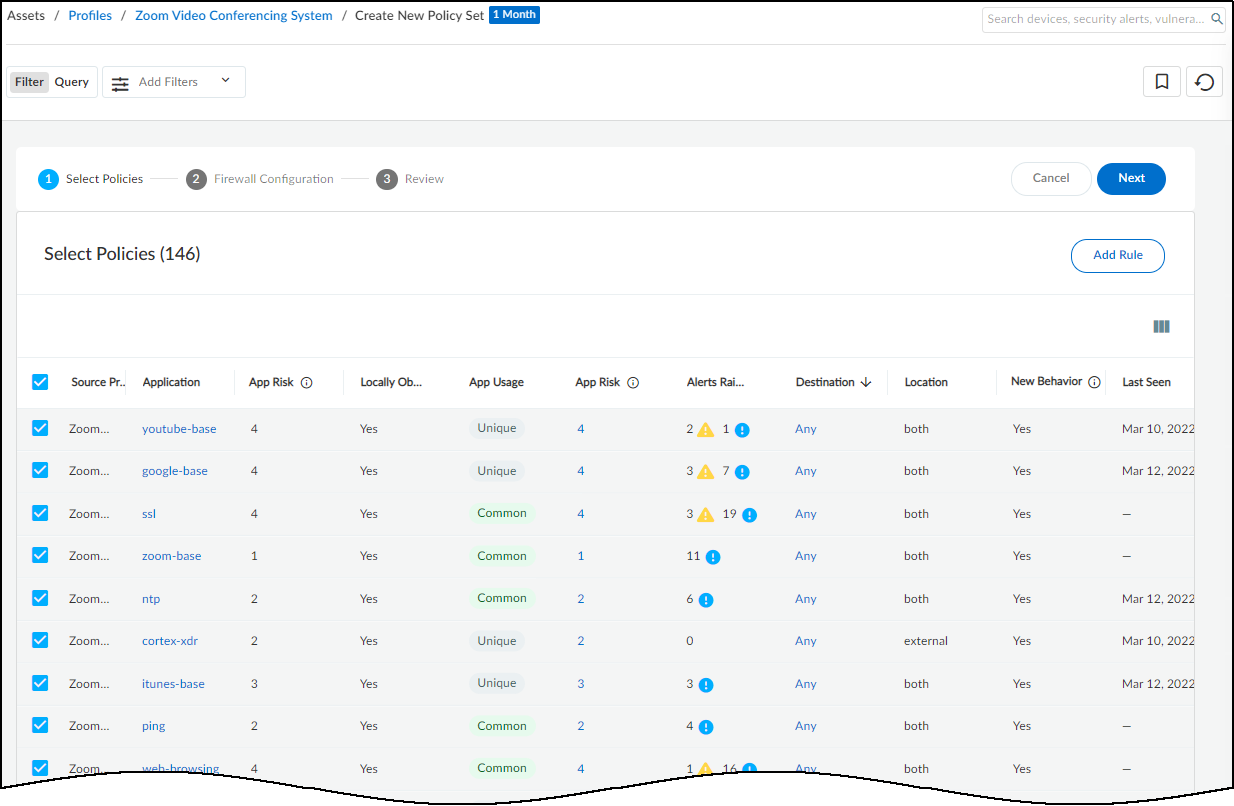
- Select the recommended policy rules to include in the policy set.IoT Security automatically generates a list of policy rule recommendations. These are based on common applications that devices in the same device profile in multiple IoT Security tenant environments use and on unique applications that only devices in your environment have used during the last month (note the 1 Month label to the right of the breadcrumbs at the top of the page). The rule recommendations are organized by application with all rules selected by default. Clear any you don’t want to use based on your organization’s policy and practice as well as the information provided.
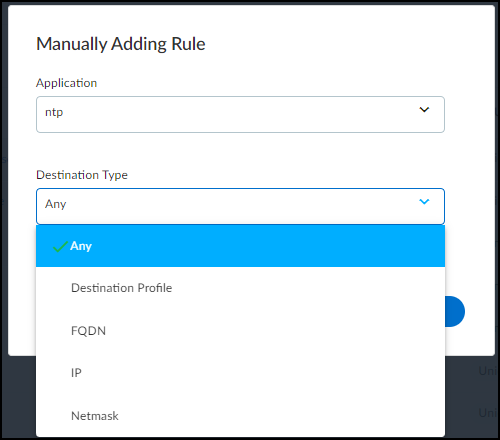
 In addition to the automated policy rules that IoT Security generates based on observed network behaviors of devices in the same profile, you can manually add other rules to the set. In the policy set creation workflow, click Add Rule and then set an application and destination. By default, Any appears in both the Application and Destination Type fields. To change the application, delete Any and start typing the application for which you want to create a rule until autocompletion provides enough letters to select it. To set a destination, first choose a destination type: Destination Profile (for internal destinations), FQDN, IP, or Netmask. Then choose one or more destination profiles from the list or enter one or more FQDNs, IPv4 or IPv6 addresses, or netmasks. When done, Create the rule.
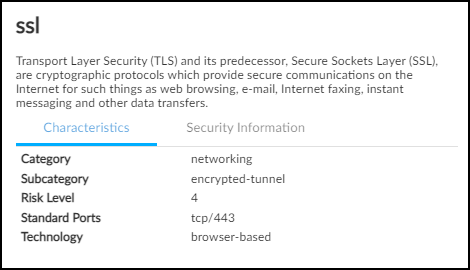
In addition to the automated policy rules that IoT Security generates based on observed network behaviors of devices in the same profile, you can manually add other rules to the set. In the policy set creation workflow, click Add Rule and then set an application and destination. By default, Any appears in both the Application and Destination Type fields. To change the application, delete Any and start typing the application for which you want to create a rule until autocompletion provides enough letters to select it. To set a destination, first choose a destination type: Destination Profile (for internal destinations), FQDN, IP, or Netmask. Then choose one or more destination profiles from the list or enter one or more FQDNs, IPv4 or IPv6 addresses, or netmasks. When done, Create the rule. The App Risk column contains the risk level for this application as defined in Applipedia. Risk levels are graded from 1 to 5, with numbers approaching 5 carrying increasingly more risk. Hover your cursor over the application name to display a pop-up panel with information about the application retrieved from Applipedia. For explanations about this information, see Discover IoT Device Applications.
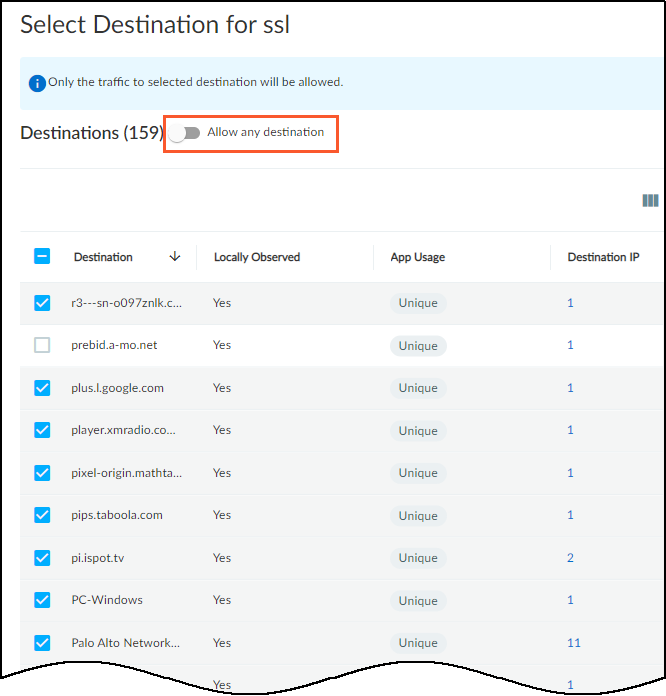
The App Risk column contains the risk level for this application as defined in Applipedia. Risk levels are graded from 1 to 5, with numbers approaching 5 carrying increasingly more risk. Hover your cursor over the application name to display a pop-up panel with information about the application retrieved from Applipedia. For explanations about this information, see Discover IoT Device Applications. The Alert Raised column provides the number of alert instances involving each application that occurred on devices in the source profile. This information is useful when deciding whether to include recommended behaviors in a set of policy rules. For example, if you notice a behavior is associated with a high number of alerts, you might delay adding a rule that permits this behavior until you investigate how serious the alerts are. If they are all low severity alerts, you might decide they’re acceptable. On the other hand, if they are high or critical severity alerts, you might decide to resolve them first before proceeding.By default, IoT Security recommends permitting IoT devices in the source profile to use applications with all destinations detected in observed network traffic. This is indicated by Any in the Destination column. If you don’t want to allow certain destinations, click Any, toggle off Allow any destination, clear these destinations from the list, and then close the Select Destination panel.
The Alert Raised column provides the number of alert instances involving each application that occurred on devices in the source profile. This information is useful when deciding whether to include recommended behaviors in a set of policy rules. For example, if you notice a behavior is associated with a high number of alerts, you might delay adding a rule that permits this behavior until you investigate how serious the alerts are. If they are all low severity alerts, you might decide they’re acceptable. On the other hand, if they are high or critical severity alerts, you might decide to resolve them first before proceeding.By default, IoT Security recommends permitting IoT devices in the source profile to use applications with all destinations detected in observed network traffic. This is indicated by Any in the Destination column. If you don’t want to allow certain destinations, click Any, toggle off Allow any destination, clear these destinations from the list, and then close the Select Destination panel.
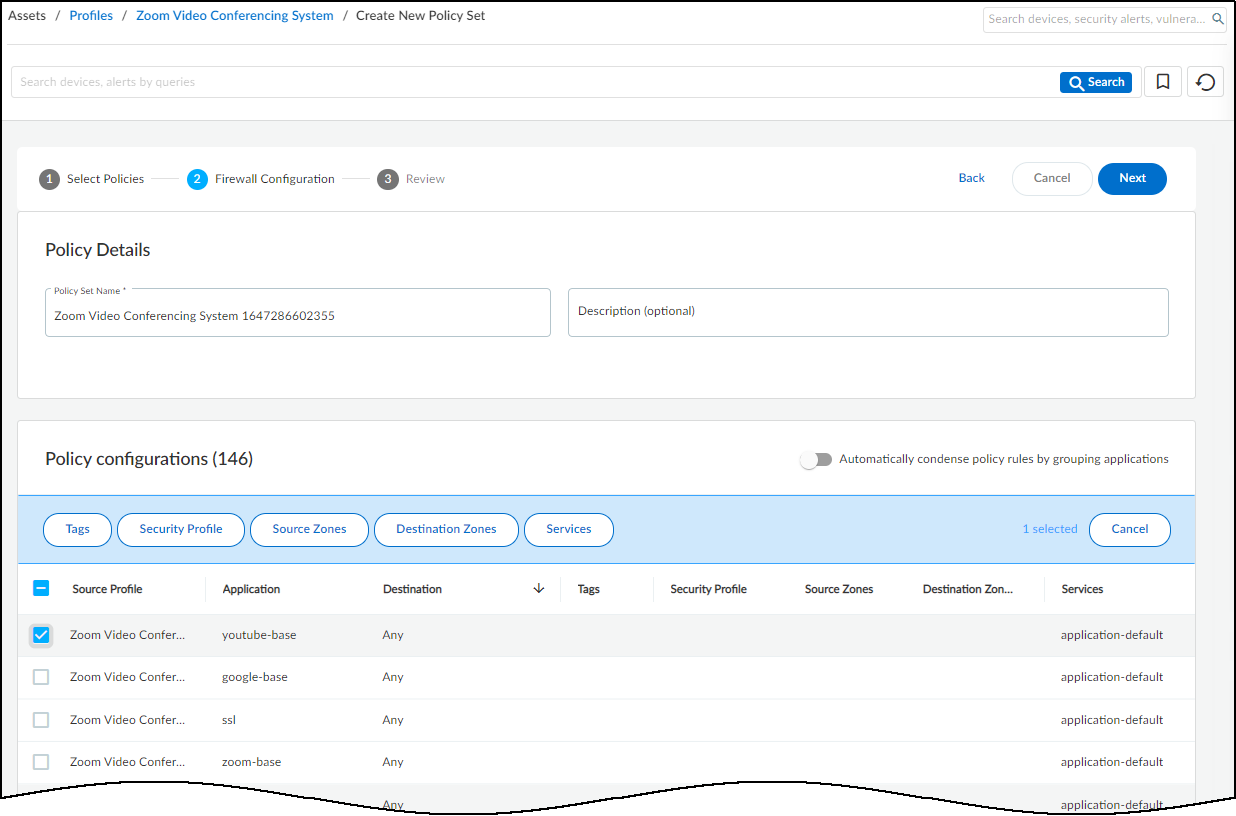
- Use the automatically generated policy rules configuration or modify it as necessary.Use the default policy set name or enter your own. Optionally add a description for future reference.
 If you want to reduce the number of policy rules that IoT Security generates, enable Automatically condense policy rules by grouping applications. When multiple rules have different applications but everything else is the same—the same destination or set of destinations and, if configured, the same tags, security profiles, source and destination zones, and services—IoT Security gathers them all into a single rule and puts all the applications that had previously been the only differentiating element in the rules into a single list of applications. For example, if this option isn’t enabled (its default state) and there’s one destination for ten different applications, IoT Security creates ten rules. However, if you enable this option, IoT Security creates just one rule that includes a set of ten applications.
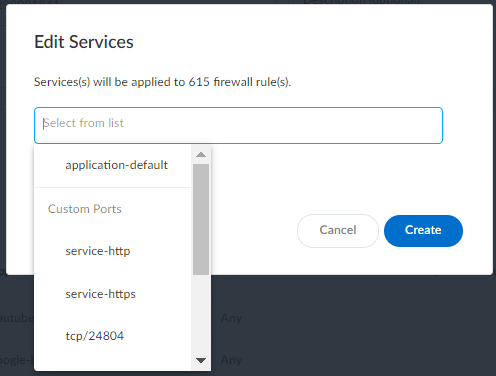
If you want to reduce the number of policy rules that IoT Security generates, enable Automatically condense policy rules by grouping applications. When multiple rules have different applications but everything else is the same—the same destination or set of destinations and, if configured, the same tags, security profiles, source and destination zones, and services—IoT Security gathers them all into a single rule and puts all the applications that had previously been the only differentiating element in the rules into a single list of applications. For example, if this option isn’t enabled (its default state) and there’s one destination for ten different applications, IoT Security creates ten rules. However, if you enable this option, IoT Security creates just one rule that includes a set of ten applications. IoT Security always groups destinations together to reduce the number of recommended policy rules. Unlike the application group option, it doesn’t require you to enable it.Optionally apply tags, a security profile, source and destination zones, and services so that they become part of the policy rules when the Panorama or firewall administrator imports them. This saves the administrator from having to edit imported rules to apply them later. Select the rules you want to apply these to and then click Tags, Security Profile, Source Zones, Destination Zones, or Services at the top of the page to see your choices. Create or select previously-defined options and then click Apply or Create. You can apply one or more tags, source zones, destination zones, and services to the same application.By default, an application uses its standard port and displays application-default in the Services column. When you edit a service, the Edit Services dialog box shows any non-standard ports that IoT Security has observed an application using plus the two options service-http and service-https. Select the service to use in the rule and click Create.
IoT Security always groups destinations together to reduce the number of recommended policy rules. Unlike the application group option, it doesn’t require you to enable it.Optionally apply tags, a security profile, source and destination zones, and services so that they become part of the policy rules when the Panorama or firewall administrator imports them. This saves the administrator from having to edit imported rules to apply them later. Select the rules you want to apply these to and then click Tags, Security Profile, Source Zones, Destination Zones, or Services at the top of the page to see your choices. Create or select previously-defined options and then click Apply or Create. You can apply one or more tags, source zones, destination zones, and services to the same application.By default, an application uses its standard port and displays application-default in the Services column. When you edit a service, the Edit Services dialog box shows any non-standard ports that IoT Security has observed an application using plus the two options service-http and service-https. Select the service to use in the rule and click Create.
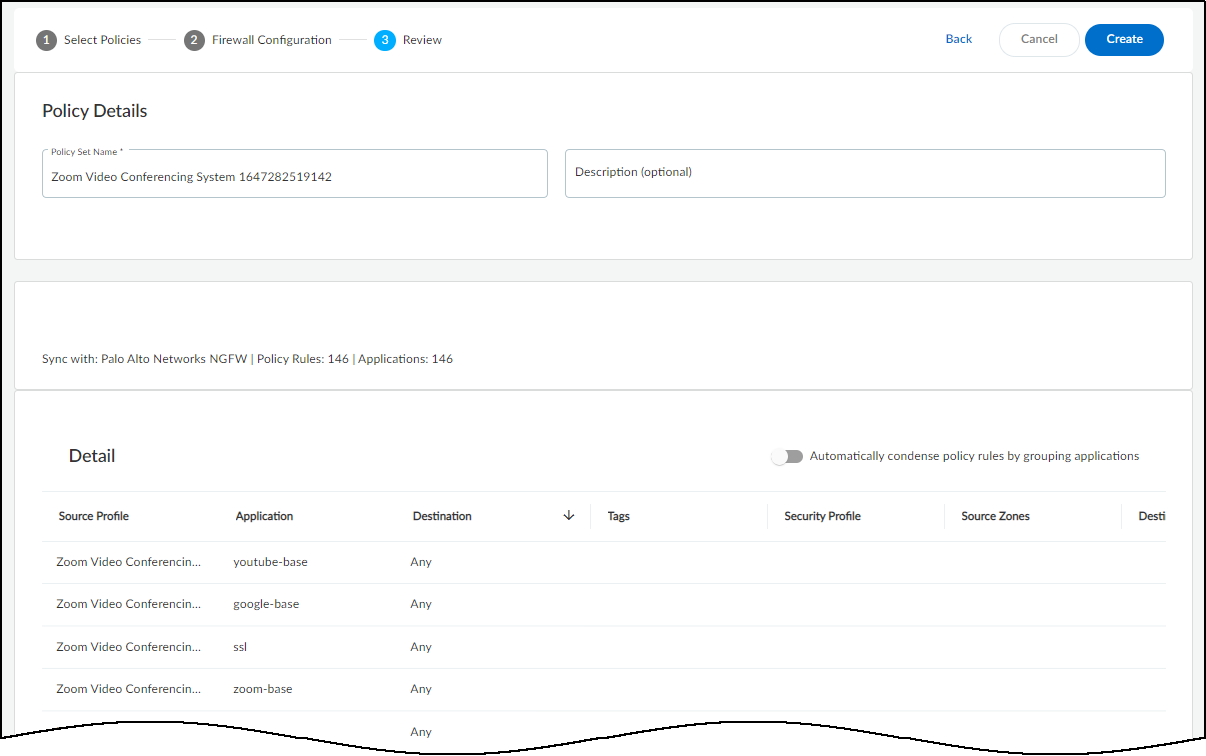
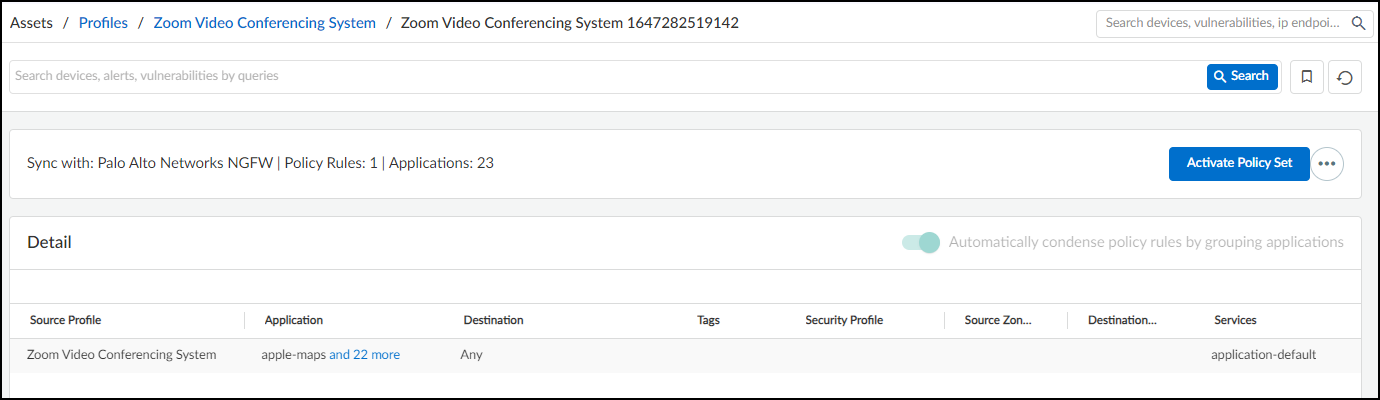
- Carefully review the rule set and then, when you’re satisfied with it, Create the recommended policy rules set.
 When reviewing the policy set, notice that IoT Security displays the default service ports for many of the allowed applications. These are the service ports that the selected applications have been using on the network during the past month. If an application hasn't been observed in over a month, its service ports will no longer show up in the list.IoT Security learns the service ports for applications by observing network traffic. Be sure to allow it enough time to collect the session data it needs, keeping in mind that IoT Security needs more time for applications that are used less frequently.After you click Create, IoT Security creates and saves the policy set. You can view all the policy sets that you created for a device profile on the Policy page. IoT Security also prompts you to activate the policy set, which is necessary to make it available for Panorama and individual firewalls to import.
When reviewing the policy set, notice that IoT Security displays the default service ports for many of the allowed applications. These are the service ports that the selected applications have been using on the network during the past month. If an application hasn't been observed in over a month, its service ports will no longer show up in the list.IoT Security learns the service ports for applications by observing network traffic. Be sure to allow it enough time to collect the session data it needs, keeping in mind that IoT Security needs more time for applications that are used less frequently.After you click Create, IoT Security creates and saves the policy set. You can view all the policy sets that you created for a device profile on the Policy page. IoT Security also prompts you to activate the policy set, which is necessary to make it available for Panorama and individual firewalls to import. - To activate a policy set to make it available for Panorama and individual firewalls to import, click Activate Policy Set.
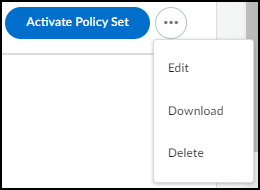
 A device profile can have only one active policy set at a time.If you see anything you want to change before activating the policy set, click the More Actions icon ( … ) and then click Edit. IoT Security returns to the first page (Select Policies) so that you can make the changes.
A device profile can have only one active policy set at a time.If you see anything you want to change before activating the policy set, click the More Actions icon ( … ) and then click Edit. IoT Security returns to the first page (Select Policies) so that you can make the changes. From the same More Actions menu, you can download the policy set as a spreadsheet and you can delete it.To save the policy set without activating it, navigate to any other page in the IoT Security portal.
From the same More Actions menu, you can download the policy set as a spreadsheet and you can delete it.To save the policy set without activating it, navigate to any other page in the IoT Security portal.