IoT Security
Policy Rule Recommendations
Table of Contents
Expand All
|
Collapse All
IoT Security Docs
-
-
- Firewall Deployment Options for IoT Security
- Use a Tap Interface for DHCP Visibility
- Use a Virtual Wire Interface for DHCP Visibility
- Use SNMP Network Discovery to Learn about Devices from Switches
- Use Network Discovery Polling to Discover Devices
- Use ERSPAN to Send Mirrored Traffic through GRE Tunnels
- Use DHCP Server Logs to Increase Device Visibility
- Control Allowed Traffic for Onboarding Devices
- Support Isolated Network Segments
-
Policy Rule Recommendations
IoT Security uses machine learning to recommend policy rule sets and ACL rule sets
based on the observed network behaviors of IoT devices.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
IoT Security uses machine learning to automatically
generate Security policy rule recommendations based on the normal,
acceptable network behaviors of IoT devices in the same device profile.
It then provides these recommendations for next-generation firewalls
to control IoT device traffic.
IoT Security derives its recommendations from the network behaviors
it observes in traffic generated by IoT devices in the same profile
across multiple IoT Security tenants. It classifies the applications
in the observed behaviors into three groups:
- Common applications not locally observed – Applications commonly used by devices in the device profile in multiple IoT Security tenant environments but not observed in yours
- Common applications locally observed – Applications commonly used by devices in the device profile in multiple IoT Security tenant environments including yours
- Unique applications – Applications that are not typically used by devices in this device profile and were observed in use by devices in your environment only
Currently, policy rule recommendations are not supported in multi-vsys firewalls.
They must be manually created.
From PAN-OS 11.1, there's a different process
for recommending Security policy rules to next-generation firewalls from that described
here. The following workflow remains applicable to firewalls running PAN-OS versions
prior to PAN-OS 11.1.
IoT Security then formulates a set of policy rule recommendations.
These rules allow devices in this device profile to continue network
behaviors that are common among multiple tenant environments and
those that are unique to yours. The premise is that these behaviors
are necessary for devices belonging to this device profile to function.
You can accept all these recommendations or disable or modify individual
rules to meet the security requirements of your network. When you’re
satisfied with a policy set, save and activate it. Once activated,
it becomes available for firewalls to import—either through Panorama
or directly—and then add to their rule set.
When a Panorama or firewall administrator imports a set of Security
policy rules from IoT Security, the import operation automatically
creates device objects from source and destination profiles in the
recommended rules and uses those objects in the Security policy
rules it constructs. For the firewall to identify which IoT devices
to apply its policy rules to, it uses IP address-to-device mappings
that IoT Security provides through Device-ID. The firewall learns
the device profile of an IoT device from the mapping and applies
rules with matching device objects as the source.
The IoT Security app makes policy rule recommendations only for IoT devices that it has
identified with a high degree of confidence (a confidence score of 90-100%). It does
not consider the network behaviors of low- and medium-confidence IoT devices (0-69%
and 70-89% scores). In addition, IoT Security does not provide policy rule
recommendations, alert and vulnerability detection, and network behavior analysis
for IT devices, which are devices that aren’t built for a specific task, such as
personal computers, smart phones, and tablets for example. For IT devices, the IoT
Security app provides device identification only.
After allowing sufficient time for IoT Security to collect the
full behaviors of IoT devices in a profile, you’re ready to create
policy rule recommendations for it.
To begin, log in to the IoT Security portal, navigate to AssetsProfiles, and then click a profile name.
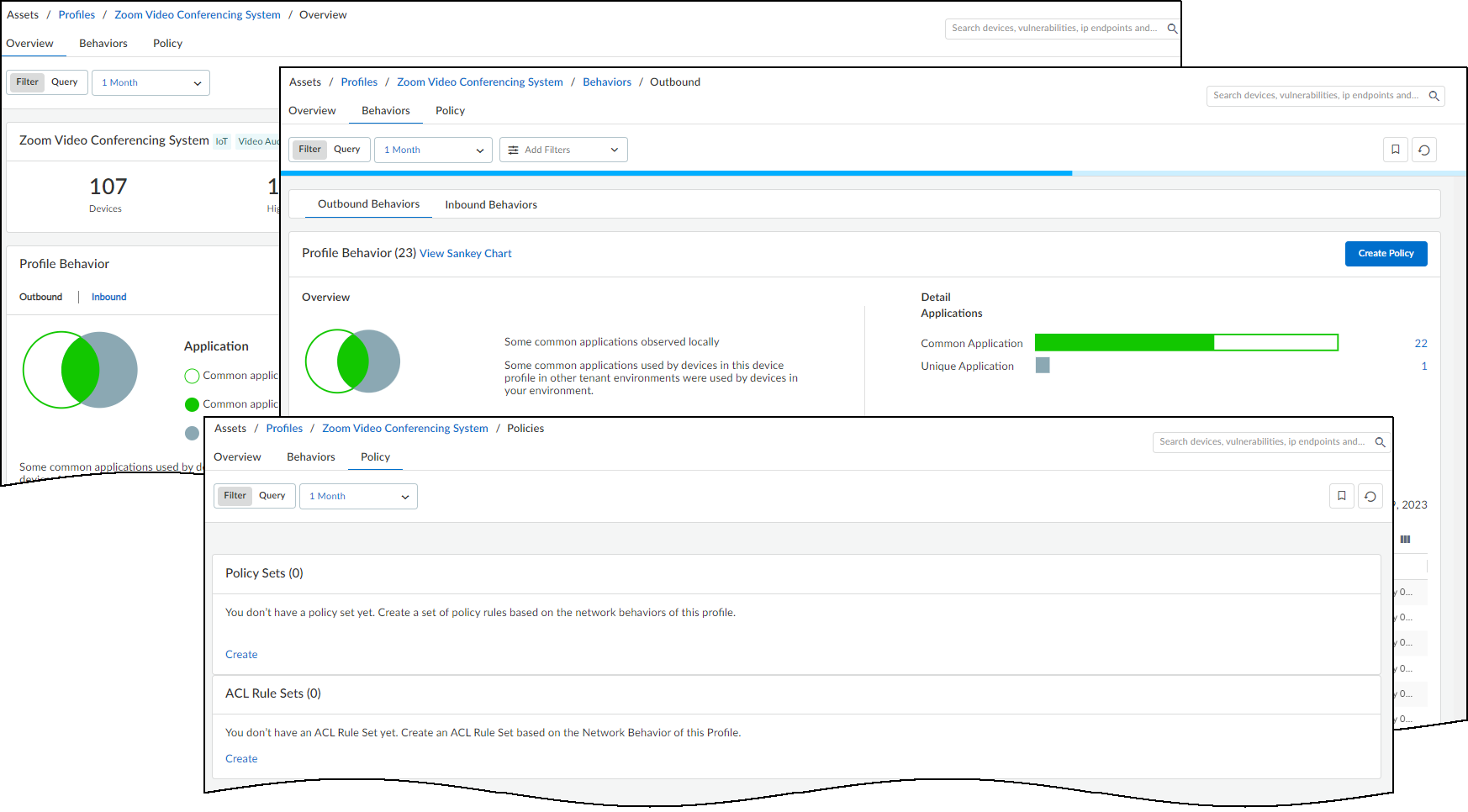
IoT Security displays three profile details pages:
- Overview – View a summary about the high-confidence IoT devices in this profile and their related risk factors for the past day, week, or month. See Device Profile Overview.
- Behaviors – View the behaviors of high-confidence IoT devices belonging to this profile in your local network environment and in other IoT Security tenants’ environments. Also create Security policy rule sets based on these observed behaviors for next-generation firewalls. See Device Profile Behaviors.
- Policy – View previously created Security policy rule sets for next-generation firewalls and ACL rule sets for integration with Cisco ISE. IoT Security generates both types of rule sets from the observed network behaviors of high-confidence IoT devices in this profile in your local network environment and in other IoT Security tenants’ environments. See Device Profile Policy.
