Network Security
Your Web Access Security Policies at a Glance
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Your Web Access Security Policies at a Glance
Before you begin, talk to your Account Administrator and make sure that you've been assigned the role of Web Security Admin. Once you’re a Web Security Administrator, select ManageConfigurationNGFW and Prisma AccessOverviewWeb Security, and Enable Web Security.
Be sure you've selected one of following Configuration Scopes:
- GlobalProtect
- Explicit Proxy
- Remote Networks
- One of your NGFWs
After you've enabled Web Security, go to ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb Security, and configure Web Access Policy to set restrictions for internet access and SaaS applications.
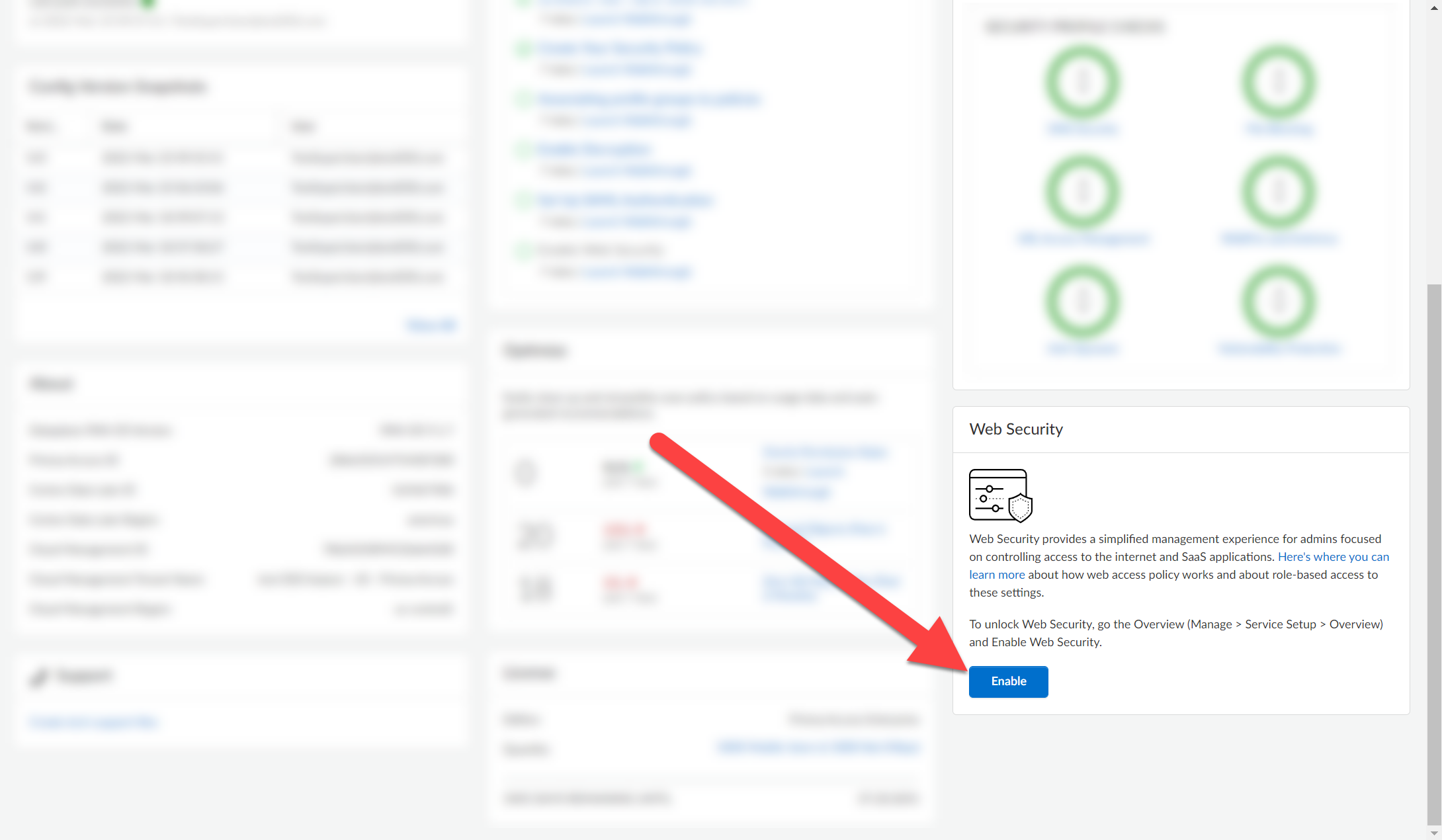
You can also pin Web Security to the sidebar for easy access.
A) Security Policies
Configure your web access Security policies on this tab.
B) Security Policy Recommendations
C) Security Rule Name
Shows the name of the security rule. Select the security rule name in this column to see an advanced view of the security rule.
D) Logs
Select the
![]() icon to see the security rule in the Log Viewer. You can also select Incidents and AlertsLog Viewer to view your logs.
icon to see the security rule in the Log Viewer. You can also select Incidents and AlertsLog Viewer to view your logs.
E) State
Shows whether the security rule is enabled or disabled.
F) Tags
Shows any tags associated with the security rule.
G) Source Location
Shows which locations the security rule affects.
H) User
Shows which users the security rule affects.
I) Search
Use keywords to look for a security rule.
J) Show / Hide columns
Show or hide columns to improve visibility.
K) Delete
Remove a security rule.
L) Clone
Duplicate a security rule and modify it slightly to create a security rule that’s similar to the one you’re duplicating.
M) Enable
Change the state of a security rule to enabled.
N) Disable
Change the state of a security rule to disabled.
O) Move
Move a security rule up or down to change the order of enforcement.
P) Add Policy
Q) Description
Shows the description of the security rule.
R) Advanced Settings
Shows additional security settings configured for the security rule.
S) URL Categories / Web Applications
Shows URL categories and Web Applications you’ve blocked or allowed. Hover your cursor over an allowed URL Category or Web Application to see additional information.
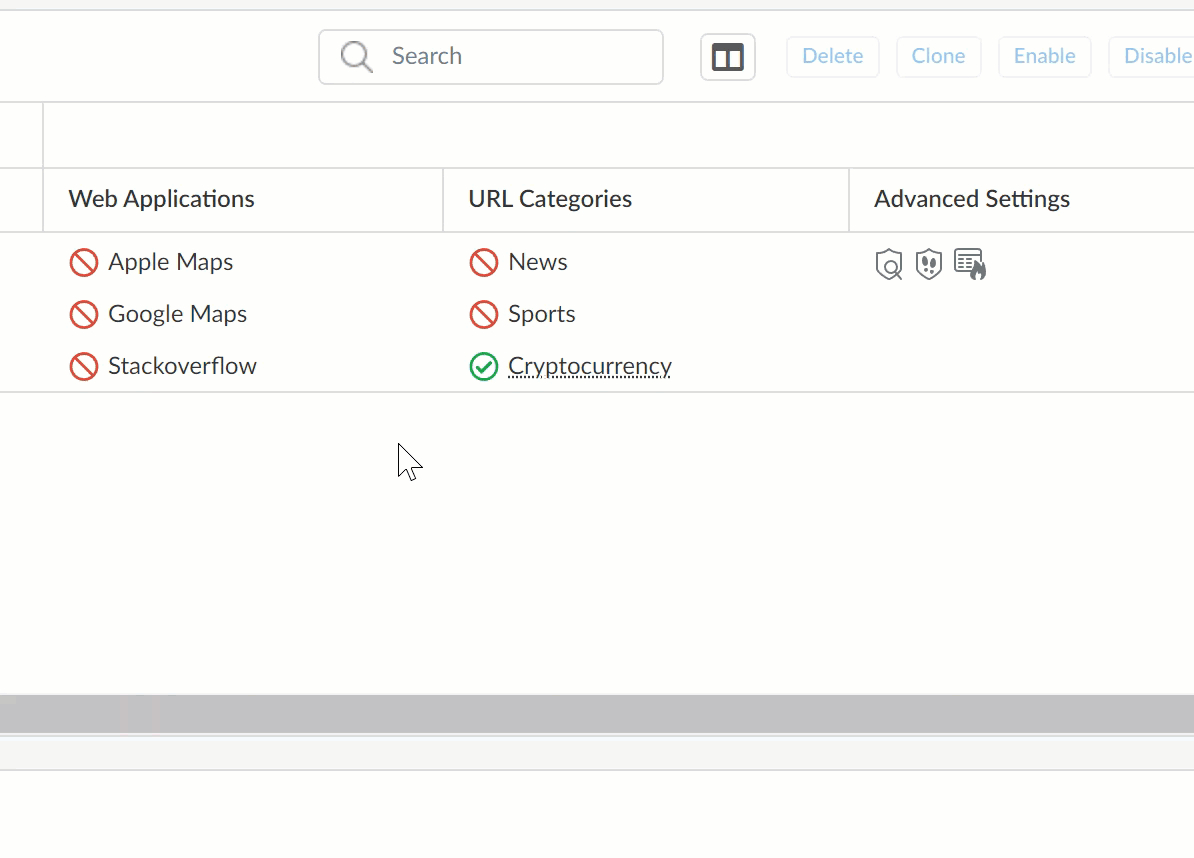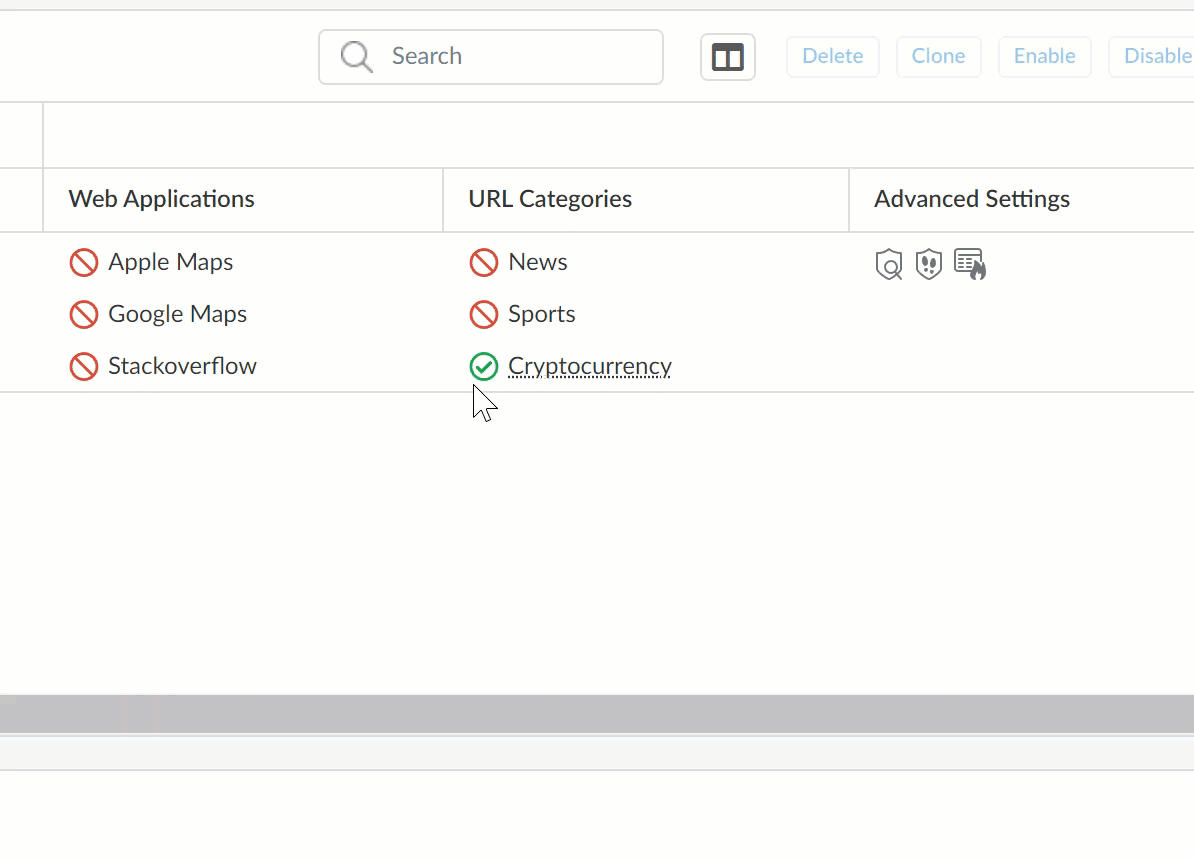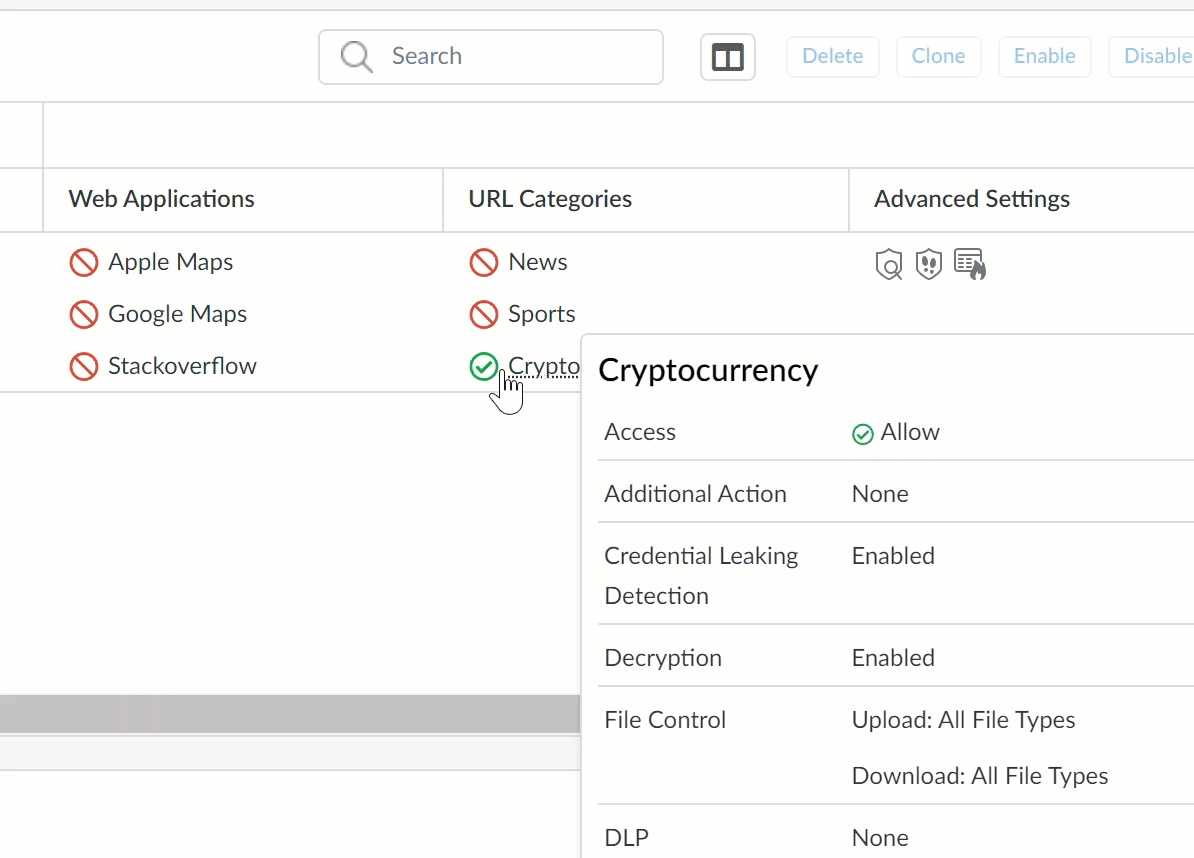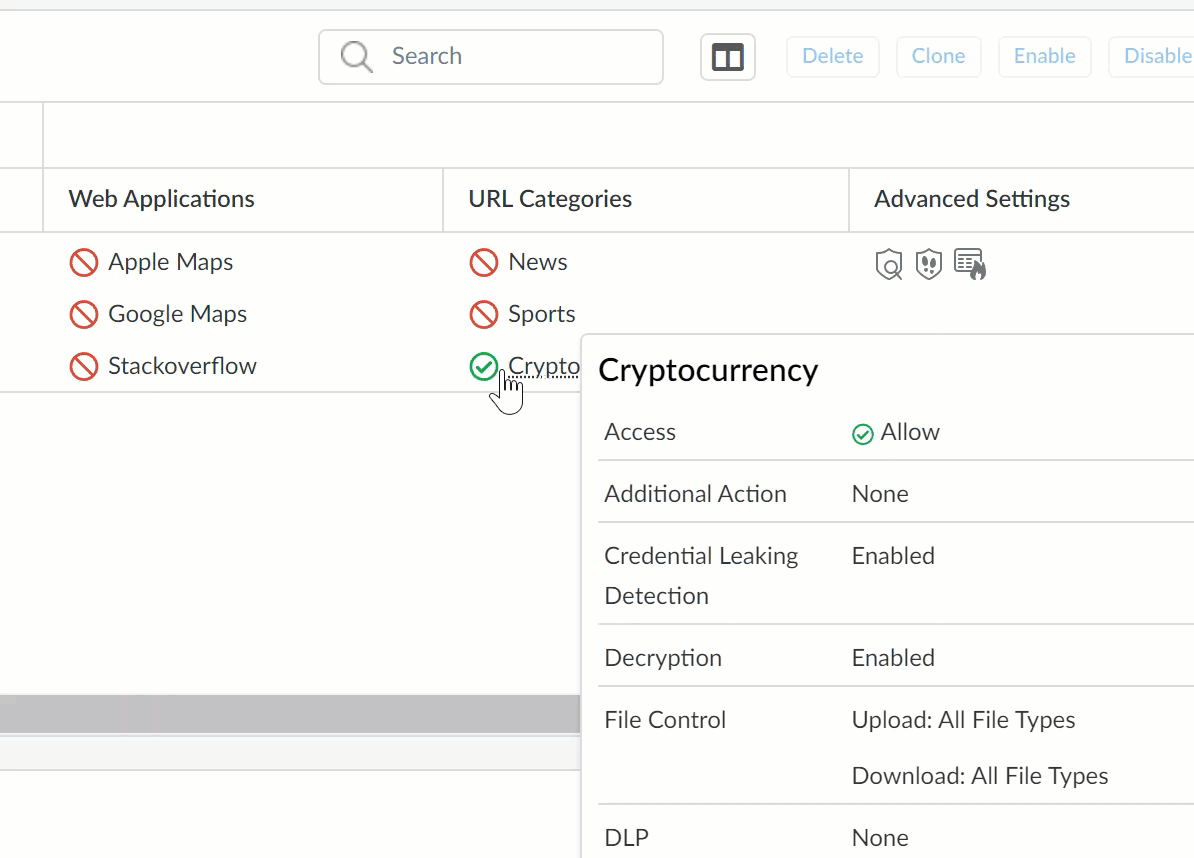
T) Custom Web Access Policies
Shows custom web access policies you’ve created.
U) Default Web Access Policies
Shows the web access policies available by default.
- Global Web AccessEnforces your web application and URL category access restrictions for all users.
- Global Catch All PolicySets the default action for all outbound traffic to any Web Application or URL Category to allow. It’s a good practice to you leave the Global Catch All Policy enabled. Otherwise, any traffic not matching your Web Security rules is enforced according to the Security policy defined under ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy.
