Next-Generation Firewall
New Features in April 2024
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
New Features in April 2024
These are the new features introduced in April 2024 for AIOps for NGFW Free, and for
AIOps for NGFW Premium.
These are the new features introduced in April 2024 for AIOps for NGFW Free, and
for AIOps for NGFW Premium. AIOps for NGFW Premium updates include new
features to support Cloud Management for NGFWs.
Cloud Management for NGFWs: Aggregate Interface Usability Enhancement
|
April 26, 2024
Supported on Strata Cloud Manager for: Cloud Management for
NGFWs.
|
Configuring an Aggregate Ethernet interface variable in snippets or folders allows
you to have reusable common configuration across the entire deployment. Aggregate Ethernet interface variable
reduces duplication of configuration and significantly simplifies the process of
updating and maintaining common configurations.
When you add interfaces for your firewalls, you can now configure the
Aggregate Ethernet interface variable type in addition to
the existing Layer 2, Layer 3, and tap interface types.
Cloud Management for NGFWs: Device Onboarding Rules
|
April 26, 2024
Supported on Strata Cloud
Manager for: Cloud Management for
NGFWs with an AIOps for NGFW Premium
license.
|
Use a device onboarding rule to automate parts of the Palo
Alto Networks NGFW onboarding to Strata Cloud Manager whether you are manually
onboarding Palo Alto Networks NGFW or onboarding using Zero Touch Provisioning
(ZTP). This allows you to associate the firewall with a folder and apply predefined
configuration when the firewall first connects to Strata Cloud Manager. You can
create multiple device onboarding rules to define different match criteria that
apply to different Palo Alto Networks NGFW. Device onboarding rules are designed to
simplify and greatly reduce the time spent onboarding new Palo Alto Networks NGFW at
scale and ensure the correct configuration is applied to newly onboarded Palo Alto
Networks NGFW.
Device onboarding rules use Match Criteria to define which
Palo Alto Networks NGFW the rule applies to. This includes information such as the
firewall Model and any Labels applied
to the firewall during the onboarding process. You can define the rule
Action to specify a Target Folder
one or more Palo Alto Networks NGFW are added to and the Snippet
Association define any firewall-specific snippet configurations that
need to be applied. Additionally, if you use SD-WAN or Cloud Identity Engine (CIE)
you can also define and apply those necessary configurations in the device
onboarding rule to ensure all required connectivity and user-based visibility and
policy enforcement immediately after onboarding.
Cloud Management for NGFWs: Transparent Web Proxy
|
April 26, 2024
You can now use Strata Cloud Manager to configure a transparent
proxy on your firewalls.
Supported on Strata Cloud
Manager for:
|
Prisma Access has its own, separate method of configuring explicit proxy. This
new feature applies only to cloud-managed firewalls.
You can now configure a web proxy on the firewalls you're
managing with Strata Cloud Manager. That means that if you plan to use an
NGFW as a proxy device to secure your network, you can now configure your proxy
settings across your deployment from a simple, unified management interface.
This interface includes an in-app proxy auto-configuration (PAC) file
editor so that you can edit your proxy settings and modify your PAC file all in one
place whenever network changes arise.
The web proxy supports two methods for routing traffic:
- For the explicit proxy method, the request
contains the destination IP address of the configured proxy and the client
browser sends requests to the proxy directly. You can use one of following
methods to authenticate users with the explicit proxy:
-
Kerberos, which requires a web proxy license.
-
SAML 2.0, which requires a Prisma Access license and the add-on web proxy license.
-
- For the transparent proxy method, the request contains the destination IP address of the web server and the proxy transparently intercepts the client request (either by being in-line or by traffic steering). There is no client configuration and Panorama is optional. Transparent proxy requires a loopback interface, User-ID configuration in the proxy zone, and specific Destination NAT (DNAT) rules, which you can configure using Transparent Proxy Rules in Strata Cloud Manager. Transparent proxy does not support X-Authenticated Users (XAU) or Web Cache Communications Protocol (WCCP).
You can push web proxy configurations to the following platforms:
-
PA-1400
-
PA-3400
-
VM Series (with a minimum of four vCPUs)
Strata Cloud Manager: Configuration Indicator
|
April 26, 2024
Supported on Strata Cloud
Manager for:
Prisma Access (Managed by Strata Cloud Manager)
NGFW (Managed by Strata Cloud Manager)
|
Get clarity on the configuration elements that are applicable for a particular scope
and whether they are inherited from a common configuration scope or generated by the
system.
The color-coded configuration indicators help you
understand where the configurations are inherited from, and also visually
distinguish the object types for easy scanning.
Strata Cloud Manager: External Gateway Integration for Prisma Access and On-Premises NGFWs
|
April 26, 2024
Supported on Strata Cloud
Manager for:
|
Enable integration between Prisma Access deployments and on-premises NGFWs deployed
as external gateways.
In the Prisma Access configuration, when setting up the hybrid Prisma Access
deployment with security service edge (SSE) and on-premises NGFWs, you can now
configure the NGFWs as external gateways by referencing the
NGFWs' GlobalProtect gateway IP addresses. This eliminates manual configuration and
minimizes the risk of misconfiguration.
AIOps for NGFW: Strata Cloud Manager Command Center
|
April 11, 2024
Supported on Strata Cloud Manager
with AIOps for NGFW Premium license.
|
The Strata Cloud Manager Command
Center is your new NetSec homepage; it is your first stop to assess
the health, security, and efficiency of your network. In a single view, the command
center shows you all users and IoT devices accessing the internet, SaaS
applications, and private apps, and how Prisma Access, your NGFWs, and your security
services are protecting them.
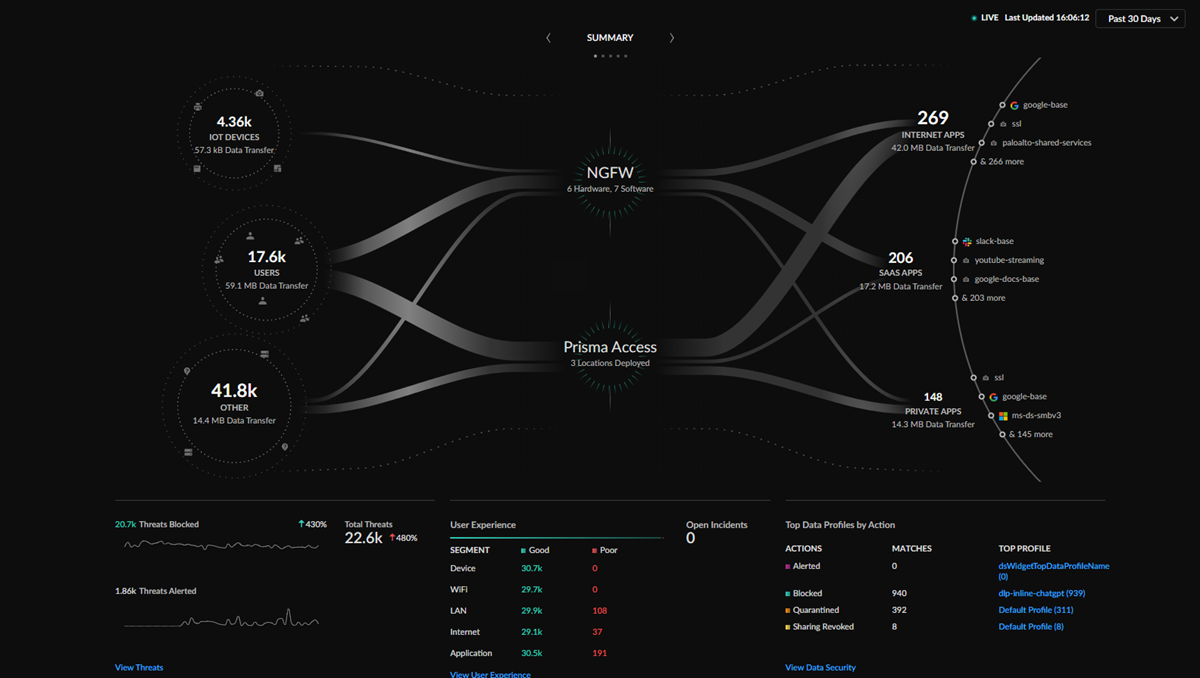
The command center provides you with four different views, each with its
own tracked data, metrics, and actionable insights to examine and interact with:
- Summary: A high-level look at all your network and security infrastructure. Monitor the traffic between your sources (users, IoT) and applications (private, SaaS), and see metrics onboarded security subscriptions.
- Threats: Dig deeper into anomalies on your network and block threats that are impacting your users. Review the traffic inspected on your network and see how threats are being detected and blocked around the clock by your Cloud-Delivered Security subscriptions.
- Operational Health: Review incidents of degraded user experience on your network and see root-cause analysis of the issues and remediation recommendations.
- Data Security: Find high-risk sensitive data and update data profiles to further secure your network. Review the sensitive data flow across your network and SaaS applications.
When the command center surfaces an issue through one of these views that
you should address or investigate (an anomaly, a security gap, a degraded user
experience, something that impacts the security and health of your network), it
provides a path to where you can take actions to further secure your network.
For example, if you are looking at the Threats view and would like more information
about Command and Control threats on your network, you can click C2 in the Blocked
and Alerted Threats table and jump to Activity Insights, where you can drill
down and investigate details about all the Command and Control threats, such as the
threat name, severity, and change the action from Alert to Drop.
