Next-Generation Firewall
New Features in September 2023
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
New Features in September 2023
These are the new features introduced in September 2023 for AIOps for NGFW Free, and
for AIOps for NGFW Premium.
These are the new features introduced in September 2023 for AIOps for NGFW Free, and for
AIOps for NGFW Premium. AIOps for NGFW Premium updates include new features to support
Cloud Management for NGFWs.
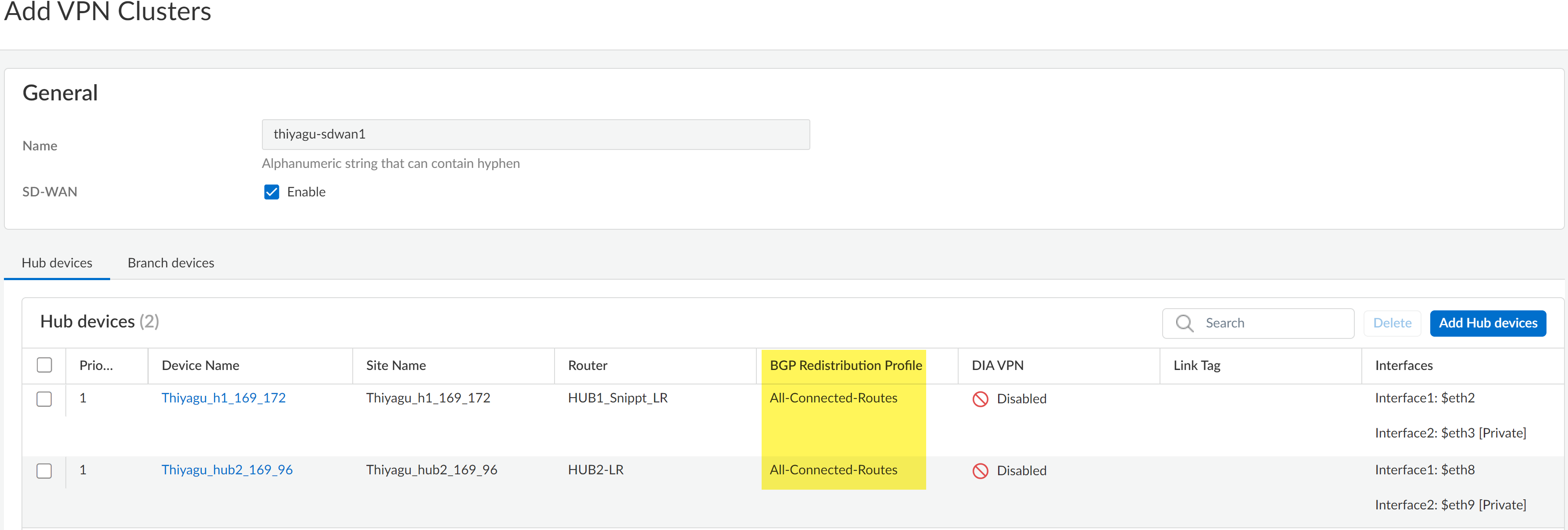
Cloud Management for NGFWs: New Predefined BGP Distribution Profile (Auto VPN & SD-WAN)
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Auto VPN (ManageConfigurationNGFW and Prisma AccessGlobal SettingsAuto VPN) allows you to configure secure connectivity between Strata Cloud Manager and your managed firewalls using SD-WAN. The routing protocol used by Auto
VPN is the Border Gateway Protocol (BGP) Redistribution profile and determines the
network reachability based on IP prefixes available within autonomous systems (AS).
Firewalls added to a VPN cluster on are now automatically assigned the predefined
All-Connected-Routes BGP Redistribution profile by
default. The All-Connected-Routes BGP Redistribution
broadcasts all connected routes to the VPN peers in the cluster. Additionally, this
BGP Redistribution profile not only provides the tunnel and route peering
configuration required for connectivity, but also completes route advertisements to
allow for branch to branch communication.
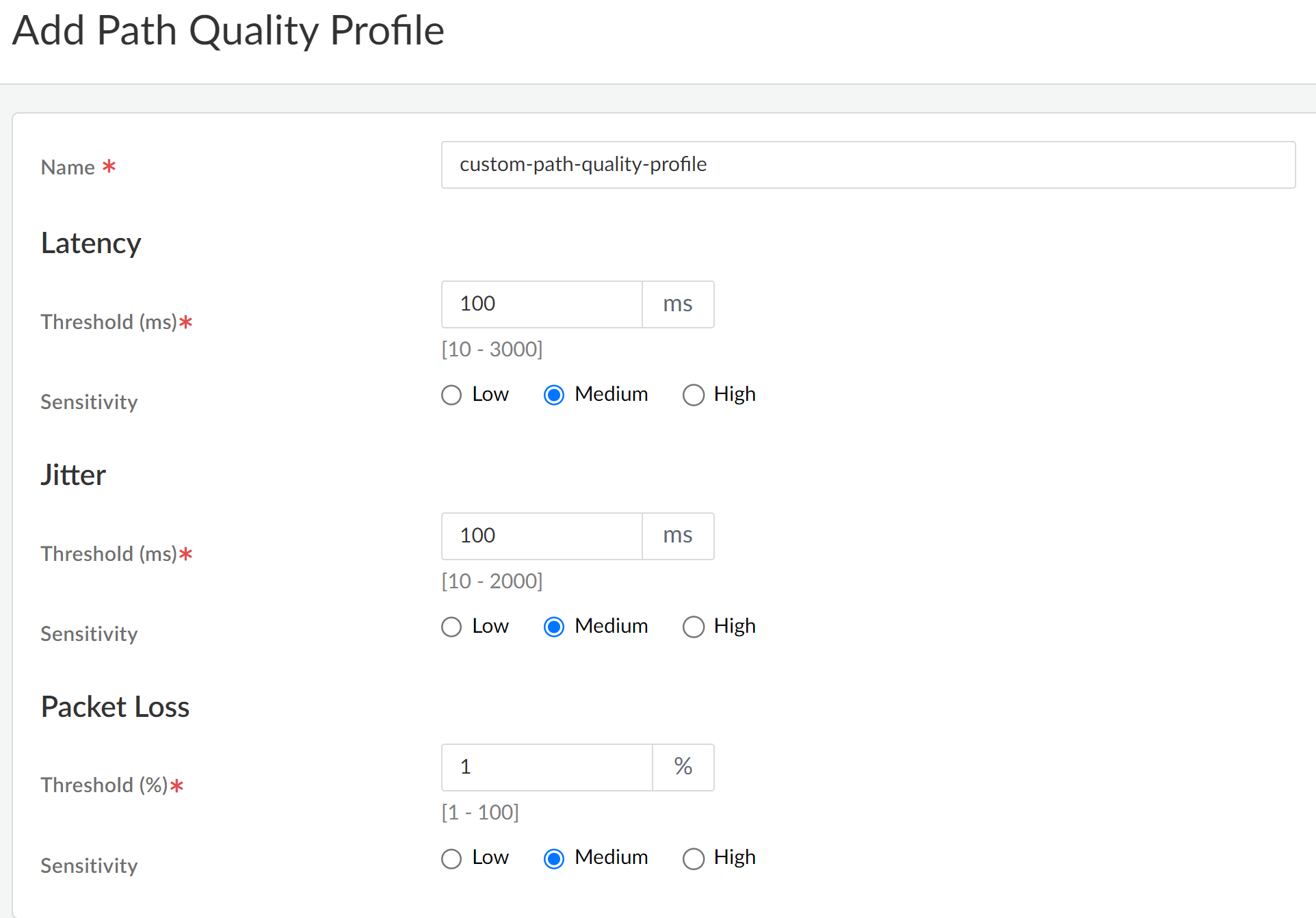
Cloud Management for NGFWs: Custom Path Quality Profile (SD-WAN)
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Create a custom path quality profile on Strata Cloud Manager for firewalls
leveraging SD-WAN. A path quality profile allows you
to define unique network quality requirements for business-critical and
latency-sensitive applications, application filters, application groups, services,
service objects and service group objects that have requirements based on latency,
jitter, and packet loss percentage. Applications and services can share a path
Quality profile. Specify the maximum threshold for each parameter, above which the
firewall considers the path deteriorated enough to select a better path.
The firewall treats the latency, jitter, and packet loss thresholds as OR conditions,
meaning if any one of the thresholds is exceeded, the firewall selects the new best
(preferred) path. Any path that has latency, jitter, and packet loss less than or
equal to all three thresholds is considered qualified and the firewall selected the
path based on the associated Traffic Distribution profile.
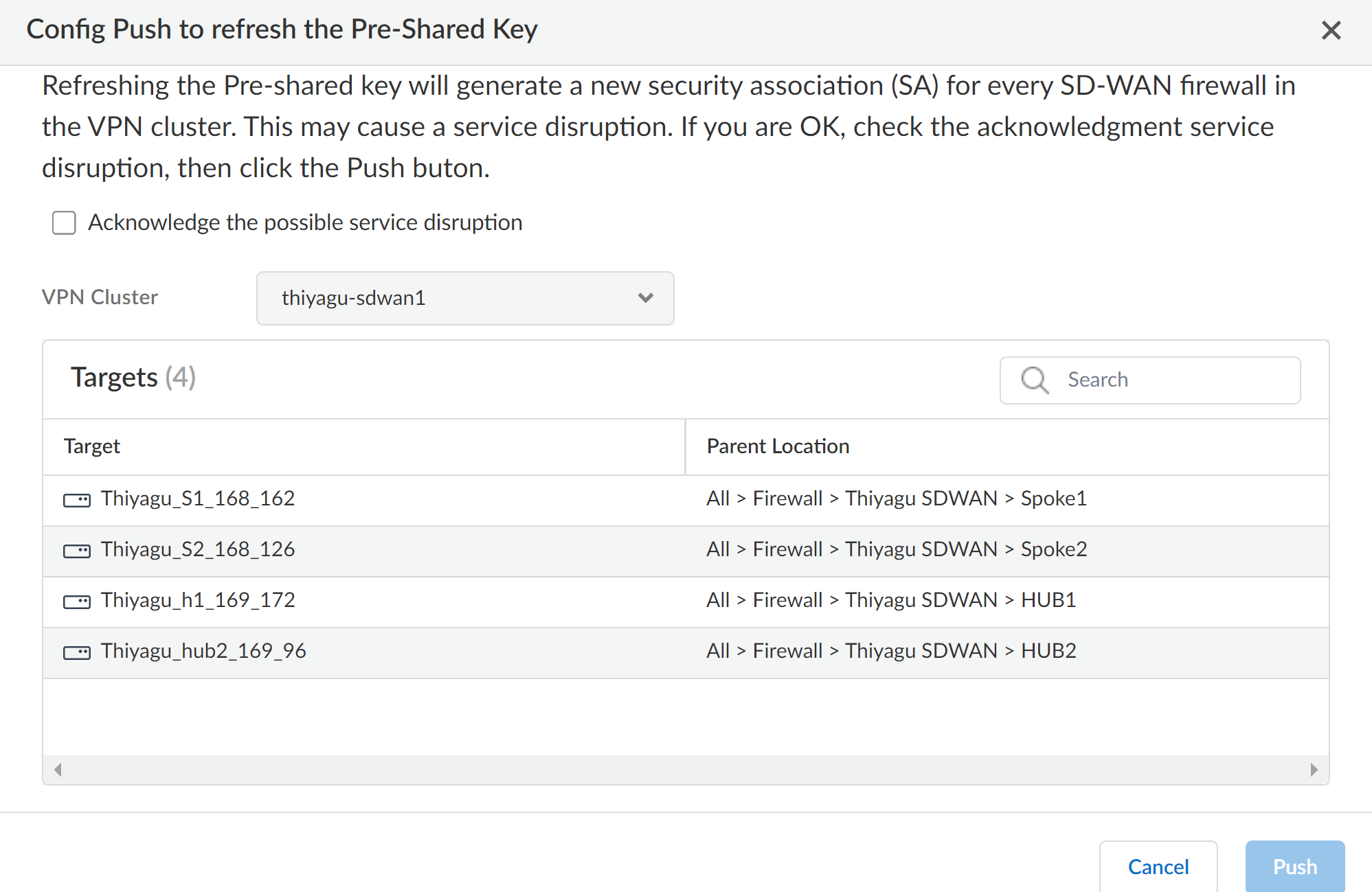
Cloud Management for NGFWs: Pre-Shared Keys Refresh (Auto VPN & SD-WAN)
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Auto VPN allows you to configure secure
connectivity between Strata Cloud Manager and your managed firewalls using SD-WAN. Peers in the VPN cluster use a
pre-shared key to mutually authenticate each other. Strata Cloud Manager now allows
you to refresh the pre shared keys used for authenticating VPN tunnels for existing
VPN clusters (ManageConfigurationNGFW and Prisma AccessGlobal SettingsAuto VPN).
Cloud Management for NGFWs: Cloud IP Tag Collection (with the Cloud Identity Engine)
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Enforcing your security policy consistently across all the firewalls in your network
relies on those firewalls having the most up-to-date identity information from your
sources, such as cloud-based identity management systems. With the array of
management systems and large numbers of users and devices, it can often be
time-consuming and difficult to correlate identity information with its originating
sources and ensure that it was provided to all necessary devices.
You can now use Strata Cloud Manager with the Cloud Identity Engine to manage IP
address-to-tag (also known as IP-tag) mappings and simplify your security policy by
creating tag-based rules. When you configure a cloud connection in the Cloud
Identity Engine to your cloud-based identity management system (either Azure or
AWS), you can use the Cloud Identity Engine to collect IP-tag mappings.
You can see all of your IP-tag mappings, as well as their associated sources, in the
Cloud Identity Manager. Using filters to highlight the most relevant information,
you can quickly identify issues with your security policy, such as a source that is
currently unavailable. You can then use the Strata Cloud Manager to create tag-based
security policy using dynamic address groupsand distribute it to
the firewalls in your network to ensure they have the latest information needed to
consistently enforce security policy. You can also share the IP-tag mappings with
other firewalls in your network by using User Context segments in the Cloud
Identity Engine.
By leveraging the capabilities of Strata Cloud Manager with the identity information
that the Cloud Identity Engine provides, you can more easily create and manage your
security policy using tags.
Cloud Management for NGFWs: Configuration Version Snapshot
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Manage configuration pushes for your cloud managed NGFWs alongside your Prisma Access
deployments with Config Version Snapshots.
Evaluate configuration pushes, compare your candidate configuration to previously
pushed configurations, and rollback recent changes in the event of any unintended
consequences of a recent push.
Load previous configurations to use as candidates for your configuration push and
make further changes to expand the scope of the original configuration. Restore
previous configurations to immediately rollback the changes of a recent
configuration push.
Review the devices or deployments impacted or targeted by your configuration pushes
for the full scope of the changes.
Cloud Management for NGFWs: Troubleshooting for NGFW Connectivity and Policy Enforcement
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Troubleshoot these
networking and identity features–track down and resolve connectivity issues or
policy enforcement anomalies:
Network Troubleshooting for NAT and DNS Proxy
Troubleshoot your NGFWs from Strata Cloud Manager without having to move
between various firewall interfaces. If you experience connectivity issues after
deploying and configuring your NGFWs, you can get an aggregate view of your routing
and tunnel states, and drill down to specifics to find anomalies and problematic
configurations.
Identity and Policy Troubleshooting
Troubleshoot your identity-based policy rules and dynamically defined
endpoints. Check the status of specific NGFWs and expose possible mismatches between
how you expect a policy to work and its actual enforcement behavior.
Cloud Management for NGFWs: Config Cleanup
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Do dynamic business needs often require you to deal with rapid configuration changes
that result in complex configurations with a number of zero hit rules, zero hit
objects, unused objects, and duplicate objects? Such configurations can lead to a
poor security posture and can inadvertently increase the attack surface of your
network. Config Cleanup has you covered.
Config Cleanup gives you a comprehensive view of all policy rules that have no hits,
objects that aren't referenced directly or indirectly in your configuration, objects
that are referenced in a policy rule but have no hits in the Traffic log during the
specified time frame, and objects of the same type with different names but have the
same values so that you can better:
- Manage attack surface exposure
- Prioritize remediation actions
- Remediate over time
- Respond to audit questions when they arise
Identify and remove unused configuration objects and policy rules from your
configuration. Removing unused configuration objects eases administration by
removing clutter and preserving only the configuration objects that are required for
security enforcement.
Review unused objects and policy rules across your entire Strata Cloud Manager
configuration for the last 6 months, and optimize policy rules that are overly
permissive rules to convert these to be more specific, focused rules that only allow
the applications you’re actually using.
Together with Policy Optimizer, these tools help you
ensure that your policy rules stay fresh and up to date.
Cloud Management for NGFWs: Policy Optimizer
|
September 29, 2023
Now supported for Cloud Management for
NGFWs (with an AIOps for NGFW Premium
license)
|
Hone and optimize overly permissive security rules so that they only allow
applications that are actually in use in your network. Rules that are too broad
introduce security gaps because they allow applications that aren’t in use in your
network. Policy Optimizer enables you to convert
these overly permissive rules to more specific, focused rules that only allow the
applications you’re actually using.
Strata Cloud Manager analyzes log data and categorizes rules as overly permissive
when they are allowing any application traffic, and the rules
must be at least 90 days old. These rules can introduce security loopholes, if
they’re allowing traffic that’s not necessary for enterprise use.
For rules identified as overly permissive, Strata Cloud Manager auto-generates
recommendations you can accept to optimize the rule. The new, recommended rules are
more specific and targeted than the original rule; they explicitly allow only the
applications that have been detected in your network in the last 90 days.
Select an overly permissive rule to review, adjust, and accept optimization
recommendations. Replacing these rules with the more specific, recommended rules
strengthens your security posture. You can choose to accept some or all of the rule
recommendations. Accepting recommendations to optimize a rule does not remove the
original rule. The original rule remains listed below the new rules in your Security
policy; this is so you can monitor the rule, and remove it when you’re confident
that it’s not needed. Both the original rule and optimized rules are tagged so you
can easily identify them in your Security policy:
Together with Config Cleanup, these tools help you
ensure that your policy rules stay fresh and up to date.
Enhancements to Probable Root Cause Analysis
|
September 28, 2023
|
To troubleshoot the issues that cause alerts, AIOps for NGFW leverages
advanced AI capabilities to provide probable causes for these alerts. By
reviewing these probable causes, you can identify the source of the issue and follow
the provided recommendations for resolving it. You can view the probable causes for
the following scenarios:
-
High Processing Activity
-
Single or Multiple Greedy Session Detection and Remediation
-
Session Exhaustion with Connectivity Loss
-
High Packet Buffer Utilization due to Single Application
-
High Packet Descriptor On-Chip Utilization due to Single Application
-
Slow-Path DoS Attack Detection and Remediation Suggestion
-
High URL Cache Lookup Activity Detection and Remediation
-
High Content Processing Activity Detection and Remediation
Regional Support for Hosting AIOps for NGFW
|
September 28, 2023
|
You can now host your instance of AIOps for NGFW in the following regions:
-
Israel
-
Indonesia
-
Taiwan
-
Qatar
In this way, your telemetry and firewall log data is processed by a local AIOps for
NGFW instance without the data ever leaving your geographic region. To host AIOps for NGFW in new regions for new
customers, select the desired region during the Free or Premium activation process.
If you are an existing customer with an AIOps for NGFW instance, it will continue to
operate from its original location.
