Next-Generation Firewall
NAT Policy Rules
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
NAT Policy Rules
Understand NAT policy rules and NAT rule capacities.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
You configure a NAT rule to match a packet’s source zone and destination zone, at a
minimum. In addition to zones, you can configure matching criteria based on the packet’s
destination interface, source and destination address, and service. You can configure
multiple NAT rules. The firewall evaluates the rules in order from the top down. Once a
packet matches the criteria of a single NAT rule, the packet is not subjected to
additional NAT rules. Therefore, your list of NAT rules should be in order from most
specific to least specific so that packets are subjected to the most specific rule you
created for them.
It is important to understand that in firewall policy rules (including NAT), the set of
IPv4 addresses is treated as a subset of the set of IPv6 addresses. However, the set of
IPv6 addresses is not a subset of the set of IPv4 addresses. An IPv4 address can match a
set or range of IPv6 addresses; but an IPv6 address cannot match a set or range of IPv4
addresses.
In all policy types, the keyword any for a source or destination
address means any IPv4 or IPv6 address. The keyword any is
equivalent to ::/0. If you want to express "any IPv4 address", specify 0.0.0.0/0.
During policy matching, the firewall converts an IPv4 address into an IPv6 prefix where
the first 96 bits are 0. An address of ::/8 means, match the rule if the first 8 bits
are 0. All IPv4 addresses will match ::/8, ::/9, ::/10, ::/11, ... ::/16, ... ::/32, ...
through ::/96.
If you want to express "any IPv6 address, but no IPv4 addresses", you must configure two
rules. The first rule denies 0.0.0.0/0 to deny any IPv4 address (as the source or
destination address), and the second rule has ::/0 to mean any IPv6 address (as the
source or destination address), to satisfy your requirement.
Static NAT rules do not have precedence over other forms of NAT. Therefore, for static
NAT to work, the static NAT rules must be above all other NAT rules in the list on the
firewall.
NAT rules provide address translation, and are different from security policy rules,
which allow or deny packets. It is important to understand the firewall’s flow logic
when it applies NAT rules and security policy rules so that you can determine what rules
you need, based on the zones you have defined. You must configure security policy rules
to allow the NAT traffic.
Upon ingress, the firewall inspects the packet and does a route lookup to determine the
egress interface and zone. Then the firewall determines if the packet matches one of the
NAT rules that have been defined, based on source and/or destination zone. It then
evaluates and applies any security policies that match the packet based on the original
(pre-NAT) source and destination addresses, but the post-NAT zones. Finally, upon
egress, for a matching NAT rule, the firewall translates the source and/or destination
address and port numbers.
Keep in mind that the translation of the IP address and port do not occur until the
packet leaves the firewall. The NAT rules and security policies apply to the original IP
address (the pre-NAT address). A NAT rule is configured based on the zone associated
with a pre-NAT IP address.
Security policies differ from NAT rules because security policies examine post-NAT zones
to determine whether the packet is allowed or not. Because the very nature of NAT is to
modify source or destination IP addresses, which can result in modifying the packet’s
outgoing interface and zone, security policies are enforced on the post-NAT zone.
A SIP call sometimes experiences one-way audio when going
through the firewall because the call manager sends a SIP message on behalf of the phone
to set up the connection. When the message from the call manager reaches the firewall,
the SIP ALG must put the IP address of the phone through NAT. If the call manager and
the phones are not in the same security zone, the NAT lookup of the IP address of the
phone is done using the call manager zone. The NAT policy should take this into
consideration.
No-NAT rules are configured to allow exclusion of IP addresses defined within the range
of NAT rules defined later in the NAT policy. To define a no-NAT policy, specify all of
the match criteria and select No Source Translation in the source translation
column.
You can verify the NAT rules processed by selecting DeviceTroubleshooting and testing the traffic matches for the NAT rule. For example:
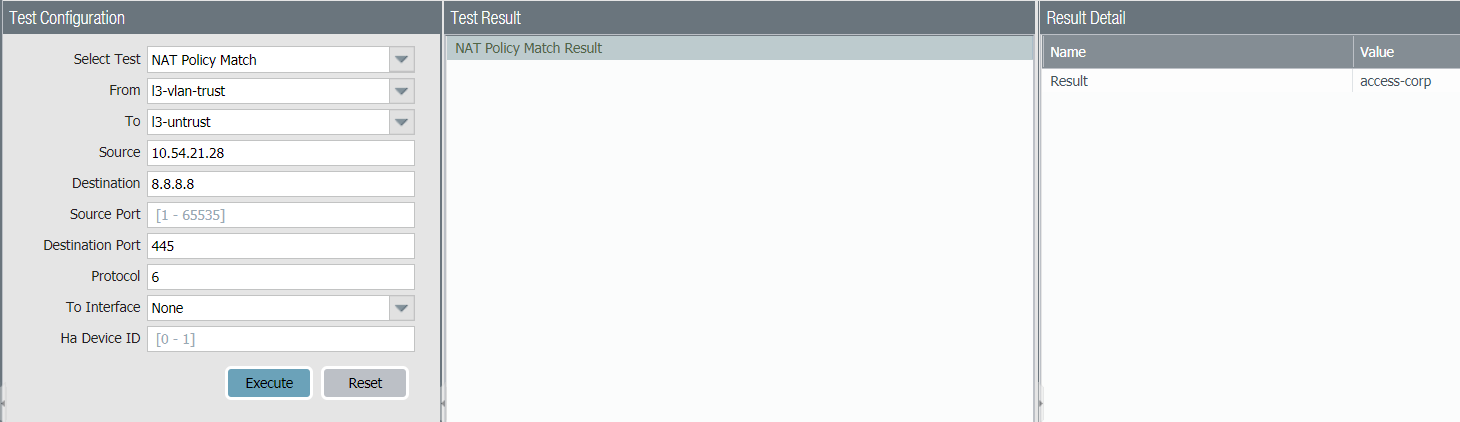
NAT Address Pools Identified as Address Objects
When configuring a Dynamic IP or Dynamic IP and
Port NAT address pool in a NAT policy rule, it is typical to
configure the pool of translated addresses with address objects. Each address object
can be a host IP address, IP address range, or IP subnet.
Because both NAT rules and security policy
rules use address objects, it is a best practice to distinguish between them by
naming an address object used for NAT with a prefix, such as
“NAT-name.”
Proxy ARP for NAT Address Pools
NAT address pools are not bound to any interfaces. The following figure illustrates
the behavior of the firewall when it is performing proxy ARP for an address in a NAT
address pool.
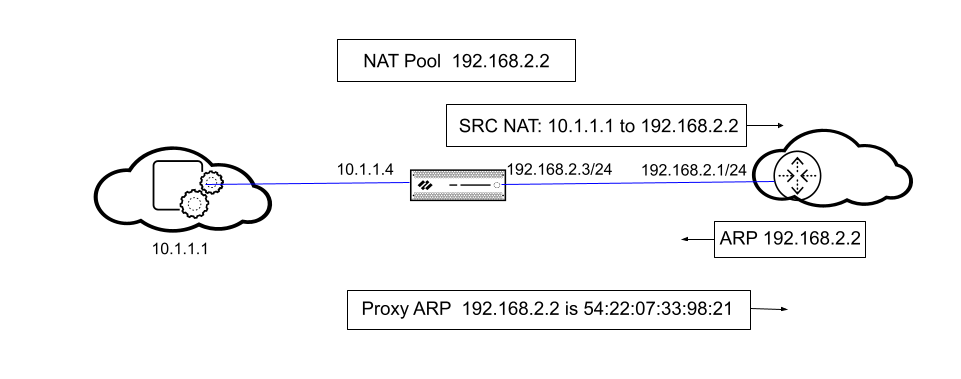
The firewall performs source NAT for a client, translating the source address
10.1.1.1 to the address in the NAT pool, 192.168.2.2. The translated packet is sent
on to a router.
For the return traffic, the router does not know how to reach 192.168.2.2 (because
that IP address is just an address in the NAT address pool), so it sends an ARP
request packet to the firewall.
In our first scenario, when the NAT pool address (192.168.2.2) is in the same subnet
as the egress/ingress interface IP address (192.168.2.3/24), the firewall can send a
proxy ARP reply to the router, indicating the Layer 2 MAC address for 192.168.2.2 is
54:22:07:33:98:21, as shown in the figure above.
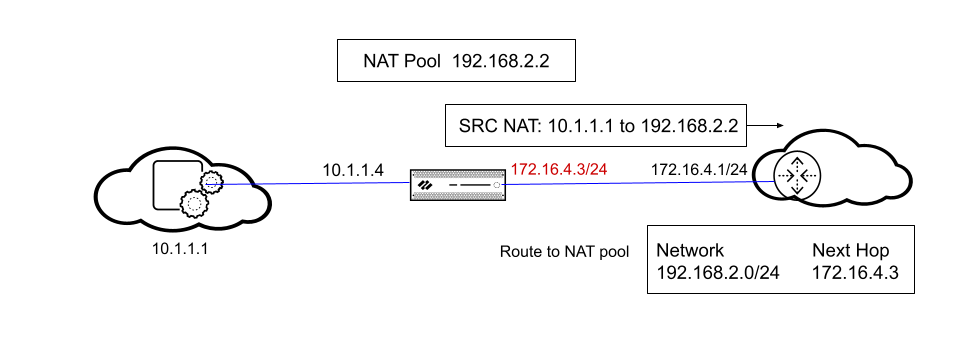
No Proxy ARP When the NAT Pool Address Isn't a Subnet of the Egress/Ingress Interface
In our second scenario, the NAT pool address (192.168.2.2) isn't a subnet of an
interface on the firewall, so the firewall won't send a proxy ARP reply to the
router. This means that the router must be configured with the necessary route to
know where to send packets destined for 192.168.2.2, in order to ensure the return
traffic is routed back to the firewall, as shown in the figure below.
NAT Rule Capacities
The number of NAT rules allowed is based on the firewall model. Individual rule
limits are set for static, Dynamic IP (DIP), and Dynamic IP and Port (DIPP) NAT. The
sum of the number of rules used for these NAT types cannot exceed the total NAT rule
capacity. For DIPP, the rule limit is based on the oversubscription setting (8, 4,
2, or 1) of the firewall and the assumption of one translated IP address per rule.
To see model-specific NAT rule limits and translated IP address limits, use the
Compare Firewalls tool.
Consider the following when working with NAT rules:
- If you run out of pool resources, you cannot create more NAT rules, even if the model’s maximum rule count has not been reached.
- If you consolidate NAT rules, the logging and reporting will also be consolidated. The statistics are provided per the rule, not per all of the addresses within the rule. If you need granular logging and reporting, do not combine the rules.
