Management Features
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Management Features
What new management features are in PAN-OS 11.1?
Accelerate Insights and Enhance Security with Telemetry Autoenablement
|
September 2025
|
Telemetry autoenablement for Palo Alto
Networks devices streamlines the activation and configuration of telemetry,
eliminating complex workflows and manual setup. This feature ensures that upon
device onboarding, telemetry is automatically enabled and configured to stream data
to the correct data residency region, determined by your location or existing
configurations.
Strata Cloud Manager or hub now manages telemetry settings, rather than
individual Panorama or firewall devices. These services store information for all
devices within a tenant service group (TSG), simplifying and automating telemetry
configuration. This approach removes operational hurdles, enabling full utilization
of telemetry's benefits while maintaining control over data sharing preferences.
Consistent telemetry data streaming provides enhanced security, faster
security responses, and access to advanced features through critical threat
insights. Telemetry autoenablement ensures your devices send valuable diagnostic and
usage information, significantly improving support case resolution times and
offering real-time insights into performance, usage, and potential issues.
You have the ability to manage your telemetry settings at the TSG
level, including the option to change the telemetry tier from Full to Diagnostic
through the hub interface or Strata Cloud Manager. This tiered approach ensures you
can choose the level of information shared while adhering to data privacy
requirements. Additionally, all telemetry configuration changes are logged for audit
purposes, assisting with compliance and security policy adherence.
API Key Certificate
|
November 2023
|
With PAN-OS and Panorama, the option to encrypt the API key using a self-signed
certificate is now available, ensuring enhanced security when you retrieve your API
key. This feature utilizes the PAN-OS device certificate management function to
encrypt the API key for added protection.
See use cases for Keys and Certificates on PAN-OS for more
information on how to manage certificates using PAN-OS and Panorama.
This feature introduces a new field under DeviceSetupManagementAuthentication settings that enables you to select an API Key
Certificate to encrypt your API key. To use this feature, simply
generate an RSA Certificate above 3,027 bits and select the created certificate as
the API key certificate under the Authentication Settings
option.
The existing workflow to generate the API key will still be the same, but now all
existing API keys will be invalid when you add or change an API key certificate.
Configuration Audit Enhancements
|
November 2023
|
Configuration changes often complicate adherence to strict industry compliance
standards and tracing the specific source of unexpected system outages. On Panorama® management server, configuration audit now provides granular,
object-level detail to significantly simplify this process. Your security
administrators can now perform a configuration audit to compare the precise
differences between any two selected configuration versions stored within your Panorama. When reviewing a configuration audit, the Change Summary section
provides a simplified, granular, per-object view of every configuration object that
was added, deleted, or modified. This ensures that security administrators can
quickly assess the impact of changes, immediately trace back potential outage causes
to a specific admin and time, and perform regular security compliance audits with
high precision. The improvements to configuration audits on Panorama enable
security administrators focus immediately on critical details, such as the object
name, its exact location, the modification time, and the administrator who performed
the operation, enabling fast and effective remediation.
Policy Rulebase Management Using Tags
|
November 2023
|
Managing complex security environments often leads to sprawling policy rulebases,
making efficient administration and auditing extremely difficult. Policy Rulebase
Tag Management solves this challenge by allowing your security administrators to
easily categorize and organize your policy rules. Tags enable security
administrators to quickly identify the purpose, function, or ownership of any policy
rule, fostering a clearer understanding of your organization's overall security
posture. Policy Rulebase Management Using Tags ensures administrators maintain
precision and control regardless of the scale of their network security
infrastructure.
After assigning tags to policy rules, security administrators can use the integrated
Tag Browser to visually group and manage
your policy rulebase. This organization streamlines common operational procedures
and helps improve efficiency. For instance, your security administrators can now
add, delete, or move sets of related policies more efficiently than navigating a
flattened rule hierarchy. Furthermore, security administrators can filter the policy
rulebase using one or more tag search criteria, dramatically narrowing the list of
displayed rules for precise management. Importantly, viewing the rulebase using
these visual tags does not alter the fundamental rule evaluation order, preserving
security integrity/
Palo Alto Networks supports Policy Rulebase Management Using Tags across all policy
rulebases for your Panorama® management server and standalone NGFW running
PAN-OS 10.2.5 or later 10.2 release or PAN-OS 11.0.3
or later 11.0 release. If you manage NGFW using a Panorama,
you can centrally create and assign these organization tags.
Secure Copy Protocol Support
|
November 2023
|
In air-gapped deployments where your devices have no outbound internet connection,
your security administrator can enable Secure Copy Protocol (SCP) to
upload essential files directly to your Next-Generation Firewall (NGFW). PAN-OS® supports SCP uploads for superuser administrators only,
ensuring granular control over who can perform uploads. Once SCP uploads are enabled
for a superuser administrator, you can use this account to write custom scripts and
automation for file uploads using the command-line interface (CLI) rather than the
web interface. This ability is critical for maintaining security and operational
readiness in isolated networks.
SCP uploads are supported from local devices running a Microsoft Windows, macOS, or
any Linux operating system. The upload must be performed exclusively from your local
device command-line. Palo Alto Networks does not support SCP applications like
WinSCP and FileZilla. You can use SCP Support to upload all critical operational
files, including PAN-OS software versions and patches, content updates
(such as Applications and Threats, WildFire, and antivirus), XML configuration
files, PAN-OS plugins, and license key files. PAN-OS generates a
system log every time an SCP upload succeeds or fails, providing a clear audit trail
for compliance and security monitoring.
Strata Command Center
|
March 2024
|
Network security administrators often struggle with fragmented visibility
across their security infrastructure, making it difficult to quickly assess overall
network health, identify emerging threats, and understand the impact of security
events on user experience. Traditional approaches require navigating between
multiple dashboards and tools to piece together a comprehensive view of security
posture.
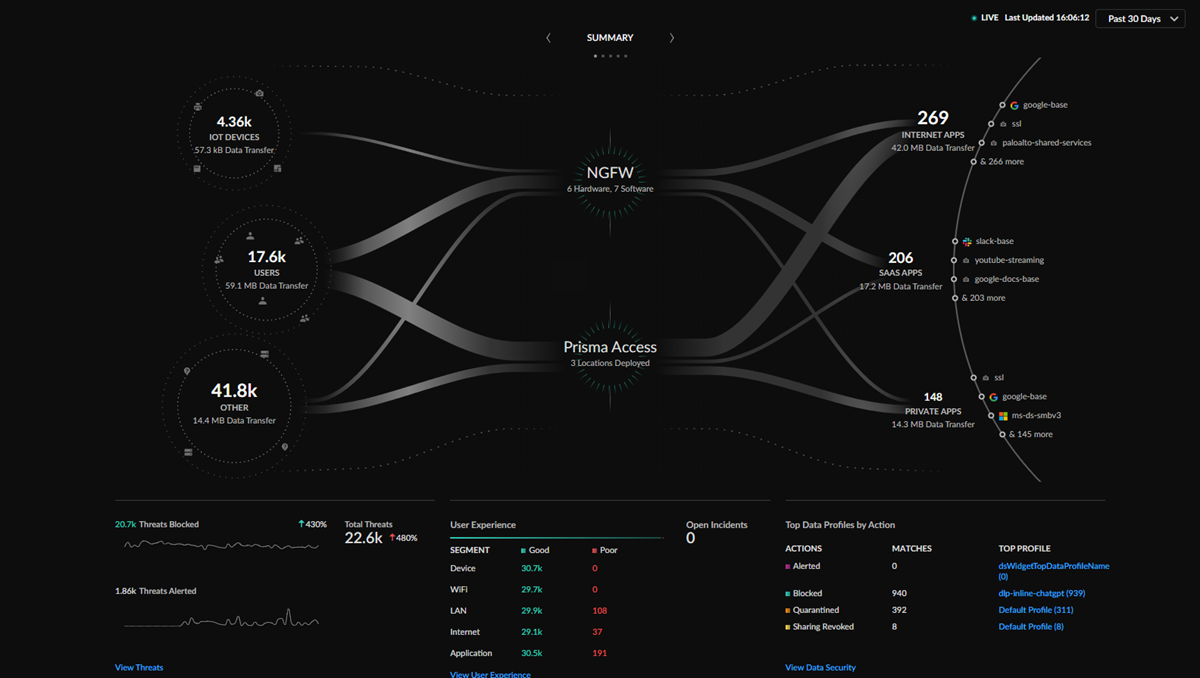
The Strata Cloud Manager Command Center
serves as your new NetSec homepage and provides your first stop to assess the
health, security, and efficiency of your network. In a single view, the command
center shows you all users and IoT devices accessing the internet, SaaS
applications, and private apps, and demonstrates how Prisma® Access, your NGFWs, and
your security services protect them.
View Preferred and Base Releases of PAN-OS Software
|
May 2024
|
The Panorama web interface now displays the
preferred releases and the corresponding base releases of PAN-OS software. Before
you upgrade or downgrade Panorama or PAN-OS, you can view the list of preferred and
base releases and choose your preferred target PAN-OS release. Preferred releases
offer the latest and the most advanced features and ensure stability and
performance. When there are no preferred releases available, the corresponding base
version is not displayed. If necessary, you can choose to view either preferred
releases or base releases.
