Best Practices for Securing Administrative Access
Table of Contents
End-of-Life (EoL)
Best Practices for Securing Administrative Access
Learn the best practices for securing administrative
access to your firewalls to prevent successful cyberattacks through
an exposed management interface.
Protecting your network from cyberattacks
begins with a secure firewall deployment. If the network you use
to manage your sensitive IT devices—including your Palo Alto Networks
next-gen firewalls and Panorama—is not secured properly, you can’t
detect and defend against vulnerability exploits that could lead
to infiltration and/or the loss of sensitive data. The ultimate
goal when securing firewall access is to ensure that even if an
attacker gains access to privileged credentials, you can still thwart
their ability to get in and do damage. Follow these best practice
guidelines to ensure that you secure administrative access to your
firewalls and other security devices in a way that prevents successful
attacks.
- Isolate the Management Network
- Use Service Routes to Access External Services
- Restrict Access to the Mangement Interface
- Manage Administrator Access
- Create Strong Administrator Passwords
- Scan All Traffic Destined for the Management Interface
- Replace the Certificate for Inbound Management Traffic
- Keep Content and Software Updates Current
Isolate the Management Network
All Palo Alto Networks firewalls provide an
out-of-band management port (MGT) that you can use to perform the
firewall administration functions. Alternatively, you can choose
to use the MGT port for initial configuration, and then configure
a data port for management access to the firewall. Either way, because
the management interface provides access to your security configuration,
you must take the following precautions to safeguard access to this
interface:
Do not enable access to
your management interface from the internet or from other untrusted
zones inside your enterprise security boundary. This applies whether
you use the dedicated management port (MGT) or you configure a data
port as your management interface.
- Isolate the management interface on a dedicated management VLAN.
- Limit the source IP addresses allowed in to the management network to those of your dedicated management devices, such as a jump server or a bastion host.
- Use a jump server or bastion host (with screen recording) to provide secure access from your corporate network in to your dedicated management network, and require that users authenticate and are authorized to access your management network.
- If you don’t have a bastion host, use Authentication Policy with multi-factor authentication (MFA) to require administrators to successfully authenticate before you allow them to continue to the firewall web interface login page or CLI login prompt. This prevents access to the management interface using stolen credentials or through vulnerability exploits.
- Limit access to users in your security admin, network admin, or IT user groups, as appropriate for your organization.
- If you must enable remote access to the management network, require access through a VPN tunnel using GlobalProtect. After administrators successfully establish a VPN tunnel into your VPN zone, they must still authenticate into the management network through your bastion host.
- Do not use an interface management profile that allows HTTP, HTTPS, Telnet, or SSH on the interface where you have configured a GlobalProtect portal or gateway because this configuration exposes access to the management interface via the internet. Do not use HTTP or Telnet internally because those protocols transmit in cleartext.
- If you are using a template to deploy a VM-Series firewall that includes a field for restricting management access to a specific IP address, make sure to supply a CIDR block that corresponds to your dedicated management IP addresses or network. If necessary, modify the corresponding security group to add additional hosts or networks after the template launch. Do not make the allowed source network range larger than necessary and do not ever configure the allowed source as 0.0.0.0/0.
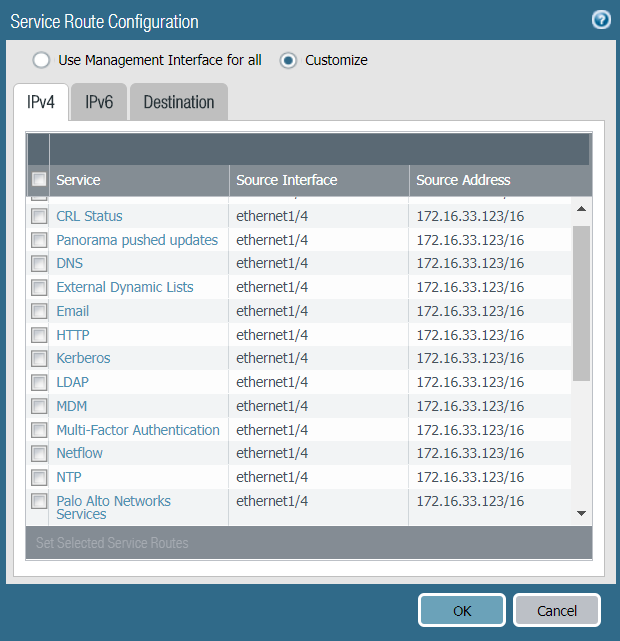
Use Service Routes to Access External Services
By default, the firewall uses the management
(MGT) port to access services that are outside of the management
network on potentially untrusted networks, such as DNS servers,
NTP servers, and authentication servers, including services that
require internet access, such as Palo Alto Networks Services and
AutoFocus. Because your management interface—whether on the MGT
port or a data port—must be isolated on the management network,
you must use service routes (DeviceSetupServicesService
Route Configuration) to enable access
to these services. When you configure a service route, the firewall
instead uses the specified source interface and address to access
the services you need. Specify the source IP address/interface for
your service route on an interface that does not have management
access (HTTPS or SSH) enabled.
Restrict Access to the Management Interface
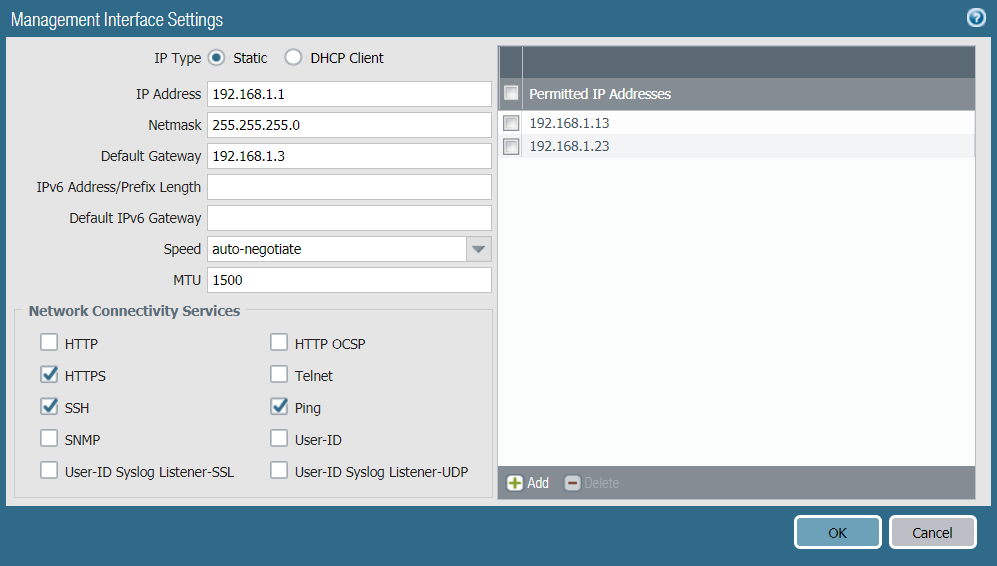
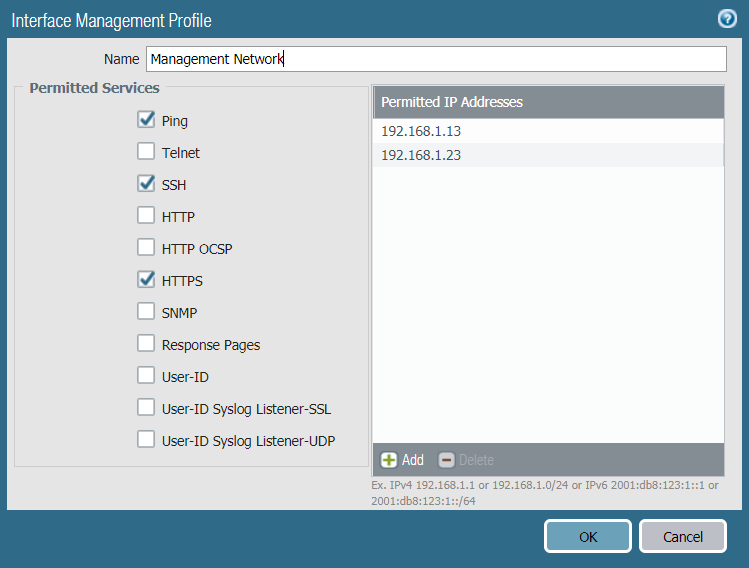
- Restrict the IP addresses that are permitted to access the management interface.Even if your firewall is on a dedicated management network that is only accessible by a device on the same VLAN or through a bastion host or VPN tunnel, you can secure the firewall further by restricting the source IP addresses that can access the management interface to those of your administrators. Limiting access to the management interface reduces the attack surface by helping to prevent access from unexpected IP addresses or subnets and prevents access using stolen credentials.
- Restrict the services that are available on the management interface.
- Do not allow access over Telnet and HTTP because these services use plaintext and are not as secure as the other services and could compromise administrator credentials. Instead, require administrators to access the firewall interfaces over SSH or HTTPS.
- Enable ping if you want to be able to test connectivity to the interface, but do not enable any other services on the management interface.
- The way you configure these settings depends on whether you are using the MGT port or a data port for access to the firewall management interfaces:
- If you are using the MGT port as your management interface, select DeviceSetupInterfaces and select the Management interface to configure the settings to restrict who can access the management interface and what services the interface allows.
![]()
- If you are using a data port as your management interface, after you configure the interface, select NetworkNetwork ProfilesInterface Mgmt and Add an interface management profile to restrict who can access the management interface and what services the interface allows.Do not attach an interface management profile that allows Telnet, SSH, HTTP, or HTTPS to an interface where you have configured a GlobalProtect portal or gateway because this will expose the management interface to the internet. Do not use HTTP or Telnet for any management interface profile because those protocols transmit in cleartext.
![]()
Manage Administrator Access
- The firewall is preconfigured with a default administrative account (admin) that provides full read-write access (also known as superuser access) to the firewall. You must change the default admin account password (DeviceAdministratorsadmin) immediately upon initial configuration.If compliance, audit, or security requirements stipulate that the default administrative account must be removed from your devices, you can remove it after you create at least one other superuser administrative account. You cannot remove the default administrative account until you configure at least one other superuser administrative account on the device.
- Configure a Firewall Administrator Account for each individual who needs access to the administrative or reporting functions of the firewall. This allows you to better protect the firewall from unauthorized configuration (or modification) and to enable logging of the actions of each individual administrator.
- Assign each administrator account to an admin role profile that limits management privileges to only those functions the individual administrator needs.
- For administrators with change privileges, require MFA using external authentication and authorization using RADIUS or SAML. See Configure Local or External Authentication for Firewall Administrators for details on how to configure external authentication with MFA.If you have a strong authentication infrastructure using smart cards, Configure Certificate-Based Administrator Authentication to the Web Interface and Configure SSH Key-Based Administrator Authentication to the CLI.If available, use privileged account management (PAM) and/or privileged identity management (PIM) solutions to secure administrator credentials externally.
- Monitor the System logs to identify abnormal account activity on any of your administrator accounts. For example, if the logs show excessive login attempts or repeated logins at certain times of day, this may indicate that an administrative account has been compromised. Also, educate all administrators about how to Use the Administrator Login Activity Indicators to Detect Account Misuse.
Create Strong Administrator Passwords
Configure a strict password policy, including
requiring frequent password changes (DeviceSetupManagementMinimum Password Complexity).
You are responsible for assessing the appropriate
password requirements for your organization; however, the following
characteristics are best practices for creating strong passwords.
Passwords should:
- Be a minimum of eight characters
- Not be based on a single dictionary word
- Not include context specific words (for example, the name of a website)
- Not include a username or derivatives of a username (for example, @dmin, Johnny)
- Not have repetitive or sequential characters (for example, aaaaaa, 1234abcd)
- Include uppercase and lowercase characters, numbers, and special characters (including spaces)
One way to
create a strong password is to create a long passphrase rather than
a complex password. Industry standards recommend creating long,
unique passphrases that you will remember easily (using whatever
characters you want, including dictionary words) instead of creating
convoluted and complex passwords that are easy to forget. Longer
passwords with a minimum of 15 characters are believed to compensate
for the use of dictionary words. Try to create a passphrase based
on long, familiar phrases that only you know or string together
at least four words.
For more information on how to determine
the appropriate password requirements for your organization, we
recommend the following resources:
Scan All Traffic Destined for the Management Interface
Because security policy
and decryption policy do not evaluate management plane traffic,
you cannot directly scan the MGT port for threats. If you are using
the MGT port as your management interface, consider routing traffic
destined for the MGT port through a data port or through another
firewall so that you can apply these important security checks to
your management traffic.
- Create security policy rules to allow access to the management interfaces of the firewall and Panorama (web interface or CLI). The way you define the policy depends on whether or not you are using a bastion host to enable access to the management network.
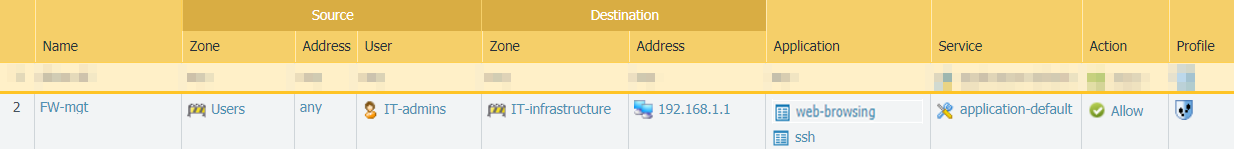
- If you are not using a bastion host to isolate your management network, create a security policy rule to allow access from the Users zone to the IT Infrastructure zone. This security policy rule must be very granular and specify the source zone, source IP address (if available), and source user group of the user attempting to access the management interface, as well as the destination zone, IP address of the appliance (firewall or Panorama), and the App-ID to identify the specific management application (web interface or CLI) running on the application default port. For example, you would use the web-browsing App-ID to allow access to the web interface and the ssh App-ID to allow access to the CLI. You must also attach a Vulnerability Protection profile to the rule, as described in the next section.The following example rule allows access from the users zone directly to the IT Infrastructure zone, and restricts access to users in the IT-admins group who are attempting to access the management interface IP address to access the web-browsing application on the application-default port only:
![]()
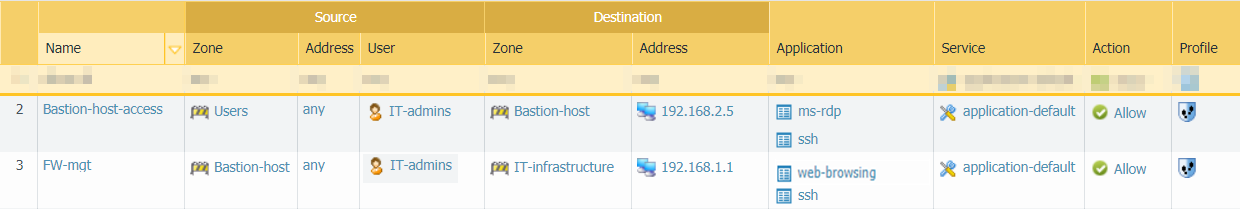
- If you are using a bastion host to enable access to your management network, you need two security policy rules: one rule to allow access from user zone to the bastion host zone and a second rule to allow access from the bastion host zone to the IT infrastructure zone. Again, both of these security policy rules should be as granular as possible and include source zone, address (if available), user and destination zone and address, and the App-ID. Keep in mind that if you are using a bastion host, the user IP address is usually the IP address of the bastion host so you cannot identify the User-ID for the administrator unless you are using the Terminal Server agent on the bastion host to identify individual users. In this case, you must also attach a Vulnerability Protection profile to both rules, as described in the next section.In the example rules that follow, the first rule allows access from the Users zone to the Bastion-host zone for users in the IT-admins group who are attempting to access the specified bastion server IP address over SSH and/or RDP. The second rule allows access to users from the Bastion-host zone to the IT-infrastructure zone attempting to access the web-browsing application on the default port on the firewall with the specified destination address.
![]()
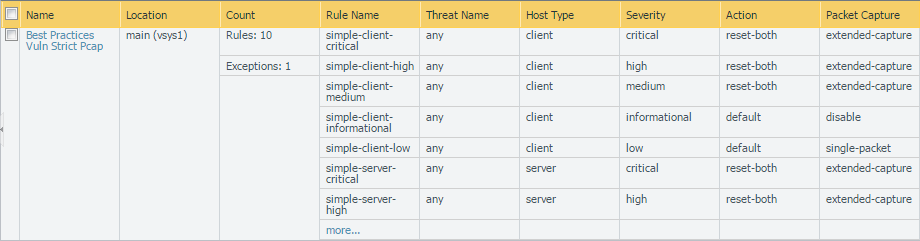
- Attach a best practice Vulnerability Protection profile to the security policy rules that allow access in to your management network to protect against buffer overflows, illegal code execution, and other attempts to exploit client- and server-side vulnerabilities. To create a profile for the purpose of protecting your management interface, clone the strict profile and then enable extended packet capture to help you track down the source of any potential attacks.
![]()
- Configure SSL Inbound Inspection or Configure SSL Forward Proxy for traffic to or from the management interface to ensure that you can decrypt and scan the traffic for threats. Attach a best practice decryption profile to the decryption policy rule to ensure that you are blocking vulnerable SSL/TLS versions such as TLS 1.0 and SSLv3, and rejecting sessions using weak encryption algorithms such as RC4 and 3DES, and weak authentication algorithms such as MD5 and SHA1.
Replace the Certificate for Inbound Management Traffic
By default, the firewall ships with a default
certificate that enables HTTPS access to the web interface over
the management (MGT) interface or any other interface that supports
HTTPS management traffic. To improve the security of inbound management
traffic, replace
the default certificate with a new certificate issued specifically
for your organization. Use certificates signed by your enterprise
CA so that users won’t learn to ignore certificate warnings. In
addition, in the SSL/TLS profile, set the Min version to TLSv1.2 so
you use the strongest protocol and set the Max version to Max so
that you continue to use the strongest protocol as stronger versions
become available.
Keep Content and Software Updates Current
Current content and software updates ensure
that you are always protected by the latest security patches and
threat updates.
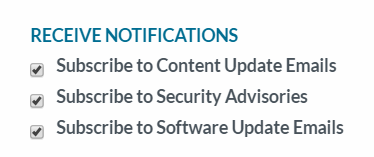
- To ensure that you are always alerted to the latest updates and security advisories, go to the Palo Alto Networks Support Portal, select Edit Profile, and Subscribe to Content Update Emails, Subscribe to Security Advisories, and Subscribe to Software Update Emails. Make sure you Save Edits.
![]()
- Follow the Best Practices for Applications and Threats Content Updates when updating to the latest content release version.
- Before you upgrade PAN-OS, read the latest release notes.